In This Issue
- Verizon Deploys NFV
- Amazon’s Cloud Profit
- Telefonica & Red Hat
- Report from the CEO
- NetApp Flash Learning
- Succeed Moore’s Law
- New Fog Computing
- MEC and Fog Report
- Flowthings Edge IoT
- Why IoT Needs Fog
- Quantum Computing
- AI and Cybersecurity
- FBI Hacking Expanded
- Encryption w/o Tears
- Why Users Cut Cord
- Pressure on Copyright
- Coming DCIA Events
Verizon’s Huge NFV Deployment Impacts Telecoms Everywhere
Excerpted from Ostatic Report by Sam Dean
 As this year began, we spotted a lot of action from telecom players and the open source community surrounding Network Function Virtualization (NFV) technology.
As this year began, we spotted a lot of action from telecom players and the open source community surrounding Network Function Virtualization (NFV) technology.
Red Hat and NEC Corporation said a few months ago that they formed a partnership to develop NFV features in the OpenStack cloud computing platform, with the goal of delivering carrier-grade solutions based on Red Hat’s OpenStack build.
Telecom providers have had longstanding problems with vendor lock-in in their infrastructure stacks, and OpenStack and other open tools could represent the cure.
This week, in partnership with Big Switch Networks, Dell, and Red Hat, Verizon announced that it has deployed “the industry’s largest-known” NFV OpenStack cloud deployment across five of its data centers in the US.
The move may prove influential in the telecom space. NewsFactor Business Report has a good summary of how to think about NFV:
NFV enables network services typically provided by separate devices like routers, firewalls, and load balancers to be delivered… Read More
Amazon’s Cloud Business Lifts its Profit to a Record
Excerpted from NY Times Report by Nick Wingfield
 Amazon delivered a blowout quarter on Thursday, joining Facebook as one of the rare bright spots in a technology sector that has recently produced a string of disappointing earnings reports.
Amazon delivered a blowout quarter on Thursday, joining Facebook as one of the rare bright spots in a technology sector that has recently produced a string of disappointing earnings reports.
Helped by its fast-growing Amazon Web Services (AWS) business, the company jumped to the most profitable quarter in its nearly 22-year history.
Amazon often flip-flops between showing profits and losses, depending on how aggressively it decides to plow money into big new business bets.
Investors have granted the company much wider leeway to do so than other technology companies of its size often receive, because of its history of delivering outsize growth.
For the first quarter, which ended March 31, Amazon reported net income of $513 million, or $1.07 a share, up from a loss of $57 million, or 12 cents a share, in the same period a year ago.
Revenue at the company rose to $29.13 billion from $22.72 billion a year ago.
Amazon’s share price jumped more than 12 percent in after-hours trading after the results were released… Read More
Telefonica & Red Hat Mobilize Business Processes
Excerpted from Telefonica Press Announcement
 Telefonica Business Solutions, a leading provider of a wide range of integrated communication solutions for the B2B market, and Red Hat, the world’s leading provider of open source solutions, today announced an agreement establishing Red Hat Mobile Application Platform as the global reference platform for operators within the Telefonica Group to mobilize the business processes of its customers on their path to digital transformation.
Telefonica Business Solutions, a leading provider of a wide range of integrated communication solutions for the B2B market, and Red Hat, the world’s leading provider of open source solutions, today announced an agreement establishing Red Hat Mobile Application Platform as the global reference platform for operators within the Telefonica Group to mobilize the business processes of its customers on their path to digital transformation.
The Red Hat Mobile Application Platform has been used by Telefonica in some markets since 2012, completing Telefonica’s Group Enterprise Managed Mobility proposition, as it provides users an open, agile, and collaborative approach to developing, integrating, and deploying mobile applications.
A collaborative approach to mobile, enabled by open standards-based technologies such as the Red Hat Mobile Application Platform, can help facilitate greater mobile adoption and maturity, as well as reduce both costs and time to market.
Organizations are increasingly investing in mobile application development to help transform the way they do business by reinventing business processes, automating existing processes, and mobilizing legacy web applications.
To match the rate at which mobile is evolving in the enterprise, and better meet challenges such as security and scalability… Read More
Report from DCIA CEO Marty Lafferty
 Five of the filmmaking industry’s most experienced audio-visual experts and solution providers will participate in a panel on June 23rd during the Creative Storage Conference (CS 2016), held at the DoubleTree Hotel West Los Angeles in Culver City, CA, and co-sponsored by the DCIA.
Five of the filmmaking industry’s most experienced audio-visual experts and solution providers will participate in a panel on June 23rd during the Creative Storage Conference (CS 2016), held at the DoubleTree Hotel West Los Angeles in Culver City, CA, and co-sponsored by the DCIA.
The “Conversations with Independent Filmmakers” session will feature leading members of the digital video industry who will discuss how they have improved their creative workflows, the industry trends they’re seeing, as well as challenges and opportunities visual storytellers face today.
Panelists will include Cirina Catania of the Catania Group, John Putch of PutchFilms, Lewis Smithingham of “30ninjas,” Woody Woodhall of Allied Post Audio, and Larry O’Connor of OWC Digital.
Tom Coughlin, Chair of the 2016 Creative Storage Conference, says, “This will be one of the most exciting and informational sessions held during the conference.
The panelists will be discussing the opportunities and challenges the entire industry faces as video and audio technologies evolve their digital storage requirements.
With this panel, attendees will meet the representative experts in the filmmaking industry who are shaping and delivering the technologies we use today and will demand tomorrow.
The tenth annual Creative Storage Conference and exhibits will bring together the vendors, end-users, researchers, and visionaries who are focused on the growing storage demands of HD, UltraHD, 4K, and HDR film production and how they are affecting every stage of the production process from content capture to editing to archiving to content distribution.
The preliminary conference agenda is posted on the conference website here.
Today’s filmmakers are creating outstanding visual stories that educate, entertain, inspire, and preserve history.
Thanks to low-cost 4K cameras, inexpensive/easy-to-use production tools, and powerful desktop/notebook systems, they are also breaking new ground in the visual storytelling industry.
Their challenge isn’t just storing their content but managing, controlling, tracking, and protecting that content.
Other sessions at CS 2016 will explore storage requirements for various elements of media and entertainment workflows for today and into the future.
Conference registration is now open. To register, click here.
We hope you’ll plan now to join us for the tenth annual Creative Storage Conference. Share wisely, and take care.
Accelerating Global Learning with NetApp Flash
Excerpted from MarketWired Report
 “We knew we needed to build a more powerful foundation to support our long-term e-learning and achieve our Bring Your Own Device goals,” says Lee J. DeAngelis, Senior Systems Administrator at The University of Scranton.
“We knew we needed to build a more powerful foundation to support our long-term e-learning and achieve our Bring Your Own Device goals,” says Lee J. DeAngelis, Senior Systems Administrator at The University of Scranton.
“We looked at other flash storage solutions, but the plug-and-play deployment of NetApp solutions made it an easy choice.”
Located in Pennsylvania, the University of Scranton decided to take e-learning to the next level by connecting students and faculty anywhere in the world, with an innovative Bring Your Own Device (BYOD) program.
The university also planned to offer university-owned software free of charge to students and faculty.
However, the institution was already experiencing performance issues and delays with existing resource-intensive applications. To make the BYOD program a success and to support existing applications, the university needed a highly scalable storage system.
The university moved its VMware Horizon View VDI deployment to NetApp AFF storage systems to expand its mobile-friendly content-delivery solutions, eliminate existing performance issues, and build a solid foundation for the future… Read More
Tech Looks for Moore’s Law Successor
Excerpted from NY Times Report by John Markoff
 For decades, the computer industry has been guided by a faith that engineers would always find a way to make the components on computer chips smaller, faster and cheaper.
For decades, the computer industry has been guided by a faith that engineers would always find a way to make the components on computer chips smaller, faster and cheaper.
But a decision by a global alliance of chip makers to back away from reliance on Moore’s Law, a principle that has guided tech companies from the giant mainframes of the 1960s to today’s smartphones, shows that the industry may need to rethink the central tenet of Silicon Valley’s innovation ethos.
Chip scientists are nearly at the point where they are manipulating material as small as atoms.
When they hit that mark within the next five years or so, they may bump into the boundaries of how tiny semiconductors can become.
After that, they may have to look for alternatives to silicon, which is used to make computer chips, or new design ideas in order to make computers more powerful.
It is hard to overstate the importance of Moore’s Law to the entire world.
Despite its official sound, it is not actually a scientific rule like Newton’s laws of motion. Instead, it describes the pace of change… Read More
The New Thing Called “Fog Computing”
Excerpted from Business Insider Report by Julie Bort
 By now, you’ve probably heard of cloud computing.
By now, you’ve probably heard of cloud computing.
That’s where companies rent shared software, computers, and storage instead of buying and installing it all themselves.
They pay for their usage via subscriptions, accessing it over the Internet.
Cloud computing is all the rage right now, on track to be a $10 billion business for Amazon in 2016; Microsoft hopes it will become a $20 billion business by 2018, and Google thinks it will become bigger than its Internet ad business by 2020.
So what comes after the cloud? If you ask Cisco, it’s something called “fog computing.”
Last month, Cisco was joined by other industry leaders including Intel, Microsoft, ARM, Dell, and Microsoft to back a new “fog computing” consortium, the OpenFog initiative.
It sounds like something straight from a Saturday Night Live parody skit, but it’s not.
Later this month, the consortium is holding a conference at Princeton University. Princeton is leading the research into fog computing. So what exactly is it? To understand fog computing, you first have to understand cloud computing… Read More
Mobile Edge Computing & Fog Computing Market Report
 Mobile Edge Computing (MEC) is a concept developed by ETSI (European Telecommunications Standards Institute) that aims to bring computational power into Mobile RAN (radio access network) to promote virtualization of software at the radio edge.
Mobile Edge Computing (MEC) is a concept developed by ETSI (European Telecommunications Standards Institute) that aims to bring computational power into Mobile RAN (radio access network) to promote virtualization of software at the radio edge.
MEC enables the edge of the network to run in an isolated environment from the rest of the network and creates access to local resources and data.
Fog Computing is a distributed computing infrastructure in which some application services are controlled at the network edge in a smart device and some application services are controlled in a remote data center (e.g., a centralized cloud).
In a Fog Computing environment, a considerable amount of processing may occur in a data hub on a smart mobile device or on the edge of the network in a smart router or other gateway device.
This distributed approach is rising in popularity due to the Internet of Things (IoT) and the immense amount of data that sensors generate.
This research evaluates the technologies and solutions involved with distributed computing in a mobile/cellular and edge cloud environment… Read More
Flowthings Adds Real-Time Edge Processing to IoT
Excerpted from Benzinga Report
 Flowthings.io today announced the availability of comprehensive edge processing and data orchestration for Internet of Things (IoT) solutions.
Flowthings.io today announced the availability of comprehensive edge processing and data orchestration for Internet of Things (IoT) solutions.
The company’s new Edge Execution Engine now executes processing, filtering, and intelligent routing capabilities within edge gateways and devices — complementing previously released cloud processing capabilities.
Flowthings is the first IoT platform to offer real-time data orchestration on both the Edge and in the Cloud, all available on-demand and programmable from the same drag-and-drop web interface.
“The IoT is an emerging ecosystem where innumerable sensors, devices, and gateways gather and communicate real-time data to a wildly heterogeneous universe of apps, visualizations, analytics, databases and systems of record,” said Eric Alterman, Flowthings CEO.
“By enabling real-time event processing, data orchestration, routing, and interoperability between vendor solutions at the edge and in the cloud, Flowthings.io becomes the nervous system that connects entire IoT ecosystems, uniting isolated data silos.” Meanwhile, Dell IoT revealed its partnership with Flowthings in a separate announcement this week… Read More
Why the Internet of Things Needs Fog Computing
Excerpted from IoT World News Blog by Sam Oliver
 Fog Computing. We’ve been hearing a ton of buzz around it in the channel lately, but to some, it’s still a little foggy (I had to).
Fog Computing. We’ve been hearing a ton of buzz around it in the channel lately, but to some, it’s still a little foggy (I had to).
What really defines fog computing? And why all the hype?
To take a high-level look at fog computing, it essentially serves as an extension of the concepts of cloud computing at the edge.
To get a little deeper, this means fog computing extends IT capability around applications and services to edge devices like never before possible.
Before we go too deep into fog computing, we need a little background history on why it’s come to be so popular.
One of the mains reasons is due to the concept of the Internet of Things (IoT), but the reason IoT has gained major attention from many suppliers and consumers is due to the rise in cloud computing.
IoT and cloud computing go hand in hand. One does not necessarily need the other to exist, but the fact is that the information… Read More
IBM Quantum Computing Marks New Era For Cloud Computing
Excerpted from Forbes Report by Greg Satell
 Two years ago, I called the cloud the most disruptive technology ever, because it made the world’s most advanced technologies available to just about anyone with an Internet connection.
Two years ago, I called the cloud the most disruptive technology ever, because it made the world’s most advanced technologies available to just about anyone with an Internet connection.
Previously, only large enterprises that could afford to maintain expensive IT staffs could access cutting edge capabilities.
Still, while the cloud has proved to be highly disruptive, it offered few capabilities that didn’t exist before.
Sure, it made those capabilities cheaper, more efficient and more accessible, but the truth is that, outside of large data applications like Hadoop and Spark, it didn’t allow us to do much that we couldn’t do before.
IBM’s announcement today that it will make quantum computing available on its IBM Cloud platform will help change that.
For the first time, anyone who wants to will be able to benefit from a technology that virtually no one had access to before.
That, in itself, is big news. But it also opens the door to something much bigger — a truly new era for cloud computing. Take a look at a quantum computer and it’s hard to know what you’re looking at… Read More
Will Artificial Intelligence Revolutionize Cybersecurity?
Excerpted from CSM Report by Jack Tetsch
 Most people probably have no idea they encounter artificial intelligence (AI) technology at nearly every turn on the Internet.
Most people probably have no idea they encounter artificial intelligence (AI) technology at nearly every turn on the Internet.
It’s how retailers track shoppers’ behavior and show them ads that attempt to match their tastes in clothing or electronics.
While that’s a relatively simply use of AI, researchers, entrepreneurs, and US government officials are investing heavily into moving much more advanced AI into health care for such pursuits as drug research, automotive technology like self-driving cars, and even for teaching computers how to track and defend themselves against hackers.
In fact, within the past year, security startups, leading academics, government agencies, and some of the largest digital security firms in the country have invested heavily in AI technology for cybersecurity, believing that recent advancements in processing power could allow computers to outperform humans when it comes to many aspects of defending networks.
“Just imagine a world in which bots are out there looking for vulnerabilities and other bots or AI is simultaneously poking holes, plugging holes, poking back,” said Ryan Calo, a law professor and director of the Tech Policy Lab at the University of Washington, a think tank that examines cybersecurity and AI policy… Read More
FBI Hacking Ability Expanded by Supreme Court Ruling
Excerpted from Inquisitr Report by Louis Babcock
 The Supreme Court made a ruling on Thursday that will allow the FBI, and other law enforcement agencies, to expand their ability and scope when it comes to hacking into computers wherever they may be.
The Supreme Court made a ruling on Thursday that will allow the FBI, and other law enforcement agencies, to expand their ability and scope when it comes to hacking into computers wherever they may be.
Even though the Supreme Court issued the ruling, Congress needs to approve it due to the fact that it will expand the powers of law enforcement.
Prior to Thursday’s ruling, warrants could only be issued by federal judges within their own jurisdictions.
This new ruling allows any federal judge to issue a warrant for searching a computer and eliminates the lines of jurisdiction. Computers could be hacked and searched anywhere in the world as long as a federal judge signs off on it.
A case in Oklahoma has shown the need for this type of rule change.
Evidence in a child pornography had to be thrown out due to the fact that a warrant for the evidence was not properly authorized.
FBI agents had found people on the dark web who were trafficking in child pornography. A federal judge in Virginia gave the FBI a warrant… Read More
Encryption without Tears
Excerpted from Wall St. Journal Report by Senators Richard Burr and Dianne Feinstein
 In an increasingly digital world, strong encryption of devices is needed to prevent criminal misuse of data. But technological innovation must not mean placing individuals or companies above the law.
In an increasingly digital world, strong encryption of devices is needed to prevent criminal misuse of data. But technological innovation must not mean placing individuals or companies above the law.
Over the past year the two of us have explored the challenges associated with criminal and terrorist use of encrypted communications. Two examples illustrate why the status quo is unacceptable.
The first is the Islamic State-inspired terrorist attack last year in Garland, Texas. FBI Director Jim Comey said the attackers “exchanged 109 messages with an overseas terrorist” the morning of the shooting, but the FBI cannot access those messages to determine the exact role of Islamic State in the shooting and how to help prevent future attacks.
Another case involves the murder of Brittney Mills, eight months pregnant when she was shot to death last year on her front porch in Baton Rouge, La. Her unborn son was delivered at the hospital but died a week later.
Even though police found Brittney’s smartphone next to her body, the murder remains unsolved and law enforcement cannot access any information on her encrypted phone, including an electronic diary Brittney kept.
These are two of the many cases where law enforcement is unable to fully investigate terrorism or criminal activities… Read More
Why Are Internet Users Cutting the Cord?
Excerpted from eMarketer Report
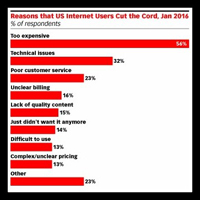 A growing percentage of American households are cutting the cable TV cord each year. According to January 2016 research, cost is one of the top reasons.
A growing percentage of American households are cutting the cable TV cord each year. According to January 2016 research, cost is one of the top reasons.
In the survey from Salesforce, more than half of US internet users said one of the reasons they have cut the cord is because it’s too expensive.
Additionally, nearly a third of said it was because of technical issues.
Poor customer service was another reason, 23% of respondents said it was. Other reasons why internet users cut the cord included unclear billing, lack of quality content, as well as the complex and unclear pricing.
Separate research from TVfreedom and The Harris Poll also revealed that most internet users believe that pay TV is too expensive.
Some 61% of internet users strongly agreed that pay TV services are too expensive. With another quarter of internet users somewhat agreeing, a whopping 86% believed on some level that pay TV was too pricy.
Just 4% of respondents said they strongly disagreed and 6% said they didn’t know… Read More
Needless Pressure to Change Copyright Laws
Excerpted from Business Line Report by Devika and Radhika Agarwal
 The recently leaked Intellectual Property chapter of the Regional Comprehensive Economic Partnership has garnered much attention worldwide.
The recently leaked Intellectual Property chapter of the Regional Comprehensive Economic Partnership has garnered much attention worldwide.
Given the imminent negotiations over the free-trade agreement between India and 15 other Asia-Pacific countries, the leaked draft gives a direct insight into the stand that participating countries would be taking over IP protection, one of the major concerns of the FTA.
The provisions relating to copyright protection are particularly worrisome, since they call for stringent measures, in excess of India’s current IP law obligations under the WTO.
Under the RCEP, each party must ratify or accede to the WIPO Copyright Treaty (WCT) and the WIPO Performances and Phonograms Treaty (WPPT). The WCT and the WPPT (together known as WIPO Internet Treaties) protect the rights of authors and performers/producers of phonograms respectively.
A unique feature of the WIPO Internet Treaties is that they provide effective legal remedies against the circumvention of technological measures taken by authors and performers/producers of phonograms to protect their works on the Internet… Read More
Coming Events of Interest
DataCloud Europe 2016 — June 8th-9th in Monte Carlo, Monaco. The 2016 conference will focus on cloud computing advances and changes in data management, with a stellar line-up of speakers including global infrastructure leaders and subject matter experts.
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
2016 Creative Storage Conference — June 23rd in Culver City, CA. The tenth annual CS will bring together digital storage providers, equipment manufacturers, software distributors, and professional media and entertainment end-users to explore the conference theme “The Art of Storage.”
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Mobile World Congress Shanghai — June 29th – July 1st in Shanghai, China. MWC Shanghai is a very unique gathering that brings together industry participants ranging from C-Level mobile executives to end-user consumers passionate about mobile.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
