In This Issue
- Trump Meets with Pai
- Amazon Lightning Rod
- End Near for Cloud?
- Report from the CEO
- Infrastructure’s Face
- CS Startups to Watch
- Expert Shortage Opp
- ML & Human-Centric
- Cyber Defenses Faith
- Managing DC Security
- CL Misunderstandings
- Experts at RSA Advice
- Focus on the “T” in IoT
- Cloud-to-Client Direct
- AWS Glitch Disruptive
- Oscars Flub Evocative
- Coming DCIA Events
Trump Meets with FCC’s Pai
Excerpted from Broadcasting & Cable Report by John Eggerton
 President Donald Trump met with FCC Chairman Ajit Pai Monday afternoon in the Oval Office, according to the White House.
President Donald Trump met with FCC Chairman Ajit Pai Monday afternoon in the Oval Office, according to the White House.
The meeting was confirmed afterwards by an FCC spokesperson.
“Chairman Pai had a warm meeting with President Trump this afternoon, in which they reconnected for the first time since Chairman Pai was elevated to head the FCC,” said the spokesman.
“No proceedings pending at the FCC were discussed.”
It will be a busy week outside of the FCC for the Chairman, who in addition to heading to the White House will be on Capitol Hill Wednesday along with the other Commissioners for a Senate Commerce Committee oversight hearing.
The President, as a candidate, talked about blocking the AT&T-Time Warner deal, but the FCC’s role in that deal will likely be limited to advising the Justice Department since the companies say the deal won’t have to be submitted for a public interest review with the FCC.
Pai has been actively targeting some of former FCC Chairman Tom Wheeler’s signature regulatory moves… Read More
Amazon Typo a Lightning Rod
Excerpted from MIT Technology Review Report by Jamie Condliffe
 If you’re going to put all your data in the cloud, you want it to be a well-built cloud.
If you’re going to put all your data in the cloud, you want it to be a well-built cloud.
This week, Amazon – the world’s largest provider of such infrastructure – showed that construction skills are still lacking.
On Tuesday, large parts of the Internet simply stopped working.
Slack wouldn’t let people communicate with colleagues, Trello wouldn’t let you manage a project, and, sadly, the MIT Technology Review website wouldn’t let you read about emerging technology. There were also complaints about smart-home hardware failing to work properly.
The reason: Amazon’s S3 cloud storage system failed.
Amazon is the world’s largest cloud computing provider, so many services that rely upon it were also unable to function properly.
And this wasn’t just a blip: the problem took at least four hours to fix.
It’s hard to accurately quantify the true cost of such an outage… Read More
End Is Near for Cloud Computing?
Excerpted from TechTarget Report by Joel Shore
 Cloud computing is a long way from being fully mature, but its obsolescence may already be upon us.
Cloud computing is a long way from being fully mature, but its obsolescence may already be upon us.
Is the cloud’s future really up in the air?
As Peter Levine, a partner at venture capital firm Andreessen Horowitz, puts it, “Everything that’s popular in technology always gets replaced by something else,” be it Microsoft Windows, minicomputers exemplified by Digital Equipment Corp., specialized workstations typified by Sun Microsystems, or, yes, even cloud computing.
As Levine explains it, cloud computing, which he views as the centralization of IT workloads into a small number of super-mega-huge datacenters, is an unsustainable, unworkable, slow-to-respond method.
The need for instantaneous information makes the network latency associated with a device-to-datacenter model and the corresponding datacenter-to-device return trip simply too long and therefore unacceptable.
Computing, Levine suggests, will move to a peer mesh of edge devices, migrating away from the centralized cloud model.
Consider smart cars. They need to continually exchange information with each other about immediate, hyperlocal traffic conditions… Read More
Report from DCIA CEO Marty Lafferty
 The DCIA is encouraged by the updated draft of the Trump administration cybersecurity executive order now being reviewed by industry leaders, and we are hopeful that the order will be issued shortly.
The DCIA is encouraged by the updated draft of the Trump administration cybersecurity executive order now being reviewed by industry leaders, and we are hopeful that the order will be issued shortly.
The order is expected to hold federal managers accountable for vulnerabilities in their technology systems and require adoption of the series of cybersecurity best practices developed by the National Institute of Standards and Technology (NIST).
Other portions of the order will likely focus on ensuring cyber protections for critical infrastructure.
The federal government’s long-standing investment in aging, legacy information technology poses significant challenges, however, against nation-state backed sophisticated cyberattacks.
The White House Office of Management and Budget (OMB) acknowledged that re-engineering $80 billion of legacy systems to provide state-of-the-art cybersecurity is going to be very difficult.
But we believe that holding agency heads accountable will help expose the real issues in doing so more quickly and spur the procurement of needed new technologies to secure their systems.
Members of the commission established under former President Obama to examine the federal government’s cybersecurity efforts have also reiterated their call for more cooperation between the public and private sector and more leadership in the White House to spearhead efforts on cybersecurity.
That group’s report laid out sixteen recommendations to streamline and strengthen the federal government’s cybersecurity efforts in December.
The commission also recommended the appointment of an Assistant to the President for Cybersecurity, who would report through the National Security Adviser and coordinate efforts on digital security across agencies, as well as an “all-of-government deterrence” against cyberattacks by coordinating work across agencies and departments.
We encourage the issuance of this important executive order. Share wisely, and take care.
Changing Face of Infrastructure Cybersecurity
Excerpted from NextGov Report by Jake Olcott

On January 31st, President Donald Trump met with cybersecurity experts at the White House to discuss his plans to strengthen the government’s ability to safeguard its computer networks.
Though an expected executive order outlining Trump’s approach has not been signed yet, among the details Trump shared with reporters was that he would require all federal agencies to update their information technology systems and, working with utilities and other private industries, shore up protection of the electrical grid and other critical infrastructure.
In focusing attention on the security of critical infrastructure, Trump is correctly reacting to a growing number of attacks in recent years on energy, water and transportation systems.
From a ransomware attack against San Francisco’s municipal transportation authority to charges that seven men with links to the Iranian government hacked into a small dam in New York, malicious attackers are increasingly expanding beyond traditional targets such as banks, retailers, and government agencies and going after essential infrastructure.
If it aims to take a holistic and leading-edge view of the nation’s cybersecurity posture, the administration would be wise… Read More
Cybersecurity Startups to Watch in 2017
Excerpted from Dark Reading Report by Ericka Chickowski
 In spite of a slowdown in the overall funding activity from venture capital firms in 2016, the cybersecurity market continued to raise money at full steam.
In spite of a slowdown in the overall funding activity from venture capital firms in 2016, the cybersecurity market continued to raise money at full steam.
Last year saw the market break records in terms of funding deals, with Q3 tallying up to be the most active quarter for deals in cybersecurity in the last five years, according to CBInsights.
That influx of money is driving innovation in a number of areas.
Particularly notable market segments targeted by these firms include security for data centers and public cloud infrastructure, security orchestration, and incident response tools, and third-party risk assessment tools.
The following 20 firms are primarily early-to-middle-stage startups, with a few more mature start-ups that have courted growth equity to change course or expand into a particularly hot new market segment.
We believe these firms are worth watching due to several factors.
On the funding front, they either managed to snag $25+ million in funding in 2016, or garnered a notable funding round in the last 3 months… Read More
Trump Can Address Cybersecurity Expert Shortage
Excerpted from The Hill Report by Algirde Pipikaite
 Rudy Giuliani will face many challenges in his new role as cybersecurity advisor to President Trump.
Rudy Giuliani will face many challenges in his new role as cybersecurity advisor to President Trump.
Hopefully, Giuliani will prioritize the introduction of policies that tackle the ever-growing shortage of cybersecurity workers.
According to the ISC 2015 Global Information Security Workforce Study, more than 1.5 million cybersecurity professionals will be needed globally by 2020.
An estimated 500,000 to 1 million cybersecurity jobs remain unfilled in the US.
Companies are having trouble finding the right professional possessing practical cybersecurity defense skills.
The problem is not a lack of talent, but, in part, an education system that withholds cybersecurity training until college.
College education is not for everyone.
Many millennials that are savvy in information technology (IT) are looking for education models that replace enrolling in four-year academic institutions that results in loads of student debt… Read More
Machine Learning & Human-Centric Society
Excerpted from Embedded Design Blog by Anthony Wong
 Imagine being surrounded by technologies, and hardly being aware of them.
Imagine being surrounded by technologies, and hardly being aware of them.
For instance, a person walks into a room and without doing anything, the entire atmosphere is fine-tuned to his or her current mood or expectations.
Measurements are taken, personal data is sensed and recorded, and the room adjusts to integrate with the person’s countenance.
All this occurs without turning a switch or adjusting an appliance-simply walk into the room.
We’re beginning to move in this direction, with recent advances in medical technology, with personal fitness devices, and with smart home systems.
Behind the scenes, as the individual enters the room, the unseen technology helps advance the person’s security, health, comfort, and even creativity by providing a seamless set of adjustments and changes to everything from room temperature to computer access to food preparation… Read More
Executives Have More Faith in Cyber Defenses than Staff
Excerpted from NextGov Report by Joseph Marks

Government and private-sector executives are much more bullish on their companies’ cybersecurity than operators on the front lines, according to a report released today.
Executives are far more likely than operators – the IT and cyber staff – to believe their companies’ cybersecurity strategies have been fully implemented, according to the report from Intel Security and the Center for Strategic and International Studies think tank.
Operators are also five times more likely to believe their organizations lack incentives for cybersecurity professionals to improve their organizations to counter emerging threats, the report found.
“Almost half of operators reported no incentives existing in their organization,” the report said.
“It is possible that incentives, even when they exist, may not actually be known by employees, especially if they are lower down in the organization’s structure.”
There’s also a gap between how executives and operators assess the damage of a cyber breach, the report found… Read More
Managing Security in Distributed Computing
Excerpted from Ericm News Report by Erkuden Rios, Massimiliano Rak, and Samuel Afolaranmi
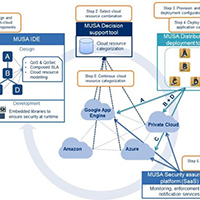
Multi-cloud Secure Applications (MUSA) is an EU H2020 funded research project which is aimed at ensuring security in multi-cloud environments.
The main goal of MUSA is to support the lifecycle of applications with strict security requirements over heterogeneous cloud resources.
MUSA will result in a security framework that includes security-by-design mechanisms as well as runtime security monitoring and enforcement to mitigate security incidents.
Multi-cloud applications rely on the adoption of cloud services of different capability types (i.e., infrastructure, platform or software as a service) from different cloud service providers (CSPs).
Multi-cloud follows the concept of distributed computing in which the components are dispersed but communicate in an integrated manner to achieve the desired goal.
This model offers the opportunity to select the best CSPs that satisfy both application and component level requirements… Read More
Cybersecurity Language Misunderstandings
Excerpted from Dark Reading Report by Blake Moore
 Have you ever traveled to a place where you didn’t speak the local language and attempted to ask for help?
Have you ever traveled to a place where you didn’t speak the local language and attempted to ask for help?
Language is the key to communication and a critical component in effective public-private information sharing in the cyber domain.
Unfortunately – although some international organizations have attempted to document them – there are no common definitions for cyber terms globally across government, business, and academia.
When you throw in industry buzzwords and marketing jargon around cybersecurity, it can become nearly impossible for organizations to speak quickly and efficiently with each other about security.
To fully engage in cross-industry dialogue within the context of cybersecurity, we must speak the same language.
We can’t outmaneuver threats without it.
There are at least 16 different definitions of the term “cyber-attack” globally, all of which span a fairly large spectrum.
Most of them, at least mention something about denying, disrupting, destroying, or degrading information systems… Read More
Experts at RSA Give Cybersecurity Advice
Excerpted from ITWorld Report by Michael Kan
 Come to the RSA show, and you’ll find plenty of cybersecurity technology.
Come to the RSA show, and you’ll find plenty of cybersecurity technology.
The top vendors from across the industry are here, showing products for fighting ransomware, preventing data breaches and more.
But even the best security software is useless if users and businesses aren’t taking the right steps to protect themselves. So we asked experts at the show for their best cybersecurity tips.
Joe Stewart, Director of Malware Research at Dell SecureWorks
He advises everyone to set up two-factor authentication to protect their internet accounts, especially email. It can be particularly useful when stopping hackers who are trying to steal login passwords from users, whether through malware or email phishing schemes.
Even if the hacker manages to loot your passwords, two-factor authentication ensures you’re still protected from all but the most sophisticated attacks: access to your account will require another form of authentication, such as your fingerprint… Read More
Staying Agile by Focusing on the “T” in IoT
Excerpted from Inside Big Data Report by Timothy Butler
 Unlike traditional internet of things (IoT) solutions, edge computing looks to bring the power of the data closer to the asset itself so that decision making is quicker and data is nearer the hands of the right folks who can take the right actions.
Unlike traditional internet of things (IoT) solutions, edge computing looks to bring the power of the data closer to the asset itself so that decision making is quicker and data is nearer the hands of the right folks who can take the right actions.
In practice, it’s called, “Decision making at the point of read.”
In 2017, we will begin to see more of a focus on the benefits of edge computing – and to be more specific – solutions that will address industrial applications, which are the logical, more affordable option for small and medium sized corporations.
This new approach is a deviation from traditional IoT solutions, which uses the cloud to collect streaming telemetry data and send it back to a centralized system for analysis.
These traditional IoT platforms are expensive, can be plagued by complexity, and returns on the investment remain largely unproven. For these reasons focusing on more agile, less expensive, and easier to scale edge solutions will likely gain in popularity and utility.
In order for this new approach to be successful, enterprises must begin to focus on the “T” within IoT as opposed to the “I”… Read More
Cloud-to-Client Direct: Serverless Computing
Excerpted from ZDNet Report by Joe McKendrick
 ‘Hybrid cloud isn’t going to be a mix of AWS and Google, or AWS and on-premise. It will be a mix of AWS and client machines.’
‘Hybrid cloud isn’t going to be a mix of AWS and Google, or AWS and on-premise. It will be a mix of AWS and client machines.’
One of the buzzwords to emerge over the past year is that of “serverless” computing or architecture, which, as the term suggests, involves the provisioning of key information technology resources to users without the fuss and muss of acquiring and activating additional hardware, which not only means servers, but disk space as well.
Let the cloud vendors worry about the messy details of protocols, security, resource provisioning, processor speeds, and memory allocation, and focus on the applications business users need to run their organizations.
Serverless is, for all intents and purposes, another name for Platform-as-a-Service (PaaS).
There are vendor tools and environments suited for such a purpose, including Amazon Web Services Lambda, IBM BlueMix OpenWhisk, and Microsoft Azure Functions, Buzzwording aside, full-throttle adoption of serverless platforms may even stir rethinking of optimal hybrid cloud architectures, and what it means for IT teams to serve as brokers of needed business services.
That’s the experience of Gojko Adzic, a highly regarded thought leader in the IT space and partner at Neuri Consulting… Read More
Amazon’s Cloud Glitch Disrupts
Excerpted from Seattle Times Report by Angel Gonzalez
 Amazon says it fixed a problem that triggered a lengthy outage on its cloud storage service, causing widespread frustration among popular online services Tuesday.
Amazon says it fixed a problem that triggered a lengthy outage on its cloud storage service, causing widespread frustration among popular online services Tuesday.
The disruption, which stemmed from an East Coast location, hampered the operations of a wide array of Amazon clients, from media companies to makers of corporate communications software.
Reactions to the outage spread rapidly on Twitter, with memes depicting scenes of chaos from “The Office” and houses on fire.
The problem – and the ensuing outcry – show how important the cloud has become to the smooth functioning of the internet economy, as enterprises migrate their data and computing processes from their own premises to data centers operated by Amazon and other cloud giants.
But it also shows how far-reaching glitches at these data centers – touted as highly reliable – can be.
In Amazon’s case the cloud service may have been so robust that it lulled users into an exaggerated sense of security… Read More
Oscars Flub Evokes Recent Cloud-Computing Snafus
Excerpted from TechTarget Report by Joel Shore
 Now that La La Land Moonlight has won the Academy Award for best picture, this is as good a time as any to look back at some screw-ups in the world of cloud computing.
Now that La La Land Moonlight has won the Academy Award for best picture, this is as good a time as any to look back at some screw-ups in the world of cloud computing.
May we all learn from our mistakes.
The Force is not with you: Take a trip back to May 9, 2016, less than a year ago.
It was on that day the Silicon Valley NA14 instance of Salesforce.com went offline, a condition colloquially known as Total Inability To Support Usual Performance (I’m not going anywhere near the acronym).
Customers lost several hours of data and the outage dragged on for nearly 24 hours.
CEO Mark Benioff took to his Twitter account to ask for forgiveness. Shortly after, Salesforce moved some of its workloads to Amazon Web Services.
AWS giveth, AWS taketh away: Though transferring workloads to AWS helped Salesforce recover lost customer confidence (though not lost data), the opposite was true for Netflix… Read More
Coming Events of Interest
fintech:CODE — March 16th-17th in London, UK. A new international knowledge exchange platform bringing together all DevOps, IT, and IoT stakeholders who play an active role in the finance and tech scene. Key topics include software development, technical challenges for DevOps, DevOps security, cloud technologies and SaaS.
retail:CODE — March 16th-17th in London, UK. 20 real-life case studies, state-of-the-art keynotes, and interactive World Café sessions, 35+ influential speakers will share their knowledge at the intersection of the retail and technology sectors.
Delivery of Things World — April 24th and 25th in Berlin, Germany. Over 400 IT executives will discuss what DevOps really means for business. This event brings together all stakeholders to share their experience and expertise.
Security of Things World — June 12th and 13th in Berlin, Germany. A world class event focused on the next information security revolution. Security concerns that preoccupy enterprise customers today and pragmatic solutions to threats.
Autonomous Systems World — June 14th and 15th in Berlin, Germany. An international knowledge exchange among top experts in the field, providing a unique glimpse into the fascinating world of autonomous robots, intelligent machines, and smart technologies.
INTRASECT — June 29th and 30th in Washington, DC. The first conference of its kind to engage key stakeholders in a comprehensive and engaging examination of existing and future regulatory policy governing the usage of commercial autonomous vehicles.
