In This Issue
- Citrix Taps NetApp
- Verizon Activated IO
- Telefonica & Red Hat
- Report from the CEO
- Cloud Biggest Trend
- Social Media’s Role
- Softbank & Alibaba
- SEC Slams Email Bill
- Cybersecurity Risk
- Mixed Cyber Legacy
- Random Numbers
- App Protect Platform
- US-China Group Meets
- IoT to Cloud’s Edge
- Analytics to Net Edge
- In-Memory for NUMA
- Coming DCIA Events
Citrix Taps NetApp for All-Flash Arrays
Excerpted from Citrix & NetApp Press Announcement
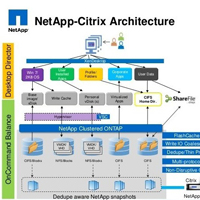 “Introducing NetApp all-flash arrays into our software development process has reduced storage latency up to tenfold, enabling us to significantly increase the number of tests we can run and the accuracy of our results,” said Satish Sambandham, Senior Manager, Product Development for Citrix.
“Introducing NetApp all-flash arrays into our software development process has reduced storage latency up to tenfold, enabling us to significantly increase the number of tests we can run and the accuracy of our results,” said Satish Sambandham, Senior Manager, Product Development for Citrix.
“NetApp all-flash arrays give our engineering team the scale-out capacity, performance, and non-disruptive operations we need to deliver new features in our flagship XenApp and XenDesktop product lines with utmost speed and quality.”
Citrix is a global technology leader with more than 300,000 customers worldwide that use its software to drive productivity and improve quality of life for workers around the globe.
Citrix constantly improves and updates its products to deliver value to customers.
However, manual testing of software was time consuming. Citrix wanted to improve efficiency and move further into DevOps by introducing new capabilities for automation.
Citrix needed a solution that could support automated testing on a large scale, drive down latency and would work well with the Citrix XenServer and NFS shared storage… Read More
Verizon Gets Activated IO to its Cloud
Excerpted from The Register Report by Chris Mellor
 Verizon business customers can now back up their data to Verizon’s cloud using Actifio copy data virtualization.
Verizon business customers can now back up their data to Verizon’s cloud using Actifio copy data virtualization.
Actifio’s basic technology makes a gold copy of primary or production data and then produces virtualized instances of it whenever a file copy is needed.
The Actifio-based on-premises Cloud Backup service uploads changed blocks from virtualized applications and sends them to Verizon’s cloud.
In previous incarnations of the technology, Actifio sends the data to a remote site to provide business continuity and disaster recovery.
Verizon is calling its offering “Premise to Cloud Backup” and says once the data is in the cloud, it can be used for application test and development.
It is using the Actifio technology as a pipeline so that data and apps can be moved to/from Verizon’s cloud to on-premises data centers as workload demands change.
In effect Actifio’s tech is being used as a cloud storage gateway, with customers having a hybrid on-premises/Verizon cloud IT set-up… Read More
Telefonica & Red Hat Mobilize Business Processes
Excerpted from VanillaPlus Report by Sheetal Kumbhar
 Red Hat a provider of open source solutions, and Telefonica Business Solutions, a provider of a wide range of integrated communication solutions for the B2B market, have agreed to establish Red Hat Mobile Application Platform as the global reference platform for operators within the Telefonica Group to mobilize the business processes of its customers on their path to digital transformation.
Red Hat a provider of open source solutions, and Telefonica Business Solutions, a provider of a wide range of integrated communication solutions for the B2B market, have agreed to establish Red Hat Mobile Application Platform as the global reference platform for operators within the Telefonica Group to mobilize the business processes of its customers on their path to digital transformation.
The Red Hat Mobile Application Platform has been used by Telefonica in some markets since 2012, completing Telefonica’s Group Enterprise Managed Mobility proposition, as it provides users an open, agile, and collaborative approach to developing, integrating, and deploying mobile applications.
A collaborative approach to mobile, enabled by open standards-based technologies such as the Red Hat Mobile Application Platform, can help facilitate greater mobile adoption and maturity, as well as reduce both costs and time to market.
Organizations are increasingly investing in mobile application development to help transform the way they do business by reinventing business processes, automating existing processes, and mobilizing legacy web applications.
To match the rate at which mobile is evolving in the enterprise, and better meet challenges such as security, scalability, and integration… Read More
Report from DCIA CEO Marty Lafferty
 The DCIA is pleased to partner with Informa Telecoms & Media on Cloud and DevOps World, which will focus on strategies, business models, and technologies that can activate the cloud and drive new opportunities for organizations worldwide.
The DCIA is pleased to partner with Informa Telecoms & Media on Cloud and DevOps World, which will focus on strategies, business models, and technologies that can activate the cloud and drive new opportunities for organizations worldwide.
With less than a month until the 2016 conference kicks off, on June 21st in London, England, I wanted to remind you to register now to attend the event.
Informa is a leading business intelligence, academic publishing, knowledge and events business, operating within the knowledge and information economy.
It serves commercial, professional, and academic communities in many different sectors by helping them connect and learn, and by creating and providing access to content and intelligence that helps people and businesses work smarter and make better decisions faster.
Informa has over 6,500 colleagues around the world, with a presence and customers in North and South America, Asia, Europe, the Middle East and Africa.
Cloud & DevOps World will provide opportunities to drive businesses into the digital economy and realize the potential of cloud computing.
Speakers include representatives from major brands such as Airbus, Amazon Webs Services, Hotels.com, Ikea, Lufthansa, Ovum, Red Hat, Sony, Twitter, and Vistaprint to name a few of the more than one-hundred who will make presentations and participate in discussions.
With experts from industry leading companies like these offering case studies and thought leadership guidance at the event, can you afford to miss out?
If you’re an employee of a DCIA Member Company or a qualified DCINFO reader, you’ll be able to attend the event for free and simply need to register online here.
Otherwise, passes are attractively priced, and you can register here.
All registrations are subject to availability and issued on a first-come-first-served basis.
Still not convinced? For more information please visit the conference agenda.
We hope to welcome you at the Cloud and DevOps World from June 21st through 22nd at Olympia in London. Share wisely and take care.
Cloud Computing Will Be 2016’s Biggest IT Trend
Excerpted from Vanguard Report by Emeka Aginam
 Information and communications technology (ICT) stakeholders in Africa, recently, in Lagos, admitted that cloud computing would be one of the mega-trends in the information technology (IT) field in 2016.
Information and communications technology (ICT) stakeholders in Africa, recently, in Lagos, admitted that cloud computing would be one of the mega-trends in the information technology (IT) field in 2016.
The forecast was made at the just concluded Huawei Cloud Congress West Africa in Nigeria.
The event, which was in its second edition, had the theme “Transforming with Cloud, Setting New Benchmarks.”
It also provided an opportunity for Huawei to share its vision and ideas about the future and strategies on how to work together with various industries in order to advance ICT, and showcase its experiences in IT.
The over 200 industry stakeholders who participated at the event noted that to adapt effectively, telecom carriers and big businesses must change their business models, build ecosystems, add new infrastructure, develop organizations and processes, and learn new skills.
They argued that IT has shifted from being a support system to a business and production system even as the emergence of technologies represented by cloud computing are driving the need to change and reshape IT.
For instance, IDC, at the summit forecast that cloud computing will be one of 2016’s IT mega-trends… Read More
Social Media’s New Role as Content Curator
Excerpted from NY Times Report by John Herrman
 By the end of last week, Mark Zuckerberg said that Facebook would conduct “a full investigation” into accusations that editors at the company prevented news stories from conservative outlets from appearing in a section of the social network’s service.
By the end of last week, Mark Zuckerberg said that Facebook would conduct “a full investigation” into accusations that editors at the company prevented news stories from conservative outlets from appearing in a section of the social network’s service.
But the statement, issued after a weeklong crush of attention about the accusation, leapfrogged a perhaps more obvious question — one that Facebook’s 1.65 billion monthly users around the world may not have considered.
Facebook has editors?
It does, and it isn’t alone. Most major social media platforms have, in recent years, amassed editorial teams of their own, groups that select, tame and fill gaps in the material produced by users and media companies.
The teams are often tiny compared with the rest of their sprawling organizations.
But most of these employees — whether they are called curators, reporters, editors or something else — make editorial choices that reach huge audiences. How and why these decisions are made are generating new questions for the companies, and their users, to grapple with… Read More
Softbank & Alibaba Group Form Cloud JV
Excerpted from Telecomasia Report by Fiona Chau
 Alibaba Group has teamed up with its largest shareholder Softbank Group to provide public cloud computing services in Japan.
Alibaba Group has teamed up with its largest shareholder Softbank Group to provide public cloud computing services in Japan.
The two announced on Friday that they have formed a joint venture, called SB Cloud Corp, to deliver Alibaba Cloud’s technology and services for Japanese enterprises, ranging from start-ups to multinational companies.
Softbank, the telecom subsidiary of Softbank Group, owns 60% stake in the venture and Alibaba Group holds the remaining shares, the companies said.
The Tokyo-headquartered JV, incorporated in January, will open a new data center in Japan and provide Japanese enterprises with Alibaba Cloud’s data storage and processing services, enterprise-level middleware as well as cloud security services.
The companies said SB Cloud will play a key role in supporting Alibaba Cloud’s business presence in the Japan market where demand for public cloud computing services is growing rapidly.
The pair added that the deal enables Alibaba Cloud to further expand its cloud computing service platform with SoftBank… Read More
SEC Commissioners Slam Email Privacy Bill
Excerpted from Securities Law Daily Report by Bob Tricchivelli
 Members of the Securities and Exchange Commission (SEC) oppose a piece of legislation that would require the federal government to get a warrant in order to obtain old emails during an investigation.
Members of the Securities and Exchange Commission (SEC) oppose a piece of legislation that would require the federal government to get a warrant in order to obtain old emails during an investigation.
At issue is HR 699, which passed the House unanimously in April.
The bill would undo part of the Electronic Communications Privacy Act (ECPA) that considers email messages more than 180 days old “abandoned” and allows them to be gathered by investigators with a subpoena or a court order instead of a warrant.
Because the SEC lacks the authority to obtain criminal warrants, the bill would stifle the agency’s investigative powers and make it impossible to obtain information from Internet service providers (ISPs), SEC Chairman Mary Jo White and Commissioners Kara Stein and Michael Piwowar said in a May 11th letter to Senate Judiciary Committee Chairman Charles Grassley (R-IA).
“This would be true even in situations where the ISP is the only available source, such as when a subscriber deletes his emails, or when hardware is lost or damaged, or the subscriber flees to another jurisdiction,” the Commissioners wrote… Read More
DCINFO Editor’s Note: The DCIA participates in the Digital Due Process (DDP) coalition, which advocates Senate passage of a companion measure for HR 699.
SEC Says Cybersecurity Biggest Risk to System
Excerpted from Reuters Report by Lisa Lambert & Suzanne Barlyn
 Cybersecurity is the biggest risk facing the financial system, the Chair of the US Securities and Exchange Commission (SEC) said on Tuesday, in one of the frankest assessments yet of the threat to Wall Street from digital attacks.
Cybersecurity is the biggest risk facing the financial system, the Chair of the US Securities and Exchange Commission (SEC) said on Tuesday, in one of the frankest assessments yet of the threat to Wall Street from digital attacks.
Banks around the world have been rattled by a $81 million cyber theft from the Bangladesh central bank that was funneled through SWIFT, a member-owned industry cooperative that handles the bulk of cross-border payment instructions between banks.
The SEC, which regulates securities markets, has found some major exchanges, dark pools, and clearing houses did not have cyber-policies in place that matched the sort of risks they faced, SEC Chair Mary Jo White told the Reuters Financial Regulation Summit in Washington, DC.
“What we found, as a general matter so far, is a lot of preparedness, a lot of awareness, but also their policies and procedures are not tailored to their particular risks,” she said.
“As we go out there now, we are pointing that out.”
White said SEC examiners were very pro-active about doing sweeps of broker-dealers and investment advisers to assess their defenses… Read More
A Mixed Legacy on Cyber for Obama
Excerpted from FCW Report by Sean Lyngaas
 President Barack Obama has shepherded billions of dollars of investments toward cybersecurity programs, created senior federal IT positions, and set up a blue-ribbon panel to explore the issue years down the road.
President Barack Obama has shepherded billions of dollars of investments toward cybersecurity programs, created senior federal IT positions, and set up a blue-ribbon panel to explore the issue years down the road.
But will that be enough for history to judge him favorably on cyber-policy?
A group of former federal officials on May 18th delivered a mixed verdict: the Obama administration has done well to make cybersecurity relevant to top agency officials and not just techies, but should have done more to follow through on key policies.
At the center of the Obama legacy will be a voluntary framework that companies can use to assess their cybersecurity risk.
The National Institute of Standards and Technology (NIST) oversaw the development of the framework following a 2013 executive order from Obama. Administration officials have touted the framework’s adoption in the US private sector, and promoted it as a model for other countries.
Nonetheless, some in industry say implementation of the framework has been slowed by a lack of clear data on its cost effectiveness… Read More
Random Numbers Approach for Cybersecurity
Excerpted from Phys.org Report
 With an advance that one cryptography expert called a “masterpiece,” University of Texas at Austin computer scientists have developed a new method for producing truly random numbers, a breakthrough that could be used to encrypt data, make electronic voting more secure, conduct statistically significant polls and more accurately simulate complex systems such as Earth’s climate.
With an advance that one cryptography expert called a “masterpiece,” University of Texas at Austin computer scientists have developed a new method for producing truly random numbers, a breakthrough that could be used to encrypt data, make electronic voting more secure, conduct statistically significant polls and more accurately simulate complex systems such as Earth’s climate.
The new method creates truly random numbers with less computational effort than other methods, which could facilitate significantly higher levels of security for everything from consumer credit card transactions to military communications.
Computer science professor David Zuckerman and graduate student Eshan Chattopadhyay will present research about their method in June at the annual Symposium on Theory of Computing (STOC), the Association for Computing Machinery’s premier theoretical computer science conference.
An invitation to present at the conference is based on a rigorous peer review process to evaluate the work’s correctness and significance.
Their paper will be one of three receiving the STOC Best Paper Award… Read More
Fraud Prevention App Protection Platform
Excerpted from Networks Asia Report by Boo Leong Khoo
 Financial institutions and online service providers are engaging customers via a widening array of channels as part of their digital transformation strategies.
Financial institutions and online service providers are engaging customers via a widening array of channels as part of their digital transformation strategies.
Today, it is commonplace for services to be offered and transacted via different end points such as the browser and mobile devices.
However, even as more critical services move online or to the cloud, fraud and the increasingly complex ways that cyber-criminals carry them out remains the key issue for banks and consumers, according to Lim Chin Keng, Director of Security Solutions for APAC at F5 Networks.
For example, account takeover is increasingly becoming a pervasive online fraud.
“The fraudster or cyber-criminal obtains the victim’s password and other personal identifiable information (PII) to carry out an unauthorized login to an account and perform transactions without the victim’s knowledge,” says Lim.
“Financial malware or trojan that may have been unknowingly installed or embedded on the user’s device can easily steal a victim’s login credentials. This is also known as a man-in-the-middle (MITM) attack.”
While attackers often target individuals via the client endpoint, which is seen as the weakest link, through MITM attacks… Read More
US-China Cyber Group Holds First Meeting
Excerpted from The Hill Report by Katie Bo Williams
 A group of senior officials from the United States and China on Wednesday held its first meeting on cybersecurity issues in accordance with an anti-hacking pledge struck by the two nations in September.
A group of senior officials from the United States and China on Wednesday held its first meeting on cybersecurity issues in accordance with an anti-hacking pledge struck by the two nations in September.
The so-called Senior Experts Group addressed “international norms of state behavior and other crucial issues for international security in cyberspace,” according to a State Department statement that provided few other details.
The meeting was led on the US side by Christopher Painter, Coordinator for Cyber Issues at State, and Wang Qun, Director-General of the Department of Arms Control in China’s Ministry of Foreign Affairs, on the Chinese side.
Other officials from the State Department, the Department of Defense (DoD), Department of Justice (DoJ), and Department of Homeland Security (DHS) were also present.
The group is expected to meet twice a year.
Cybersecurity — specifically, allegations of wholesale pilfering of U.S. data by Beijing-backed hackers — has long haunted the US-China trade relationship.
In September, the two nations struck a deal that neither would hack the other for commercial gain… Read More
IoT Has to Move to the Cloud’s Edge
Excerpted from info World Report by David Linthicum
 I attended “Internet of Things (IoT) World” in Santa Clara, CA, this week and served as the track chairman for, you guessed it, Cloud and IoT.
I attended “Internet of Things (IoT) World” in Santa Clara, CA, this week and served as the track chairman for, you guessed it, Cloud and IoT.
The vibe I got throughout the event was one of confusion: IoT seems to be so systemic, yet is difficult to define.
As one presenter put it, “It’s like plastic. It’s going to be a part of everything.”
In the context of the IoT, the trouble with the cloud is that data needs to be sent back from the sensors gathering info, such as a Nest thermostat or a Fitbit, to a database in a remote public cloud.
The time that it takes for the data to be transferred from the device or sensor to the remote public cloud — that is, the latency — is often too much to meet the requirements of the IoT system.
We need to do something different — and we can start by doing IoT applications at the cloud’s edge.
This means that we avoid sending all data from sensors and devices back to the cloud, but instead build data and applications on the edge of the network that can handle most of the data gathering and processing… Read More
Bringing IoT Analytics to the Network Edge
Excerpted from Engineering.com Report by Shawn Wasserman
 IoT data is kind of like the attic of a house. It has a way of collecting objects and files that might be useful — if you can only remember where it is.
IoT data is kind of like the attic of a house. It has a way of collecting objects and files that might be useful — if you can only remember where it is.
Data on the IoT is ever-growing, and the computational expense and latency of central cloud-based analytics means more of this data will go unused.
As the IoT looks set to increase from 6.4 billion devices in 2016 to 20.8 billion devices by 2020, according to Gartner, it’s clear that this messy attic won’t clean itself.
“IoT promises significant advances for users, but the fact that only 10 percent of IoT data even makes it to the cloud proves that current analytics solutions are too reliant on central processing to be effective,” said Simon Arkell, CEO of Predixion Software.
This means the IoT industry needs to find a new way to process this data to ensure it is being used to its full potential.
Enter the cleaning crew: edge computing technologies.
Using Predixion RIOT, engineers will be able to make better use of edge computing… Read More
In-Memory Breathes New Life into NUMA
Excerpted by The Next Platform Report by Timothy Morgan
 Hyperscalers and the academics that often do work with them have invented a slew of distributed computing methods and frameworks to get around the problem of scaling up shared memory systems based on symmetric multiprocessing (SMP) or non-uniform memory access (NUMA) techniques that have been in the systems market for decades.
Hyperscalers and the academics that often do work with them have invented a slew of distributed computing methods and frameworks to get around the problem of scaling up shared memory systems based on symmetric multiprocessing (SMP) or non-uniform memory access (NUMA) techniques that have been in the systems market for decades.
SMP and NUMA systems are expensive and they do not scale to hundreds or thousands of nodes, much less the tens of thousands of nodes that hyperscalers require to support their data processing needs.
It sure would be convenient if they did.
But for those who are not hyperscalers, like HPC centers or large enterprises, the good news is that they generally do not need tens of thousands of nodes and hundreds of thousands of cores to do analytics or simulation, and that means SMP or NUMA systems that scale to dozens or perhaps hundreds of nodes are particularly useful because the shared memory in these machines, at tens of terabytes, is sufficiently large enough to hold their datasets and do processing across a high speed memory fabric instead of an Ethernet, InfiniBand, or PCI-Express fabric.
And thus, we are seeing the continuing adoption of big memory iron in the market, even in the era of very mature distributed computing… Read More
Coming Events of Interest
DataCloud Europe 2016 — June 8th-9th in Monte Carlo, Monaco. The 2016 conference will focus on cloud computing advances and changes in data management, with a stellar line-up of speakers including global infrastructure leaders and subject matter experts.
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
2016 Creative Storage Conference — June 23rd in Culver Cirty, CA. The tenth annual CS will bring together digital storage providers, equipment manufacturers, software distributors, and professional media and entertainment end-users to explore the conference theme “The Art of Storage.”
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Mobile World Congress Shanghai — June 29th – July 1st in Shanghai, China. MWC Shanghai is a very unique gathering that brings together industry participants ranging from C-Level mobile executives to end-user consumers passionate about mobile.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
