In This Issue
- IT Security Tops $75B
- US & China Seek Deal
- Hybrid Mkt 29% CAGR
- Report from the CEO
- Cloud to Manage Risk
- IBM Launches IT Tool
- Cloud Security Shroud
- SMBs & Cybersecurity
- Safe Enterprise Video
- Pico Cassettes & DRM
- Intel Joins VZ’s 5G TF
- NetApp: CTO Bregman
- CB: Containerization
- IaaS & PaaS: B, M, CM
- VM Cloud Provisioning
- Distrib/Orchestrate?
- Coming DCIA Events
Gartner: 2015 IT Security Spending to Top $75 Billion
Excerpted from DigiTimes Report by Joseph Tsai
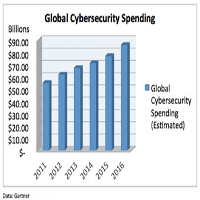 Worldwide spending on information security will reach $75.4 billion in 2015, an increase of 4.7% over 2014, according to the latest forecast from Gartner.
Worldwide spending on information security will reach $75.4 billion in 2015, an increase of 4.7% over 2014, according to the latest forecast from Gartner.
The increase in spending is being driven by government initiatives, increased legislation, and high-profile data breaches.
Security testing, IT outsourcing, and identity and access management present the biggest growth opportunities for technology providers.
According to Gartner, spending in areas such as endpoint protection platforms and consumer security software is starting to see commoditization, leading to a downgrade in the forecast for these segments in 2015.
While the visibility and growing awareness of the impact of security threats keeps attention on security, the bulk of the security software market is composed of mature technology areas where the penetration rate is already high.
“Interest in security technologies is increasingly driven by elements of digital business, particularly cloud, mobile computing, and now also the Internet of Things (IoT), as well as by the sophisticated and high-impact nature of advanced targeted attacks,” said Elizabeth Kim, Research Analyst at Gartner… Read More
US and China Seek Arms Deal for Cyberspace
Excerpted from NY Times Report by David Sanger
 The United States and China are negotiating what could become the first arms control accord for cyberspace, embracing a commitment by each country that it will not be the first to use cyber-weapons to cripple the other’s critical infrastructure during peacetime, according to officials involved in the talks.
The United States and China are negotiating what could become the first arms control accord for cyberspace, embracing a commitment by each country that it will not be the first to use cyber-weapons to cripple the other’s critical infrastructure during peacetime, according to officials involved in the talks.
While such an agreement could address attacks on power stations, banking systems, cellphone networks and hospitals, it would not, at least in its first version, protect against most of the attacks that China has been accused of conducting in the United States, including the widespread poaching of intellectual property (IP) and the theft of millions of government employees’ personal data.
The negotiations have been conducted with urgency in recent weeks, with a goal to announce an agreement when President Xi Jinping of China arrives in Washington for a state visit on Thursday.
President Obama hinted at the negotiations on Wednesday, when he told the Business Roundtable that the rising number of cyber-attacks would “probably be one of the biggest topics” of the summit meeting.
His goal: for Americans and the Chinese to be able to coalesce around a process for negotiations and bring a lot of other countries along… Read More
Hybrid Cloud Market Growing at 29.22% CAGR
Excerpted from MarketWatch Report
 One of the most important trends in cloud computing is the availability of hybrid cloud market solutions from various service providers.
One of the most important trends in cloud computing is the availability of hybrid cloud market solutions from various service providers.
For instance, Fujitsu offers hybrid cloud services based on Microsoft Windows Azure, which enables interoperability between applications and systems.
The service is offered for different scenarios, including when a business needs additional resources in the public cloud to support heavy workload.
The hybrid cloud market service offered by Fujitsu also addresses the issue of enterprises having to rely on multiple cloud vendors.
According to the 2015 Hybrid Cloud Market Report, organizations are focusing on hybrid cloud as it provides the benefits of both private and public cloud models.
The hybrid cloud also provides IT infrastructure and application support to enterprises at a low cost.
Therefore, with the adoption of hybrid cloud market services, enterprises are reducing their capital and operational expenditure… Read More
Report from DCIA CEO Marty Lafferty
 This week, we have some good news to report.
This week, we have some good news to report.
The US Senate has reached an agreement to drop Section 603 of the Intelligence Authorization Act of 2016 (S. 1705).
The provision would have required online services to report an undefined category of suspicious communications to the government, creating a vague obligation that inevitably would have led to over-reporting of users’ activities to avoid violating the law.
Section 603 would have risked bringing wholly innocent people under the scrutiny of federal authorities.
The provision would have made the content of private communications — emails, text messages, social media posts, files, and photos stored in the cloud — accessible by the government without a warrant.
Not only would there have been an absence of appropriate due process, but also no notice would have been given to users.
Individuals would have had no opportunity to contest allegations, and trust in US-based Internet services would have been seriously eroded around the world.
With its failure to provide limits on the use of reported information, and no safeguards against abuse, Section 603 represented a clear invasion of privacy and a certain threat to freedom of expression.
In August, the DCIA joined with thirty other trade associations and human rights organizations led by the Center for Democracy & Technology (CDT) in sending a message to US Senate leadership opposing Section 603.
We are especially grateful to Senator Ron Wyden (D-OR) for placing a hold on the bill until this provision was removed this week by Senate action.
And we offer thanks to everyone who spoke out against the provision.
The commentary and public pressure about the dangers of this reporting requirement were instrumental in ensuring that it was removed from the bill.
The Intelligence Authorization Act is expected to pass the Senate by unanimous consent later this year.
The House passed its version of the bill — without such a reporting requirement — in June.
This week’s action represents a clear victory for free expression and the privacy rights of Internet users everywhere. Share wisely, and take care.
Using Cloud Computing to Manage Global Business Risk
Excerpted from HostReview Report by Sujain Thomas
 When businesses have relatively small footprints the issue of managing risk is usually far simpler and can be handled by the managerial and audit teams relatively easily.
When businesses have relatively small footprints the issue of managing risk is usually far simpler and can be handled by the managerial and audit teams relatively easily.
However, when businesses start operations across the globe and establish linkages with thousands of suppliers spread across the globe, it can be very difficult to minimize the risks.
To overcome the limitations of internal systems, recourse is being taken to cloud computing strategies that have proven very effective.
There has been no other technology development that has had a greater impact on the reduction of risk of operating a supply chain than cloud technology.
Cloud computing has made it possible for companies to stay in touch on a real-time basis with thousands of their suppliers spread all across the globe round the clock.
The conventional ERP-based solutions configured to manage supply chain systems internally by inter-connecting departments within the organization do not prove to be very well positioned to handle the business processes required to manage suppliers… Read More
IBM Launches IT Tool to Catch Unauthorized Cloud Apps
Excerpted from NYC Today Report by Peter Jenkins
 IBM recently launched a tool that can tame unauthorized cloud apps within an organization with ease and enhance quality assurance.
IBM recently launched a tool that can tame unauthorized cloud apps within an organization with ease and enhance quality assurance.
The ill practice of running unauthorized cloud apps, termed as Shadow IT, has been a major concern before big companies.
The illicit use also results into wastage of time and resources. It also poses threat of data leak.
Earlier, Skyhigh Networks, a start-up, had offered a similar tool.
The technology available for the purpose until now was limited to discovering cloud applications that employees use within any company.
IBM’s Security Enforcer, meanwhile, goes several steps ahead in not only identifying the bad element but also blocking it.
The main control then goes to the credible IT operators who can centrally control the entire system with protected credentials.
“We believe that this IBM cloud tool will surely stand out in the market as it not only makes cloud computing safe in corporations… Read More
Computer Scientist Seeks Stronger Cloud Security Shroud
Excerpted from UT Dallas News Report by Chaz Lilly
 Dr. Zhiqiang Lin, of the Erik Jonsson School of Engineering and Computer Science at UT Dallas, is working to advance the field of cloud computing, and in the process, has developed a technique that allows one computer in a virtual network to monitor another for invasions or viruses.
Dr. Zhiqiang Lin, of the Erik Jonsson School of Engineering and Computer Science at UT Dallas, is working to advance the field of cloud computing, and in the process, has developed a technique that allows one computer in a virtual network to monitor another for invasions or viruses.
Lin’s research has earned the assistant professor of computer science a National Science Foundation Faculty Early Career Development (CAREER) Award, which provides him with $500,000 in funding for five years.
“Dr. Lin’s technical achievements are significant,” said Dr. Bhavani Thuraisingham, Executive Director of the UT Dallas Cyber Security Research and Education Institute and the Louis A. Beecherl Jr. Distinguished Professor in the Jonsson School.
“He has developed a highly novel method to carry out virtual machine introspection and will be exploring this area further.”
Virtual machine introspection is the viewing of a virtual machine’s actions from the outside.
“Virtual machine introspection is a useful technique for protecting cloud applications, as many hosting providers offer services on virtual machines to their clients,” said Erick Bauman, who works in Lin’s Systems and Software Security Lab… Read More
Small Businesses Take Action on Cybersecurity
Excerpted from Daily Herald Report by Rich Klicki
 If there’s one fear that universally keeps business owners up at night, it the fear of being hacked.
If there’s one fear that universally keeps business owners up at night, it the fear of being hacked.
There’s no argument that cyber-crime is a serious global problem, and it’s the one global problem that’s also at the forefront of Main Street businesses, according to an online payroll services provider SurePayroll.
The Glenview-based company’s monthly Small Business Scorecard optimism survey recently found 60 percent of small business owners are concerned enough about cyber-crime to take extra precautions assuring their data is secure.
That number is up from 56 percent a year ago.
“It tells you just how serious this issue has become for business owners, regardless of size,” said SurePayroll General Manager Andy Roe.
“It’s not just the big chains that are focused on security right now.”
“Small business owners understand that any sort of breach or lack of confidence when it comes to online security could have a big impact,” he added. SurePayroll surveys 5,000 small businesses nationwide for its monthly Scorecard… Read More
How to Keep Enterprise Video Safe and Secure
Excerpted from Streaming Media Report by Jan Ozer
 You’re the tech guy or gal for a medium-sized company, and the CEO just told you she wants to start using an online video platform to distribute video around the enterprise.
You’re the tech guy or gal for a medium-sized company, and the CEO just told you she wants to start using an online video platform to distribute video around the enterprise.
Live all-hands-on-deck meetings, converted to VoD for those who can’t make it live, plus product demos, some training, a few marketing videos — you know the drill.
She finishes by saying, “And I want it secure.”
You nod your head in agreement as she walks off, and then you wonder, “What the heck does that mean?”
Well, let’s talk about that.
First, the unfortunate reality is that by using screen capture software, employees can capture any video they can play.
But let’s put this aside for a moment, and return to it.
Second, many OVPs deliver encoded MP4 files via progressive download, which any browser-based video capture tool — Firefox’s Video Download Helper, for instance — can capture with a click or two… Read More
Pico Cassettes Are DRM Token Game Cartridges
Excerpted from siliconANGLE Report by Eric David
 At last week’s Tokyo Game Show, Japanese company Beatrobo announced a new line of mobile game cartridges called Pico Cassettes, which are meant to be plugged into your smartphone’s headphone jack.
At last week’s Tokyo Game Show, Japanese company Beatrobo announced a new line of mobile game cartridges called Pico Cassettes, which are meant to be plugged into your smartphone’s headphone jack.
Beatrobo CEO Hiroshi Asaeda said that Pico Cassettes are meant to be a nostalgic callback to the game cartridges that ruled the console industry in the ’80s and ’90s, but there is one key difference with Pico Cassettes: They don’t actually contain any game data.
The miniature cartridges actually contain digital rights management (DRM) software, which acts as an authentication key by sending an inaudible signal through the headphone jack to unlock the game on your phone.
I’ll admit, this sounded like a terrible idea to me at first.
Ever since publishers first realized they could convince their investors that piracy could be fought with draconian protection software, the videogame industry has seen an explosion in DRM programs, most of which are awful.
Often requiring specialized software and constant access to the Internet, DRM tends to be about as much fun as a TSA checkpoint and only slightly more effective… Read More
Intel Joins Verizon’s 5G Technology Forum
 Intel has partnered with Verizon in its efforts to advance the development of 5G next generation wireless technology.
Intel has partnered with Verizon in its efforts to advance the development of 5G next generation wireless technology.
Intel will help optimize end-to-end mobile broadband and Internet of Things (IoT) device architectures to accelerate the development of 5G.
The company will work in Verizon’s 5G sandbox environments in San Francisco, CA and Waltham, MA innovation centers.
Intel is also developing its own 5G test beds in Oregon, California, and other locations.
The company is focusing on mobile broadband, IoT 5G devices, mm-wave dual connectivity technology, virtualized radio access network elements supporting MIMO, ultra-low latency response, high frequency small cells, and mobile edge computing.
Verizon and Intel will also work on network transformation initiatives that optimize the existing network and build next generation network architecture.
Intel is also working with Verizon on SDN Network Evolution for achieving business and technical benefits of a network development… Read More
NetApp Names Mark Bregman CTO to Drive Innovation
Excerpted from Talkin’ Cloud Report by Nicole Henderson
 Data management and cloud storage company NetApp named Mark Bregman Chief Technology Officer (CTO) in an announcement on Monday.
Data management and cloud storage company NetApp named Mark Bregman Chief Technology Officer (CTO) in an announcement on Monday.
Bregman joins NetApp from machine-learning startup SkywriterRX where he served as CTO, and continues to serve as a board member and an advisor.
At NetApp Bregman will be responsible for leading its portfolio strategy and innovation roadmap.
He will evaluate where the biggest opportunities are to support its vision of the Data Fabric, the company’s vision for the future of data management.
“Mark will work with NetApp’s Advanced Technology Group anticipating and capitalizing on new and emerging trends,” NetApp Executive Vice President of Product Operations Joel Reich said.
“His wealth of experience across technology sectors will be invaluable to accelerating NetApp’s innovation leadership. We look forward to Mark helping to deliver outstanding value to our customers and partners, now and into the future.”
Bregman has held senior positions at Neustar, Symantec, Veritas, AirMedia, and IBM… Read More
CloudBolt Adds SDN and Containerization
Excerpted from Business Cloud News Report
 Virtual appliance maker CloudBolt Software now offers better support for microservices, software defined networking (SDN) and containerization on its platform.
Virtual appliance maker CloudBolt Software now offers better support for microservices, software defined networking (SDN) and containerization on its platform.
It is also offering compatibility with a variety of container services.
According to CloudBolt, its customers can now virtualize their networks with access to VMware NSX directly through its system.
There is also new additional support for Docker and Kubernetes for customers wishing to use application containerization.
The addition of new support capacity for IBM SoftLayer, HP Helion, and CenturyLink Cloud means that there are now 13 cloud platforms compatible with CloudBolt.
The addition of Docker and Kubernetes marks the first time that any form of micro-services management has been available on CloudBolt’s system.
The new compatibility with VMware NSX will allow customers to spin up virtual environments within the CloudBolt platform… Read More
IaaS & PaaS: Benefits, Myths, Common Mistakes
Excerpted from ITProPortal Report by Mihail Karpuk
 The “cloud” has been a hot term for a while. Regardless of the fact that the concept has been around for about 10 years, its superstar status produces many delusions and misconceptions.
The “cloud” has been a hot term for a while. Regardless of the fact that the concept has been around for about 10 years, its superstar status produces many delusions and misconceptions.
There are still misunderstandings even about what cloud is.
Technologies that have nothing to do with the cloud are given the buzzword name, and cloud hosting is marketed as a solution to every problem a business owner might have.
Therefore, before we talk about advantages and disadvantages of cloud computing, it is important to understand what the term “cloud service” really means.
The main characteristics of the cloud are: on-demand, self-service, and scalable and measurable.
To be more specific, when using the cloud, service users should be able to choose the type and amount of the resources at any time and only pay for that amount. Why am I going into detail about this? Because these are the features that determine the main advantages of cloud technologies, namely:
Full access to easy-to-use control panels and API, enabling fast fine-tuning without intermediaries such as specialists of ticketing… Read More
Energy-Efficient VM Provisioning in Cloud Environments
Excerpted from ACL Digital Media Library Abstract
 As the increasing number of modern applications and enterprises demand more and more resources in computational power, memory, and disk storage, cloud data centers are consuming huge amounts of electrical energy.
As the increasing number of modern applications and enterprises demand more and more resources in computational power, memory, and disk storage, cloud data centers are consuming huge amounts of electrical energy.
The aim of cloud service providers is to reduce the operational costs by minimizing energy consumption while providing competitive services to their customers.
The above can be fulfilled by trying to reduce the number of active servers, using live virtual machine (VM) migrations and keeping the system performance in the requested levels according to service level agreements (SLAs).
In this paper, an efficient VM allocation mechanism for cloud data center environments is proposed.
We first describe the VM allocation policy and then we perform a series of experiments based on CloudSim 3.0.3 simulator, a toolkit for modeling and simulation of cloud computing environments and evaluation of resource provisioning algorithms.
Experimental results have shown that the proposed scheme is very efficient in terms of energy consumption and quality of service (QoS) and decreased SLA violations, compared to LrMmt provisioning mechanism presented in Anton Beloglazov and Rajkumar Buyya’s “Optimal Online Deterministic Algorithms and Adaptive Heuristics… Read More
From Distributed to Orchestrated?
Excerpted from The Pulse Report by Rich Bailey
 I’ve touched on the Global Environment for Network Innovations (GENI) a few times in this column, mostly regarding its significance to Chattanooga’s bandwidth mastery of the universe.
I’ve touched on the Global Environment for Network Innovations (GENI) a few times in this column, mostly regarding its significance to Chattanooga’s bandwidth mastery of the universe.
It extends EPB’s one-gigabit-per-second Internet speed, still the biggest community-wide ultra-high bandwidth rollout, despite Comcast’s recent announcement of two-gig service in some cities, by connecting UT-Chattanooga to 60-plus research universities who make up their own ultra-high bandwidth network through their connection to GENI.
GENI has fascinating implications about a potential role for Chattanooga as a test kitchen for new bandwidth-intensive applications that need a working network for testing.
But until I heard Andrew Armstrong, technologist-in-residence at Co.Lab and the Enterprise Center, speak about GENI at the inaugural Chattanooga Salon last month at Lamp Post Group, I was a little fuzzy on the actual technology of GENI.
Here’s how Armstrong explains it… filtered through my nontechnical understanding, of course. Any errors are definitely mine.
GENI is a platform for researching new methods of networking. As technical as that might sound, the crux of the need for a new Internet… Read More
Coming Events of Interest
New York Media Festival — October 6th-9th in New York, NY. NYME brings together 5,000 expected attendees including 1,500 senior digital, games, music, television, advertising and video leaders, brands, investors and start-ups. Networking, meetings and deal-making.
Digital Hollywood Fall — October 19th-22nd in Marina Del Rey, CA. The future of the entertainment industry. Digital Hollywood debuted in 1990 and has from its start been among the leading trade conferences in its field.
2015 US Cyber Crime Conference — November 14th-20th in National Harbor, MD. This is the only event of its kind that provides both hands-on digital forensics training and an interactive forum for cyber professionals to network.
Cloud Asia Forum — November 24th-25th in Hong Kong. Now in its sixth year, this major highlight of the Cloud World Series sponsored by Informa Telecoms & Media is the most comprehensive cloud computing event in Asia.
Government Video Expo — December 1st-3rd in Washington, DC. Sponsored by NewBay Media, GVE 2015 will be the East Coast’s largest technology event designed for video, broadcast, and audio-video professionals.
Internet of Things World Forum (IoTWF) — December 6th-8th in Dubai. IoTWF is an exclusive event that brings together the best and brightest thinkers, practitioners, and innovators from business, government, and academia to accelerate the market adoption of the Internet of Things.
CES — January 6th-9th in Las Vegas, NV. The world’s gathering place for all who thrive on the business of consumer technologies. CES has served as the proving ground for innovators and breakthrough technologies for more than 40 years.
ADRM Working Group Meeting — January 28th via Global Videoconference. Contact the DCIA for information about joining the group and attending the meeting that will focus on interoperability among DRM platforms and simplifying DRM implementation.
