In This Issue
- Distributed Computing
- Cybersecurity Sector
- AT&T and Verizon IoT
- Report from the CEO
- Thermostat Caution
- Cam Search Engine
- Cyber-Crime Booming
- IoT Security Problem
- Why We’re Vulnerable
- IoT & Cyber-Attacks
- Stopping Consumers
- Security Years Away
- Meeting the Challenge
- Israel Start-Up Funds
- Storage and Security
- Hughes-Hubbard SC
- Coming DCIA Events
Distributed Computing Tops List of Hottest Job Skills
Excerpted from Datanami Report by Alex Woodie
 If you have cloud and distributed computing skills, your job prospects for 2016 are golden.
If you have cloud and distributed computing skills, your job prospects for 2016 are golden.
That’s because those particular job skills — which parallel the rise of Hadoop and other distributed computing frameworks — topped a LinkedIn analysis of the top 25 skills to help you find a new job this year.
The sudden arrival of cloud and distributed computing as the hottest skills in the land was somewhat unexpected, according to Sohan Murthy, the head of research for data analytics and strategy at LinkedIn.
“In many ways, 2015 could be seen as the year cloud and distributed computing graduated from a niche skillset to a more prominent skillset in the global workforce,” Murthy writes in a recent blog posting.
“It was a very hot category in a few countries last year,” he says, including the United States, where it was number one.
“But there weren’t enough members with skills like Hadoop, HBase, and Hive listed on their profiles to allow us to rank the category on our global list in 2014.”
In 2015, there was a rapid increase in members worldwide listing these types of skills on their profiles… Read More
Cybersecurity Sector Will See Huge Growth in 2016
Excerpted from The Street Report by Sephi Shapira
 Some big names, including Donald Trump and Ashley Madison, fell victim to cyber-crime in 2015, along with hundreds of millions of individuals and organizations.
Some big names, including Donald Trump and Ashley Madison, fell victim to cyber-crime in 2015, along with hundreds of millions of individuals and organizations.
A single attack on insurer Anthem left almost 80 million customers and employees exposed.
An attack on The United States Office of Personnel Management (OPM) resulted in 18 million US citizens’ records and 5.6 million sets of fingerprints being stolen.
“Given the ongoing, evolutionary nature of cyber-attacks, coupled with the relatively low share of total IT spend security accounts for, we believe industry growth rates will remain stronger than industry forecasts,” said the investment bank Columbia Threadneedle Investments.
Those rates are 10%-to-15% over the next three to five years, according Columbia Threadneedle, or 8%-to-10%, according to industry analysts at Gartner.
In a $75 billion market, growth rates such as these create immense opportunities for innovative cybersecurity companies, as well as potentially outsized investment returns for those capitalizing on market demand… Read More
AT&T and Verizon Eye the Internet of Things
Excerpted from Computerworld Report by Matt Hamblen
 AT&T and Verizon — the nation’s two biggest carriers — are seeing their traditional US wireless businesses shrink, having suffered from an ongoing price war and declining buyer interest in new smartphones.
AT&T and Verizon — the nation’s two biggest carriers — are seeing their traditional US wireless businesses shrink, having suffered from an ongoing price war and declining buyer interest in new smartphones.
To make up for that drop, both carriers are increasingly focused on new areas for growth, including Internet of Things (IoT) projects, as well as far-flung investments like AT&T’s wireless service in Mexico and Verizon’s investments in new media through AOL advertising technology.
This movement into new business areas is seen as a long-range mega-trend that was borne out by the latest earnings reports from AT&T this week and Verizon last week.
“What we are seeing is that the traditional market that both carriers go after is saturated, since pretty much everyone who has wanted a cell phone already has one,” said Chris Antlitz, an analyst at TBR.
“They are both trying to grow new businesses and investing heavily in the hope they can offset the price war that’s eating into their traditional business.”
What’s happening instead? Both companies are getting big into IoT and machine-to-machine and that’s a big growth engine… Read More
Report from DCIA CEO Marty Lafferty
 With recent reports of breaches affecting connected home thermostats and video monitoring systems, it’s time for the industry to address a critical issue threatening success of the very promising Internet of Things (IoT) technology movement.
With recent reports of breaches affecting connected home thermostats and video monitoring systems, it’s time for the industry to address a critical issue threatening success of the very promising Internet of Things (IoT) technology movement.
Consumers must be able to trust that the data their newly connected devices generate, gather, and process is safe.
Failure to ensure such security risks not only adoption of IoT devices, but also the reputations and even the viability of companies that market them.
A fundamental choice for industry participants, therefore, is whether to rely on hardening devices against intrusions or to implement secure data-stream networks for IoT.
Ideally, a robust security model for IoT should handle many kinds of devices and many types of communications, but not require end-users to engage in complex set-up procedures or manage ongoing software and firmware updates.
If instead of having open inbound ports, IoT devices were designed to make only outbound connections, by using one of several secure and reliable communications protocols, it should be possible securely to transmit data bi-directionally using a publish/subscribe paradigm.
End-to-end encryption could be accomplished by combining industry-standard transport layer security (TLS) to protect the top level of data streaming with the advanced encryption standard (AES) to protect the data itself.
To alleviate the burden of devices having to filter out irrelevant data streams, token-based access control could be used at the network level, distributing tokens to IoT devices that would enable access to specific channels.
This approach would centralize control for authorizing and managing access, as well as, if warranted, completely cutting off data streams to devices.
Device presence monitoring is also critical to security and performance.
Beyond just determining whether a device is on- or off-line, more refined status elements could also be monitored by establishing a separate secure channel for IoT metadata to handle alerts and other triggers.
And finally, requiring consumers to bypass home network firewalls to connect their IoT devices not only creates confusion but also causes vulnerabilities.
Plus, end-users are not likely to take responsibility for installing updates to patch security problems.
The publish/subscribe network paradigm also can solve this, using standard outbound ports to achieve a more user-friendly plug-and-play experience.
Once plugged-in, the IoT device would subscribe to its designated announce channel and the associated server would open a private communications channel to provision the device for use.
Once provisioned, the device’s secure publish/subscribe channel would instruct it to download and install firmware updates without consumer intervention.
In combination with presence monitoring, as well as end-to-end encryption and token-based access control, updates can happen securely and automatically when devices are online and display the appropriate status.
Offline devices would simply pull the upgrade data from a channel cache when they reboot.
We urge industry participants to explore securing the networks that transmit data to and from IoT devices rather than attempting to harden device security.
This should speed time-to-market for new devices, increase consumer adoption, and reduce risks. Share wisely, and take care.
Thermostat Goes from IoT Darling to Cautionary Tale
Excerpted from TechDirt Report by Karl Bode
 Back when the Nest thermostat was announced in 2011, it was met with waves of gushing adoration from an utterly uncritical technology press.
Back when the Nest thermostat was announced in 2011, it was met with waves of gushing adoration from an utterly uncritical technology press.
Much of that gushing was certainly warranted; Nest was founded by Tony Fadell and Matt Rogers, both former Apple engineers, who indisputably designed an absolutely gorgeous device after decades of treating the thermostat as an afterthought.
But the company also leaned heavily on the same media acupressure techniques Apple historically relies on to generate a sound wall of hype potentially untethered from real life.
Courtesy of marketing and design, Nest slowly but surely became the poster child for the connected home.
Over the last year or so however things have changed, and while now Alphabet-owned Nest remains an Internet of things (IoT) darling, the unintended timbre of the message being sent is decidedly different.
For example, Nick Bilton recently wrote a piece in the New York Times noting how a glitch in the second generation of the supposedly “smart” product drained the device battery, resulting in numerous customers being unable to heat their homes… Read More
Webcam Search Engine Raises Privacy Concerns for IoT
Excerpted from CBC News Report
 A young child asleep on a couch in Israel. Mourners huddled together at a small funeral in Brazil. An elderly woman stretching in a fitness center in Poland.
A young child asleep on a couch in Israel. Mourners huddled together at a small funeral in Brazil. An elderly woman stretching in a fitness center in Poland.
All available for anyone to watch via the unsecured webcams overhead.
This isn’t “1984,” it’s the world in 2016.
Shodan, a search engine that indexes computers and devices rather than information, now allows users to pull screenshots from nanny cams, security cameras, and other connected devices around the world that don’t ask for a username or password.
Those screenshots are connected to an IP address, a unique identifier for each Internet connection or device that can be traced back to a general geographic area.
Anne Cavoukian, former Ontario Privacy Commissioner and now the Executive Director of the Privacy and Big Data Institute at Ryerson University, said she was appalled when she saw the Shodan webcam search in action.
Yet, she said, it’s only a symptom of the wider problem with the so-called Internet of Things (IoT)… Read More
Cyber-Crime Booming and IoT Will Make Things Worse
Excerpted from Quartz Report by Joon Ian Wang
 Hackers are getting better and businesses are increasingly at risk, according to a new report from global security consultants PwC.
Hackers are getting better and businesses are increasingly at risk, according to a new report from global security consultants PwC.
Worryingly for corporate digital security chiefs, this problem is expected to get worse as the Internet of Things (IoT) gains in popularity.
Here’s how bad corporate cyber-crime is right now:
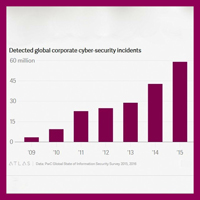
The number of detected security incidents climbed 38% in 2015 compared to a year earlier, according to PwC, and has been growing at a steady double-digit clip over the last five years.
The total number of incidents captured in the survey now stands at 59 million, although the true figure is likely to be much higher.
“The numbers have become numbing. Prevention and detection methods have proved largely ineffective,” says PwC.
These digital break-ins cost the global economy somewhere between $375 to $575 billion a year… Read More
IoT Security Problem Just Keeps Getting Bigger
Excerpted from eWEEK Report by Robert Lemos
 Recent reports about webcams being readily accessible to anyone using an Internet port-scanning service show there has been little progress in securing connected devices as we move into 2016.
Recent reports about webcams being readily accessible to anyone using an Internet port-scanning service show there has been little progress in securing connected devices as we move into 2016.
Every year or so, the Internet rediscovers that unsecured webcams are out there, leaking ready-to-watch videos of babies, pets, bank customers and even the offices of the webcam makers.
This month, the ability of the Shodan port-scanning service to easily find webcams set off a kerfuffle in the media.
Yet, the criticism is missing the point.
It’s more worrisome that people are putting devices into their homes and businesses with little concern for the security and privacy implications, security researcher Dan Tentler, told eWEEK.
Tentler has discussed the lack of security on webcams and other devices connected to the Internet at multiple conferences, and occasionally he posts interesting results from Shodan to his Twitter feed.
The popularity of the devices and their lack of security is creating a burgeoning problem, he said… Read More
Why We’re So Vulnerable
Excerpted from MIT Technology Review Report by David Talbot
 An expert in US national cybersecurity research and policy says the next generation of technology must have security built in from the very start.
An expert in US national cybersecurity research and policy says the next generation of technology must have security built in from the very start.
In an age of continuing electronic breaches and rising geopolitical tensions over cyber-espionage, the White House is working on a national cybersecurity strategy that’s expected in early 2016.
Helping to draft that strategy is Greg Shannon.
He was until recently chief scientist at Carnegie Mellon University’s Software Engineering Institute and is now on leave to serve as Assistant Director for Cybersecurity Strategy at the White House Office of Science and Technology Policy.
In an interview with MIT Technology Review senior writer David Talbot, Shannon explained that dealing with today’s frequent breaches and espionage threats — which have affected federal agencies as well as businesses and individuals — requires fundamentally new approaches to creating all kinds of software.
Shannon believes that the emergence of the Internet of things (IoT) — interconnecting billions of devices — provides an opportunity to do things correctly from the start… Read More
The IoT Will Require Security from Cyber-Attacks
Excerpted from C4RISR& Networks Report by Kevin Coleman
 Scientists have concluded that more data has been generated in the past two years than in the entire history of mankind, and the rate of data generation is intensifying.
Scientists have concluded that more data has been generated in the past two years than in the entire history of mankind, and the rate of data generation is intensifying.
Figures suggest that each and every minute, 300 hours of video are uploaded to YouTube alone.
One report states the White House has invested more than $200 million in big data projects already.
A recent Cisco Systems report projects the global Internet traffic will exceed the zettabyte (1,000 exabytes) threshold by the end of 2016.
IDC looked at the data growth trends and projected that by 2020 the digital data universe will reach 44 zettabytes. That’s 44 trillion gigabytes.
IDC estimates that big data technology and the associated services market will grow at a 26.4 percent compound annual growth rate to a whopping $41.5 billion in 2018.
One of the major sources of massive amounts of data is the Internet of Things (IoT)… Read More
What’s Stopping Consumers from Buying IoT Devices?
Excerpted from eMarketer Report
 The Internet of Things (IoT) has a wide-ranging impact across many categories, from healthcare to travel.
The Internet of Things (IoT) has a wide-ranging impact across many categories, from healthcare to travel.
And consumers are even embracing smart home devices.
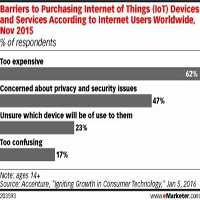
However, when it comes to purchasing an IoT device, cost is a top barrier.
According to a November survey from Accenture, nearly two-thirds of Internet users worldwide said that one of the barriers to purchasing IoT devices and services were the fact that they are too expensive.
In addition, almost half of respondents said they were concerned about privacy and security, and these issues were another hindrance to purchasing an IoT device.
The uncertainty about which device would be of use to them, as well as the confusion around these IoT devices more generally, were other barriers to purchase.
While price may be a hurdle for many consumers, others already own IoT devices.
August 2015 research from ISACA, found that 43% of US Internet users own a smart TV… Read More
Forrester: IoT Security Years Away from Being Fully Baked
Excerpted from ZDNet Report by Larry Dignan
 Many Internet of Things (IoT) technologies are in deployment among categories such as analytics, hardware, and networking, but the vendor ecosystem needs to focus on security and standards, according to a Forrester Report.
Many Internet of Things (IoT) technologies are in deployment among categories such as analytics, hardware, and networking, but the vendor ecosystem needs to focus on security and standards, according to a Forrester Report.
Forrester’s take on the IoT isn’t that shocking — the industry has developed with little thought about security — but the time frames are jarring nonetheless.
Anyone who perused the IoT dreams that surround smart homes and autos couldn’t help but notice that security issues were glossed over at best and more often ignored.
Forrester’s take highlights the push and pull of the IoT.
Forrester was upbeat about software and analytics, but wary of security and the integration issues that will arise from the lack of standards.
In its research report, Forrester noted:
Most hardware and networking IoT technologies have hit the growth phase or even the equilibrium phase… Read More
Internet of Things Security: Meeting the Challenge
Excerpted from DeveloperWorks Blog by Ravid Sagy
 In my previous post, I talked about the growing wave of security threats facing any individual or organization who is engaged and active on the Internet of Things (IoT).
In my previous post, I talked about the growing wave of security threats facing any individual or organization who is engaged and active on the Internet of Things (IoT).
In other words, just about everybody needs to worry about security.
That post should have gotten your alarm bells ringing about the need for a better security solution in IoT devices.
In this post and a follow-up, I want to describe a solution: IBM’s libsecurity, an accessible and easy-to-use library intended for non-experts, which can be used to incorporate security into your IoT design.
As I described, hackers try to gain control of IoT devices to use them for malicious purposes, such as sending misleading data or penetrating a user’s network and from there, gaining access to the cloud.
Following are some of the different methods that hackers use to gain control over the IoT devices, along with the associated protection capability provided by libsecurity:
It’s often easy for a hacker to guess the password of a device. In many cases, the device’s default password hasn’t been changed… Read More
Israel Cybersecurity Start-Ups Attract Large Investments
Excerpted from SC Magazine Report by Robert Abel
 Cybersecurity start-ups hold a premium position within Israel’s investment ecosystem and the country’s cybersecurity industry as a whole is second only to the US, according to a report from researchers at YL Ventures:
Cybersecurity start-ups hold a premium position within Israel’s investment ecosystem and the country’s cybersecurity industry as a whole is second only to the US, according to a report from researchers at YL Ventures:
“As Israel hosts Cybertech, the largest annual conference of cyber-technologies outside the United States, we, at YL Ventures, felt the time was right to share our insights on Israel’s vibrant start-up ecosystem.
As seed investors, primarily focused on Israeli cybersecurity companies, we have a unique perspective on how Israeli cybersecurity companies are developing and fairing on the global stage.
Our ‘2015 State of the Cyber Nation Report’ provides glimpses into the trajectory of Israeli companies in the markets they have been founded to serve.”
On average, both new and existing cybersecurity start-ups are raising more seed capital, compared to other Israeli start-ups, and are seeing increases in capital funding across all stages of investment with the largest increases occurring in later series of funding, according to YL Ventures.
Researchers said this may be related to the increased participation of US venture capital firms… Read More
Cybersecurity and Accessible Storage Trends
Excerpted from TV Technology Report by Karl Paulsen
 We now live in a world where organizations are more aware of cyber-threats than ever before.
We now live in a world where organizations are more aware of cyber-threats than ever before.
Cyber-crime has now surpassed the profitability of illegal drug trafficking.
Many organizations that interchange information are looking at myriad defensive measures to help keep business, industry, and personal data secure.
This elevated focus now includes storage systems as well as networks and other computer resources.
“There is no such thing as perfect security,” said cybersecurity firm FireEye in its annual Mandiant Threat Report issued in mid-2015.
Threat actors have evolved to encompass a larger scope of targets and are using a broader skillset to achieve their goals.
Determined threat actors are always finding a way through a gap in security; thus bringing the media and entertainment industry into sharper focus.
As storage systems have become more entangled in network-based communications, they have become equally vulnerable to threats… Read More
Hughes Hubbard Joins Supreme Court Battle
Excerpted from Hughes Hubbard News Report
 Hughes Hubbard (HHR) has joined a high-stakes fight on how federal and state governments divide authority over regulation of electric power generation and pricing.
Hughes Hubbard (HHR) has joined a high-stakes fight on how federal and state governments divide authority over regulation of electric power generation and pricing.
On December 15th, HHR filed a brief for amici curiae with the US Supreme Court on behalf of the National Governors Association, National Conference of State Legislatures and the Council of State Governments.
The firm was retained by the State and Local Legal Center, an organization that advocates the interests of the states before the Supreme Court.
The case presents the question of whether a state regulation requiring in-state electric utilities to enter into long-term contracts that assure stable revenues for new power generators constitutes rate setting that is preempted by federal law.
Maryland determined that its long-term energy and environmental needs required a new gas-fired generation facility.
In order to attract development of the new power plant, Maryland required the new generator to agree to a long-term price level that would allow it to recoup costs over 20 years.
The new generator would sell electric power capacity in the interstate auction supervised by the Federal Energy Regulatory Commission… Read More
Coming Events of Interest
Industry of Things World USA — February 25th-26th in San Diego, CA. A new international information exchange forum featuring four concurrent tracks covering business model generation, technology and infrastructure, data management, and security.
IoT Asia 2016 — March 30th-31st in Singapore. IoT Asia returns in 2016 with fresh insights on Internet of Things (IoT) developments around the world. The 3rd edition aims to further advance conversations and ideas on IoT and how it will impact our lives by delving into the real issues.
Delivery of Things World — April 25th-26th in Berlin, Germany. DevOps specialists, continuous development strategists, architect newbies, development geeks, and cloud geniuses from across the spectrum of DevOps transformation come together at this stimulating and innovative event.
DataCloud Europe 2016 — June 8th-9th in Monte Carlo, Monaco. The 2016 conference will focus on cloud computing advances and changes in data management, with a stellar line-up of speakers including global infrastructure leaders and subject matter experts.
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
