In This Issue
- Cybersecurity Market
- Criminal Infiltration
- OPM Promises Protect
- Report from the CEO
- Telefonica New Pay TV
- MS Edge, HTML5, DRM
- Cloud Changes Media
- DRM Storage Patents
- Higher-Capacity Chip
- Cloud Market Growth
- Public or Private Cloud
- Driving Infrastructure
- Unicorn: Fitting Label
- Amazon Mobile Cloud
- Big Data – Big Media?
- Telefonica Vivo for IoT
- Coming DCIA Events
Worldwide Cybersecurity Market Continues Upward Trend
Excerpted from CSO Online Report
 The worldwide cybersecurity market continues to grow and grow as defined by market sizing estimates that range from $75 billion in 2015 to $170 billion by 2020.
The worldwide cybersecurity market continues to grow and grow as defined by market sizing estimates that range from $75 billion in 2015 to $170 billion by 2020.
The data comes from consolidated estimates by IT industry research and analyst firms, including these figures:
A report by Visiongain, a business intelligence firm in London, indicates that the global cybersecurity market is set to be worth $75.4 billion in 2015, as high-demand continues for information security solutions.
Research firm Gartner projects that the world will spend $101 billion on information security in 2018.
The cybersecurity market is estimated to grow to $170 billion by 2020, at a compound annual growth rate (CAGR) of 9.8% from 2015 to 2020, according to a report from Markets and Markets. The aerospace, defense, and intelligence vertical continues to be the largest contributor to cybersecurity solutions.
North America and Europe are the leading cybersecurity revenue contributors, according to a report from TechSci Research in Burnaby, Canada. Asia-Pacific is rapidly emerging as a potential market for cybersecurity solution providers… Read More
How Cyber-Criminals Infiltrate the Enterprise
Excerpted from CIO Insight Report by Karen Frenkel
 A new study reveals that cyber-criminals targeted five out of six large companies in 2014, a 40% increase since 2013.
A new study reveals that cyber-criminals targeted five out of six large companies in 2014, a 40% increase since 2013.
Hackers are also using deceptive new tactics to infiltrate corporate networks, hijacking infrastructures and turning them on enterprises to evade detection, according to Symantec’s study, Internet Security Threat Report, Volume 20.
Non-targeted attacks still comprise the majority of malware, increasing by 26% this year. There were 317 million new pieces of malware created and 1 million new threats released daily.
“Attackers don’t need to break down the door to a company’s network when the keys are readily available,” said Kevin Haley, Director of Symantec Security Response.
“Attackers trick companies into infecting themselves by trojanizing software updates to common programs and patiently waiting for their targets to download them —giving attackers unfettered access to the corporate network.”
The report also finds digital extortion on the rise, with ransomware attacks growing 113 percent in 2014.
Cyber-criminals are inherently lazy, said Haley, because they prefer automated tools and rely on unwitting consumers to do their dirty work… Read More
OPM Promises to Protect Hacked Employees
Excerpted from ZDNet Report by Steven Vaughan-Nichols
 The more we find out about the US Office of Personnel Management (OPM) hack, the worse it looks.
The more we find out about the US Office of Personnel Management (OPM) hack, the worse it looks.
We’re moving into science-fiction disaster territory as the OPM admits that more than 21 million employees’ personal records have been stolen.
But, the OPM has a new, improved plan to protect their records.
The 21 million number is even higher than the FBI’s leaked 18 million figure.
On an OPM site, the agency revealed the most likely victims are those who “underwent a background investigation through OPM in 2000 or afterwards.”
In short, if you filled out a form SF-86, Questionnaire for National Security Positions; SF-85, Questionnaire for Non-Sensitive Positions; or SF-85P, Questionnaire for Public Trust Positions, your records are toast.
Or, as OPM put it, “It is highly likely that you are impacted by the incident involving background investigations.” If you underwent a background investigation prior to 2000, you still may be impacted, but it is less likely… Read More
Report from DCIA CEO Marty Lafferty
 Companies contacting the DCIA for information technology (IT) support increasingly are seeking resources with expertise in cybersecurity.
Companies contacting the DCIA for information technology (IT) support increasingly are seeking resources with expertise in cybersecurity.
There’s no question that data scientists and defenders of digital systems are in enormous demand today.
The massive cybersecurity attack in June that compromised Office of Personnel Management (OPM) records of more than twenty-one million current and former federal employees underscored the vulnerability of public as well as private sector systems to such incursions.
With no foreseeable abatement, well-qualified cybersecurity professionals need to be brought on board as soon as possible with the mission of developing enhanced infrastructure that will withstand cyber assaults.
The Cybersecurity Workforce Assessment Act of 2014 required evaluation of the readiness, capacity, and management of Department of Homeland Security (DHS) resources in this area.
The DHS Cybersecurity Workforce Recruitment and Retention Act, also passed in 2014, was intended to help DHS develop additional resources by authorizing the creation of competitive positions and the monitoring of progress.
This year, DHS added its Honors Program Cyber Student Volunteer Initiative as another step forward.
While additional cybersecurity legislation has stalled in the US Senate during 2015, government and industry collaboration is moving ahead.
On July 7th, the US Chamber of Commerce announced its new Cybersecurity Leadership Council (not to be confused with the Council on Cybersecurity) to promote relevant best practices.
Chairman Howard Schmidt set as the council’s priority the mitigation of cyber risks through cross-sector information-sharing, public and private partnerships, and the improvement of cyber hygiene in organizations of all sizes.
The new council is made of up a broad representation of businesses and associations.
The work of the DCIA’s new Advancement of Digital Rights Management (ADRM) Working Group, with its focus on improving the protection of high-value data and the related consumer experience will be applicable in this space as well.
Encryption and authentication are the core functionalities of DRM, and these are exactly what must be advanced to secure the digital ecosystem.
In the coming era, cybersecurity experts will become increasingly important to organizations in both government and industry.
The DCIA will continue to do our part to encourage, promote, and support their work. Share wisely, and take care.
Telefonica Integrates Canal+ in New Pay TV Offering
Excerpted from Digital TV Europe Report
 Telefonica is offering a basic package of 80 channels a range of on-demand films and programs, a revamped Canal+ and the Yomvi under the brand Movistar+.
Telefonica is offering a basic package of 80 channels a range of on-demand films and programs, a revamped Canal+ and the Yomvi under the brand Movistar+.
Viewers will be able to add sports, movies and series options for 20, 8, and 5 euros/month respectively. Channels will be available on an a la carte basis for 5 euros, while bullfighting channel Canal+ Toros will be available for 20 euros.
Canal+-branded services on offer will include the new Canal+ Series Xtra channel along with Canal+ Series and movie service Canal+ Estrenos.
Telefonica is also providing cloud DVR, HD, and TV on-demand including a seven-day catch-up service available across devices.
Movistar+ will be available from tomorrow to existing Canal+ customers and Movistar customers with the Fuision TV para Todos option, and will gradually be extended to all Movistar TV customers.
Optional channels on top of the basic package include the two Canal+ Series channels for 5 euros, Canal+ Estrenos for 9 euros… Read More
Microsoft Edge, HTML5, and DRM
Excerpted from Mil-Tech Report
 Microsoft is building its new browser, Edge, with the intention of avoiding many of the flaws that plagued Internet Explorer over its long and tumultuous life.
Microsoft is building its new browser, Edge, with the intention of avoiding many of the flaws that plagued Internet Explorer over its long and tumultuous life.
Part of this involves moving away from plug-ins, and Edge will not support ActiveX.
Instead, it’s focusing on interoperable media, and that means non-plug-in video players that meet HTML5 specs.
Of course, not all video players want to disseminate their content for free, which means: DRM.
Microsoft’s Edge team has published a new post explaining how it will be handling support for DRM and “premium media” in the new browser.
It says, “Windows 10 and Microsoft Edge support DASH, MSE, EME, and CENC natively, and other major browsers ship implementations of MSE and CENC compliant EME.
This support allows developers to build plug-in free web video apps that run across a huge range of platforms and devices, with each MSE/EME implementation built on top of a different media pipeline and DRM provider… Read More
Cloud Computing Changes Media Game
Excerpted from Accenture Report
 A fundamental shift is triggering major disruptions for broadcasters, calling for the scalability, cost flexibility, and agility of cloud computing.
A fundamental shift is triggering major disruptions for broadcasters, calling for the scalability, cost flexibility, and agility of cloud computing.
Advances in technology and consumer behavior are driving a transformation in the way video content is delivered to consumers.
The change involves a migration away from traditional broadcasting models and platforms toward digital distribution over the Internet to a widening array of connected devices.
This fundamental shift is triggering major disruptions for broadcasters, calling for the scalability, cost flexibility, and agility of cloud computing.
Disruptive forces require today’s established broadcasters not just to adopt a new approach to technology, but also to navigate a radical shift in their embedded culture and skill-sets.
In doing so, they will equip themselves to compete more effectively with agile over-the-top (OTT) entrants… Read More
DRM Storage Patents Available from ICAP
Excerpted from Benzinga Report
 ICAP Patent Brokerage announces for sale patents disclosing a biometric digital rights management (DRM) system with value along the entire chain of creation, encryption, and distribution of digital media, available from Divan Industries.
ICAP Patent Brokerage announces for sale patents disclosing a biometric digital rights management (DRM) system with value along the entire chain of creation, encryption, and distribution of digital media, available from Divan Industries.
This portfolio is offered as part of the Internet of Things IP Auction, with a bidding deadline of July 30th.
“With priority dates from 2000, this is a valuable portfolio for DRM, media content delivery, encryption, and biometric companies,” said Dean Becker, CEO of ICAP Patent Brokerage.
In general, this portfolio relates to DRM for distribution of digital media content.
The portfolio finds application along the entire value chain of creation, encryption, and distribution of digital media such as streaming video and audio.
Transmission of such private digital content over the Internet is problematic, even when the content is encrypted, given the ever-increasing skills of hackers.
Patents in the portfolio provide greater security for content providers who may distribute their content… Read More
IBM Discloses Much Higher-Capacity Chip
Excerpted from NY Times Report by John Markoff
 IBM said on Thursday that it had made working versions of ultra-dense computer chips, with roughly four times the capacity of today’s most powerful chips.
IBM said on Thursday that it had made working versions of ultra-dense computer chips, with roughly four times the capacity of today’s most powerful chips.
The announcement, made on behalf of an international consortium led by IBM, the giant computer company, is part of an effort to manufacture the most advanced computer chips in New York’s Hudson Valley, where IBM is investing $3 billion in a private-public partnership with New York State, GlobalFoundries, Samsung, and equipment vendors.
The development lifts a bit of the cloud that has fallen over the semiconductor industry, which has struggled to maintain its legendary pace of doubling transistor density every two years.
Intel, which for decades has been the industry leader, has faced technical challenges in recent years.
Moreover, technologists have begun to question whether the longstanding pace of chip improvement, known as Moore’s Law, would continue past the current 14-nanometer generation of chips.
Each generation of chip technology is defined by the minimum size of fundamental components that switch current at nanosecond intervals… Read More
Cloud IT Infrastructure Market Grows 25%+ in Q1
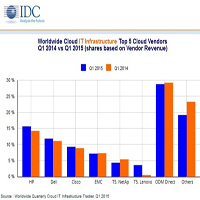 According to the International Data Corporation (IDC) report entitled Worldwide Quarterly Cloud IT Infrastructure Tracker, vendor revenue from sales of infrastructure products (server, storage, and Ethernet switch) for cloud IT, including public and private cloud, grew by 25.1% year over year to nearly $6.3 billion in the first quarter of 2015 (Q1-2015).
According to the International Data Corporation (IDC) report entitled Worldwide Quarterly Cloud IT Infrastructure Tracker, vendor revenue from sales of infrastructure products (server, storage, and Ethernet switch) for cloud IT, including public and private cloud, grew by 25.1% year over year to nearly $6.3 billion in the first quarter of 2015 (Q1-2015).
This was the second highest growth in the five quarters in which IDC has tracked year-over-year revenue and the second largest in terms of total spending in nine quarters of tracking.
Cloud IT infrastructure spending climbed to nearly 30% of overall IT infrastructure spending in Q1-2015, up from 26.4% a year ago.
Revenue from infrastructure sales for private cloud grew 24.4% year over year to $2.4 billion while sales for public cloud grew 25.5% to $3.9 billion.
In comparison, the non-cloud IT infrastructure segment increased by 6.1% in the first quarter, largely driven by increased sales of servers while storage sales declined and sales of Ethernet switches grew just by 1%.
All three technology markets showed strong year-over-year growth in both private and public cloud segments… Read More
Public or Private Cloud Storage? Have Both
Excerpted from CloudTech Report by James Bourne
 A recent survey from cloud storage and data protection hardware provider CTERA Networks found that while employees at more than half of organizations use public file, sync, and share services, almost three quarters said they were looking for an alternative.
A recent survey from cloud storage and data protection hardware provider CTERA Networks found that while employees at more than half of organizations use public file, sync, and share services, almost three quarters said they were looking for an alternative.
The report recognized what CTERA highlights as a growing interest and need for enterprise-grade, private cloud storage solutions.
Box portrays itself as primarily an enterprise player, most recently announcing a partnership with IBM, while the number of Dropbox business users has recently crept over eight million.
Like it or not, these services continue to gain wide adoption.
Rani Osnat, VP, Strategic Marketing at CTERA, told CloudTech there were few surprises in the survey, released earlier in June, but there is room for both public and private.
“There are two ways you can look at these results,” he said… Read More
Cloud to Drive Nearly Half of IT Infrastructure
Excerpted from The Platform Report by Timothy Morgan
 Utility-style computing was not invented by Amazon Web Services (AWS), but you could make a credible argument that it was perfected by the computing arm of the retail giant.
Utility-style computing was not invented by Amazon Web Services (AWS), but you could make a credible argument that it was perfected by the computing arm of the retail giant.
The information technology (IT) industry has been trying to evolve towards what we now call cloud computing for quite some time, which was made possible by waves of hardware virtualization that started on mainframes, trickled down to Unix and proprietary systems almost two decades ago, and cascaded onto X86 machinery a decade ago.
While cloud seems ordinary now, oddly enough it is still not the dominant architecture driving the IT industry.
At least not yet, anyway.
If the hyperscalers like Google and cloud builders like AWS have taught us anything, it is to relentlessly measure, correlate, and analyze.
To help understand what is going on in the IT sector as far as cloudy infrastructure goes, the box counters at IDC late last year started up a new tracker service that dices and slices sales of core infrastructure — servers, storage, and switches… Read More
Unicorn: A Fitting Label for Its Time and Place
Excerpted from NY Times Report by Farhad Manjoo
 Aileen Lee tried a few lesser terms before she hit on “unicorn.”
Aileen Lee tried a few lesser terms before she hit on “unicorn.”
One was “home run.” Another was “megahits.”
Neither quite worked for what she was going for — an unusual, mysterious word to describe what, in the tech industry, was an unusual, mysterious phenomenon: American software companies that had achieved a valuation of at least $1 billion.
It was the fall of 2013, and Ms. Lee, a longtime venture capitalist, had recently started her own firm, Cowboy Ventures.
Ms. Lee’s team had conducted a study of the start-up market over the previous decade, and she was preparing to publish the findings in an article for TechCrunch, an online publication.
But she was stuck on nomenclature. While Silicon Valley had been trying to separate tech winners from losers for decades, it had never really coined a name for the kind of start-ups the industry most treasured.
“What’s the word to describe the thing that all of us are trying to do,” Ms. Lee recalled in a recent interview, “which is to found or work for or invest in a company that is the winner of all winners?” Then the word came to her: Unicorn. “It felt right,” she said… Read More
Amazon Releases New Mobile Cloud Drive Apps
Excerpted from Top Tech News Report by Dan Heilman
 The new mobile cloud drive apps from Amazon are here, but, it seems, just barely.
The new mobile cloud drive apps from Amazon are here, but, it seems, just barely.
The company’s new Cloud Drive apps for iOS and Android bring the company one step closer to providing a complete mobile cloud storage solution.
The new apps let users view files and folders, preview documents and photos, play videos and music, and share files with other apps.
The Cloud Drive release is meant as an all-purpose complement to the photo- and music-specific apps that Amazon already offers, and is aimed at the user who wants greater productivity.
Cloud Drive provides users with folder views of everything they have stored in Amazon’s cloud.
Files can be viewed, shared or linked to — and files like PDFs, images, spreadsheets, and more are supported.
In addition, stored music and videos can be streamed from Cloud Drive.
That way, users can delete photos from their phones, for example, and still see them via the Cloud Drive iOS or Android app… Read More
Big Data, Big Deal! What about Big Media?
Excerpted from Xaxis Blog by Ekapat Chareonlarp
 At Xaxis, we see over 300 million unique IDs and billions of associated impressions traded programmatically daily.
At Xaxis, we see over 300 million unique IDs and billions of associated impressions traded programmatically daily.
We know which impressions we want and make the buying decisions in real time.
But wait… while the adrenaline rush of reaching the height requirement for this ride was overwhelming, actually getting on the ride was a different matter entirely.
I call this bad boy “Big Media” (like a rollercoaster) because it comes with a steep vertical drop of viewability, the loopty-loops of KPIs and attribution models that are all engineered perfectly for brand safety to keep everyone on track.
But enough with the analogy, what is “Big Media” really about you ask? Allow me to explain.
2005 was the year Roger Mougalas from O’Reilly Media coined the term “Big Data.”
This was also the year Hadoop emerged attempting to index the entire web.
Internet-based media and Big Data were like twins separated at birth… Read More
Telefonica Vivo and Jasper Launch IoT Platform
Excerpted from MarketWatch Report
 With the largest 3G and 4G network in Brazil, Telefonica Vivo is now launching the Vivo M2M Control Center Platform for global corporate clients in Brazil.
With the largest 3G and 4G network in Brazil, Telefonica Vivo is now launching the Vivo M2M Control Center Platform for global corporate clients in Brazil.
The platform, provided by Jasper, a global Internet of Things (IoT) platform leader, enables businesses in any market to easily deploy, manage and monetize IoT services.
With the Vivo M2M Control Center platform, Telefonica Vivo now offers a turnkey solution for Brazilian enterprises in any industry — including utilities, automotive, security, healthcare, consumer electronics, smart cities and more.
The Vivo M2M Control Center can be easily configured for the unique needs of any business model, providing businesses with real-time control and visibility of their connected devices, in addition to mobile service management, support diagnostics and flexible billing required to grow a successful connected services business.
Control Center also features Global SIM capabilities, enabling enterprises to establish processes where data communication, voice and SMS use the same hardware solution in any country.
Pioneers in Brazil Telefonica Vivo is the first operator in Brazil to use the Telefonica Global SIM capabilities of Control Center… Read More
Coming Events of Interest
ADRM Working Group Meeting — July 30th via Global Videoconference. Contact the DCIA for information about joining the group and attending the meeting that will focus on interoperability among DRM platforms and simplifying DRM implementation.
Cloud Computing Boot Camp — July 30th in Washington, DC. Designed for small-to-medium businesses (SMBs) and their counterparts in government agencies and healthcare organizations whose responsibilities include evaluating, purchasing, and implementing cloud-based solutions.
The Internet of Things (IoT) Show — September 2nd-23rd in Singapore. The IoT Show will facilitate new collaborations and partnerships as well as generate new ideas and thinking. The IoT Show is about getting the prototypes out of the lab and into the market.
Digital Hollywood Fall — October 19th-22nd in Marina Del Rey, CA. The future of the entertainment industry. Digital Hollywood debuted in 1990 and has from its start been among the leading trade conferences in its field.
2015 US Cyber Crime Conference — November 18th-20th in National Harbor, MD. This is the only event of its kind that provides both hands-on digital forensics training and an interactive forum for cyber professionals to network.
Internet of Things World Forum (IoTWF) — December 6th-8th in Dubai, IoTWF is an exclusive event that brings together the best and brightest thinkers, practitioners, and innovators from business, government, and academia to accelerate the market adoption of the Internet of Things.
