In This Issue
- Pai to Repeal Title II
- WH: Innov and Cyber
- Systemic Crisis Looms
- Report from the CEO
- Net Neutrality Change
- UK Cyber-Emergency
- Cloud Adoption State
- CISOs Not Keep Pace
- Cyber Elusive Priority
- WikiLeaks CIA Dump
- Site Security Checks
- True Cloud Definition
- Fog Is Coming: Good
- APIs Key to Transform
- Data Center Changes
- Cloud Wars New Phase
- Coming DCIA Events
Pai Launches Effort to Repeal Title II
Excerpted from Multichannel News Report by John Eggerton
 FCC Chair Ajit Pai has begun the process of reversing the classification of Internet service providers (ISPs) as Title II common carrier services and plans to vote on a Notice of Proposed Rulemaking to that effect at the May meeting.
FCC Chair Ajit Pai has begun the process of reversing the classification of Internet service providers (ISPs) as Title II common carrier services and plans to vote on a Notice of Proposed Rulemaking to that effect at the May meeting.
And while opponents have pledged to man and woman the battlements to prevent it, Pai called it “a fight that we intend to wage and it is a fight that we are going to win.”
He outlined that battle plan in a ringing and stinging indictment of Title II speech on the future of net neutrality regulation at an event at the Newseum in Washington hosted by FreedomWorks and the Small Business & Entrepreneurship (SBE) Council.
Pai has said the thought the days of Title II were numbered, and that countdown could begin May 18th (the date of the meeting).
Following Pai’s speech, Commissioner Michael O’Rielly signaled he was on board.
“I never knew this day was going to come,” he said.
In fact, he associated himself with the announcement, saying it was coming from both of them… Read More
White House Links Innovation and Cybersecurity
Excerpted from FCW Report by Sean Carberry
White House cybersecurity coordinator Rob Joyce discussed how the coming cybersecurity executive order connects with the recently announced Office of American Innovation, led by Jared Kushner.
The White House is close to finalizing its long-awaited cyber executive order, and there are growing questions over how authorities for modernizing and securing federal IT will be split between the National Security Council and the new Office of American Innovation.
Rob Joyce, the White House cybersecurity coordinator delivered his first public remarks at the Georgetown Conference on Cyber Engagement on April 24, and he said the order is “close and nearby.”
He indicated the timing of the release is less about finalizing the order than about finding the right news cycle opportunity, as a number of former officials have been speculating to FCW in recent weeks.
“I think the important focus on this is we want to make sure the cybersecurity EO emerges in sequence with other things that the administration is rolling out so that we don’t distract from other important messages that are out there,” Joyce said.
In his remarks, Joyce ran through the same overarching administration priorities that homeland security advisor Tom Bossert outlined… Read More
Systemic Cybersecurity Crisis Looms
Excerpted from Network World Report by Sean Cassidy
 The number of large-scale, highly damaging data breaches over the past few years has led some to believe the market is on its way to another systemic crisis, similar to the Great Recession.
The number of large-scale, highly damaging data breaches over the past few years has led some to believe the market is on its way to another systemic crisis, similar to the Great Recession.
Corporate greed, lax risk management procedures and insufficient oversight by regulators contributed to the 2008 financial crisis.
Likewise, the perception that cybersecurity is just another cost center coupled with organizations’ tendencies to implement bare minimum security measures could be paving the way for a systemic cybersecurity crisis.
There is a widespread notion that cybersecurity is one more hurdle for executives to deal with that drains company resources.
Cisco surveyed more than 1,000 executives, and 74 percent of participants said the main purpose of cybersecurity is to reduce risk rather than enable growth.
This ideology that cybersecurity is costly and hinders productivity is not just inaccurate, it is harmful… Read More
Report from DCIA CEO Marty Lafferty

The DCIA greatly appreciates Federal Communications Commission (FCC) Chairman Ajit Pai’s investment of time to consult with technology interests regarding a roll-back of Net Neutrality rules created by the Commission in 2015.
The 2015 classification of broadband as a utility under the heavy regulatory framework of the old-monopoly telephone system, in the DCIA’s view, threatened continuing investment and innovation.
At the time, we asked whether reclassifying the Internet as a common-carrier service was the only alternative.
In the past two decades, the Internet has gotten much faster and in many ways better – it has been a shining star of both economic growth and societal advancement worldwide.
In the US, 100+ Mbps connections are now available to 85% of households, and the world’s top web companies, including brands like Amazon, Facebook, Google, and Twitter represent American contributions to the global economy,
We enjoy an open Internet in America with access to a plethora of websites and services from a multiplicity of access points and devices; and Internet access providers support these realities because meeting these end-user demands is profitable.
The DCIA’s comments regarding the 2015 Notice of Proposed Rulemaking (NPRM) centered on four key regulatory strategies: 1) Take a Holistic Approach; 2) Treat Wireline and Wireless Equally; 3) Continue Using a Light Touch; and 4) Focus on Cross-Ownership as the Area for Greatest Potential Abuse.
On this final point, we urge the FCC and Congress to consider the adoption of an overriding principle that predates the first broadcast television station, cable system, or data delivery network, but has in fact stood the test of time.
This principle contributed to the growth and strength of another of America’s longest-term success stories – the motion picture industry – and was initiated more than a century ago when vertical integration threatened to foment undesirable monopoly powers.
It can be summarized simply as a division of basic ownership of key components of a very large content distribution system in order to promote competition.
Entities could either own the theater or own the movie, but they couldn’t own both: either control the seats audience members sit-in or control what’s shown on the screen.
In the rapidly advancing broadband era of digital content distribution, this competition-fostering principle translates to: separate ownership of the conduit and the content.
Own the plant that delivers access service – telephony, cable, satellite, wireless, etc. – OR own what people watch, listen to, or play – TV channel / movie package, music service, game platform, etc. – BUT NOT BOTH.
This bold but simple imperative could stimulate competitive growth and reduce insidious conflicts-of-interest that have crept into the telecommunications and entertainment/media sectors.
This single guideline could inform contemporary legislative and regulatory reform to help eliminate the greatest current threat to continuing innovation.
Because the devil is always in the details, there will be more to come on this. Share wisely, and take care.
Sweeping Changes to Net Neutrality Rules
Excerpted from NY Times Report by Cecilia Kang
 The Chairman of the Federal Communications Commission (FCC) on Wednesday outlined a sweeping plan to loosen the government’s oversight of high-speed internet providers, a rebuke of a landmark policy approved two years ago to ensure that all online content is treated the same by the companies that deliver broadband service to Americans.
The Chairman of the Federal Communications Commission (FCC) on Wednesday outlined a sweeping plan to loosen the government’s oversight of high-speed internet providers, a rebuke of a landmark policy approved two years ago to ensure that all online content is treated the same by the companies that deliver broadband service to Americans.
The Chairman, Ajit Pai, said high-speed internet service should no longer be treated like a public utility with strict rules, as it is now.
The move would, in effect, largely leave the industry to police itself.
The plan is Mr. Pai’s most forceful action in his race to roll back rules that govern telecommunications, cable, and broadcasting companies, which he says are harmful to business.
But he is certain to face a contentious battle with the consumers and tech companies that rallied around the existing rules, which are meant to prevent broadband providers like AT&T and Comcast from giving special treatment to any streaming videos, news sites and other content.
“Two years ago, I warned that we were making a serious mistake,” Mr. Pai said at the Newseum in Washington, where he laid out the plan… Read More
UK Likely to Face Cyber-Emergency
Excerpted from ComputerWeekly Report by Warwick Ashford
 The UK has not had to face a top-level cybersecurity threat before, but the National Cyber Security Center (NCSC) is continually preparing for what it considers to be inevitable.
The UK has not had to face a top-level cybersecurity threat before, but the National Cyber Security Center (NCSC) is continually preparing for what it considers to be inevitable.
Banks and insurers enjoy a significantly higher level of trust from consumers in the cybersecurity of their systems than any other sector but the financial services industry is less confident in its ability to
“A level-1 cyber attack would be a classic national emergency that the government would take very seriously and the average person on the street would probably notice some sort of impact on their lives,” said Felicity Oswald, deputy director of strategy and effectiveness at NCSC.
“It is not a question of ‘if’ but ‘when.’
We know it is going to happen,” she told a Policy-UK forum in London on the British approach to cybersecurity.
Most incidents are level-3.
“These are every day incidents to us, but are still hugely significant to UK organizations,” said Oswald… Read More
2017 State of Cloud Adoption and Security
Excerpted from Forbes Report by Louis Columbus
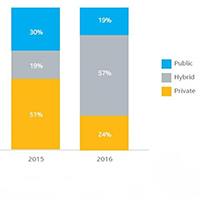 Hybrid cloud adoption grew 3X in the last year, increasing from 19% to 57% of organizations surveyed.
Hybrid cloud adoption grew 3X in the last year, increasing from 19% to 57% of organizations surveyed.
In 15 months, 80% of all IT budgets will be committed to cloud solutions.
Hybrid cloud adoption grew 3X in the last year, increasing from 19% to 57% of organizations surveyed.
In 15 months, 80% of all IT budgets will be committed to cloud solutions.
73% of companies are planning to move to a fully software-defined data center within 2 years.
49% of businesses are delaying cloud deployment due to a cybersecurity skills gap.
These and many other insights are from the recently published report, Building Trust in a Cloudy Sky: The State of Cloud Adoption and Security.
Late last year Intel Security surveyed over 2,000 professionals for its annual cloud security research study.
The 2,009 respondents were drawn from a third-party database of IT and technical decision makers… Read More
CISOs Unable to Keep Pace with Data Breaches
Excerpted from ITBusinessEdge Report by Sue Poremba
 For the most part, cybersecurity seems to continue to be reactive rather than proactive.
For the most part, cybersecurity seems to continue to be reactive rather than proactive.
Yes, security systems are in place to prevent potential incidents, but overall, I think too many organizations are unprepared for when that incident does happen and spend a lot of time reacting to the aftermath.
However, according to new research, organizations appear to be falling behind on their reactive approach.
For The Global CISO Study: How Leading Organizations Respond to Security Threats and Keep Data Safe report, ServiceNow surveyed 300 CISOs and found that 81 percent said they believe data breaches in their company are going unaddressed.
Another 78 percent said they are concerned that they don’t have the capability to even detect a data breach (if that’s true, then no wonder the breaches aren’t being addressed). And when they are able to identify potential cybersecurity events, 70 percent admit they struggle to prioritize the security events. And as the report stated:
This failure to prioritize can paralyze organizations, given that they can be hit by thousands of cyberattacks daily… Read More
Cybersecurity Remains Elusive Business Priority
Excerpted from Network World Report by Jon Oltsik

I’ve been remiss by not blogging earlier this year about ESG’s annual IT spending intentions research.
The year 2017 continues to follow a pattern: Cybersecurity is a high business and IT priority for most organizations.
Based upon a global survey of 641 IT and cybersecurity professionals, the ESG research reveals:
While just over half (53%) of organizations plan on increasing IT spending overall this year, 69% said they are increasing spending on cybersecurity.
As far as cybersecurity spending goes, 48% will make their most significant cybersecurity technology investments in cloud security, 39% will in network security, 30% in endpoint security, and 29% in security analytics.
Respondents were asked which business outcomes were their highest priorities for this year.
The top three results were as follows: 43% said “reducing costs,” 40% said “increasing productivity,” and 39% said “improving information security.”
When asked which business initiatives will drive the most IT spending, 39% said “increasing cybersecurity,” the top selection of all… Read More
WikiLeaks CIA Dump Most Damaging Yet
Excepted from TechCrunch Report by Eric O’Neill
 It’s impossible to keep up with the nonstop news coverage and multiple storylines around the recent WikiLeaks CIA dump.
It’s impossible to keep up with the nonstop news coverage and multiple storylines around the recent WikiLeaks CIA dump.
The initial Vault 7 data drop led to Assange’s press conference about “helping” private companies patch vulnerabilities, all while fear started to spread around the intelligence community listening in to our internet-connected Samsung TVs and Apple products at home, and Cisco disclosing that its routers and Internet switches had been hacked.
Most recently, CIA Director Mike Pompeo criticized WikiLeaks in his first public address since being confirmed, calling the organization a “non-state hostile intelligence service.”
Pompeo makes an undeniable point about the far-reaching consequences of a leak such as this one – which, speaking from an intelligence perspective, is likely the most frightening yet.
The truth of the matter is that the breach of the CIA’s attack tools not only placed the US at a deficit in our offensive cyber-capabilities, it has threatened the world’s most critical businesses, organizations, and national security peace of mind.
To echo Pompeo’s statements, we are now all more vulnerable… Read More
Checking a Website’s Security
Excerpted from NY Times Report by JD Biersdorfer
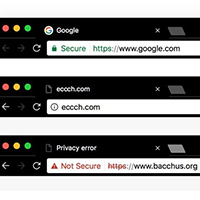 Q. I was browsing online and noticed a small letter “i” in a circle. What does that mean? I use the Chrome browser.
Q. I was browsing online and noticed a small letter “i” in a circle. What does that mean? I use the Chrome browser.
A. The web is full of sites that do not use the strongest security, and some browsers – including Google Chrome and Mozilla Firefox – now warn users when the page they are visiting may put their information at risk.
In Chrome, that “i” symbol indicates a site may not be secure because it is using an unencrypted connection to exchange data with your computer.
When you click the “i” on the left side of the Chrome address bar, you can see more information about the site, adjust some settings and possibly see a “Your connection to this site is not secure” warning.
As you may have noticed from online shopping, sites with secure connections use a form of the HyperText Transfer Protocol Secure technology to encrypt data between their web servers and your computer; this helps protect your credit-card number and other personal information from being intercepted by someone else.
These sites also have a security certificate from a presumably trusted authority that verifies the website’s identity… Read More
True Cloud Definition Lost on Some IT Pros
Excerpted from Search Cloud Computing Report by Mark May
 In almost any enterprise IT shop, you are likely to see at least one laptop sticker that says, “There is no cloud. It’s just someone else’s computer.”
In almost any enterprise IT shop, you are likely to see at least one laptop sticker that says, “There is no cloud. It’s just someone else’s computer.”
I understand that the saying is good for a laugh, but aside from that, it could not be further from the truth.
If we stick to the definition of cloud computing outlined by the US government’s National Institute of Standards and Technology (NIST), the cloud has five attributes: on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service.
Do you notice anything on that list about location?
Cloud computing, in all its various deployment models, has fundamentally changed how computing works.
It is not a place, but rather a way of managing IT resources.
If we dig deeper into the NIST definition of cloud computing, we can see it has three common service models:
Software-as-a-Service (SaaS) is a software deployment model where an application is delivered over the internet… Read More
Fog Is Coming: Good News for Cloud
Excerpted from CIO Report by Robert MacInnis
 The cloud has been in the news a lot lately, and mostly for bad behavior.
The cloud has been in the news a lot lately, and mostly for bad behavior.
It’s been slow, expensive, insecure or simply MIA – taking major corporations offline for hours and raising questions about the future of cloud computing.
Is cloud computing going away? Absolutely not, but a rapidly emerging new technology may mean that we won’t be stuck with our cloudy blues for long.
Imagine enabling organizations to leverage the benefits of both cloud and on-site IT, with the speed, resiliency, bandwidth and scalability to run existing workloads – regardless of location – and to power new technologies such as the Internet of Things (IoT) and machine learning.
This new approach is called “fog computing,” and it is poised to have a huge impact on how – and where – computing happens in the very near future.
Fog looks like a cloud, but it’s closer to you… Read More
APIs Key to Digital Transformation
Excerpted from CloudTech Report by Monica Brink
 Digital transformation continues to dominate boardroom discussions as businesses increasingly realize the organizational and cost efficiencies that digitization can provide.
Digital transformation continues to dominate boardroom discussions as businesses increasingly realize the organizational and cost efficiencies that digitization can provide.
The concept reflects technology’s role in both shaping and stimulating strategic decision-making, with its ability to automate and simplify business processes, improve customer relationships, enhance productivity, and reap cost savings.
In fact, IDC predicts that by the end of 2017, two-thirds of CEOs of global 2000 enterprises will have digital transformation at the center of their corporate strategy.
However, it can be a challenge for organizations to implement a digitization strategy against a background of increasingly complex day-to-day IT operations, which often involve managing both cloud and on-premises IT infrastructure.
For many, application programming interfaces (APIs) are an essential component of merging the old and the new IT platforms, capturing vast amounts of data and ultimately achieving their digital transformation strategy.
The most common description of an API is a set of functions and procedures that allow applications to access features or data… Read More
Cloud Changes Data Center Industry
Excerpted from Data Center Frontier Report by Rich Miller
 Welcome to our sixth Data Center Executive Roundtable, a quarterly feature showcasing the insights of thought leaders on the state of the data center industry, and where it is headed.
Welcome to our sixth Data Center Executive Roundtable, a quarterly feature showcasing the insights of thought leaders on the state of the data center industry, and where it is headed.
In our First Quarter 2017 roundtable, we will examine four topics: How the rise of the cloud is shaping the data center industry, the prospects for additional consolidation and M&A, the latest significant trends in data center tools, and how the focus on speed to market is affecting the data center supply chain.
Here’s a look at our distinguished panel:
Jeff Klaus is General Manager of Intel Data Center Software Solutions, which provide real-time, server-level data on the power and thermal conditions across a wide range of data center servers.
Sean Iraca is vice president of service enablement at Digital Realty, the leading provider of wholesale data centers and technology real estate.
Gary Niederpruem is Vice President, Global Marketing and Strategy for Vertiv… Read More
Cloud Wars Enter New Phase
Excerpted from CloudTech Report by Rick Delgado
 Imagine a business where the product keeps getting better and better, like storage space and video quality, but the prices keep falling steadily as the product continues to improve.
Imagine a business where the product keeps getting better and better, like storage space and video quality, but the prices keep falling steadily as the product continues to improve.
It’s happening in cloud computing – and this ‘race to zero’ has people in the industry deeply worried.
The current leader, Amazon Web Services (AWS), slashed their prices an astounding 44 times in the past six years.
Amazon’s strategy, it seems, is more of a low cost, high volume model.
This strategy seems to be working according to research company Gartner, who reported that AWS stores twice as much customer data as the next seven leading public cloud companies.
AWS profits in 2016 grew over 120% and sales grew over 60%, extinguishing any assumptions that AWS was a loss leader product for Amazon as a whole.
Amazon is betting at such a low cost, enterprise businesses will treat cloud services like you treat products at Walmart.
With such low prices on products, you’ll keep adding more to your cart… Read More
Coming Events of Interest
Security of Things World — June 12th and 13th in Berlin, Germany. A world class event focused on the next information security revolution. Security concerns that preoccupy enterprise customers today and pragmatic solutions to threats.
Autonomous Systems World — June 14th and 15th in Berlin, Germany. An international knowledge exchange among top experts in the field, providing a unique glimpse into the fascinating world of autonomous robots, intelligent machines, and smart technologies.
INTRASECT — June 29th and 30th in Washington, DC. The first conference of its kind to engage key stakeholders in a comprehensive and engaging examination of existing and future regulatory policy governing the usage of commercial autonomous vehicles.
Industry of Things World Asia — July 3rd and 4th in Singapore. An international knowledge exchange platform bringing together more than 300 high-level executives who play an active role in the industrial internet of things (IoT).
Industry of Things World Europe — September 18th and 19th in Berlin, Germany. Join more than 1,000 high-level executives to rethink your technology and business strategy for scalable, secure, and efficient IoT.
IoT Solutions World Congress — October 3rd through 5th in Barcelona, Spain. This event has grown enormously in no time and is an excellent barometer and source of information, inspiration, collaboration and transformation.
