In This Issue
- 3.5M Cyber Jobs Open
- Cloud & Cybersecurity
- Cloud Wars Top Ten
- Report from the CEO
- Telecom Cloud Market
- VZ Mobile Cloud Vision
- Telefonica MapReduce
- OpenText Buys Firm
- Cloud Change Agent
- Pushing Cloud to Edge
- Edge Best Practices
- Open Internet Docket
- NAB & Cybersecurity
- Computing Power Up
- Intel Video Processor
- Hollywood in Attack
- Coming DCIA Events
3.5 Million Cybersecurity Job Openings by 2021
Excerpted from CSO Report by Steve Morgan
 A new report out from Cybersecurity Ventures estimates there will be 3.5 million unfilled cybersecurity jobs by 2021, up from 1 million openings last year.
A new report out from Cybersecurity Ventures estimates there will be 3.5 million unfilled cybersecurity jobs by 2021, up from 1 million openings last year.
Employment figures from the US and India highlight the cybersecurity labor crisis.
In 2017, the US employs nearly 780,000 people in cybersecurity positions, with approximately 350,000 current cybersecurity openings, according to CyberSeek, a project supported by the National Initiative for Cybersecurity Education (NICE), a program of the National Institute of Standards and Technology (NIST) in the US Department of Commerce.
The current number of US cybersecurity job openings is up from 209,000 in 2015.
At that time, job postings were already up 74 percent over the previous five years, according to a Peninsula Press analysis of numbers from the Bureau of Labor Statistics.
At this rate, the US is on pace to hit a half-million or more unfilled cybersecurity positions by 2021.
The National Association of Software and Services Companies (NASSCOM) estimates India will need 1 million cybersecurity professionals… Read More
Cloud Computing and Cybersecurity in 2017
Excerpted from Information Age Report by Ren Rossi
 The adoption of cloud computing has been on the up since as far back as 2008, when a survey conducted by the Pew Research Institute found that cloud services were used by nearly 69% of Americans.
The adoption of cloud computing has been on the up since as far back as 2008, when a survey conducted by the Pew Research Institute found that cloud services were used by nearly 69% of Americans.
Since then, the industry has experienced hyper-growth and exceeded the already vast predictions of how big it would become.
IDC predicts that the cloud computing market in 2017 will be worth $107 billion and, according to Gartner, by 2020 a corporate ‘no-cloud’ policy will be as unusual as a ‘no-internet’ policy would be today.
Indeed, it would be difficult to imagine an organization in 2017 that did not use webmail, file sharing and storage, and data backup.
As the use of cloud computing spreads so does awareness of the associated risks.
At the time of writing, there have been 456 data breaches worldwide this year according to the Identity Theft Resource Center (ITRC), following a 40% increase in 2016 compared to the previous year… Read More
The Cloud Wars Top Ten
Excerpted from Forbes Report by Bob Evans
 The secret sauce that’s made cloud computing a generational phenomenon is not so much the technology itself-although much of it is truly extraordinary-but rather the transformative ability of the cloud to help businesses accelerate innovation, digitalize their operations, engage more intimately with customers, and attract and retain world-class talent.
The secret sauce that’s made cloud computing a generational phenomenon is not so much the technology itself-although much of it is truly extraordinary-but rather the transformative ability of the cloud to help businesses accelerate innovation, digitalize their operations, engage more intimately with customers, and attract and retain world-class talent.
In that context, I’ve created the Cloud Wars Top 10 as a weekly ranking of the enterprise-tech companies that are doing the best job of aligning their cloud technology to the rapidly evolving needs of businesses.
Because as great as the technology is, buying decisions today are being made by business executives who have little or no interest in arcane, deep-tech discussions and are instead solely focused on picking the best solution for linking global supply chains with demand chains, closing financial books in days instead of weeks, finding and hiring superb people, and transforming how business is done from what’s convenient for the seller to what’s most appealing to the buyer.
For too long, the enterprise-tech business has communicated with the world from an “inside-out” perspective that leads every discussion with product features, product specs, product details, and product POVs.
In today’s rapidly accelerating business climate, such approaches are counterproductive… Read More
Report from DCIA CEO Marty Lafferty

Following up on last week’s report covering the impact on cloud service providers (CSPs) of new cybersecurity regulations in China, this week’s report turns to a similar discussion of new data protection regulation in Europe.
The DCIA’s primary concern is that the General Data Protection Regulation (GDPR), which becomes effective in May 2018, will impact in a material way the business models of CSPs.
The GDPR will substantially change the ways in which personal data of EU customers must be protected.
The new regulations will require that CSPs, where necessary, take measures to improve their data protection capabilities, and in all cases revise their service level agreements (SLAs) to reflect new liabilities placed on them by the GDPR.
CSP customer organizations in turn should ensure that their CSPs understand and contractually accept their new obligations.
All related systems and processes concerning personal data and increased risks need to be reviewed and updated before the May 2018 deadline, and the higher costs must be addressed.
Under the GDPR, data processing is broadly defined, and includes storage of personal data.
Personal data also has a broad definition and includes any data that relates to an identified or identifiable living human.
CSPs not based in the EU will be impacted by the GDPR if they are offering goods or services to EU-based individuals, either directly or through resellers, and will be covered by its provisions whether or not they have knowledge of their customers using their services to process or store personal data.
Please contact the DCIA for assistance in the necessary due diligence and auditing of your cloud supply chain to ensure compliance. Share wisely, and take care.
Global Telecom Cloud Market 2017
Excerpted from Press Announcement from GlobeMetrix
 The Global Telecom Cloud Market 2017 examines the performance of the telecom cloud market.
The Global Telecom Cloud Market 2017 examines the performance of the telecom cloud market.
It encloses an in-depth judgment of the telecom cloud market state and the competitive landscape globally.
This report analyzes the potential of telecom cloud market in the present and the future prospects from various angles in detail.
The Global Telecom Cloud Market 2017 report includes telecom cloud industry volume, market Share, market trends, telecom cloud growth aspects.
A wide range of applications, utilization ratio, supply and demand analysis are also included in the report.
It shows manufacturing capacity, telecom cloud price during the forecast period from 2017 to 2022.
To get a sample of the report, please click here.
The report covers the top telecom cloud manufacturing industry players from regions like United States, EU, Japan, and China… Read More
Verizon’s Vision for Mobile and Cloud
Excerpted from Light Reading Report by Craig Mastsumoto
 Fancy technologies such as autonomous cars and the Internet of Things (IoT) are going to give the telecom network a new look, according to Ed Chan.
Fancy technologies such as autonomous cars and the Internet of Things (IoT) are going to give the telecom network a new look, according to Ed Chan.
That means changing not only the mobile network, but also the fiber network and the way we think about the cloud, the Verizon Communications Senior Vice President said during his keynote at the Big Communications Event in May.
For example, the downloading of information won’t be the network’s main priority.
The fiber network, in particular, is going to need fatter upload pipes — a symmetric network, ideally, Chan said — but even that won’t be enough.
“It needs to now be interacting with the information in the physical world,” he said.
Those interactions will have to be nearly real-time, which is why mobile edge computing (MEC) is being discussed so heavily.
In-vehicle sensors, for instance, will gather information that needs to be acted upon immediately; there won’t be time to shunt sensor information to the cloud… Read More
Telefonica’s MapReduce Service
Excerpted from Telefonica Business Solutions Blog
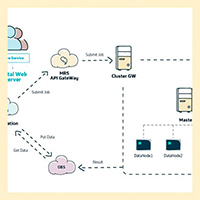
With rapid development of the Internet era, enterprise data is increasing explosively.
An urgent demand is developed on how to generate value from the complex and chaotic data and how to use the data to implement innovations and seize business opportunities.
Obviously, conventional data processing is incompetent in this big data era.
MapReduce Service (MRS) provides storage and analysis capabilities for massive data and builds a reliable, secure, and easy-to-use operation and maintenance (O&M) platform.
Users can apply for use Hadoop, Spark, HBase, and Hive services to quickly create clusters and provide storage and computing capabilities for massive data analysis or real-time processing.
After data storage and computing are fulfilled, the cluster service can be terminated, and no fee will be charged accordingly. You can also choose to run clusters permanently.
MRS delivers the following functions: analysis and computing of massive data… Read More
OpenText Buys Cloud Firm for $103 Million
Excerpted from The Record Report by Terry Pender
 OpenText is buying a US cloud computing company for $103 million.
OpenText is buying a US cloud computing company for $103 million.
The deal for Covisint, announced Monday after the markets closed, is expected to be completed in the third quarter of this year pending approvals by regulators and Covisint shareholders.
OpenText intends to pay for Covisint with cash-on-hand, the Waterloo-based company said in a brief statement.
It is offering $2.45 a share for Covisint’s shares.
That is 23 per cent more than the closing price of Covisint’s shares on Friday
OpenText, Canada’s largest software company, specializes in enterprise information management.
It develops software that organizes corporate and government information on the Internet.
Covisint, headquartered in Detroit, is a leading cloud-based platform for applications related to identity, automotive and the internet of things (IoT)… Read More
Cloud as Change Agent in Your Enterprise
Excerpted from CIO Report by Pete Bartolik
 Are you an enabler or a digital leader? Do you view the CIO’s role as that of a change agent or more like an IT triage surgeon?
Are you an enabler or a digital leader? Do you view the CIO’s role as that of a change agent or more like an IT triage surgeon?
Many CIOs are conflicted by the need to maximize the value of existing infrastructure while laying the path for digital transformation.
Some CIOs may think that the key to effective digital leadership lies in simply clearing the way for business units to quickly innovate by freely consuming cloud services.
Grasping a leadership role may be a better option.
Gartner says that 29% of IT spend comes from business units, and that rate is going to increase.
“This business-driven IT was often a means of getting around traditional slow-paced IT processes,” Gartner states.
“However, in today’s world, it is more often designed to provide technically savvy business people a means of implementing new ideas quickly, while adapting to, or entering, new markets as effortlessly as possible… Read More
Key Drivers Pushing Cloud to the Edge
Excerpted from Forbes Report by Jankiram MSV
 Today’s cloud computing architecture resembles 70s mainframes.
Today’s cloud computing architecture resembles 70s mainframes.
The heavy lifting happens in dense data centers that act as the central point of gravity.
In both the scenarios, applications share the underlying infrastructure.
While this architecture works for the majority of the scenarios, the emerging use cases demand a different approach.
Edge computing fundamentally changes the cloud by making it distributed and decentralized.
With edge, the core building blocks of cloud such as compute, storage, and the network will move closer to the applications.
Cloud providers will move abstract layers such as machine learning models, serverless computing, and lightweight databases that run on the core infrastructure to the edge.
Since the latency involved in making a round trip to the cloud is minimized, edge computing dramatically improves the user experience… Read More
Best Practices for Edge Computing Deployments
Excerpted from Data Center Journal Report by Jack Pouchet
 Every time you use your bank card to pay for a cappuccino, join a conference call from the road, or access a streaming service to kick back and relax, you’re benefiting from a big IT trend-the growth in edge computing.
Every time you use your bank card to pay for a cappuccino, join a conference call from the road, or access a streaming service to kick back and relax, you’re benefiting from a big IT trend-the growth in edge computing.
Whether the goal is speeding the delivery of applications and content to remote users or collecting data from remote sites, edge sites are growing in number and importance.
They range from regional and local data centers to the small computer rooms and communications centers in regional offices to network closets and internet of things (IoT) gateways in retail stores, school buildings, government offices and industrial sites.
And although they vary in size and complexity, they share some common traits.
They are by their nature physically distant from the primary data center-and the team that supports it.
Many are also in spaces that were never designed for IT, such as storerooms, factories, industrial sites, and utility closets.
This situation can mean having to manage remote IT and network assets without visibility into that technology… Read More
Open Internet Docket Explodes
Excerpted from Multichannel News Report by John Eggerton
 The FCC’s open internet docket, dubbed “Restoring Internet Freedom,” has seen a huge wave of comments, or at least a major update of the number posted, since Friday June 2nd, with more than 4.9 million posted, up by about 2 million from Friday afternoon’s 2.9 million-plus.
The FCC’s open internet docket, dubbed “Restoring Internet Freedom,” has seen a huge wave of comments, or at least a major update of the number posted, since Friday June 2nd, with more than 4.9 million posted, up by about 2 million from Friday afternoon’s 2.9 million-plus.
Sen. Ed Markey (D-MA), an opponent of Republican FCC chair Ajit Pai’s proposal to roll-back Title II, said earlier this year he thought the comments would dwarf those in the docket for the 2015 Open Internet order, which exceeded 4 million.
With still more than two months left in the comments cycle, he could be right.
Pai has signaled the FCC would err on the side of allowing “questionable” comments for the sake of a full and robust record.
“There’s obviously a tension between having an open process where it’s easy to comment and preventing questionable comments from being filed, and generally speaking, this agency has erred on the side of openness,” he told reporters at last month’s public meeting.
“We want to encourage people to participate in as easy and accessible a way as possible… Read More
NAB Embarks on Cybersecurity Evangelism
Excerpted from TV Technology Report
 Kelly Williams is senior director, engineering and technology policy in the Technology Department of the National Association of Broadcasters; he served on the FCC’s CSRIC working group mentioned below.
Kelly Williams is senior director, engineering and technology policy in the Technology Department of the National Association of Broadcasters; he served on the FCC’s CSRIC working group mentioned below.
This interview is part of the Radio World eBook “The Internet of Broadcast Things.”
RADIO WORLD: What sorts of resources on cybersecurity are available from organizations like the Department of Homeland Security, NIST, FCC and NAB? KELLY WILLIAMS: There are a number of resources and documents on the Department of Homeland Security’s website, although they tend to be more global in scope.
The top level for the federal government is the National Institute of Standards and Technology.
They are charged with creating the standards for cyber security that all government agencies must adhere to, including the FCC.
NIST has a number of reports and papers on its website under the Computer Security Resource Center.
The FCC responded to the NIST mandate by creating CSRIC, the Communications Security Reliability and Interoperability Council… Read More
Computing Power Outstripping our Knowledge
Excerpted from Forbes Report by Joe McKendrick
 We may have made a lot of advances in technology in recent years, but most businesses still can’t see what’s on the road right in front of them.
We may have made a lot of advances in technology in recent years, but most businesses still can’t see what’s on the road right in front of them.
If anything, “businesses are driving a car using only a rear-view mirror, with an opaque wall instead of a windshield in front.”
That’s the observation of Dr. Vishal Sikka, CEO of Infosys.
I had the opportunity to sit down with Sikka at his company’s recent Confluence conference in San Francisco.
Supercomputing power is available to all, but are we ready?
Moore’s Law — which posits that processing power will continue to grow geometrically — apparently has some time left and may go on for decades, Sikka says.
However, organizations are focusing too much on speed and capacity, and not enough on the knowledge aspect of all the compute power coming their way.
“In corporate planning, organizations have a tough time building out their financial plans,” he remarks… Read More
IoT Security and 4k Video on Intel Core Processors
Excerpted from Electronics Weekly Report by Alun Williams
 Check out a couple of new whitepapers on the site relating to IoT and the video optimization on 7th-gen Intel Core processors.
Check out a couple of new whitepapers on the site relating to IoT and the video optimization on 7th-gen Intel Core processors.
They’re from Intel and cover fog computing and embedded applications that rely on video and media processing.
Note that both these are Intel whitepapers and that you do have to provide some details to download the free whitepapers.
This Intel report covers how IoT systems can be assured of end-to-end security today and also count on a roadmap for future security requirements, it says.
Intel writes: The IoT offers tremendous value, but also introduces major security challenges.
One of the primary benefits of fog computing is how it simplifies security.
Rather than address security across a large number of endpoints, fog computing aggregates and maps connections across a relatively small number of gateways.
Consolidation ensures consistent policy enforcement and smooths integration across disparate IT systems… Read More
More Leaks: “Hollywood Is Under Attack”
Excerpted from The Hollywood Reporter Report by Tatiana Siegel
 “There’s always more.” That was the chilling response TheDarkOverlord gave to The Hollywood Reporter when asked if the hacking collective planned to leak additional Hollywood content in the wake of Monday’s release of eight unaired episodes of ABC’s Funderdome.
“There’s always more.” That was the chilling response TheDarkOverlord gave to The Hollywood Reporter when asked if the hacking collective planned to leak additional Hollywood content in the wake of Monday’s release of eight unaired episodes of ABC’s Funderdome.
“Hollywood is under attack, and we’re at the forefront of this most recent offensive,” wrote the pseudonymous hacking collective to THR.
“We’re not in the business to scare anyone. We’re in the business of earning vast amounts of internet money.”
But even more alarming, TheDarkOverlord also claims to have studio movies in addition to the unaired series and films from such networks as IFC and National Geographic that have been been previously reported.
Though Netflix and Disney/ABC balked at paying ransom demands, others quietly have paid up, according to knowledgeable sources.
“Make no mistake, Hollywood is under assault,” the hacking collective wrote to THR… Read More
Coming Events of Interest
Security of Things World — June 12th and 13th in Berlin, Germany. A world class event focused on the next information security revolution. Security concerns that preoccupy enterprise customers today and pragmatic solutions to threats.
Autonomous Systems World — June 14th and 15th in Berlin, Germany. An international knowledge exchange among top experts in the field, providing a unique glimpse into the fascinating world of autonomous robots, intelligent machines, and smart technologies.
INTRASECT — June 29th and 30th in Washington, DC. The first conference of its kind to engage key stakeholders in a comprehensive and engaging examination of existing and future regulatory policy governing the usage of commercial autonomous vehicles.
Industry of Things World Asia — July 3rd and 4th in Singapore. An international knowledge exchange platform bringing together more than 300 high-level executives who play an active role in the industrial internet of things (IoT).
Industry of Things World Europe — September 18th and 19th in Berlin, Germany. Join more than 1,000 high-level executives to rethink your technology and business strategy for scalable, secure, and efficient IoT.
IoT Solutions World Congress — October 3rd through 5th in Barcelona, Spain. This event has grown enormously in no time and is an excellent barometer and source of information, inspiration, collaboration and transformation.
