In This Issue
SolidFire Now Officially Part of NetApp
Excerpted from Forbes Report by Justin Warren
 NetApp announced today that the company has completed its acquisition of scale-out flash array maker SolidFire.
NetApp announced today that the company has completed its acquisition of scale-out flash array maker SolidFire.
I spoke to SolidFire Principal Architect Jeremiah Dooley and NetApp Flash Architect Andy Grimes at the TECH.unplugged conference today in Austin, TX about the announcement.
Dooley confirmed that SolidFire will remain a separate entity within the larger NetApp, with the existing field sales team.
“Our staff and our customers were very happy to hear that all staff would be staying,” he said.
The existing brand will also be maintained for a time, though Dooley speculates that it will probably be retired at some point “but not in the foreseeable future.”
Grimes praised the SolidFire culture, and emphasized NetApp’s desire to maintain it now that the acquisition has completed.
Dooley was keen to reinforce that being owned by NetApp only meant positive things for SolidFire. “We have access to a much bigger budget now,” he joked.
Dooley also told me that my interview with NetApp CEO George Kurian and SolidFire’s then CEO, Dave Wright is being used as a primer… Read More
Clinton Calls Cybersecurity an Important Challenge
Excerpted from The Washington Free Beacon Report by Alyssa Canobbio
 At the end of a get-out-the-vote campaign event in New Hampshire on Wednesday, Hillary Clinton was asked about her plans for protecting cybersecurity.
At the end of a get-out-the-vote campaign event in New Hampshire on Wednesday, Hillary Clinton was asked about her plans for protecting cybersecurity.
“It is one of the most important challenges the next president is going to face,” Clinton said.
Clinton said that the technology offenses conducted by hostile states have become more advanced.
She named Russia, China, Iran, and North Korea as countries that are just going to accelerate their attacks on the cyber-infrastructure of the United States.
“We first have to figure how to create what would be an understanding with these nations that we will not tolerate their cyber theft and their cyber evasiveness, and we certainly would never ever sit still for a cyber-attack,” Clinton said.
Clinton also spoke of another level of cyber-attackers that is made up of terrorist networks and hacker networks who have nothing to lose when they release a cyber-attack.
Clinton added that the US needs to work on both levels to prevent attacks from happening and giving them the information they want… Read More
Some Consumers Pay Attention to Cybersecurity
Excerpted from NetworkWorld Report by Fredric Paul
 When it comes to cybersecurity, it’s long been safe to assume that almost nobody is doing much of anything to protect themselves.
When it comes to cybersecurity, it’s long been safe to assume that almost nobody is doing much of anything to protect themselves.
But a new survey by credit-monitoring company Experian reveals that notion may no longer be completely accurate.
While the survey of more than 1,000 US adults, conducted by Edelman Berland in September 2015, reveals plenty of the kind of security holes that give professionals nightmares, it also showed that a significant number of people are now paying at least some attention to online security and privacy issues.
I don’t think we’ll ever get to fully secure online experience, but frankly, I expected far worse.
For one thing, the vast majority of respondents now seem to be aware that cybersecurity is something they ought to be worried about.
A whopping 93% say identity theft is a growing problem, for example, and more than 9 out of 10 (91%) believe that people should be more concerned about the issue (some 71% worry that it will happen to them).
Almost three quarters (73%) are worried about making online purchases, and more than two-thirds (69%) say they’re concerned… Read More
Report from DCIA CEO Marty Lafferty
 US House of Representatives Judiciary Committee Chairman Bob Goodlatte (R-VA) this week issued the following statement.
US House of Representatives Judiciary Committee Chairman Bob Goodlatte (R-VA) this week issued the following statement.
“In March, the House Judiciary Committee plans to markup the Email Privacy Act, a bipartisan bill to reform the Electronic Communications Privacy Act (ECPA) of 1986.
Over the past several years, the Committee has conducted robust oversight of this decades-old law and has worked with stakeholders to identify reform priorities.
It’s clear that the law needs to be modernized and updated to ensure it keeps pace with ever-changing technologies so that we protect Americans’ constitutional rights and provide law enforcement with the tools they need for criminal investigations in the digital age.
I look forward to moving this legislation through the Committee next month and working with House leaders to bring the bill to the floor.”
As DCINFO readers will recall, the DCIA participates in the Digital Due Process (DDP) coalition, which advocates long overdue ECPA reform.
We strongly supported the testimony of Chris Calabrese, Vice President, Policy, at the Center for Democracy and Technology (CDT), at December’s Hearing on this subject, and we opposed those who spoke against his views.
There is simply no need for the carve-outs sought by opponents to weaken privacy protections, circumvent judicial oversight, and evade the warrant requirement.
We also supported the views of Google’s Director of Law Enforcement Information and Security, Richard Salgado, whose testimony cited the Riley v. California Supreme Court decision requiring law enforcement to obtain a warrant before searching digital content on a mobile phone, and the fact that four states have already updated their own versions of ECPA.
Currently proposed federal legislation to reform ECPA will provide the same level of safety and security to digital data as US citizens already have for printed material.
HR 699 now has the backing of 304 Members of Congress, a significant majority of both parties.
It’s time, finally, to extend the fourth amendment to the digital world and bring basic privacy protection into the twenty-first century. Share wisely, and take care.
US Declares 22 Clinton Emails “Top Secret”
Excerpted from Associated Press News Report by Bradley Klapper
 The Obama administration confirmed for the first time Friday that Hillary Clinton’s home server contained closely guarded government secrets, censoring 22 emails that contained material requiring one of the highest levels of classification.
The Obama administration confirmed for the first time Friday that Hillary Clinton’s home server contained closely guarded government secrets, censoring 22 emails that contained material requiring one of the highest levels of classification.
The revelation comes three days before Clinton competes in the Iowa presidential caucuses.
State Department officials also said the agency’s Diplomatic Security and Intelligence and Research bureaus are investigating if any of the information was classified at the time of transmission, going to the heart of Clinton’s defense of her email practices.
The department published its latest batch of emails from her time as secretary of state Friday evening.
But The Associated Press learned ahead of the release that seven email chains would be withheld in full for containing “top secret” information.
The 37 pages include messages a key intelligence official recently said concerned “special access programs” — highly restricted, classified material that could point to confidential sources or clandestine programs like drone strikes.
The documents are being upgraded at the request of the intelligence community because they contain a category of top secret information… Read More
New Techs Provide Ample Means to Track Suspects
Excerpted from NY Times Report by David Sanger
 For more than two years the FBI and intelligence agencies have warned that encrypted communications are creating a “going dark” crisis that will keep them from tracking terrorists and kidnappers.
For more than two years the FBI and intelligence agencies have warned that encrypted communications are creating a “going dark” crisis that will keep them from tracking terrorists and kidnappers.
Now, a study in which current and former intelligence officials participated concludes that the warning is wildly overblown, and that a raft of new technologies — like television sets with microphones and web-connected cars — are creating ample opportunities for the government to track suspects.
“‘Going dark’ does not aptly describe the long-term landscape for government surveillance,” concludes the study, titled, “Don’t Panic: Making Progress on the ‘Going Dark’ Debate,” to be published Monday by the Berkman Center for Internet and Society at Harvard.
The study argues that the phrase ignores the flood of new technologies “being packed with sensors and wireless connectivity” that are expected to become the subject of court orders and subpoenas, and are already the target of the National Security Agency as it places “implants” into networks around the world to monitor communications abroad.
The products, range from toasters to bedsheets, light bulbs, cameras, toothbrushes, door locks, cars, watches and other wearables… Read More
Cybersecurity: 2 People Separated by Common Language
Excerpted from Financial Services Report by Murray Kenyon
 Early in my federal government career, I worked for a time in England.
Early in my federal government career, I worked for a time in England.
There I learned the humor — and truth — of the old maxim that “England and America are two countries separated by a common language.”
Similarly, since entering the private sector at FSR last year, I’ve realized that when government and industry communicate, we may use the same words, but we sometimes don’t mean the same thing.
Passage of the Cybersecurity Act of 2015 provides us a new and important opportunity to make sure we’re using the same words AND meaning the same thing.
The Administration has not yet involved industry in helping shape the cyber-threat information sharing policies and procedures that are due to Congress on February 17th. It’s understandable that there are constraints given the 60-day deadline Congress established, but this law took years to pass and the ball can’t be fumbled at implementation.
FSR and other well-meaning public- and private-sector individuals have rallied around the notion of robust public-private sharing of cyber-threat information for at least the last several years… Read More
Help Wanted: 1,000 Cybersecurity Jobs at OPM
Excerpted from Forbes Report by Steve Morgan
 There are one million cybersecurity job openings in 2016.
There are one million cybersecurity job openings in 2016.
Where are all of those jobs?
This week we take a look at the cybersecurity job boom in the US government sector.
The Office of Personnel Management (OPM) suffered the largest cyber-attack over the past year, resulting in the theft of contact records on more than twenty million people including those who applied for government security clearances and went through background checks, and nearly two million spouses and domestic partners of those applicants.
As the OPM hack news unraveled, it got worse — revealing that hackers stole the digital fingerprints of more than five million people employed by the US federal government… the same fingerprints that are sometimes used for access to so-called locked down buildings and computers.
OPM recently announced it is hiring 1,000 new cybersecurity professionals, which have been approved by the US Department of Homeland Security (DHS).
Federal News Radio recently listed the duties the new cyber hires will carry out — which includes cyber-risk and strategic analysis… Read More
Alphabet Grows Briskly to Close in on Apple
Excerpted from NY Times Report by Conor Dougherty
 Wall Street got its first glimpse of the financial details of a new conglomerate called Alphabet on Monday.
Wall Street got its first glimpse of the financial details of a new conglomerate called Alphabet on Monday.
Investors liked what they saw so much that the outfit formerly known as Google is poised to become the world’s most valuable company.
Despite spending $3.6 billion a year on projects like self-driving cars that don’t make much money, Alphabet’s advertising business propelled the company to a strong last three months of 2015, outpacing expectations and sending the stock up in after-hours trading.
Now, when Wall Street opens for business on Tuesday, Alphabet will most likely be worth more than Apple, which has been the most valuable company in the world for nearly four years.
Apple is still generating enviable profits but is dealing with concerns that its franchise iPhone business is slowing down.
If investors are sending any sort of signal to big tech companies, which have taken their lumps from shareholders this year, it is simply this: You are free to spend on side projects so long as your main business is not showing signs of weakness.
“The main thing is the core business,” said Josh Spencer, who manages T. Rowe Price’s Global Technology Fund… Read More
Cognitive Cloud Computing Can Transform Companies
Excerpted from Business Standard Report
 Ginni Rometty, Chairman, President and Chief Executive Officer of US information technology giant IBM, said India had the potential to grow at 10 per cent annually for the next two years. This century could, she felt, be India’s.
Ginni Rometty, Chairman, President and Chief Executive Officer of US information technology giant IBM, said India had the potential to grow at 10 per cent annually for the next two years. This century could, she felt, be India’s.
Speaking at IBM’s flagship customer event, ‘Think Forum’, she spoke at length about IBM’s cognitive cloud computing system, Watson, and how it had the potential to transform companies across the board.
Watson is an artificially developed intelligence that works in natural languages.
Currently, it is being applied in 36 countries and at a little more than 5,000 companies in the world. “Watson will not replace us but assist us.”
“This cognitive system is human plus machine,” she said.
Asked how the system could benefit India, she said Watson can provide technical support, reduce the time to solve problems and offer a platform for the growing start-up system, among other things. During the session, Martin Jetter, Senior Vice-President at IBM, got into a conversation with Himanshu Kapania, Managing Director, Idea Cellular.
In the past eight years, said Kapania, they had grown at a fast pace and one of the factors was a cognitive system… Read More
Microsoft and Google Lead Cloud Growth — AWS Rules
Excerpted from Datamation Report by Pedro Hernandez
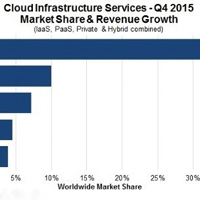 Amazon Web Services (AWS) is still the cloud provider to beat, but other IT titans are growing faster, according to a new analysis from the Synergy Research Group.
Amazon Web Services (AWS) is still the cloud provider to beat, but other IT titans are growing faster, according to a new analysis from the Synergy Research Group.
With nearly a third of the cloud infrastructure services market, AWS closed out the fourth quarter (Q4) of 2015 in first place. “Amazon/AWS continues to be in a league of its own with a worldwide market share of over 31 percent” for the year, said John Dinsdale, Chief Analyst and Research Director at Synergy.
Amazon’s share of the market grew 63 percent last quarter, year-over-year, but Microsoft and its sprawling cloud portfolio are growing faster.
Microsoft’s cloud grew a whopping 124 percent last quarter, compared to the same year-ago period.
All told, the Redmond, WA software company claimed 9 percent of the cloud infrastructure services market in 2015 for second place.
Meanwhile, a Mountain View, CA rival also made some major progress.
Google notched a 108 percent year-over-year growth rate in Q4 2015. For the full year, Google claimed 4 percent of the market… Read More
PrismTech Joins the OpenFog Consortium to Help IoT
Excerpted from PrismTech Press Announcement
 PrismTech a global leader in software platforms for distributed systems, today announced that it has joined the OpenFog Consortium.
PrismTech a global leader in software platforms for distributed systems, today announced that it has joined the OpenFog Consortium.
The OpenFog Consortium was formed to accelerate the deployment of fog computing technologies through the development of an open architecture that identifies core technologies and capabilities such as distributed computing, networking, and storage.
The OpenFog Consortium was formed by a coalition of leaders in the Internet of Things (IoT) ecosystem including ARM, Cisco, Dell, Intel, Microsoft Corp, and the Princeton University Edge Laboratory.
Fog computing distributes the resources and services of computation, communication, control, and storage closer to devices and systems at or near the users.
The OpenFog non-profit global consortium is driving industry and academic leadership in fog computing architectures with whitepapers, testbeds, and other deliverables that demonstrate best practices for interoperability and composability between cloud and edge architectures.
By utilizing existing standards and proven approaches, the consortium will reduce the time required to deliver end-to-end IoT scenarios… Read More
What’s Next for Object Storage?
Excerpted from CCI Report by Marcus
 After nearly 20 years, you’d expect object storage to be making big waves in the market by now.
After nearly 20 years, you’d expect object storage to be making big waves in the market by now.
But despite its promise of a more efficient, simpler way to store and manage data assets, object storage has hardly made a splash in the storage world to date.
Could 2016 be the year that that’s about to change? Many think so.
One of the major reasons why object storage could finally be on the verge of making a name for itself in the storage market is that it is the driving force for the leader in public cloud storage (Amazon S3).
S3’s huge success is generating greater interest in object storage generally, which is helping to build up customer awareness of what it can do.
Another possible driver for object storage adoption could be OpenStack, the free, open-source software platform for cloud computing that enables solutions to be deployed as infrastructure-as-a-service (IaaS).
OpenStack Object Storage, also known as Swift, is a scalable redundant storage system… Read More
IoT Changing How Media Companies Operate
Excerpted from eMarketer Report
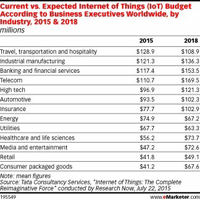 While the Internet of Things (IoT) is still in the early stages of development, the media and entertainment industry already has many of the digital building blocks in place to make it a reality.
While the Internet of Things (IoT) is still in the early stages of development, the media and entertainment industry already has many of the digital building blocks in place to make it a reality.
Large publishers and broadcasters — many of which control the content and its delivery — have switched to digital business models and have the network and IT infrastructure to support high-speed transmission, new formats (e.g., 3-D, 4-D, 4-K ultra HD, high dynamic range, virtual reality) and multichannel delivery, as explored in the new eMarketer report, “The Internet of Media and Entertainment Things: What Marketers Need to Know Now.”
Because a growing percentage of media and entertainment content is consumed on digital and mobile devices, the number of industry-related IoT connections is rising.
In its “State of the Market: The Internet of Things 2015” report, Verizon Communications found that IoT connections on its network in the media and entertainment vertical increased 120% in 2014 compared with 2013.
Other research reveals similar growth potential.
An April 2015 survey of worldwide business executives by Tata Consultancy Services (TCS) produced interesting results… Read More
Nokia’s IoT Security Tool Takes in the Whole Network
Excerpted from CIO Report by Stephen Lawson
 Nokia is taking the principle of “united we stand” to the Internet of Things with a platform that can harness systems from multiple vendors for network-wide security.
Nokia is taking the principle of “united we stand” to the Internet of Things with a platform that can harness systems from multiple vendors for network-wide security.
The company’s NetGuard Security Management Center is designed to monitor and control all the security components on a network. This will help carriers and other IoT service providers take a more holistic approach to preventing and responding to attacks.
Nokia will sell it to users of any brand of network. The company, once heavily invested in handsets, is now overwhelmingly a mobile infrastructure maker and is in the process of taking over network equipment vendor Alcatel-Lucent. NetGuard is a security product, mostly software, that’s separate from Nokia’s underlying infrastructure offering. It will be demonstrated at Mobile World Congress in Barcelona this month and is expected to ship later this year.
Concern about security is one of the biggest hurdles to IoT deployments. The prospect of having thousands of connected devices spread around factories, hospitals or highways makes some IT administrators worry about attacks that could spread throughout a network.
Nokia says a system that looks at the whole network brings greater security than point products… Read More
The 100 Coolest Cloud Computing Vendors of 2016
 In a few short years “the cloud” has gone from industry buzzword to a term thrown around in everyday conversation. While cloud computing may not be understood by the majority of laymen, it’s certainly not a mystery to tech professionals, particularly in the channel, where moving beyond traditional on-premise technology deployments to cloud-based models is becoming the new norm.
In a few short years “the cloud” has gone from industry buzzword to a term thrown around in everyday conversation. While cloud computing may not be understood by the majority of laymen, it’s certainly not a mystery to tech professionals, particularly in the channel, where moving beyond traditional on-premise technology deployments to cloud-based models is becoming the new norm.
With popularity comes crowds, and in the era of mainstream cloud computing you would be hard-pressed to find a vendor that doesn’t have some form of cloud offering. For solution providers, finding the ideal vendor partner in such a saturated space can be difficult.
So where to begin your search?
For the sixth straight year, CRN presents the 100 Coolest Cloud Computing Vendors, the channel’s best resource for narrowing down key vendors to partner with.
The list is broken up into five segments: Platform and Development, Software, Security, Storage and Infrastructure.
Many of the staples from the first Cloud 100 list released in 2010 are thriving and find themselves once again on this year’s list… Read More
Coming Events of Interest
Industry of Things World USA — February 25th-26th in San Diego, CA. A new international information exchange forum featuring four concurrent tracks covering business model generation, technology and infrastructure, data management, and security.
IoT Asia 2016 — March 30th-31st in Singapore. IoT Asia returns in 2016 with fresh insights on Internet of Things (IoT) developments around the world. The 3rd edition aims to further advance conversations and ideas on IoT and how it will impact our lives by delving into the real issues.
Delivery of Things World — April 25th-26th in Berlin, Germany. DevOps specialists, continuous development strategists, architect newbies, development geeks, and cloud geniuses from across the spectrum of DevOps transformation come together at this stimulating and innovative event.
DataCloud Europe 2016 — June 8th-9th in Monte Carlo, Monaco. The 2016 conference will focus on cloud computing advances and changes in data management, with a stellar line-up of speakers including global infrastructure leaders and subject matter experts.
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
