In This Issue
- Court Upholds Rules
- Title II Draws Jeers
- Non-Discriminatory?
- Report from the CEO
- Groups File Complaint
- Cable Industry Lobby
- Sharing Law Applies
- Cybersecurity Caucus
- Asia Defenses Tighten
- Big Data Net Security
- NetApp Protects Data
- Telefonica & Fortinet
- Firm and Consultant
- NetApp Flash Storage
- IARPA Ask: Deception
- Taking the Grid Offline
- Coming DCIA Events
Court Upholds Obama-Backed Net Neutrality Rules
Excerpted from Politico Report by Alex Byers

A federal appeals court Tuesday upheld a White House-supported effort to make internet service providers (ISPs) treat all web traffic equally, delivering a major defeat to cable and telephone companies.
The DC Circuit Court of Appeals, in a 2-1 vote, affirmed the FCC’s latest net neutrality rules, which consumer groups and President Barack Obama have backed as essential to prevent broadband providers from blocking or degrading internet traffic.
The telecom industry and Republicans have heavily criticized the rules as burdensome and unnecessary regulation, with Texas Senator Ted Cruz once labeling it “Obamacare for the Internet.”
AT&T immediately announced it would appeal the ruling, saying it’s always expected the issue to be decided by the Supreme Court.
Several industry trade groups are expected to join the effort.
The court decision marks a victory for FCC Chairman Tom Wheeler, who led the agency’s Democratic majority in approving the rules in February 2015 over the objections of the agency’s two GOP Commissioners… Read More
Title II Decision Draws Jeers from ISPs & GOP
Excerpted from Broadcasting & Cable Report by John Eggerton

ISPs and other opponents of the FCC‘s Title II-based Open Internet order were regrouping Tuesday after a court defeat that will be appealed to the Supreme Court but in the meantime were making their unhappiness known.
A three-judge panel of the US Court of Appeals for the District of Columbia rejected all the ISP challenges to the rules, including the reclassification of ISPs as common carriers and the application of the rules to interconnection and mobile wireless operators.
It was essentially a sweep for the Commission and the Obama Administration, which strongly backed the rules.
But the long legal road for net neutrality rules is not over.
AT&T has already pledged to take it to court – it has 90 days to appeal – and others will almost surely be joining them.
“I am deeply disappointed by the DC Circuit’s 2-1 decision upholding the FCC’s Internet regulations,” said FCC Commissioner Ajit Pai, who voted against the rules.
“For many of the reasons set forth in Judge Stephen Williams’ compelling dissent, I continue to believe that these regulations are unlawful… Read More
“Non-Discriminatory” Broadband: Miscarriage?
Excerpted from Report by CircleID Report by Martin Geddes

The foundational idea behind “net neutrality” is one of fairness by constraining ISP power over network mechanisms.
The theory is this: if there is “non-discriminatory” local traffic management, then you have “fair” global outcomes to both users and application providers.
There are thousands of pages of academic books making this assumption, and it is the basis of recent EU telecoms law.
This is a false application of a common carriage metaphor to a stochastic distributed computing system.
The regulatory result is technically incompetent and practically unenforceable.
The core problem is one of showing intentionality for a “best effort” service whose performance is undefined.
Is an ISP deliberately “throttling” the service to a particular application? Hard to tell when the service can legitimately do anything anyway! Flukes and faults look identical.
Let’s just assume for a moment that this “throttling” concept is technically meaningful (it’s not), and unpack what this would imply… Read More
Report from DCIA CEO Marty Lafferty
 The DCIA is going on the record to oppose an expansion of the National Security Letter (NSL) statute.
The DCIA is going on the record to oppose an expansion of the National Security Letter (NSL) statute.
We object to recently added language in the Senate Intelligence Authorization Act for Fiscal Year 2017.
We dispute the similarly worded amendment filed by Senator John Cornyn (R-TX) to the reform bill for the Electronic Communications Privacy Act (ECPA).
We disagree with any version of these bills that would increase the government’s ability to access private data without a court order.
This proposed expansion of the NSL statute has been characterized by some government officials as merely fixing a “typo” in the law.
In reality, though, it would drastically amplify the ability of federal agencies to gather sensitive information about users’ online activities without court oversight.
These provisions would expand a category of data, known as Electronic Communication Transactional Records (ECTRs), that the FBI, for example, could obtain using administrative subpoenas, which do not require probable cause.
These records include a host of online information, such as IP addresses, routing and transmission files, session data, and more.
The new categories of information that could be collected using an NSL- without any oversight from a judge – would paint an incredibly intimate picture of an individual’s life.
For example, a person’s browsing history, email metadata, physical location, and exact date and time he or she signed in or out of a particular online account.
This information could reveal details about a person’s political affiliation, medical condition, religious preference, sexual orientation, and even his or her movements throughout the day.
Our concern is compounded by a history of government abuse.
In the past decade, the FBI has issued over 300,000 NSLs, illegally exploiting them in the bulk collection of tens of thousands of records to obtain data not permitted under the statute, using the information to gain access to cases not relevant to authorized investigations, and storing the collected material indefinitely.
Given the sensitive nature of information that could be swept up under the proposed expansion, and the documented past abuses of the existing NSL statute, we urge the Senate to remove these provisions from the Intelligence Authorization Act and the ECPA reform bill. Share wisely, and take care.
Groups File FCC Complaint over MVPD Set-Top Privacy
Excerpted from Multichannel News Report by John Eggerton
 Public Knowledge, the Center for Digital Democracy and Consumer Watchdog have petitioned the FCC to enforce cable set-top privacy rules against Comcast, AT&T, and Cablevision in particular, and the industry more generally, and argue that means mandating an opt-in regime for use of set-top data for marketing purposes.
Public Knowledge, the Center for Digital Democracy and Consumer Watchdog have petitioned the FCC to enforce cable set-top privacy rules against Comcast, AT&T, and Cablevision in particular, and the industry more generally, and argue that means mandating an opt-in regime for use of set-top data for marketing purposes.
That comes in a complaint being filed today with the Commission, according to a copy provided to Multichannel News.
While the FCC is currently deciding how to apply its multichannel video programming distributor (MVPD) privacy rules to broadband – including proposing an opt-in regime for some uses – the groups are suggesting it also needs to apply those rules better to cable ops already under privacy regs.
They argue that MVPDs are using consumer data for advertising purposes without properly obtaining consumer consent or letting customers know the extent of that information collection.
“The Commission should enforce the relevant privacy provisions to ensure that cable operators only use subscriber information when they have the consent required by law,” they said.
They say that cable operators – they include AT&T and its U-verse video service in that category – collect and share customer data… Read More
Cable Industry Lobbies to Block FCC Moves
Excerpted from NY Times Report by Cecilia Kangjune

In recent weeks, staff members for Bobby Rush, a Democratic Congressman from Illinois, have asked fellow lawmakers to sign a letter opposing a Federal Communications Commission proposal to limit how broadband providers can share users’ personal data.
Last month, 60 lawmakers signed a separate letter voicing their objections to an FCC regulation that would open the market for cable television set-top boxes (STBs).
What the actions have in common: the financial connections and legwork of cable companies like Comcast.
The National Cable & Telecommunications Association (NCTA), an industry lobbying group, said it had edited the letter shared by Mr. Rush’s staff.
Cable industry lobbyists also helped gather the 60 signatures on the STB letter; nearly all of the lawmakers who signed count cable and telecom companies as top campaign donors, according to federal disclosures.
The behind-the-scenes activity by cable companies and their industry groups is part of the biggest lobbying push by the $115 billion industry… Read More
Info-Sharing Law Applies to Industry
Excerpted from The Hill Report by Joe Uchill

The Departments of Homeland Security and Justice say that recent legislation lets businesses share cyber-threat information with industry interests as well as government.
The agencies released a document Tuesday night clarifying the Cybersecurity Information Sharing Act (CISA).
The measure, which passed in the 2015 omnibus, was designed to allow companies to share threat information with the federal government and other industry members while limiting potential civil liabilities for doing so.
But since its passage, business have questioned whether the wording of the bill limited the information-sharing to just government.
Even before the document was released, the business world expected that they were meant to share information with each other.
“We anticipate that the Departments will accommodate the Chamber’s request to clarifying the protections afforded to a non-federal entity when it shares cyber-threat information with another non-federal entity,” Matthew Eggers wrote… Read More
Senators Establish Cybersecurity Caucus
Excerpted from The Hill Report by Katie Bo Williams

Two US Senators on Tuesday announced the creation of a Cybersecurity Caucus to keep lawmakers and staffers up-to-date on cyber policy.
The caucus, from Senators Mark Warner (D-VA) and Cory Gardner (R-CO), will focus on the issue’s impact on national security, the economy and digital security.
“Rifle shots targeting a massive, growing problem have fallen well-short of sufficient. We need a grand strategy to combat positively identified bad actors, and that requires a broad policy response that is adaptable to technological developments and the ever-changing cyber field,” Gardner said.
Cyber-attacks account for up to $120 billion in economic and intellectual property loss annually and cost the average US firm more than $15 million per year, the lawmakers note.
But Congress has struggled to get its arms around the issue, which touches almost every sector of government and private industry. Some issues – such as encryption – have become the object of jurisdictional wrangling amongst multiple committees who see the issue as their bailiwick… Read More
Regulators Tighten Cyber Defenses in Asia
Excerpted from Wall St. Journal Report by Anjie Zheng
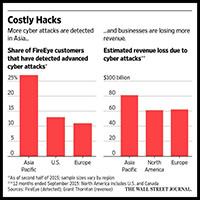
When the names and birth dates of more than 11 million children and adults were leaked from its online learning database last November, toy maker VTech Holdings didn’t discover the breach until a reporter emailed the company nine days later.
Company executives said VTech took four more days after being notified before it asked users to change their passwords – and another 16 days before it issued a public statement about the breach.
“It really took us some time to dig deep to find out if there was anything irregular going on,” VTech Chairman Allan Wong said.
VTech’s incident highlights how a company can be blindsided by a cyber-attack, and the risks involved when companies collect and store the personal information of millions of users online.
Losses from such incidents are particularly steep in Asia because regulations on cybersecurity and disclosure lag those in the West, say cybersecurity experts.
“People think hacking only happens in the West and that Asia is a safe haven,” said Kok Tin Gan, Risk Assurance Partner at consultancy PricewaterhouseCoopers in Hong Kong… Read More
Big Data Will Fix Internet Security… Eventually
Excerpted from InfoWorld Report by Roger Grimes

I’ve long written that only a large-scale improvement of the internet’s authentication mechanisms (that is, pervasive identity) could significantly reduce crime.
If everyone on the internet had a default, assured identity, attackers would have a much harder time committing and getting away with cyber-crimes.
We’ve seen some progress over the years, such as two-factor authentication and better access controls.
The days are numbered for simple log-on names and passwords.
And though it takes time for defensive controls, warrants, and legal evidence to be collected, efforts on the part of law enforcement are resulting in a greater number of successful prosecutions.
Still, I’m disappointed that pervasive anonymity and weak authentication remain the norm. At the moment, internet crime seems to be at its zenith – and much of society has accepted today’s sad state of affairs as inescapable.
They think we can’t do any better. Nothing could be further from the truth. As the internet matures, legitimate uses will prevail… Read More
NetApp Strengthens Data Protection in Hybrid Cloud
Excerpted from Broadway World Report

“Working with our clients to plan and schedule a migration and pointing their systems to the new data all this has to be done in a very short period of time. In healthcare and, specifically, hospitals, there is no downtime,” said Jim Avazpour, Director, I&O Platforms, Cerner.
“With NetApp OnCommand Insight we have the ability to proactively triage and address an incident quickly without downtime and can confidently migrate our clients’ data in real time during business hours.”
NetApp today announced enhancements to its data protection software, including NetApp OnCommand Insight.
The company also introduced NetApp Data Protection Solutions for Microsoft Office 365 to help customers reduce the risk of data loss while enabling business continuity with the right mix of cloud resources.
“The data protection and recovery software market continues to show solid growth.”
“The advancement of virtual computing and cloud computing and the need for rapid data recovery are forcing IT organizations to continuously augment their data protection strategies,” said Phil Goodwin, Research Director, IDC Storage Group… Read More
Telefonica & Fortinet Managed Security Services
Excerpted from MarketWired Report

Telefonica, one of the world’s leading providers of communications services and solutions, and Fortinet, a global leader in high-performance cyber security solutions, today announced a strategic alliance agreement that will add Fortinet’s Security Fabric architecture into Telefonica’s portfolio of managed security services.
The agreement underscores Fortinet as a strategic security infrastructure partner to deliver solutions integrated with some of Telefonica’s key managed security services, which include, the CleanPipes service, ElevenPath’s FAAST persistent pen-testing and virtual patching solution, and ElevenPath’s Metashield Protector service.
Fortinet is the security infrastructure provider used for all Telefonica’s CleanPipes deployments worldwide today and will continue to be a part of the evolution of the service architecture.
Telefonica customers will benefit from the combination of Telefonica’s strategic security services and Fortinet’s Security Fabric, which delivers pervasive and adaptive cybersecurity from Internet of Things (IoT) to the cloud.
Increasing awareness of the cybersecurity risks facing businesses, a security talent challenge, and growing compliance enforcement are prompting businesses of all sizes to migrate risk out of their IT departments and into the hands of professionals… Read More
Cybersecurity Firm & Consulting Giant Framework
Excerpted from Health IT Report by Bill Siwicki

Most healthcare executives and board members are quite aware of the importance of cybersecurity, but many may feel poorly prepared when it comes to managing risks because of the numerous technical and non-technical aspects of this complex issue.
To help executives better prepare their organizations for modern cybersecurity threats, Palo Alto Networks, a global cybersecurity vendor, and PwC, a consulting firm giant, have released “Security Framework: A Guide for Business Leaders.”
The goal is to provide executives with a practical framework for addressing the people, process and technology elements of the cybersecurity challenge, the two firms said.
“Although information technology has created a new digital age, transforming every aspect of modern life and bringing with it greatly enhanced productivity gains and standards of living, its underlying infrastructure is inherently vulnerable to exploitation,” the report notes.
“This leaves society open to fundamental cybersecurity risks. Businesses globally constantly face an onslaught of malicious activity… Read More
NetApp Flash Storage Selected By Globe Telecom
Excerpted from Host Review Report
 NetApp SolidFire, the leader in all-flash storage systems built for the next generation data center, today announced that Globe Telecom, a leading full-service telecommunications company in the Philippines, through its Globe Business group, has deployed NetApp SolidFire’s all-flash scale-out storage platform to support its Virtual Private Cloud and Dedicated Private Cloud offerings.
NetApp SolidFire, the leader in all-flash storage systems built for the next generation data center, today announced that Globe Telecom, a leading full-service telecommunications company in the Philippines, through its Globe Business group, has deployed NetApp SolidFire’s all-flash scale-out storage platform to support its Virtual Private Cloud and Dedicated Private Cloud offerings.
With NetApp SolidFire’s automated, scalable infrastructure that guarantees performance, Globe Business’ internal and external customers can meet their storage capacity and performance needs today and in the future at a cost two to three times lower than before.
Globe Business provides an entire suite of products and services for mobile, fixed, broadband, data connections, internet and managed services.
With its own network of data centers around the country, Globe Business prides itself on continuously improving value-added services for its customers.
In order to accelerate its cloud offerings and give it an even better competitive edge, Globe Business turned to NetApp SolidFire… Read More
IARPA Wants Cybersecurity Software for ‘Deception’
Excerpted from FedScoop Report by Chris Bing
 In warfare – both physical and cyber-based – the act of deception can be at times more useful than an outright attack.
In warfare – both physical and cyber-based – the act of deception can be at times more useful than an outright attack.
Or at least that’s what the Intelligence Advanced Research Projects Activity is thinking, based on a call that its contracting officers put out this week.
IARPA may soon be in the market for a piece of cybersecurity technology that uses “denial and deception,” or D&D, to protect federal data assets, according to a recent request for information.
This technology is expected to confuse and otherwise deceive a would-be hacker before a breach can occur.
The RFI published by the agency earlier this week titled “Deception for Cyber Defense Research” notes that while this nascent technology is available in the private sector it requires additional research to become effective at scale.
Responses to the RFI are due on July 1st.
“Adapting D&D to support the engagement of cyber adversaries is a concept that has been gaining momentum, although, the current state of research and practice is still immature: many techniques lack rigorous experimental measures of effectiveness… Read More
Prevent Blackout by Taking Power Grid Offline
Excerpted from ForeignPolicy Report by Elias Groll

With hackers attacking electrical grids, banks, and a growing list of other targets, some policymakers and security researchers are calling for turning the clock back to an earlier era when devices weren’t connected to the internet – or vulnerable to digital attack.
The American power grid is more efficient than ever before because electricity plants, transformers, and other key pieces of infrastructure are networked together, allowing for electricity to be redirected in real time from areas with too much to those needing more.
The problem is that those gains have also left the overall system open to attack.
Power stations and grids run by network-connected computer control systems can be hacked to cause widespread power outages.
American intelligence officials have long warned that the US grid would represent a ripe target in a time of war, and US adversaries are heavily investing in the capabilities to take it down.
In Ukraine, hackers attacked a portion of the country’s grid over Christmas and succeeded in knocking out power for thousands of customers… Read More
Coming Events of Interest
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
2016 Creative Storage Conference — June 23rd in Culver City, CA. The tenth annual CS will bring together digital storage providers, equipment manufacturers, software distributors, and professional media and entertainment end-users to explore the conference theme “The Art of Storage.”
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Mobile World Congress Shanghai — June 29th – July 1st in Shanghai, China. MWC Shanghai is a very unique gathering that brings together industry participants ranging from C-Level mobile executives to end-user consumers passionate about mobile.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
