In This Issue
- IoT Pushes Innovation
- Big Data: Economics
- Billion Cloud VR Users
- Report from the CEO
- New Cyber Strategy
- IoT Reshapes Internet
- USTRANSCOM’s Cloud
- Cisco & Google Cloud
- ARM IoT Security Plan
- Complex Compliance
- Keep Cloud Data Safe
- Build a Digital Defense
- Mostly Mobile Devices
- Infrastructure Attacks
- Major Botnet Warning
- 2017 Storage Visions
- Coming DCIA Events
Growth of IoT Pushing Tech Innovation
Excerpted from CETUSNews Report by Angus Loten
 As a growing number of firms turn to connected devices to glean ever more data on customers or processes, central software platforms handling the inflow of that data are being pushed to the edge – literally, says Forrester Research.
As a growing number of firms turn to connected devices to glean ever more data on customers or processes, central software platforms handling the inflow of that data are being pushed to the edge – literally, says Forrester Research.
In its latest outlook on information technology trends, the IT industry research firm puts the internet of things (IoT), and its likely impact on cloud computing, in first place.
The growth of IoT is driving a host of related tech innovations, largely aimed at cutting down the lag time between gathering data into a cloud platform, analyzing it and taking action.
“Latency is becoming an issue as firms try to push more data to software that runs in the cloud or in the data center,” the report says.
Given the growing amount of data, it’s becoming “increasingly uneconomical to do all processing centrally,” it adds.
As such, the rapid adoption of IoT is accelerating edge computing, an architecture where data is processed closer to where it is generated – that is, at the “edge” of the network.
This includes the development of a host of emerging tools, such as gateway servers, microdata centers, cloudlets… Read More
Big Data: About Economics Not Technology
Excerpted from Customer Think Report by Jacob Morgan
 Bill Schmarzo, author of “Big Data: Understanding How Data Powers Big Business” and “Big Data MBA: Driving Business Strategies with Data Science“, is responsible for setting strategy and defining the big data service offerings for Dell EMC’s Big Data Practice.
Bill Schmarzo, author of “Big Data: Understanding How Data Powers Big Business” and “Big Data MBA: Driving Business Strategies with Data Science“, is responsible for setting strategy and defining the big data service offerings for Dell EMC’s Big Data Practice.
As a CTO within Dell EMC’s 2,000+ person consulting organization, he works with organizations to identify where and how to start their big data journeys.
He is a University of San Francisco School of Management (SOM) Executive Fellow where he teaches the “Big Data MBA” course.
Big data is a term.
The adjective ‘big’ has no meaning.
Most companies are interested in looking at the ‘boat load of data’ they have but are not sure what to do with it.
Right now, companies are only looking at the data to see ‘what happened’… Read More
How Cloud Can Activate a Billion VR Users
Excerpted from Upload VR Report by Simon Solotko
 Every technology needs a corresponding business model to thrive.
Every technology needs a corresponding business model to thrive.
Facebook’s technology is a social matrix which intelligently channels user generated content (UGC) interspersed with advertising through a massive social network.
Powering the model requires billions of living, active users.
For virtual reality to become a core technology for the social matrix it needs billions of users.
Facebook has said as much, placing the technical responsibility of jacking one billion users into virtual reality – and with it the social matrix business model – in the hands of the same engineer who went to hell and back again to bring us 3D gaming: John Carmack.
Oculus Connect 4 featured John Carmack’s fabled unscripted talk, a tradition which began in his days at ID software during the annual gathering of the faithful – Quakecon.
He was and remains the paradigmatic software engineer, wielding code to whatever end… Read More
Report from DCIA CEO Marty Lafferty

The DCIA salutes the US Department of Homeland Security (DHS) and the National Cyber Security Alliance (NCSA) on completing their fourteenth annual National Cybersecurity Awareness Month.
This year’s themes included Cybersecurity in the Workplace is Everyone’s Business, Protecting Critical Infrastructure from Cyberthreats, Simple Steps to Online Safety, The Internet Wants You to Consider a Career in Cybersecurity, and Today’s Predictions for Tomorrow’s Internet.
The importance of cybersecurity education and dissemination of private and public sector best practices cannot be overstated.
According to the Gimalto Breach Level Index, there were 918 data breaches during the first half of 2017 resulting in 1.9 billion data records being exposed – a 164% increase over the last six months of 2016 – and North America was the hardest-hit area, suffering 86% of the breaches – an increase of 23% — with the number of affected records jumping by 201%.
Highlights from Cybersecurity Awareness Month included confirmation that the US Cyber Command is being elevated to a full combatant command.
The Cyber Mission Force, a 6,200-person maneuver force of 133 teams, has reached initial operating capability, and work continues toward achieving final operating capability within a year.
For Cybersecurity Awareness Month, the Army focused on training and making cybersecurity an operational priority.
The Marine Corps has transformed the former Navy-Marine Corps internet into a unified network, is modernizing the civilian and military work force by upgrading old military occupational specialties for the information age, and investing in IT modernization.
The Navy established an office called CyberSafe to ensure proper protections, risk management, and investment in the right areas; and established its own standards for cybersecurity across the service.
In addition to the five DHS focus areas, another priority for the Air Force this year has been to extend its cybersecurity messaging into the field.
As Essye Miller, the Defense Department’s Deputy Chief Information Officer for Cybersecurity noted, “This is not just about the Defense Department and our mission, but about helping people understand that resilience in mission assurance is everybody’s responsibility at home or in the workplace.”
Share wisely, and take care.
Plans for New Cybersecurity Strategy
Excerpted from NextGov Report by Joseph Marks
 The Trump administration is planning to write a new cybersecurity strategy,
The Trump administration is planning to write a new cybersecurity strategy,
White House Homeland Security Adviser Tom Bossert said Tuesday, suggesting that the slew of Obama-era cyber plans and strategies are fast outliving their usefulness.
There’s no timeframe for when the strategy will launch, Bossert told reporters, but it will follow the broad outlines of a cybersecurity executive order President Donald Trump released in May.
“As soon as we’re prepared to put forward a strategy that will be beneficial to the government and the nation, we’ll do so,” Bossert said on the sidelines of a Washington cybersecurity conference hosted by Palo Alto Networks.
Like the executive order, the cybersecurity strategy is likely to be broken into three main components, Bossert said.
Those three components are: improving the security of federal government computer networks; leveraging government resources to better secure critical infrastructure, such as hospitals, banks and financial firms; and establishing norms of good behavior in cyberspace and punishing bad behavior.
The Obama administration launched a cyberspace policy review soon after taking office in 2009… Read More
Seven Ways IoT Is Reshaping the Internet
Excerpted from Report by Network World Report by Macej Kranz
 Two decades ago, the internet was the shiny new object in the room.
Two decades ago, the internet was the shiny new object in the room.
The Worldwide Web was just emerging as a new paradigm for communication and commerce, and the world brimmed with possibilities.
Today, not only has the internet fulfilled those nascent dreams, it has become the undisputed foundation of the digital age.
But now there’s a new paradigm in town – the internet of things (IoT).
For years, IoT has been growing up inside factories and oil platforms, in ships, trucks, and trains – quietly changing long-standing industrial processes.
It has made its way into virtually every industry – agriculture, aviation, mining, healthcare, energy, transportation, smart cities, and on and on.
IoT is no longer just the next phase of the internet – it’s fundamentally reshaping the internet as we know it… Read More
USTRANCOM Trailblazing Cloud Transition
Excerpted from America’s Navy Report by Michael Kleiman
 US Transportation Command (USTRANSCOM) is the first Department of Defense (DoD) organization to initiate migration of its cyber domain to a commercial cloud provider to improve mission assurance, while strengthening information technology efficiency and effectiveness. Last month, the first wave of five USTRANSCOM IT systems transitioned to a commercial cloud-based solution.
US Transportation Command (USTRANSCOM) is the first Department of Defense (DoD) organization to initiate migration of its cyber domain to a commercial cloud provider to improve mission assurance, while strengthening information technology efficiency and effectiveness. Last month, the first wave of five USTRANSCOM IT systems transitioned to a commercial cloud-based solution.
Relying heavily on the transportation industry to help accomplish its mission, USTRANSCOM faces significant challenges to provide transportation service providers timely information to carry out its tasks.
As a result of this, and in addition to the threat of a cyber-domain attack and the command’s aging electronic infrastructure, USTRANSCOM Commander Air Force Gen. Darren W. McDew subsequently directed the organization’s move to the cloud earlier this year.
The move will, among other things, allow USTRANSCOM to streamline and strengthen its security when working with industry partners while allowing them quicker access to vital transportation information.
In February, the command’s Cloud Center of Excellence (CCoE) stood up… Read More
Cisco & Google’s Mutual Interest in Cloud
Excerpted from NY Times Report by Don Clark
 Google and Cisco Systems, two trendsetters in different eras of the internet, are joining forces as the growth of cloud computing puts new pressure on big tech companies and leads to strange corporate bedfellows.
Google and Cisco Systems, two trendsetters in different eras of the internet, are joining forces as the growth of cloud computing puts new pressure on big tech companies and leads to strange corporate bedfellows.
The Silicon Valley giants on Wednesday announced a collaboration to help companies manage software and technology services that may run in their own data centers or in facilities operated by external cloud services.
Google, the largest unit of its parent, Alphabet, hopes to benefit from Cisco’s close ties to corporate customers as the search engine giant tries to catch up to Amazon, the market leader in cloud services, and Microsoft.
Cisco could also use some help.
The tech giant, which in 2000 briefly became the world’s most valuable publicly traded company when its computer networking equipment was used to build the internet, faces a serious threat from cloud services.
Companies that once spent heavily on new hardware from Cisco and other suppliers increasingly rent cloud services instead, with companies like Amazon doing most of the heavy lifting in the background.
“Every company that built an empire on selling equipment to companies to put in their data centers is feeling incredible pressure… Read More
ARM Unveils Plan to Secure the IoT
Excerpted from Silicon Angle Report by Mike Wheatley
 The potential of the internet of things (IoT) grows by the day as more devices and objects are connected to each other.
The potential of the internet of things (IoT) grows by the day as more devices and objects are connected to each other.
Just one problem: The vast majority of IoT devices appear to be woefully insecure.
With that in mind, UK-based chip designer ARM today unveiled its vision for protecting more than a trillion connected devices, with security embedded deep into the silicon that powers them.
What ARM is proposing is a common industry framework it calls the Platform Security Architecture, which lays out a secure foundation for every connected device.
The company’s proposal has been endorsed by a wide range of cloud, hardware and chip manufacturing partners, including the likes of Google, Cisco Systems, and Baidu.
With its proposal, ARM is attempting to tackle three major problems with the IoT today.
The first is that most IoT devices cannot easily be updated with new software to patch known vulnerabilities… Read More
Complexity, Compliance, Containerization
Excerpted from Help Net Security Report
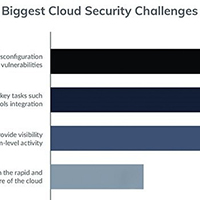 A new report by Threat Stack and ESG sheds light on the security and business challenges that accompany the growth of public cloud environments and containers.
A new report by Threat Stack and ESG sheds light on the security and business challenges that accompany the growth of public cloud environments and containers.
Overall, the findings show a gap in security and compliance readiness across fast-growing cloud and container environments.
31% of those surveyed said that they are unable to maintain security as their cloud and container environments grow – a startling figure in the context of today’s threat landscape.
As a result, 62% say that they’re seeking greater visibility into their public cloud workloads.
57% of those surveyed reported significant delays in the sales cycle due to trouble meeting customer security requirements, while 59% reported the same issue around meeting customer compliance requirements.
Accordingly, nearly one in three of all investments in cloud security are now driven by the need to satisfy customer and partner compliance demands.
40% of respondents reported they will have hybrid environments within a year – an increase from the current 12%… Read More
How to Keep Data Safe in the Cloud
Excerpted from The Week Report by Harold Maass
 Cloud storage and cloud computing are booming.
Cloud storage and cloud computing are booming.
Worldwide public cloud service revenues are expected to grow by 18.5 percent in 2017 to a whopping $260 billion – and there’s no reason to think that pace will slow down any time soon.
It’s not hard to see why business is booming.
The cloud offers families a convenient way to store everything from pictures to documents, and provides individuals and businesses efficient new ways to work together, handle services such as payroll or online software, and share what they’re doing via remote networks of servers.
But there’s a catch.
All that data collected in a shared space makes a prime target for hackers.
And despite the clear risk, RedLockfound in its recent Cloud Security Trends report that 81 percent of organizations are not doing enough to protect their cloud environments. Here’s a quick look at how data in the cloud is vulnerable… Read More
Building a Digital Defense against Dangers
Excerpted from FBI Tech Tuesday Report by Beth Anne Steele
 In recent years, we have seen an increase in the number of small and medium-sized businesses using cloud computing services.
In recent years, we have seen an increase in the number of small and medium-sized businesses using cloud computing services.
If your business uses a cloud computing service, your data is stored on hardware owned by and housed at a different company.
You access your information via a web-based service that you can log into from any of your company’s computers.
This system has its advantages.
For example, it shifts the responsibility of buying and maintaining hardware and software from your business to your cloud computing service provider.
You only need the right software and some computers from which you can run it.
However, cloud computing also comes with its own set of risks.
The two biggest concerns? Losing access to your data and someone else stealing your data… Read More
It’s Mostly about Protecting Mobile Devices
Excerpted from Computing Report by Tom Allen
 “It’s ironic,” says Rich Campagna, CEO at cloud access security broker (CASB) Bitglass, “but cloud security has become mostly about mobile device protection.
“It’s ironic,” says Rich Campagna, CEO at cloud access security broker (CASB) Bitglass, “but cloud security has become mostly about mobile device protection.
If there are 15,000 devices able to access your network and you don’t own 10,000 of them, that’s a problem.”
Campagna is talking to us about the proliferation of the bring-your-own-device trend: a thorn in the side of many IT departments, who cannot manage security on personal computers and mobiles.
As the cloud has grown, so has the number of workers accessing sensitive company data through their own devices. Thankfully there have been massive investments in cloud security by vendors: Microsoft, for example, spends over $1 billion annually.
Those investments mean that the fears over massive, industry-wide hacks of cloud vendors’ databases haven’t materialized yet.
Instead, most of the threats that affect data in the cloud stem from human error: poor usage or insufficient configuration of apps. As an example, take the Amazon S3 bucket leaks, which stem from unsecured data stores… Read More
Feds Warn of Infrastructure Cyberattacks
Excerpted from The Hill Report by Josh Delk
 The Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) issued a joint statement on Friday warning of an increased danger posed to infrastructure sectors by a malicious “multi-stage intrusion campaign,” which the agencies warned had successfully compromised several of their security networks.
The Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) issued a joint statement on Friday warning of an increased danger posed to infrastructure sectors by a malicious “multi-stage intrusion campaign,” which the agencies warned had successfully compromised several of their security networks.
The analysis points to cyberattack campaigns going on since at least May 2017 that the agencies said have been targeting the aviation, energy, and nuclear industries.
The agencies did not name any specific networks that had been compromised by the attacks.
Hackers reportedly used emails and malicious websites in a phishing campaign to obtain the credentials necessary to access and sabotage the networks.
According to the report, the campaigns first focus on “staging targets,” third-party and peripheral organizations tied to the primary targets which hackers then use to house their malware for attacks.
The agencies said that the hackers were targeting the company-controlled sites of specific agencies, to access information on equipment and organizational designs and “control-system capabilities” that could be used to harm the organizations… Read More
Experts Warn of Impending Botnet Hurricane
Excerpted from GovTech Report by Tim Johnson
 Just as hurricane trackers chart storms in the Atlantic before they make landfall, cybersecurity researchers track viral infections that threaten mayhem. They’ve found a doozy.
Just as hurricane trackers chart storms in the Atlantic before they make landfall, cybersecurity researchers track viral infections that threaten mayhem. They’ve found a doozy.
A massive zombie robotic network, or botnet, has expanded to infect “an estimated million organizations” and could bring corners of the internet to its knees, an Israeli cybersecurity company, Check Point Software, says.
“The next cyber hurricane is about to come,” Check Point says.
Several cybersecurity researchers Monday confirmed Check Point’s findings, saying the botnet could replicate, and perhaps dwarf, the Mirai botnet that almost exactly a year ago took down major websites on the Atlantic Coast, crippling a part of the internet’s backbone and slowing traffic to a crawl.
The botnet, which has been named either “Reaper” or “IoTroop,” was first detected in mid-September. A Chinese cybersecurity firm, Qihoo 360, says the botnet is swelling by 10,000 devices a day, forcibly recruiting foot soldiers in an ever-larger invisible rogue army.
Cybercrime gangs form botnets by infecting internet-enabled devices, often wireless cameras or routers with weak security features… Read More
2017 Storage Visions Conference Highlights
Excerpted from Storage Visions Report by Thomas Coughlin
 The DCIA co-sponsored 2017 Storage Visions Conference (SV 2017) was held Monday, October 16 in Milpitas, CA.
The DCIA co-sponsored 2017 Storage Visions Conference (SV 2017) was held Monday, October 16 in Milpitas, CA.
358 people registered for the event that featured insightful sessions and cutting-edge exhibits.
39% of attendees were director level or higher. 24% were engineers.
The 2017 Storage Visions Conference theme was “New Visions for Digital Storage” and it brought together the vendors, end users, researchers and visionaries that will meet the growing demand for digital storage for all aspects of unstructured data.
The 2017 conference features keynote talks by Dreamworks, Intel, Quantum, Micron and Red Hat. Following are some highlights from the conference keynotes:
Tim Long from Micron spoke about their use of AI and connected devices to drive the next generation of semiconductor manufacturing, version 4.0.
This new type of factory can predict failures and organize servicing of manufacturing equipment using deep learning of die defects… Read More
Coming Events of Interest
Mobility Unmanned — November 1st and 2nd in Washington, DC. Providing key stakeholders the unique opportunity to explore cutting-edge autonomous technology and examine the emerging regulatory landscape governing the commercial use of unmanned vehicles in all sectors – air, land, and sea.
Industrial Internet of Things (IoT) Europe — November 7th and 8th in Munich, Germany. IoT Europe will bring together forward-thinking companies from the manufacturing, energy, and transportation sectors to pave the way for the Industrial IoT revolution.
Government Video Expo & National Drone Show — November 28th-30th in Washington, DC. The 22nd annual GVE will feature a full exhibit floor with numerous training options, free seminars, keynotes, networking opportunities, and five new educational pavilions.
CES — January 9th through 12th in Las Vegas, NV. Organized by the Consumer Technology Association, this large annual event typically hosts presentations of new products and technologies in the consumer electronics industry.
Industry of Things World USA 2018 — March 7th through 9th in San Diego, CA will bring together the entire industrial internet of things (IIoT) ecosystem for this third annual event featuring three days of high level networking and learning.
Delivery of Things World 2018 — April 23rd and 24th in Berlin, Germany. Meet the most influential DevOps practitioners and experts and discuss what DevOps means for your business.
