In This Issue
- Touhill First Fed CISO
- Verizon’s IoT LED Add
- Apply Fog to the IoT?
- Report from the CEO
- Regs: Cybersecurity
- NetApp Storage Boom
- Ensuring File Security
- Telefonica’s LA Cloud
- Privacy vs Security
- DoJ IoT Devices Study
- Huawei Enters Cloud
- Serverless Technology
- IoT Analytics to Edge
- DHS Chf on Vote Hack
- FTC vs Ransomware
- EU Unifies Digital Mkt
- Coming DCIA Events
Gregory Touhill Named First Federal CISO
Excerpted from GovInfoSecurity Report by Eric Chabrow
 President Obama has named Gregory Touhill, a retired Air Force brigadier general, as the US federal government’s first Chief Information Security Officer (CISO) .
President Obama has named Gregory Touhill, a retired Air Force brigadier general, as the US federal government’s first Chief Information Security Officer (CISO) .
A September 8th White House blog announced the appointment of Touhill, who now serves as Deputy Assistant Secretary for Cybersecurity and Communications in the Department of Homeland Security (DHS).
In his new role, Touhill will report to federal CIO Tony Scott, who’s based in the White House Office of Management and Budget (OMB).
Grant Schneider, Director for Cybersecurity in the White House National Security Council, was named acting deputy CISO.
In February, Obama created the federal CISO post as part of a multifaceted initiative known as the Cybersecurity National Action Plan that’s aimed at strengthening the nation’s IT security.
Scott and White House Cybersecurity Coordinator Michael Daniel, in the blog, say Touhill will leverage his considerable experience in managing a range of complex and diverse technical solutions with his strong knowledge of civilian and military best practices… Read More
Verizon Adds LED Lighting to IoT Portfolio
Excerpted from Electronics360 Report by Peter Brown
 Mobile carrier Verizon Communications has signed an agreement to purchase light-emitting diode (LED) luminaire start-up company Sensity Systems.
Mobile carrier Verizon Communications has signed an agreement to purchase light-emitting diode (LED) luminaire start-up company Sensity Systems.
The deal will see Sensity’s LED lighting conversion products added to Verizon’s ThingSpace Internet of Things (IoT) platform in order to continue Verizon’s push into the smart city.
Terms of the deal were not disclosed.
With the acquisition of Sensity, Verizon says it will accelerate the deployment of large-scale implementations for the digital transformation of cities, universities and venues.
The company’s ThingSpace platform allows communities to increase economic development, drive citizen engagement and enable sustainability.
“Rapid urbanization is putting a huge strain on city services globally, coupled with inefficiencies caused by an aging infrastructure that currently supports critical functions, such as fire and emergency services, public transportation, lighting… Read More
Is Now the Time to Apply Fog to the IoT?
Excerpted from IoT Evolution Report by Vladimir Krylov
 Fog computing, a term originally introduced by Cisco, at first seemed like the exotic idea of a company that was in constant search of new product applications.
Fog computing, a term originally introduced by Cisco, at first seemed like the exotic idea of a company that was in constant search of new product applications.
But the term has become the basis for network solutions, including in IoT.
The main idea of fog computing architecture is to distribute data processing and operation procedures over various devices that are connected via the Internet to the cloud (i.e. a virtualized computing environment), as well as to many other devices located in the network.
One of the key features of fog computing is a vertical distribution of functions by layers that extend from sensors, then in the fog, and, finally, in the cloud depending on the processing latency.
This architecture implements high-latency (days to months) enterprise operations in the cloud, whereas technical operations with low latency (milliseconds to hours), starting from high speed to transactional analytics, are realized in fog nodes.
Patterns and rules for machine learning algorithms are formed in the cloud, then they move to the fog for quick implementation… Read More
Report from DCIA CEO Marty Lafferty
 Plan now to join us this December here in Washington, DC at the Government Video Expo (GVE) 2016 and the National Drone Show (NDS), the next co-located events in the DCIA’s expanded partnership with NewBay Media.
Plan now to join us this December here in Washington, DC at the Government Video Expo (GVE) 2016 and the National Drone Show (NDS), the next co-located events in the DCIA’s expanded partnership with NewBay Media.
NewBay Media connects and informs millions of constituents in the world’s most dynamic industries through its award-winning content, integrated media capabilities, and high-profile network-building informative events.
NewBay’s brands include Broadcasting & Cable, Multichannel News, TV Technology, Music Week – more than 60 print and digital publications in all, and over 100 integrated web and mobile applications, conferences and conventions, custom marketing services, and e-commerce capabilities.
GVE 2016 & NDS offer attendees three days of education, conversation, engaging keynotes, and an exhibit floor filled with the latest technologies.
Both events take place December 6th through 8th at the Walter E. Washington Convention Center.
Designed for video, broadcast, and AV professionals, GVE 2016 & NDS feature a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions and networking opportunities, as well as a range of educational sessions and workshops.
Highlights this year include Keynotes from industry experts including Robert G. Kennedy, President & Co-CEO of C-SPAN, and Timothy E. Herlocker, Director of the Emergency Operations Center of the Fire Department of New York City, The D.C. Post|Production Conference, an event that offers three days with three tracks of educational sessions, The Government Learning Technology Symposium, Intensive Production Workshops, and the Advanced UAV Workshop for drone pilots and producers.
For more information and to register, click here. We look forward to seeing you there! Share wisely, and take care.
For Regulators, Cybersecurity Must Be More
Excerpted from The Hill Report by Jacob Olcott
 Hardly a week goes by without a headline-grabbing cyberattack on a bank, retailer, health insurer, government agency, or political campaign.
Hardly a week goes by without a headline-grabbing cyberattack on a bank, retailer, health insurer, government agency, or political campaign.
The hacking surge has cast a harsh light on America’s cybersecurity preparedness and forced the public and private sectors to respond to a growing and evolving threat.
As organizations enhance their own defenses, federal regulators in critical industries such as financial services, healthcare and energy are also becoming more involved, examining companies’ security infrastructure and policies and enforcing cybersecurity readiness.
But are these regulatory efforts working? What more should regulators be doing?
There has been a flurry of regulatory activity in recent months, including some great personnel moves.
In June, the Securities and Exchange Commission (SEC) announced the appointment of Christopher Hetner, the former cybersecurity chief at Ernst & Young and GE Capital, as senior adviser on cybersecurity to SEC Chair Mary Jo White… Read More
This Area of Storage Is Booming for NetApp
Excerpted from Market Realist Report by Adam Rogers
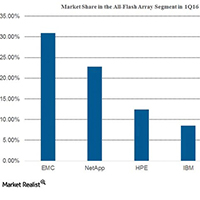 NetApp has repeatedly stated that flash storage plays an important role in the IT (information technology) transformation of businesses.
NetApp has repeatedly stated that flash storage plays an important role in the IT (information technology) transformation of businesses.
The adoption of flash storage has increased during the past few quarters as companies look to gain competitive advantages over peers through greater speeds on key business applications.
What this means is that hard disk installations are being replaced by flash, thereby making flash the primary option for on-premise deployments.
This transition from hard disk to flash is extremely important because enterprise data management and data protection capabilities are essential to customers.
NetApp has stated that it is “uniquely positioned to enable customers to consolidate on to flash and create All-Flash data centers.”
According to IDC’s Worldwide Quarterly Enterprise Storage Systems Tracker, NetApp is growing faster than the overall all-flash array market… Read More
Best Practices for Ensuring File Security
Excerpted from Accounting Today Report by Scott Gordon
 It’s no secret that professional services firms house troves of hack-worthy data.
It’s no secret that professional services firms house troves of hack-worthy data.
Accountants, lawyers, consultants, recruiters, media, creative, IT, and other service providers routinely access and share sensitive information to meet client needs-making them prime targets for cybercriminals and the ideal potential victims for data mishandling.
In June, insurance giant State Farm had 70,000 email addresses belonging to company personnel and independent contractors compromised when collaboration with a trusted professional services marketing partner, DAC Group, went awry due to a server breach.
But you don’t have to be a large, national firm for cybercriminals to take an interest.
In May, two California-based accountants experienced unauthorized access to their work computers.
Lynn N. Talbott, Jr., CPA disclosed that her firm’s breach compromised customer names, genders, dates of birth, telephone numbers, addresses, Social Security numbers, W-2 information and direct deposit bank account information… Read More
Telefonica Strengthens Cloud in Latin America
Excerpted from Telefonica Press Announcement
 Telefonica Business Solutions, leading provider of a wide range of integrated communication solutions for the B2B market, has signed a global contract with acens, a Cloud service Company part of Telefonica, to commercialize acens’ software-as-a-service (SaaS) products in Latin America.
Telefonica Business Solutions, leading provider of a wide range of integrated communication solutions for the B2B market, has signed a global contract with acens, a Cloud service Company part of Telefonica, to commercialize acens’ software-as-a-service (SaaS) products in Latin America.
With this agreement, Telefonica reinforces, enlarges and internationalizes its Cloud portfolio and brings best-in-class cloud services to its enterprise customers.
Cloud products such as Website Creation Tool, E-Shop, Domain Name Registration or Cloud Mail, among others, are services that enable Telefonica’s Small & Medium Enterprise (SME) customers to move their traditional business to the internet and help them with the digital transformation of their business in an effective manner.
These SaaS products have been designed with simplicity and cost efficiency in mind and will bring to Telefonica’s customers substantial benefits such as the avoidance of expensive product development, high technical flexibility and service scalability, quick time to market, no investment in own IT infrastructure as well as pay-per-use service.
Internet presence and marketing tools are expected to grow significantly in the coming years… Read More
Digital Privacy vs Public Security
Excerpted from Inquirer Report by Drexx Laggui
 WIKIMAPIA or Google Maps can give criminals the ability to assess escape routes or vulnerabilities of bank branches or homes of kidnap victims, while Facebook or Instagram or Twitter can yield great information about the lifestyle patterns, family, and friends, or the financial capacity of the victims.
WIKIMAPIA or Google Maps can give criminals the ability to assess escape routes or vulnerabilities of bank branches or homes of kidnap victims, while Facebook or Instagram or Twitter can yield great information about the lifestyle patterns, family, and friends, or the financial capacity of the victims.
The #WarOnDrugs has reached a crescendo now that President Duterte has issued Proclamation No. 55 declaring a state of national emergency on account of lawless violence.
According to open-source reports, elements of the illegal drug trade have stepped up their battle against the government by establishing a partnership with terrorists and kidnap-for-ransom organizations in their efforts to distract or discourage law enforcers from doing their jobs.
The bombing of a Davao City night market on Sept. 2 is a heinous sample of their criminal synergy. The #WarOnDrugs is not easy. The numbers are not in favor of our government.
The 2015 Annual Report of the Philippine National Police revealed a volume of 201,010 for index crime, and 474,803 for nonindex crime, for a total of 675,813 reported crimes to the police alone… Read More
DoJ Studies Security Threats of Net-Linked Devices
Excerpted from Reuters Report by Dustin Volz
 The US Justice Department has formed a threat analysis team to study potential national security challenges posed by self-driving cars, medical devices, and other Internet-connected tools, a senior official said.
The US Justice Department has formed a threat analysis team to study potential national security challenges posed by self-driving cars, medical devices, and other Internet-connected tools, a senior official said.
The new group’s goal is to secure the so-called “Internet of Things (IoT)” from exploitation by “terrorist threats” and by others who might try to hack devices to cause loss of life or achieve political or economic gain, according to Assistant Attorney General John Carlin, head of the Justice Department’s national security division.
The impetus for the team, which has been informally active for about six months, was an understanding that the internet is vulnerable to cyberattacks partly because it was not designed with security in mind, Carlin told Reuters, after announcing the group on Thursday at the Intelligence and National Security Alliance conference in Washington, DC.
Carlin said the group, a small team of about five-to-ten people, did “not want to be alarmist” about new technologies such as self-driving cars, but that it wanted to identify and address security challenges presented by the internet of things before they are exploited.
He cited the July truck attack in Nice, France as an example of how automated driving systems could present a national security threat… Read More
Huawei Enters Cloud Computing Space
Excerpted from Investopedia Report by Shoshanna Delventhal
 China’s leading technology firm, Huawei Technologies, recently announced plans to beef up its efforts to compete against Western rivals in the data-storage market.
China’s leading technology firm, Huawei Technologies, recently announced plans to beef up its efforts to compete against Western rivals in the data-storage market.
Huawei already holds a place at the top three of the world’s largest telecom-networking gear and smartphone makers.
The company now sees its next stage of growth in cloud computing, an industry largely dominated by Western companies.
Huawei’s Deputy Chairman Guo Ping said in an interview that the company will spend $1 billion or more on research-and-development (R&D) to focus on equipment and operating systems for data centers, reports The Wall Street Journal.
While the Shenzhen-based company’s telecom equipment is effectively banned in the United States due to security concerns, it is likely to expand into Europe, Russia, and Africa, regions where Huawei’s wireless networks are already in use.
The company seeks to grow the amount of its total revenue generated outside of China, now standing at 60%.
Due to heightened cybersecurity concerns, a growing number of companies are building exclusive cloud platforms.
Huawei now seeks to join Western competitors in expanding into the space by supplying equipment and software for private data centers… Read More
Serverless Technologies: The Future of Cloud
Excerpted from Computing Report by Peter Sbarski

There’s a new term that’s stirring up interest and passion in the IT community.
Funnily enough, it might herald the future of cloud computing, at least going by the amount of attention that major cloud vendors — Amazon, Microsoft, Google and IBM — are giving it.
“Serverless” is the term that’s causing ruckus but the awareness and understanding of serverless technologies and architectures is growing day by day.
Serverless technologies are managed services that developers can use to build systems.
These services can execute code, store data, or perform other useful operations such as authentication.
A common thread among these services is that the developer doesn’t have access to the underlying infrastructure.
There’s no way to change hardware or update the operating system.
Everything is managed and looked after by a vendor such as Amazon or Microsoft… Read More
IoT Pushes Analytics Closer to the Edge
Excerpted from CIO Report by Stephen Lawson
 As the internet of things (IoT) starts to generate data from far-flung sensors and automate remote equipment, it doesn’t always make sense to house all the intelligence for these systems in data centers.
As the internet of things (IoT) starts to generate data from far-flung sensors and automate remote equipment, it doesn’t always make sense to house all the intelligence for these systems in data centers.
The alternative is edge computing, where smaller systems located on site in factories or other facilities can make sense of IoT data and act on it.
Edge computing components like gateways can shorten response times or just filter out sensor readings that don’t matter so they won’t burden the network.
But how to build edge computing systems and write their software, like so much else in IoT, is still a work in progress.
The constraints on things like size and power are unique to this new field.
On Tuesday, Silicon Valley startup FogHorn Systems introduced the Lightning software platform, which is designed to bring real-time analytics and machine learning down to edge devices, including IoT gateways and even very low-powered processing components built into industrial products… Read More
DHS Chief: ‘Very Difficult’ for Hackers to Skew Vote
Excerpted from The Hill Report by Julian Hattern
 Department of Homeland Security (DHS) Secretary Jeh Johnson on Thursday downplayed concerns about malicious hackers influencing US elections amid rising fears about foreign actors trying to wreak havoc on Election Day.
Department of Homeland Security (DHS) Secretary Jeh Johnson on Thursday downplayed concerns about malicious hackers influencing US elections amid rising fears about foreign actors trying to wreak havoc on Election Day.
While hackers in the US or abroad might be able to steal data from individual election officials, Johnson said at an event hosted by The Atlantic, they would not be able to skew the overall vote count.
“It would be very difficult through any sort of cyber intrusion to alter the ballot count, simply because it is so decentralized and so vast,” he said, noting the series of state, local, and county systems involved in running elections. “It would be very difficult to alter the count.”
Johnson was responding to new fears about hackers from Russia, in particular, whom intelligence officials are reportedly investigating over suspected efforts to disrupt the election.
The FBI is separately investigating hacks at election sites in Arizona and Illinois, and Russia is believed to be behind this summer’s release of massive data files from the Democratic National Committee.
Despite Johnson’s claims, however, hackers would not necessarily need to alter a particular vote count in order to inject chaos… Read More
FTC Focuses on Combating Ransomware
Excerpted from CIO Report by Kenneth Corbin
 Ransomware, where a hacker commandeers a user’s computer files and threatens to permanently delete them unless an extortion payment is made, is on a sharp uptick and now ranks “among the most troubling cyberthreats,” the head of the Federal Trade Commission (FTC) is warning.
Ransomware, where a hacker commandeers a user’s computer files and threatens to permanently delete them unless an extortion payment is made, is on a sharp uptick and now ranks “among the most troubling cyberthreats,” the head of the Federal Trade Commission (FTC) is warning.
FTC Chair Edith Ramirez addressed the issue at a recent forum that the agency convened to examine the spread of ransomware and explore strategies to combat the crime.
“The spate of ransomware incidents are escalating at an alarming rate,” Ramirez says, citing an estimate from the Department of Justice (DoJ) that incidents of ransomware, now averaging some 4,000 a day, have increased 300 percent in the past year.
“The financial motivation for ransomware attacks suggests that the threat is unlikely to go away any time soon,” she says, warning businesses to step up their own defenses to ensure that they are protecting their users from online scammers.
The agency has already brought dozens of enforcement actions against companies for failing to adopt what it considers reasonable security protections… Read More
EU Rules Look to Unify Digital Market
Excerpted from NY Times Report by Mark Scott
 Google may have to pay publishers for their content. Facebook might, too. WhatsApp could have to follow tougher telecom standards.
Google may have to pay publishers for their content. Facebook might, too. WhatsApp could have to follow tougher telecom standards.
A new set of rules, expected to be unveiled by European Union (EU) officials on Wednesday, is likely to put new pressure on American tech companies.
Europe calls it consumer protection. Silicon Valley calls it protectionism.
In some ways, they are both right.
In a decade of sluggish growth, local lawmakers assert that these proposed changes will bring together the region’s national economies into a so-called single digital market.
The aim? To give the bloc’s roughly 500 million consumers unfettered access to services like movie streaming, online shopping and cloud computing, no matter where they live.
At the same time, the proposals would force some of the world’s largest tech companies to comply with stringent rules… Read More
Coming Events of Interest
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
EuroCloud Forum — October 5th-6th in Bucharest, Romania. The seventh annual EuroCloud Congress will be held for the first time in Romania. With the theme “Creating New Frontiers in European Cloud,” it will be the sector’s largest forum on the future of cloud in Europe.
Internet & Mobile World 2016 — October 5th-6th in Bucharest, Romania. The largest business-to-business (B2B) expo-conference for information technology (IT) and digital solutions in Central & Eastern Europe (CEE).
Security of Things World USA — November 3rd-4th in San Diego, CA. SoTWUSA has been designed to help you find pragmatic solutions to the most common security threats facing the IoT.
Rethink! Cloudonomic Minds — November 21st-22nd in London, England. R!CM will cover how IoT is impacting cloud strategies and how to take advantage of these two key technology trends.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
CES 2017 — January 5th-8th in Las Vegas, NV. More than 3,800 exhibiting companies showcasing innovation across 2.4 million net square feet, representing 24 product categories.
Industry of Things World USA — February 20th-21st in San Diego, CA. Global leaders will gather to focus on monetization of the Internet of Things (IoT) in an industrial setting.
