In This Issue
- Alphabet Tops Google
- Sundar Pichai to Lead
- Google Data Services
- Report from the CEO
- DreamFactory for VZ
- Vertical Mobile Video
- Digital Certs in Mobile
- Cloud and Nets Future
- Designing Cloud Apps
- Senators Clear Choice
- Human Cybersecurity
- White House’s Rules
- Billions in Investment
- Facebook on Security
- 5 Top Myths Debunked
- AWS Outage Lessons
- Coming DCIA Events
Alphabet Lets Google Chase Moonshots & Stay Profitable
Excerpted from Wired Report by Cade Metz
 Google is now many Googles.
Google is now many Googles.
Company co-founder Larry Page said in a blog post Monday that Google is reorganizing into multiple companies that will sit under a new umbrella operation called Alphabet.
Core businesses — Search, YouTube, and Android — will operate semi-separately from Google’s myriad “moonshots,” including the X lab and Page’s various life-science projects.
This unexpected transformation shows just how diverse the company has grown since its founding 17 years ago.
Though Google began as a search company, it now dabbles in everything from smartphone operating systems to product-delivery drones to cancer-detecting wristbands.
But the move also underscores that Page and his top lieutenants, including new chief financial officer Ruth Porat, are keen to prevent the moonshots from dragging down the company’s stock price and limiting its ability to attract top talent.
With Alphabet, Page can show investors that the company’s bread-and-butter businesses remain highly profitable, even if the moonshots fail… Read More
Sundar Pichai Will Lead Google with Users in Mind
Excerpted from NY Times Report by David Streitfield and Mike Isaac
 The technology industry is partial to dramatic, sometimes blustery, often larger-than-life top executives.
The technology industry is partial to dramatic, sometimes blustery, often larger-than-life top executives.
Sundar Pichai will have to work hard to be ranked among that colorful crew.
He sent news of his ascension to the top slot at Google — he is just the third person to officially run the search company — on Twitter, very obliquely.
“Thanks,” he replied on Monday to two people who had congratulated him. And that was it.
One of those messages on Twitter, from the former Facebook executive Bret Taylor, was rather understated itself. “One of the most capable technology leaders I have worked with,” Mr. Taylor called Mr. Pichai.
That is a clue to more than the personality of Google’s new leader. It is also what he wants the technology to be: a servant perfectly attuned to the user’s needs at the moment.
“I would love for my phone to scream if I am about to miss an important thing in my life, and never bother me if I’m doing something very important and the information coming in is less important than what I’m doing,” Mr. Pichai said in a recent interview… Read More
Google Bulks-Up on Data Services for its Cloud Business
Excerpted from Fortune Report by Jonathan Vanian
 Google said Wednesday that two new big data services are now available to the general public.
Google said Wednesday that two new big data services are now available to the general public.
Google has been pushing hard into the potentially lucrative business of cloud computing, in which companies rent computing power from their data centers to other businesses.
On Wednesday, Google took another step by expanding its data-crunching services that help companies build sophisticated software in the cloud.
The search giant says that customers can use its new data services, plus its other products, to build software for detecting financial fraud detection, genomics analysis, and inventory management.
Cloud Dataflow, one of Google’s new services, helps software developers build applications that require analyzing data in both real-time and over longer stretches.
Google’s other newly introduced product, Cloud Pub/Sub, helps computers and mobile devices send data back and forth.
Google’s announcement comes shortly after a corporate reorganization that puts all of its businesses under a new holding company, Alphabet… Read More
Report from DCIA CEO Marty Lafferty
 The DCIA is pleased to join with Digital Media Wire and Empiricly in the launch of their exciting new event, the New York Media Festival (NYME), from October 6th through 9th in New York City.
The DCIA is pleased to join with Digital Media Wire and Empiricly in the launch of their exciting new event, the New York Media Festival (NYME), from October 6th through 9th in New York City.
Digital Media Wire provides strategic consulting and manages marketing campaigns for digital media brands, and owns and produces industry conferences.
The company also publishes daily newsletters and operates the popular www.dmwmedia.com news and community portal.
Empiricly is an events and media company focused on the cross-section of the innovation sector and the Millennial generation.
The company helped bring the developer hackathon movement to NYC, and also founded and produces the wildly popular #techdrinkup party.
The NY Media Festival will bring together leading companies in entertainment, media, and technology for riveting discussion and debate.
Conferences will include one-day programs on Games, Video, and Music, with a focus on brands, advertising, monetization, and distribution.
NYME will also assemble the world’s most innovative start-ups, creators, and developers at the Innovation Unconference.
The “unconference” will showcase big ideas driving the future of entertainment, media, and technology.
Start-ups can apply for free exhibition space for a limited time.
The DCIA will be producing a major webcast during the NY Media Festival featuring its key conference themes of games, video, music, and innovation.
Speakers, sponsors, exhibitors, and delegates are invited to participate with interviews or solo presentations in our on-site studio or at their exhibit booths.
Find out more about participating in the NYME Webcast by contacting Digital Media Wire CEO Ned Sherman at ned@digitalmediawire.com.
And by the way, the NY Media Festival doesn’t end when the sun goes down.
Evening and night-time entertainment will include VIP dinners and receptions, Tech-Media Crawl, live music, and after-parties; stating with a gala kick-off on October 6th.
Plan now to join us for this spectacular event: click here to speak at the event; click here to sponsor or exhibit; or click here to register now.
Share wisely, and take care.
DreamFactory’s App Dev Portal for Verizon Cloud
Excerpted from Sys-Con Media Report
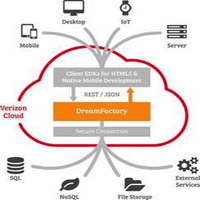 Developers now have a new, “cloud-first” platform to create enterprise applications via a new portal just launched by DreamFactory, creator of the leading open-source REST API backend for application developers, and Verizon Partner Solutions.
Developers now have a new, “cloud-first” platform to create enterprise applications via a new portal just launched by DreamFactory, creator of the leading open-source REST API backend for application developers, and Verizon Partner Solutions.
REST APIs are a type of application programming interface (API) popular for use with software applications that communicate over the Internet.
The co-branded DreamFactory-Verizon Partner Solutions portal enables developers to use DreamFactory hosted on the Verizon Cloud to connect with multiple backend databases and services, and auto-generate REST APIs to power their enterprise applications.
Once developers have tested these RESTful services on the free portal, they can easily move these backend workloads into scalable development, test, and production deployments on Verizon Cloud, the company’s enterprise-class infrastructure-as-a-service cloud-computing platform.
“DreamFactory and Verizon Partner Solutions are making it much easier for application developers to get the RESTful services they need… Read More
Advertisers Should Think Vertically in Age of Mobile Video
Excerpted from ClickZ Report by Emily Alford
 Vertical video, once seen as amateurish and annoying has become de rigueur with the advent of Snapchat and Periscope.
Vertical video, once seen as amateurish and annoying has become de rigueur with the advent of Snapchat and Periscope.
Marketers should take the trend seriously or be left behind.
Vertical video – video shot in portrait, rather than the standard landscape mode – has been a long-standing Internet joke, but the advent of mobile-first and mobile-only social platforms have given vertical video new relevance for marketers.
As apps like Snapchat, Periscope and Meerkat increasingly become important ways for marketers to engage audiences, vertical video has proven a more natural way for mobile users to view content.
In fact, Snapchat’s Evan Spiegel reports that users are nine times more likely to view a vertical video than horizontal content.
The reason viewers are more willing to watch vertical video could be because it’s more natural than turning a phone sideways, according to Rob Norman, chief digital officer for GroupM.
“In order to be successful, all media and all advertising has to have the most comfortable and organic experience,” Norman says… Read More
Digital Certificates Key to Mobile Security
Excerpted from ComputerWeekly Report by Warwick Ashford
 Digital certificates are key to any mobile security strategy, according to Mike Raggo, Director of Security Research at enterprise mobility management firm MobileIron.
Digital certificates are key to any mobile security strategy, according to Mike Raggo, Director of Security Research at enterprise mobility management firm MobileIron.
“Many companies are still trying to apply traditional security policies to mobile devices, but they do not always work because mobile operating systems are fundamentally different to those on PCs, laptops, and servers,” he told attendees of the DEF CON 23 hacker conference in Las Vegas.
Mobile operating systems, he said, have a sandboxing type of approach in how they handle apps and data, while operating systems on PCs and the data of apps is typically shared across all apps.
“On a mobile device, you also have user capabilities that allow you to share data and do things like open an email attachment and open it in a secondary app, edit it, and then upload it to Dropbox and things like that,” he said.
Raggo added that with the explosion of social media, cloud, and mobile, “data lives everywhere”, which means traditional firewalls have “vaporized.”
Additionally, with the advent of bring your own device (BYOD), users are supplying and configuring their own devices for use at work… Read More
Cloud Computing and the True Future of Networks
Excerpted from BetaNews Report by Dirk Paessler
 Cloud computing, network virtualization, and on-demand technology services are changing how we think about information technology (IT).
Cloud computing, network virtualization, and on-demand technology services are changing how we think about information technology (IT).
If these new services become as ubiquitous as predicted we could see companies accessing their IT services remotely, at the expense of their own IT infrastructure and applications.
If this happens, the thinking goes, the importance of the Local Area Network and the IT administrator could diminish as well.
It’s not worth saying the last rites over the LAN and IT administrator just yet, though.
There’s no denying that times are changing and the increasing use of cloud computing will mean a shift in ICT practices.
Cloud allows flexibility, efficiency, and can be employed for so many tasks that we will certainly see a transition on some level.
But arguably the uptake of cloud will not be on the scale, or at the speed, that is predicted.
Nor will it fundamentally change the IT administration role in the way that some assume… Read More
Designing Applications for the Cloud
Excerpted from Public Technology Report by Simon Hansford
 These days, cloud is one of the most over used terms in the computing industry.
These days, cloud is one of the most over used terms in the computing industry.
Many products and services that have existed for years have been renamed or refreshed to incorporate the word cloud to benefit from the cache, or the increased stock market value, that the term brings.
Most information technology (IT) professionals will recognize the National Institute of Standards Technology (NIST) Definition of cloud computing with three services models — Platform-as-a-Service (PaaS), Infrastructure-as-a-Service (IaaS), and Software-as-a-Service (SaaS) — four deployment models and five essential characteristics.
Both these IT professionals and their business colleagues, will have been inundated with marketing messages, case studies and proof points that reinforce that cloud computing will increase availability, reduce costs and improve the quality of IT.
Hence, any surveys that attempt to understand how widely cloud computing is understood, rather than where, when and how much it is used, will lead IT organizations to believe that there is a deep understanding of cloud computing and no further training or education on the subject is needed.
It’s possible that this superficial understanding based on skewed survey results is the single biggest barrier to more businesses benefiting… Read More
Senators Have Clear Choices on CISA in the Fall
Excerpted from Washington Examiner Report by Charlie Mitchell
 Digital privacy groups were not persuaded by a “manager’s amendment” developed by Intelligence Chairman Richard Burr (R- NC) and ranking member Dianne Feinstein (D-CA), the bill’s main sponsors, aimed at tightening the requirements on privacy and government uses of the data.
Digital privacy groups were not persuaded by a “manager’s amendment” developed by Intelligence Chairman Richard Burr (R- NC) and ranking member Dianne Feinstein (D-CA), the bill’s main sponsors, aimed at tightening the requirements on privacy and government uses of the data.
The Senate fumbled on cyber legislation as it headed out the door for a month-long recess, but perhaps set the stage for success in the fall by separating the debate on information-sharing from assorted “poison pills” that had varying degrees of relevance to cybersecurity.
Majority Leader Mitch McConnell (R-KY) and Minority Leader Harry Reid (D-NV) on August 5th ended nearly a week of back-and-forth proposals — and acrimonious public comments — on how even to proceed to the Cybersecurity Information Sharing Act (CISA) by wearily agreeing to postpone consideration until September.
They would fold the process for consideration of the so-called CISA bill into a broader deal on debating the Iran nuclear accord, with an agreement that cybersecurity could come up, at the leaders’ discretion, following the Iran debate in September. Prior to that, McConnell and Reid traded barbs all week along with their proposals for getting the CISA debate started… Read More
Cybersecurity’s Human Factor: Lessons from the Pentagon
Excerpted from Harvard Business Review Report by Michael Byers
 The vast majority of companies are more exposed to cyber-attacks than they have to be.
The vast majority of companies are more exposed to cyber-attacks than they have to be.
To close the gaps in their security, CEOs can take a cue from the US military.
Once a vulnerable IT colossus, it is becoming an adroit operator of well-defended networks.
Today the military can detect and remedy intrusions within hours, if not minutes.
From September 2014 to June 2015 alone, it repelled more than 30 million known malicious attacks at the boundaries of its networks.
Of the small number that did get through, fewer than 0.1% compromised systems in any way.
Given the sophistication of the military’s cyber-adversaries, that record is a significant feat.
One key lesson of the military’s experience is that while technical upgrades are important, minimizing human error is even more crucial. Mistakes by network administrators and users — failures to patch vulnerabilities in legacy systems, misconfigured settings… Read More
White House Issues Cybersecurity Rules for Contractors
Excerpted from The Hill Report by Cory Bennett
 The Obama administration has released draft guidelines that would require government contractors handling sensitive data to meet baseline security requirements and report digital intrusions to authorities.
The Obama administration has released draft guidelines that would require government contractors handling sensitive data to meet baseline security requirements and report digital intrusions to authorities.
The rules would also allow the Department of Homeland Security (DHS) to deploy its own network monitoring programs at a contractor if it is not meeting the necessary standards.
“The proposed guidance will strengthen government agencies’ clauses regarding the type of security controls that apply, notification requirements for when an incident occurs, and the requirements around assessments and monitoring of systems,” said the proposal from the Office of Management and Budget (OMB).
The new rules are part of a broad effort to secure government networks in the wake of a spate of cyber-attacks at high-profile agencies and contractors.
In the recent digital assault on the US government that exposed more than 21 million people’s data, suspected Chinese hackers were able to crack Office of Personnel Management networks after lifting a contractor’s security credentials.
That contractor, KeyPoint Government Solutions, is one of two major background-check processors that were breached… Read More
Investors Pour Billions into Cybersecurity Firms
Excerpted from CSO Report by Tom Morgan
 Venture capital firms and corporate investors have put a record amount of money in to cybersecurity companies over the past year, and there’s no end in sight.
Venture capital firms and corporate investors have put a record amount of money in to cybersecurity companies over the past year, and there’s no end in sight.
Last week we reported that the cybersecurity market is white hot, and we shared a list of mergers and acquisitions in the space. We promised to follow up this week with VC and corporate investment deals, so here it comes.
Before we give you the list of deals, let’s set the stage with some cyber market figures and goings-on.
The worldwide cybersecurity market is defined by market sizing estimates that range from $77 billion in 2015 to $170 billion by 2020. We broke these numbers down in a previous blog.
Globally, venture-backed cybersecurity companies raised $1.9 billion last year, a record, according to Dow Jones VentureSource.
CB Insights reported that in the first half of 2015, venture firms invested $1.2 billion into cybersecurity startups.
Yup, you read it correctly – one point two billion in just the first six months of 2015… Read More
Facebook Calls for Cybersecurity in Emerging Markets
Excerpted from Financial Times Report by Hannah Kuchler
 Facebook‘s new security chief has called on the Internet industry to go beyond securing the web “for the 1 per cent” and create cyber security defenses that will work across emerging markets.
Facebook‘s new security chief has called on the Internet industry to go beyond securing the web “for the 1 per cent” and create cyber security defenses that will work across emerging markets.
Alex Stamos, a former Yahoo security executive famous for his vehement criticism of the US National Security Agency, said he would prioritize building security solutions to protect people who do not have the benefits of the most up to date technology.
Speaking on the sidelines of the Def Con cybersecurity conference in Las Vegas, NV, Mr. Stamos said consumer Internet companies such as Facebook could not rely on the security industry to keep all their users across the world safe.
“We can’t say you are only safe if you are on the latest phone in a country with a great human rights record,” he said.
Responsibility for fighting hackers has landed mainly with the private sector, unlike so-called offline criminals who are targeted by law enforcement agencies.
Private sector companies tend to target wealthy customers such as banks rather than ordinary users in developing countries… Read More
Debunking Top 5 Myths Keeping Businesses from the Cloud
Excerpted from B2B News Report by Jeff Blackey
 The use of cloud computing in business has flourished over the past decade with exponential growth in adoption rates over the last several years.
The use of cloud computing in business has flourished over the past decade with exponential growth in adoption rates over the last several years.
Enterprise cloud subscription revenues are foretast to reach $67 billion by 2018, attaining a compound annual growth rate of 17.3 percent in the forecast period.
Despite its undeniable popularity, it is the subject of numerous misconceptions and myths preventing businesses from leveraging its benefits.
Below are the five biggest myths about cloud computing exposed.
Myth 1: Cloud is Less Secure than On-Premise Solutions
Cloud computing is often perceived as being less secure than traditional premise-based environments, as many assume that the cloud operates like the Internet, as an open network susceptible to countless threats.
However, there have been very few reported security breaches in the public cloud to date… Read More
AWS Outage Shows Need for Decentralized Cloud Computing
Excerpted from Inside Bitcoins Report
 This morning, Amazon Web Services (AWS) underwent a major cloud outage, causing both its Elastic Compute Cloud and Simple Storage Service solutions to receive many request errors in the United States.
This morning, Amazon Web Services (AWS) underwent a major cloud outage, causing both its Elastic Compute Cloud and Simple Storage Service solutions to receive many request errors in the United States.
AWS is a cloud computing solutions provider ran by Amazon, a company most known for its large online retail network.
Amazon began investigating a rise in errors for requests made to Amazon S2 in the US-STANDARD region at 12:36 AM PDT.
Just a few minutes after this investigation began, the company reported even more errors for the EC2 APIs and launch failures for EC2 instances in Amazon’s US-EAST-1 region.
Additionally, AWS experienced heightened latencies in its SendEmail, SendRawEmail, and Send SMTPEmail APIs in the US-EAST-1 region.
Two AWS customers, Heroku and GitHub, have confirmed that they have experienced issues due to the AWS outage.
Heroku reported that customers could not push changes to their apps, while GitHub users saw increased error rates on repository release downloads and issue image uploads… Read More
Coming Events of Interest
Cloud Partners 2015 — September 16th-18th in Boston, MA. This Informa-hosted conference is totally focused on how the cloud can mean business for you. Learn how to enable scale, impact, and action based on cloud services.
The Internet of Things (IoT) Show — September 2nd-23rd in Singapore. The IoT Show will facilitate new collaborations and partnerships as well as generate new ideas and thinking. The IoT Show is about getting the prototypes out of the lab and into the market.
ADRM Working Group Meeting — September 24th via Global Videoconference. Contact the DCIA for information about joining the group and attending the meeting that will focus on interoperability among DRM platforms and simplifying DRM implementation.
New York Media Festival — October 6th-9th in New York, NY. NYME brings together 5,000 expected attendees including 1,500 senior digital, games, music, television, advertising and video leaders, brands, investors and start-ups. Networking, meetings and deal-making.
Digital Hollywood Fall — October 19th-22nd in Marina Del Rey, CA. The future of the entertainment industry. Digital Hollywood debuted in 1990 and has from its start been among the leading trade conferences in its field.
2015 US Cyber Crime Conference — November 14th-20th in National Harbor, MD. This is the only event of its kind that provides both hands-on digital forensics training and an interactive forum for cyber professionals to network.
Internet of Things World Forum (IoTWF) — December 6th-8th in Dubai, . IoTWF is an exclusive event that brings together the best and brightest thinkers, practitioners, and innovators from business, government, and academia to accelerate the market adoption of the Internet of Things.
