In This Issue
- Cybersecurity in 2017
- Early Trump Priority
- Data Sleeping Giant
- Report from the CEO
- Corporate Boards
- China’s Cybersecurity
- CIA & Russian Hacking
- Mach Lrning / Gov Sec
- Cloud to Keep Growing
- Nets & Sec Converge
- Enterprise Storage
- Big Data Will Evolve
- Hottest Tech Skills ’17
- AV and Cybersecurity
- Edge, Fog, and IoT
- Is Computing Cool?
- Coming DCIA Events
2017 Cybersecurity Predictions
Excerpted from ISMG Report by Tom Kellermann
 Hacks sponsored by nation-states and attacks fueled by IoT-powered botnets are just some of the daunting threats we will see in 2017, says cybersecurity thought leader Tom Kellermann.
Hacks sponsored by nation-states and attacks fueled by IoT-powered botnets are just some of the daunting threats we will see in 2017, says cybersecurity thought leader Tom Kellermann.
What are his top predictions, and how should security leaders respond?
To start with, the era of “civil” cyberwarfare is over.
Kellermann says 2017 is the year when the gloves will come off and attacks will get messier and more damaging.
“What is most concerning to me right now is that much of US critical infrastructure has been colonized by one nation-state or an adversary with backdoors and remote access terminals that would allow for them to re-enter these systems and conduct destructive attacks – like the manipulation of time or the manipulation of the integrity of data in critical systems that have a kinetic impact on society,” says Kellermann, CEO of the venture capital firm Strategic Cyber Ventures.
“I do think that geo-political tensions will serve as a harbinger for destructive cyberattacks,” he adds.
“And really, it’s a question of what our priorities will be nationally to protect ourselves from these attacks… Read More
Cybersecurity Early Trump Priority
Excerpted from NPR Report by Brian Naylor
 Cybersecurity presents an early challenge for incoming US President Donald Trump.
Cybersecurity presents an early challenge for incoming US President Donald Trump.
State-sponsored hacking is “arguably one of the biggest threats to the nation,” says Jay Kaplan, a former analyst at the National Security Agency.
State actors are behind numerous recent hacks, including the federal employee records at the Office of Personnel Management, believed to be the work of China.
In a recent report on enhancing national cybersecurity, the Obama administration avoided addressing the issue of state-sponsored hacking head-on.
But it did recommend steps – including training 100,000 new “cybersecurity practitioners” by 2020 – to fix vulnerabilities in government and private networks.
Crowdsourcing offers a path to tackle the challenge, Kaplan says.
He is CEO of Synack, which is working with the Pentagon using crowdsourcing “to uncover security holes across the federal government… Read More
Data Security Sleeping Giant
Excerpted from The Hill Report by Thomas Pahl
 The Consumer Financial Protection Bureau (CFPB) burst onto the scene almost a half dozen years ago, wielding broad new powers on a mission to protect consumers of financial goods and services.
The Consumer Financial Protection Bureau (CFPB) burst onto the scene almost a half dozen years ago, wielding broad new powers on a mission to protect consumers of financial goods and services.
The CFPB has aggressively used its authority to remake the federal consumer financial protection scheme, to the delight of some and to the dismay of others.
But few realize that the CFPB could have used its power to drastically reshape data security practices at financial firms.
Yet it never has. Few are aware that the CFPB is a sleeping giant on data security.
Congress has never assigned the CFPB any specific responsibility for data security.
With the passage of the Dodd-Frank Act, Congress did not transfer to the CFPB the authority to enforce the data security and identity theft requirements of the Gramm Leach Bliley Act and the Fair Credit Reporting Act.
The Federal Trade Commission (FTC) retained the authority to enforce these requirements.
That said, much of the development of data security law has come not through enforcing these statutes but through the FTC… Read More
Report from DCIA CEO Marty Lafferty
 President-elect Donald Trump this week named Thomas Bossert, who had served as a national security aide in the George W. Bush administration, as his chief advisor on cybersecurity.
President-elect Donald Trump this week named Thomas Bossert, who had served as a national security aide in the George W. Bush administration, as his chief advisor on cybersecurity.
Bossert currently consults privately on homeland security matters as a fellow at the Atlantic Council’s Cyber Statecraft Initiative.
Previously, he helped draft the federal government’s first cybersecurity strategy as Deputy Homeland Security Advisor under President Bush.
Bossert also served as White House Director of Infrastructure Protection Policy for two years.
In accepting his appointment, Bossert said the US, “must work toward a cyber doctrine that reflects the wisdom of free markets, private competition, and the important but limited role of government in establishing and enforcing the rule of law, honoring the rights of personal property, the benefits of free and fair trade, and the fundamental principles of liberty.”
As an Assistant to President Trump, Bossert will operate with independent status at the same level as incoming National Security Advisor Michael Flynn, ensuring that he has the authority needed to be successful in the role.
This structure represents an elevation of the position currently held by Lisa Monaco in the Obama White House; Bossert’s focus will be on domestic security concerns, while Flynn will address international security threats.
His appointment and the cabinet restructuring have received bipartisan support with Congressmen Peter King (R-NY) and Bill Keating (D-MA), for example, commenting respectively that, “It’s important to have someone at the White House at the level of the national security advisor who is dealing with counterterrorism,” and, “It’s a good move strategically.”
Frank Cilluffo, who worked with Bossert during the Bush administration and now heads George Washington University’s Center for Cyber and Homeland Security, added that Bossert will bring to the job deep knowledge of White House operations, which will be particularly valuable for this assignment. Share wisely, and take care.
Corporate Boards Unprepared for Cyberattacks
Excerpted from Computerworld Report by Matt Hamblen

Major cyberattacks against organizations of all sizes seem to happen almost weekly.
On December 14th, Yahoo announced the largest-ever data breach, involving more than 1 billion customer accounts.
Despite the scale and potential harm from such attacks, there’s wide recognition that corporate leaders, especially boards of directors, aren’t taking the necessary actions to defend their companies against such attacks.
It’s not just a problem of finding the right cyber-defense tools and services, but also one of management awareness and security acumen at the highest level, namely corporate boards.
“Our country and its businesses and government agencies of all sizes are under attack from a variety of aggressive adversaries and we are generally unprepared to manage and fend off these threats,” said Gartner analyst Avivah Litan, a longtime cybersecurity consultant to many organizations.
“Some organizations do a better job than others, but those efforts are almost always led by CIOs, CISOs or business line managers and not by corporate boards, CEOs and executive management throughout government and the private sector,” Litan added… Read More
China’s Cybersecurity Efforts Pose Challenges
Excerpted from NY Times Report by Paul Mozurdec
 It has been a tough year in China for America’s technology companies.
It has been a tough year in China for America’s technology companies.
Uber sold off its operations there. Beijing ordered some of Apple’s services shuttered. And Microsoft faced a new inquiry.
Now, in the final days of 2016, China’s internet regulator suggested the coming year may be even trickier.
A report by the regulator on Tuesday suggested it would formalize a cybersecurity review system on tech products in the country.
That could mean another problematic step for foreign tech firms in what has already become a tough market.
The report did not offer details about what the government checks would look for, but the language was similar to that described in an article in the NY Times in May about foreign companies quietly submitting to security checks targeting encryption and data storage.
Over the course of 2016 and part of 2015, a number of major foreign technology companies were subject to secretive Chinese security reviews. During the checks, Chinese officials would ask employees of the companies to answer questions… Read More
CIA Won’t Publicize Russian Hacking Evidence
Excerpted from Washington Post Report by Steven Hall
 In December, during a closed door briefing with Senators, the CIA shared a secret assessment.
In December, during a closed door briefing with Senators, the CIA shared a secret assessment.
The agency concluded it was now “quite clear” that Russia’s goal was to help Donald Trump win the White House.
“If I can’t use this information, then what good is it to have it?! Why even collect it in the first place?!”
It’s a cry of frustration, an angry rhetorical exclamation I heard many times during my 30-year career as an operations officer at the CIA.
Usually it comes from ambassadors or senior members of the national security apparatus in Washington, DC, and occasionally even from analysts in the intelligence community who have been provided with a truly stunning piece of information acquired clandestinely from human or technical sources.
The sense of frustration among these consumers of intelligence is heightened when the topic is critical and timely, and when both the government and the American public are clamoring for answers to difficult questions.
This is precisely where we as a nation find ourselves when discussing the claim by the US intelligence community… Read More
Machine Learning & Gov Cybersecurity in 2017
Excerpted from Nextgov Report by Haiyan Song
 Email security, ransomware, insider threats, and state-sponsored attacks have been headline news for the past year.
Email security, ransomware, insider threats, and state-sponsored attacks have been headline news for the past year.
Cybersecurity, which is generally viewed as bipartisan issue, has officially made it into the mainstream consciousness as a result.
And while it’s certainly never good to see news that another breach occurred, one positive outcome has been increasing conversations about the cyber-oriented world in which we all live and work, and the serious security challenges private-sector and government organizations face going forward.
These discussions are happening now and part of the focus needs to be on the future of cybersecurity, and identifying what’s on the horizon so organizations from every business sector can prepare.
Below are some security predictions for 2017 that will undoubtedly affect both industry and government operations moving forward.
The internet is a critical infrastructure: distributed denial-of-service attacks (DDoS) – like the Mirai botnet powered – on Dyn… Read More
Why Computing Cloud Will Keep Growing
Excerpted from NY Times Report by Quentin Hardy

Jeff Bezos of Amazon, along with a couple of his rivals, may eventually control much of the $1 trillion global market for business computers and software.
That is because Amazon Web Services, his big-business computing division, is starting to affect more than just the world of computer servers, data storage and networking at the core of computing.
Increasingly, it is also entangled with mobile phones, sensors and all sorts of other devices in the so-called Internet of Things.
It’s the same story at Microsoft Azure and Google Cloud Platform, the other two big cloud companies.
Start-ups and giant corporations rent the core resources, along with related software, instead of owning and running their own machines.
What’s next? As innovations like artificial intelligence and connected devices become popular, customers are putting cloud components in mobile computing, home games and email marketing campaigns. In other words, the big clouds aim to be everywhere… Read More
Will Networks and Security Converge in 2017?
Excerpted from Network World Report by Steve Garson and Dave Greenfield
 Bold predictions are in order at this time of year.
Bold predictions are in order at this time of year.
Zeus Kerravala looked into his crystal bowl for the networking space, and Taylor Armeriding did the same for security.
We went rummaging through our fortune cookies and came up with this Yoda-like one for 2017:
Security shall networking become.
What did that really mean? Our Yoda translator was of no help.
Could networking replace security (or vice versa) in 2017? Should CIOs and CISOs prepare themselves for the inevitable assimilation (head nod to you aging Trekies)?
How should, then, security and networking personnel prepare themselves for the inevitable onslaught?
We had our own ideas, of course, but we want to see what others thought, as well.
So we chased down a few SD-WAN vendors for their input at the end of galaxy (killer delay, but no black holes)… Read More
Things to Watch in Enterprise Storage in 2017
Excerpted from Forbes Report by Gina Longoria
 Enterprise storage has historically been a market that is slow to change, but a number of factors are making this an interesting space to watch right now.
Enterprise storage has historically been a market that is slow to change, but a number of factors are making this an interesting space to watch right now.
Vendors like Dell EMC, Hewlett Packard Enterprise (HPE), NetApp, Pure Storage, and others are servicing the storage market with on-premise traditional storage systems and server-based storage products.
In addition, these traditional storage vendors are being challenged by public cloud storage-as-a-service offerings from the likes of Amazon AWS, Google Cloud, Microsoft Azure, and others.
I expect to see a unique set of dynamics play out in enterprise storage over the coming years.
Here are the top five things I believe will have a major influence on the enterprise storage market in 2017.
New data models will drive the need for new storage technologies.
The confluence of mobile applications, cloud computing and the internet of things (IoT) is causing massive increases in the volume of data that needs to be moved, processed and stored by IT… Read More
How Will Big Data Evolve in the Year Ahead?
Excerpted from Newsfactor Network Report by Shirley Siluk

People, organizations and things will continue to generate ever-larger volumes of data in the months and years ahead, but expect to see some changes in how that information will be put to use, not just by humans but by artificial intelligence (AI) as well.
A recent survey by the analyst firm Gartner, for instance, found that while big data technologies are seeing more overall investment, that spending will be done by fewer companies over the next couple years.
And that trend is likely to lead to a growing divide between organizations that “know” and those that don’t, according to IDC.
Big data users will also need to ask deeper questions about the kinds of information they are and aren’t collecting and analyzing.
Beyond that, they’ll need to honestly consider their willingness to act on results that might conflict with old ways of doing business, according to Gartner.
That last lesson is one that Gartner Research Director Robert Hetu pointed out shortly after the results of the US Presidential election… Read More
Hottest Tech Skills for 2017
Excerpted from Forbes Report by Louis Columbus
 38% of enterprises plan to increase spending on data analytics (big data, enterprise analytics, data mining, and business intelligence) in 2017.
38% of enterprises plan to increase spending on data analytics (big data, enterprise analytics, data mining, and business intelligence) in 2017.
47% plan to increase spending on security technologies (access control, intrusion prevention, virus/malware protection, identity management, privacy) in 2017.
Improving employee productivity/efficiency (47%) and increasing customer satisfaction/experience (46%) are the top two business priorities for IT departments in the next 12 months.
These and many other insights are from Computerworld’s Tech Forecast 2017 survey published earlier this month.
A summary of the results can be downloaded here.
The survey has completed online by technology professionals with IT management-level titles and higher between June 30th and September 2nd of this year.
The results are based on 196 responses. For additional details of the methodology and results, please see the summary… Read More
AV Cybersecurity Will Require Restraint
Excerpted from Bloomberg BNA Report by Darren Teshima and Ian Adams
 In the rapidly evolving internet of things environment, federal regulators must be flexible to accommodate change, and they must resist the urge to ensconce autonomous vehicle cybersecurity guidance in law.
In the rapidly evolving internet of things environment, federal regulators must be flexible to accommodate change, and they must resist the urge to ensconce autonomous vehicle cybersecurity guidance in law.
Concerns about the vulnerability of America’s physical infrastructure have long been at the top of mind for national security officials.
But the growing threat of cyberattacks, both state sponsored and criminal, have led state and federal officialdom to take note.
Their concern has been magnified by the increasing number of significant cybercrime targets in the nation, including key infrastructure.
In particular, the rapid expansion of the internet of Things (IoT) – reports estimate that by 2020, there will be 30 billion connected things and 40 percent of all data generated will come from connected sensors – has increased the risk that this age’s technological wonders may be vulnerable to unfriendly manipulation.
This IoT cybersecurity risk was highlighted by the recent distributed denial of service (DDoS) attack that shut down sites like Twitter… Read More
Edge, Fog, IoT, and Securing Them All
Excerpted from CircleID Report by Gunter Ollmann
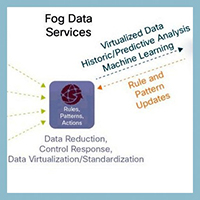 The oft used term “the Internet of Things” (IoT) has expanded to encapsulate practically any device (or “thing”) with some modicum of compute power that in turn can connect to another device that may or may not be connected to the Internet.
The oft used term “the Internet of Things” (IoT) has expanded to encapsulate practically any device (or “thing”) with some modicum of compute power that in turn can connect to another device that may or may not be connected to the Internet.
The range of products and technologies falling in to the IoT bucket is immensely broad – ranging from household refrigerators that can order and restock goods via Amazon, through to Smart City traffic flow sensors that feed navigation systems to avoid jams, and even implanted heart monitors that can send emergency updates via the patient’s smartphone to a cardiovascular surgeon on vacation in the Maldives.
The information security community – in fact, the InfoSec industry at large – has struggled and mostly failed to secure the “IoT”. This does not bode well for the next evolutionary advancement of networked compute technology.
Today’s IoT security problems are caused and compounded by some pretty hefty design limitations – ranging from power consumption, physical size and shock resistance, environmental exposure, cost-per-unit, and the manufacturers overall security knowledge and development capability. The next evolutionary step is already underway – and exposes a different kind of threat and attack surface to IoT… Read More
Is Computing as Cool and Fun as It Once Was?
Excerpted from Slashdot Report
 I got together with old computer nerd friends the other day.
I got together with old computer nerd friends the other day.
All of us have been at it since the 8-bit/1980s days of Amstrad, Atari, Commodore 64-type home computers.
Everybody at the meeting agreed on one thing — computing is just not as cool and as much fun as it once was.
One person lamented that computer games nowadays are tied to internet DRM like Steam, that some crucial DCC software is available to rent only now (e.g. Photoshop) and that many “basic freedoms” of the old-school computer nerd are increasingly disappearing.
Another said that Windows 10’s spyware aspects made him give up on his beloved PC platform and that he will use Linux and Android devices only from now on, using consoles to game on instead of a PC because of this.
A third complained about zero privacy online, internet advertising, viruses, ransomware, hacking, crapware.
I lamented that the hardware industry still hasn’t given us anything resembling photorealistic realtime 3D graphics, and that the current VR trend arrived a full decade later than it should have… Read More
Coming Events of Interest
CES 2017 — January 5th-8th in Las Vegas, NV. More than 3,800 exhibiting companies showcasing innovation across 2.4 million net square feet, representing 24 product categories.
Industry of Things World USA — February 20th-21st in San Diego, CA. Global leaders will gather to focus on monetization of the Internet of Things (IoT) in an industrial setting.
fintech:CODE — March 16th-17th in London, UK. A new international knowledge exchange platform bringing together all DevOps, IT, and IoT stakeholders who play an active role in the finance and tech scene. Key topics include software development, technical challenges for DevOps, DevOps security, cloud technologies and SaaS.
retail:CODE — March 16th-17th in London, UK. 20 real-life case studies, state-of-the-art keynotes, and interactive World Café sessions, 35+ influential speakers will share their knowledge at the intersection of the retail and technology sectors.
Delivery of Things World — April 24th and 25th in Berlin, Germany. Over 400 IT executives will discuss what DevOps really means for business. This event brings together all stakeholders to share their experience and expertise.
Security of Things World — June 12th and 13th in Berlin, Germany. A world class event focused on the next information security revolution. Security concerns that preoccupy enterprise customers today and pragmatic solutions to threats.
