In This Issue
- Senate CISA Delayed
- Co Cyber-Capabilities
- Privacy Bill of Rights
- Report from the CEO
- US Suspects Russia
- Pentagon: Deterrents
- Smart Gadget Hacking
- Battery May Track You
- Google on Biz Security
- Cyber-Oversight Bill
- Alibaba: Go Quantum
- GE’s Industrial Cloud
- Research Science Net
- SMEs Mobile & Cloud
- Cloud Comp Benefits
- Hybrid Cloud Potential
- Coming DCIA Events
Cybersecurity Bill Delayed in Senate
Excerpted from NY Times Report by Jennifer Steinhauer
 The US Senate headed into its August recess on Wednesday without voting on a cybersecurity bill, adding it to a contentious to-do list for September that includes a push to disapprove the Iran nuclear deal and a spending fight mired in abortion politics.
The US Senate headed into its August recess on Wednesday without voting on a cybersecurity bill, adding it to a contentious to-do list for September that includes a push to disapprove the Iran nuclear deal and a spending fight mired in abortion politics.
The delay of the cybersecurity bill followed a pattern that has marked the Senate since the Republicans took control this year.
Senator Mitch McConnell of Kentucky, the majority leader, has struggled to accelerate the legislative track while still permitting members of both parties to amend bills on the floor, as he has repeatedly promised to do.
In addition, Republicans’ return to the thorny abortion debate — this time by inserting a bill to defund Planned Parenthood into the calendar ahead of the cybersecurity measure — left too little time to finish the computer security legislation.
Presidential politics has also frequently played a part, with four Republican senators set to participate in primary debates on Thursday. Mr. McConnell tried this summer to attach the cybersecurity measure to a broader defense bill… Read More
Give Companies Offensive Cyber-Capabilities
Excerpted from IT World Report by Grant Gross
 Many US businesses have limited options for defending their IP networks, and the nation needs to develop more “aggressive” capabilities to discourage cyber-attacks, said Juan Zarate, the former Deputy National Security Advisor for Counter-terrorism during President George W. Bush’s administration.
Many US businesses have limited options for defending their IP networks, and the nation needs to develop more “aggressive” capabilities to discourage cyber-attacks, said Juan Zarate, the former Deputy National Security Advisor for Counter-terrorism during President George W. Bush’s administration.
The US government should consider allowing businesses to develop “tailored hack-back capabilities,” Zarate said Monday at a forum on economic and cyber-espionage hosted by think tank the Hudson Institute.
The US government could issue cyber-warrants, giving a private company license “to protect its system, to go and destroy data that’s been stolen or maybe even something more aggressive,” he added.
Zarate, now a senior counselor focused on sanctions at anti-terrorism think tank the Foundation for Defense of Democracies, called for better cybersecurity tools as well, but suggested a new way of thinking about the tools “that not only puts us on the defensive, but also on the offensive.”
With huge new breaches reported in the US every few days, the current response against cyber-attacks isn’t working, said Zarate and Steven Chabinsky, Chief Risk Officer at cybersecurity firm CrowdStrike… Read More
A Consumer Privacy Bill of Rights
Excerpted from Pulse Report by Jonathan Baskin
 I’m not sure there’s ever been clearer evidence of a crisis.
I’m not sure there’s ever been clearer evidence of a crisis.
Most company privacy policies are purposefully complicated and vague, even if they’re presented with friendly language and happy icons.
Technology innovation is on an incessant march to add new ways to collect and apply user data, the operation or implications of which few users fully understand.
Hackers have robbed private information from the US government and leading sex sites, not to mention top retailers and insurers, yet there have been no overt changes in how this info is stored.
A new generation of wearable technology promises to upload users’ every breath and movement into a cloud that is available to many, whether legally or otherwise.
And we wonder why most people feel that they’ve lost their privacy, can’t control how it’s exploited and, as a result, feel less trusting of the brands with which they do business and suspicious of their governments… Read More
Report from DCIA CEO Marty Lafferty
 The DCIA joined with thirty other trade associations and human rights organizations this week in sending a message to US Senate leadership opposing Section 603 of the Intelligence Authorization Act of 2016 (S. 1705).
The DCIA joined with thirty other trade associations and human rights organizations this week in sending a message to US Senate leadership opposing Section 603 of the Intelligence Authorization Act of 2016 (S. 1705).
Section 603 would incentivize providers of Internet communications services to over-report to government on activities of their users in order to avoid violating the law.
It would risk bringing wholly innocent people under the scrutiny of federal authorities.
Section 603 represents a clear invasion of privacy and a certain threat to freedom of expression.
Cloud-based services including social networks and user-generated content offerings support online expression and exchange of information that reflects a tremendous diversity.
They represent a vibrant manifestation of the Fourth Amendment in the digital age and an enormous benefit of a free society.
They also make it impossible for a provider to accurately judge the context of every communication, or the intent of every speaker whose voice is conveyed through these services.
Whether a given comment is a true threat, the expression of emotion, or simply a joke among friends is a determination that providers are ill-suited to make.
And more importantly, the content of private communications — emails, text messages, social media posts, files, and photos stored in the cloud — should not be accessible without a warrant obtained through due process.
Under Section 603, not only is no warrant required, but also no notice is given to users.
Individuals would have no opportunity to contest allegations, and trust in US-based Internet services would be seriously eroded around the world.
Moreover, Section 603 fails to provide limits on the use of reported information, and it contains no safeguards against abuse.
The privacy and security of cloud-based service offerings are essential attributes for their continuing adoption; and switching to non-US-based alternatives is not difficult.
Section 603 won’t work, with providers flooding the government in an overwhelming glut of false leads and inaccurate reports, wasting law-enforcement resources attempting to analyze it.
Meanwhile, bad actors will simply switch to offshore services to avoid being reported.
Join us in telling the Senate that we don’t need Section 603.
Providers are already lawfully entitled to report evidence related to the commission of a crime and in an emergency.
Please contact your Senator with the request to remove Section 603 from the Intelligence Authorization Act. Share wisely, and take care.
US Suspects Russia in Hack of Pentagon Network
Excerpted from Washington Post Report by Craig Whitlock and Missy Ryan
 US military officials said Thursday that they suspect Russian hackers infiltrated an unclassified Pentagon e-mail system used by employees of the Joint Chiefs of Staff, the latest in a series of state-sponsored attacks on sensitive US government computer networks.
US military officials said Thursday that they suspect Russian hackers infiltrated an unclassified Pentagon e-mail system used by employees of the Joint Chiefs of Staff, the latest in a series of state-sponsored attacks on sensitive US government computer networks.
The electronic intrusion was detected about July 25th, officials said.
The Pentagon immediately disabled the e-mail system, which is used by about 4,000 military and civilian personnel, in an attempt to contain the damage.
The network remains offline, although officials said they hoped to restart it in the coming days.
The Defense Department disclosed the attack shortly after it occurred, but only in recent days have investigators traced it to Russia.
Officials said the complexity and advanced nature of the hack strongly suggested that a foreign government was responsible.
“This attack was fairly sophisticated and has the indications of having come from a state actor such as Russia… Read More
Pentagon Seeks Strong Cyber-Weapons to Deter Attacks
Excerpted from LA Times Report by Patrick Semansky
 The nation that brought the world the mushroom cloud is now hard at work on a new project: coming up with cyber-weapons so strong that their very existence would deter foreign governments from attacking US databases and crucial computer systems.
The nation that brought the world the mushroom cloud is now hard at work on a new project: coming up with cyber-weapons so strong that their very existence would deter foreign governments from attacking US databases and crucial computer systems.
The idea is to try to adapt a military concept that helped keep the world safe from nuclear bombings during the Cold War to the digital battlefield of the 21st century.
For four decades, the US and the Soviet Union built up massive stockpiles of nuclear weapons but never used them.
Part of the reason was the belief on both sides that any attack would be met with an equally devastating counterstrike.
Military planners called the idea mutually assured destruction. Today, plans for “cyber-deterrence” aim to develop something analogous for the digital era.
National security officials have recently stepped up their public warnings about the need to build such a deterrent.
“If we do nothing, then one of the potential unintended consequences of this could be, does this send a signal to other nation states… Read More
Smart Gadgets from Guns to Cars Ripe for Hacking
Excerpted from Business Insider Report by Glenn Chapman
 Hackers are not just after your computer: connected devices from cars to home security systems to sniper rifles are now targets for actors looking to steal or cause mischief.
Hackers are not just after your computer: connected devices from cars to home security systems to sniper rifles are now targets for actors looking to steal or cause mischief.
The rapid growth in the Internet of Things (IoT) has opened up new opportunities for cyber-attacks and new markets for cyber-defenders.
This is among the hot topics at a Black Hat computer security conference that kicks off in Las Vegas, NV on Sunday and an infamous Def Con hacker gathering that follows.
Early glimpses have been provided of scheduled presentations about how to commandeer control of some Chrysler Fiat vehicles or accurately retarget self-aiming sniper rifles.
“The IoT is definitely one of the big new frontiers,” said Christopher Kruegel, Co-Founder of cyber security firm Lastline and a professor of computer science at a state university in Southern California.
Fiat Chrysler issued a safety recall for 1.4 million US cars and trucks in July after hackers demonstrated that they could take control… Read More
Your Laptop or Phone Battery Could Track You Online
Excerpted from BetaNews Report by Mark Wilson
 Is the battery in your smartphone being used to track your online activities?
Is the battery in your smartphone being used to track your online activities?
It might seem unlikely, but it’s not quite as farfetched as you might first think.
This is not a case of malware or hacking, but a built-in component of the HTML5 specification.
Originally designed to help reduce power consumption, the Battery Status API makes it possible for websites and apps to monitor the battery level of laptops, tablets, and phones.
A paper published by a team of security researchers suggests that this represents a huge privacy risk. Using little more than the amount of power remaining in your battery, it is possible for people to be identified and tracked online.
As reported by The Guardian, a paper entitled The Leaking Battery by Belgian and French privacy and security experts say that the API can be used in device fingerprinting.
The API can be used to determine the capacity of a website visitor’s battery, as well as its current charge level, and the length of time it will take to fully discharge. When combined, these pieces of information create a unique identifier… Read More
Google Lets Businesses Control Own Security
Excerpted from Fox Business Report by Katie Roof
 Google is now giving its enterprise clients the option to manage their own security through its customer-supplied encryption keys program.
Google is now giving its enterprise clients the option to manage their own security through its customer-supplied encryption keys program.
The idea is that businesses who use Google for cloud storage no longer have to worry that the government or a Google employee can access their proprietary information.
Google Compute Engine allows businesses to manage their network and store data. Customers of Google’s cloud services include Best Buy and Coca-Cola.
Competitors Microsoft Azure and Amazon Web Services have already introduced similar enterprise security policies.
The new initiative will ensure participating customers that they can safeguard their own data.
“What this does is provide greater control for developers over their data in case of security breaches or government queries,” said James Cakmak, Analyst at Monness Crespi & Hardt. “This removes Google from the equation.”
It could also help Google expand its enterprise business in Europe, said Jonathan Gohstand, Infoblox Vice President of Product Management… Read More
New Senate Bill Seeks to Boost Cyber-Oversight
Excerpted from The Hill Report by Cory Bennett
 A bipartisan pair of US Senators wants to boost cybersecurity oversight at federal agencies after a series of mammoth digital thefts that have rattled the government.
A bipartisan pair of US Senators wants to boost cybersecurity oversight at federal agencies after a series of mammoth digital thefts that have rattled the government.
Sens. Orrin Hatch (R-UT) and Tom Carper (D-DE) on Wednesday introduced the Federal Computer Security Act.
The measure would require inspectors general to submit a report on their agency’s security practices to Congress.
It would also mandate a Government Accountability Office (GAO) report that gives an economic analysis of the barriers agencies face when trying to implement proper cyber defenses.
The bill “will shine light on whether our federal agencies are using the most up-to-date security practices and software to safeguard our nation’s most sensitive information,” said Hatch, who chairs the Senate Finance Committee.
The measure comes on the heels of digital intrusions at the Internal Revenue Service (IRS) and the Office of Personnel Management (OPM).
At the IRS, hackers successfully imitated taxpayers, making off with more than 100,000 people’s returns… Read More
Alibaba: Quantum Computing for Next-Gen Cloud
Excerpted from Business Cloud News Report
 Alibaba’s cloud computing unit Aliyun has signed a memorandum of understanding (MoU) with Chinese Academy of Sciences (CAS) that will see the two set up a quantum computing lab to study the technology’s applications in security, networking and cloud computing.
Alibaba’s cloud computing unit Aliyun has signed a memorandum of understanding (MoU) with Chinese Academy of Sciences (CAS) that will see the two set up a quantum computing lab to study the technology’s applications in security, networking and cloud computing.
The lab will focus on experimenting with quantum theory in a bid to develop novel security technologies for e-commerce and data-centers (including, potentially, its own) and bolstering computing performance.
“The CAS — Alibaba Quantum Computing Laboratory will undertake frontier research on systems that appear the most promising in realizing the practical applications of quantum computing,” said Jianwei Pan, Executive Vice President of University of Science and Technology of China (USTC) and a CAS member.
“The laboratory will combine the technical advantages of Aliyun in classical calculation algorithms, structures and cloud computing with those of CAS in quantum computing, quantum analog computing and quantum artificial intelligence, so as to break the bottlenecks of Moore’s Law and classical computing,” Pan said.
The organizations said they want the lab to become a hub for international research in quantum computing… Read More
GE Announces Industrial Cloud-Computing Service
 General Electric (GE) announced its plans to move into the cloud services market today, with the launch of the world’s first cloud-based solution specifically designed for industrial data and analytics.
General Electric (GE) announced its plans to move into the cloud services market today, with the launch of the world’s first cloud-based solution specifically designed for industrial data and analytics.
The company will spend $500 million to promote and sell its line of products that connect machines to a distant computer network designed to capture data and promote efficiency.
The initiative is named “Predix Cloud” and will be sold as a service directly to companies.
GE provides services to a variety of customers throughout the aviation, energy, healthcare, and transportation industries. The company sees Predix Cloud as a way for these companies to reduce mistakes, save money, and provide better service.
“A more digital hospital means better, faster healthcare. A more digital manufacturing plant means more products are made faster. A more digital oil company means betters assets management and more productivity at every well,” said GE’s CEO Jeffrey Immelt.
This move is also another step into the software industry for General Electric. GE saw $4 billion from software revenue in 2014… Read More
Research Scientists to Use Much Faster Network
Excerpted from the NY Times Report by John Markoff
 A series of ultra-high-speed fiber-optic cables will weave a cluster of West Coast university laboratories and supercomputer centers into a network called the Pacific Research Platform as part of a five-year $5 million dollar grant from the National Science Foundation.
A series of ultra-high-speed fiber-optic cables will weave a cluster of West Coast university laboratories and supercomputer centers into a network called the Pacific Research Platform as part of a five-year $5 million dollar grant from the National Science Foundation.
The network is meant to keep pace with the vast acceleration of data collection in fields such as physics, astronomy, and genetics.
It will not be directly connected to the Internet, but will make it possible to move data at speeds of 10 gigabits to 100 gigabits per second among 10 University of California campuses and 10 other universities and research institutions in several states, tens or hundreds of times faster than is typical now.
The challenge in moving large amounts of scientific data is that the open Internet is designed for transferring small amounts of data, like web pages, said Thomas A. DeFanti, a specialist in scientific visualization at the California Institute for Telecommunications and Information Technology, or Calit2, at the University of California, San Diego.
While a conventional network connection might be rated at 10 gigabits per second, in practice the real rate is only a fraction of that capacity… Read More
SMEs Double Down on Mobility & Cloud
Excerpted from Computer Business Report by Alexander Sword
 Take-up of cloud computing by UK small-to-midsize enterprises (SMEs) has increased 15 percent in the last year.
Take-up of cloud computing by UK small-to-midsize enterprises (SMEs) has increased 15 percent in the last year.
Cloud-based applications are used by 69 percent of SMEs, with 53 percent believing that they are important to remote working.
In addition, 91 percent of respondents to the BT and British Chambers of Commerce survey have at least one member of staff working from home and 19 percent have more than half of their workforce working away from the main office location.
Remote access to company data, wi-fi access when out of the office and fiber-optic broadband were also seen as critical by 56 percent, 64 percent and 33 percent of respondents respectively.
Smartphones were considered the most transforming technology, with 68 percent believing that they had made the biggest difference to businesses in the last 12 months. 54 percent cited improved wi-fi access and 42 percent cloud-based applications.
79 percent claimed that the Internet had increased their speed of communication, 64 percent argued it had improved customer service… Read More
Benefits of Cloud Computing for Small Businesses
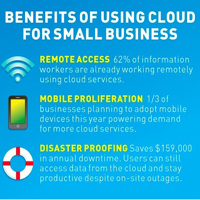 Until very recently, cloud computing has been the domain of big corporations.
Until very recently, cloud computing has been the domain of big corporations.
The cost of using cloud computing as part of a business process was just too high for small businesses.
Today, however, cloud computing is far more affordable.
Solutions from top names such as Citrix and Amazon are opening up new doors for small and home businesses.
There are a number of benefits that cloud computing brings to small businesses; some more common than the others.
In this part, we are going to look into some of the remarkable benefits that small businesses often neglect when reviewing cloud computing solutions.
For small businesses, keeping the cost down is key.
This is where being able to collaborate with people from all around the world comes in really handy.
Instead of having to have multiple on-site employees, businesses can now have freelancers from around the globe providing their expertise… Read More
Full Potential of Hybrid Cloud Computing
Excerpted from Network World Report
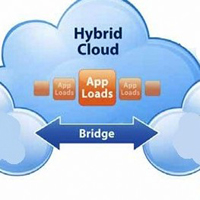 In a world increasingly enchanted with cloud computing, the hybrid cloud is emerging as the solution that addresses the broadest customer challenges.
In a world increasingly enchanted with cloud computing, the hybrid cloud is emerging as the solution that addresses the broadest customer challenges.
Although implementations — and even definitions — vary, hybrid cloud solutions broadly aim to blend the best aspects of public clouds with those of on-premises private cloud environments.
Public clouds bring reduced costs, elasticity, quick provisioning and other benefits to the party.
For their part, private clouds enable companies to meet their business requirements by maintaining data sovereignty and defining their own service-level agreements with data protection and continuous availability.
The combined benefits of agility, elasticity, availability, and simplicity — together with choice — have made hybrid cloud deployments a top agenda item for many companies.
In a recent survey of 111 IT and business executives, IDG Research Services found that 72 percent have either deployed hybrid cloud solutions already (44 percent) or plan to do so in the coming 12 months (28 percent)… Read More
Coming Events of Interest
Cloud Partners 2015 — September 16th-18th in Boston, MA. This Informa-hosted conference is totally focused on how the cloud can mean business for you. Learn how to enable scale, impact, and action based on cloud services.
The Internet of Things (IoT) Show — September 2nd-23rd in Singapore. The IoT Show will facilitate new collaborations and partnerships as well as generate new ideas and thinking. The IoT Show is about getting the prototypes out of the lab and into the market.
ADRM Working Group Meeting — September 24th via Global Videoconference. Contact the DCIA for information about joining the group and attending the meeting that will focus on interoperability among DRM platforms and simplifying DRM implementation.
New York Media Festival — October 6th-9th in New York, NY. NYME brings together 5,000 expected attendees including 1,500 senior digital, games, music, television, advertising and video leaders, brands, investors and start-ups. Networking, meetings and deal-making.
Digital Hollywood Fall — October 19th-22nd in Marina Del Rey, CA. The future of the entertainment industry. Digital Hollywood debuted in 1990 and has from its start been among the leading trade conferences in its field.
2015 US Cyber Crime Conference — November 14th-20th in National Harbor, MD. This is the only event of its kind that provides both hands-on digital forensics training and an interactive forum for cyber professionals to network.
Internet of Things World Forum (IoTWF) — December 6th-8th in Dubai, . IoTWF is an exclusive event that brings together the best and brightest thinkers, practitioners, and innovators from business, government, and academia to accelerate the market adoption of the Internet of Things.
