In This Issue
- AWS Is 10 Years Old
- VDMS Buys Volicon
- Vendors Pick NetApp
- Report from the CEO
- VZ Data Brief Digest
- John Kasich Vows
- ABI Research on VM
- Anonymous vs Trump
- Cybersecurity Chart
- Large Co Net Security
- Small Biz Breaches
- Cloud Scares Trend?
- NetApp Free Support
- Data Governance Key
- Behind NetApp Focus
- The Dragonslayer
- Coming DCIA Events
Amazon’s Cloud Computing Business Turns Ten
Excerpted from Techwire Report by Angel Gonzalez
 Amazon’s cloud-computing business turned 10 years old Monday, a short but fast-paced life that has revolutionized the technology industry and strongly contributed to Seattle’s economic boom.
Amazon’s cloud-computing business turned 10 years old Monday, a short but fast-paced life that has revolutionized the technology industry and strongly contributed to Seattle’s economic boom.
The real growth spurt for Amazon Web Services (AWS), however, may yet lie ahead.
What started as a service to provide cheap storage for software developers soon added computer power for rent on a pay-as-you-go basis, enabling a new generation of Web-oriented startups such as Airbnb and Pinterest to focus on building apps rather than the technology infrastructure to support their products.
It’s such a moneymaking machine that when its financial record was first publicly disclosed in April 2015, its shares soared to new heights.
In 2015, AWS accounted for 41 percent of Amazon’s profit, though it was only 7 percent of its revenue (some analysts expect AWS’ operating profit to surpass that of Amazon’s retail segment starting this year.)
Now, as big companies and even national governments jump on the bandwagon, analysts say cloud computing is still in its infancy. It’s a business, moreover, that Amazon dominates to a great extent, although it’s being increasingly penetrated by rivals… Read More
Verizon Digital Media Services Acquires Volicon
Excerpted from TVTechnology Report by Michael Balderston
 Volicon is now a part of the Verizon Digital Media Services family, as the two companies announced an agreement that will see Verizon acquire the video capture, archival, compliance monitoring and clip creation workflows provider.
Volicon is now a part of the Verizon Digital Media Services family, as the two companies announced an agreement that will see Verizon acquire the video capture, archival, compliance monitoring and clip creation workflows provider.
Now a part of AOL, Verizon Digital Media Services says Volicon will enable content creators, publishers, broadcasters and enterprises to deliver their content to audiences on any device.
“Volicon’s role as a trusted provider to more than 1,200 broadcast and video operators around the world, combined with deep expertise in video monitoring and analysis, will improve visibility, transparency, and quality of our clients content and ads over our global delivery footprint,” said Bob Toohey, Verizon Digital Media Services President.
Combining Volicon’s technology with Verizon’s Video Lifecycle Solution will reportedly provide customers an option to take broadcast feeds and channels directly to OTT cloud-based delivery models.
Both companies already have complementary video workflow tools that generate assets, clips, highlights and social sharing opportunities from existing live, linear and VOD workflows.
Volicon was founded in 2005 by Eli Warawski, Julius Perl and Yehuda Brand. Terms of the deal were not disclosed… Read More
Media Vendors Adopt NetApp StorageGRID Webscale
Excerpted from Infotech Lead Report
 NetApp said leading media vendors have adopted its StorageGRID Webscale object storage through partner integration and customer implementation.
NetApp said leading media vendors have adopted its StorageGRID Webscale object storage through partner integration and customer implementation.
StorageGRID Webscale is a scalable, software-defined object storage solution for large media repositories, cloud DVRs, and websites and social media sites.
In the past 12 months, media vendors — Aspera, Cantemo, Dalet, OpenText (through CyanGate), Primestream, Signiant, Silvertrak, Spectra Logic, and Vidispine — have validated their Amazon
Simple Storage Service (S3) interface with StorageGRID Webscale.
NetApp said the partner integration provides broadcast and film studios with intelligent policy-driven data management for the entire content lifecycle.
In addition, StorageGRID Webscale helps several customers store more than 50 billion media assets.
“With these new integrations, broadcasters, studios, and media cloud providers are able to enhance existing workflows… Read More
Report from DCIA CEO Marty Lafferty
 President Obama’s recently announced Commission for Enhancing National Cybersecurity intends to produce a set of actionable recommendations for the next President by December 1st.
President Obama’s recently announced Commission for Enhancing National Cybersecurity intends to produce a set of actionable recommendations for the next President by December 1st.
The commission plans to develop its proposal in collaboration with the private sector.
The DCIA sees potential in this opportunity to create a stronger relationship between government and industry.
But how do the candidates for President stack-up on the issue of cybersecurity?
Data risk management firm IDT911 researched the subject and compiled its findings in a chart that allows for side-by side comparisons.
Interestingly, the only major issue where opinion is divided along party lines is FCC Net Neutrality.
Both Democratic contenders Hillary Clinton and Bernie Sanders support it, while Republicans Donald Trump and Ted Cruz oppose it. Republican John Kasich’s stance is unclear.
Opinions vary on other topics.
Clinton, Sanders, Cruz, and Kasich all oppose renewal of the NSA program for collecting phone metadata records from US carriers. Trump is the only candidate who supports continuing it.
The USA Freedom Act is supported by Clinton and Cruz, who co-sponsored the bill.
Sanders and Trump oppose it, though for different reasons.
Sanders because he thinks it doesn’t go far enough to ensure privacy protections, while Trump because he thinks it weakens intelligence systems.
There’s a greater consensus on China. Clinton, Trump, and Cruz blame China for the massive attack on the Office of Personnel Management (OPM) last year. While Sanders and Kasich have not weighed in on this.
The candidates did not receive high marks overall for their cybersecurity and privacy policies.
Clinton was faulted for being on the wrong side of the encryption debate, as well as for showing poor judgment on her private email server.
Trump was called out for his lack of clarity on many cybersecurity topics and not understanding the nuances of the security versus privacy debate.
Sanders was criticized for having a weak stance on Net Neutrality.
As the election process advances, we urge industry participants to continue to ask questions, and join us in doing all we can to compel the candidates to take this issue seriously, and to define their positions with greater clarity.
Share wisely, and take care.
Verizon Data Breach Digest Provides Security Insights
Excerpted from NetworkWorld Report by Tim Greene
 At the 2016 RSA Conference, Network World’s Tim Greene chatted with Bryan Sartin, a Director at Verizon, about its new Data Breach Digest, and the insights it offers to enterprises looking to protect their systems.
At the 2016 RSA Conference, Network World’s Tim Greene chatted with Bryan Sartin, a Director at Verizon, about its new Data Breach Digest, and the insights it offers to enterprises looking to protect their systems.
In one case pirates — actual pirates — boarded cargo ships armed with a list of which shipping containers contained jewelry and went straight to them, stole the gems and left.
In another, attackers took control of the mainframe at a water district, mixed sewage with the drinking water, boosted the chlorine to dangerous levels and stole customer information.
These are two of 18 representative case studies in Verizon’s new Data Breach Digest, a compendium of anonymized customer investigations performed by the company’s Research, Investigations, Solutions and Knowledge (RISK) Team and released at RSA Conference 2016.
The Data Breach Digest, new this year, is a companion to Verizon’s well established annual Data Breach Investigations Report (DBIR), which is heavy on metrics, graphs and statistics about cyber-threat trends, how to predict them and how to prevent them. The Data Breach Digest tells the stories behind the metrics that give readers a trench-level view… Read More
John Kasich Vows to Retaliate Against Hackers
Excerpted from Washington Times Report by Andrew Blake
 Ohio Governor John Kasich said during Thursday’s GOP presidential debate that he’d “beef-up” the US Cyber Command as President and make sure the military is able to launch offensive attacks against critical infrastructure abroad.
Ohio Governor John Kasich said during Thursday’s GOP presidential debate that he’d “beef-up” the US Cyber Command as President and make sure the military is able to launch offensive attacks against critical infrastructure abroad.
Mr. Kasich was responding to a question about the Chinese government when he told moderator Jake Tapper that the next commander in chief must ensure the U.S. is able to fire back against state-sponsored hackers.
“When it comes to the issue of cyber-attacks, we’re going to have to beef-up the cyber command,” he said.
“And they need to understand that if you attack us, we will defend ourselves, everything, including our grid.”
“But if you do it, we have the capability to take out your systems.”
“The President has not given the Cyber Command that authority. I will.”
“They have to stop hacking everything we have in this country, or we’ll take out their systems,” Mr. Kasich said later during the debate.
The US government has largely blamed China for a wave of recent data breaches affecting US corporate and government entities… Read More
ABI Research: Cloud & Big Data to Drive VM Market
Excerpted from ABI Research Press Announcement
 ABI Research, the leader in transformative technology innovation market intelligence, expects cloud computing and big data to drive the global threat and vulnerability management (VM) market to increase from its current standing at $5.8 billion in revenue in 2015 to $8.6 billion by 2020.
ABI Research, the leader in transformative technology innovation market intelligence, expects cloud computing and big data to drive the global threat and vulnerability management (VM) market to increase from its current standing at $5.8 billion in revenue in 2015 to $8.6 billion by 2020.
Nefarious security attacks are driving market growth and subsequently increasing the number of VM solutions available to protect people and organizations.
As vulnerability assessment (VA) is a key component of a VM program, ABI Research calculates total revenues generated by the VA market to reach $1.4 billion by the end of 2016 and grow to $2.1 billion by 2020.
“There is increasing market demand for vulnerability management solutions, like the IBM QRadar Security Intelligence Platform, Barracuda Vulnerability Manager, AlienVault Unified Security Management solution, and Rapid7 Nexpose 6.0,” says Monolina Sen, Senior Analyst at ABI Research.
“The ideal VM solution is one that integrates well with third-party technologies and includes capabilities for asset management, configuration management, patch management, VA, remediation, reporting, and monitoring… Read More
Anonymous Declares Cyber War on Donald Trump
 The hacking group Anonymous is urging its followers to launch a barrage of cyber-attacks on April 1st to take down Donald Trump‘s websites and expose the “appalling” GOP presidential candidate.
The hacking group Anonymous is urging its followers to launch a barrage of cyber-attacks on April 1st to take down Donald Trump‘s websites and expose the “appalling” GOP presidential candidate.
“We need you to shut down his websites, research and expose what he doesn’t want the public to know,” a person wearing the group’s trademark Guy Fawkes mask says in a video posted by to an Anonymous YouTube channel.
“We need you to dismantle his campaign and sabotage his brand.”
In a separate written statement, Anonymous encouraged hackers to target the business mogul’s websites, including donaldjtrump.com, trump.com and trumphotelcollection.com.
Anonymous also released Trump’s alleged personal details, such as his cellphone number and Social Security number, to help hackers harass the Republican presidential front-runner.
“Dear Donald Trump, we have been watching you for a long time, and what we see is deeply disturbing,” the video says.
“You have shocked the entire planet with your appalling actions and ideals… Read More
Chart Explains Why Cybersecurity Is So important
Excerpted from Business Insider Report by Andrew Meola
 New hacking threats have emerged in the past two years, and with them have come a large increase in worldwide concern about cybersecurity.
New hacking threats have emerged in the past two years, and with them have come a large increase in worldwide concern about cybersecurity.
In 2014, 69% of executives expressed concerned about cyber-threats, including a lack of data security, according to a PricewaterhouseCoopers survey.
In 2015, an updated survey increased that number to 86%, so it’s clear that the desire for better cybersecurity is not going away anytime soon.
In an infographic, John Greenough of BI Intelligence, Business Insider’s premium research service, explains what cybersecurity is, what the investment will be, the top types of attacks, and the ways enterprises are protecting themselves.
If you find this infographic to be valuable, then you will LOVE our two extensive reports on IoT security and cyber insurance.
The IoT Security Report: This report examines how vulnerable IoT devices will create new opportunities for different types of hackers… Read More
Network Security Incidents High at Largest Companies
Excerpted from Channel Partners Report by Edward Gately
 A new survey of IT and security professionals reveals that 72 percent of organizations have experienced five or more network security incidents in the past 12 months.
A new survey of IT and security professionals reveals that 72 percent of organizations have experienced five or more network security incidents in the past 12 months.
Frost & Sullivan conducted the survey of Global 2000 companies in the United States, the United Kingdom and Germany, for network and Internet of Things (IoT) security company ForeScout.
It asked questions about security breaches and the effectiveness of certain network security tools.
Regardless of region or technology, IT and security administrators revealed that their networks have significant blind spots, underscoring that too many organizations deploy network security technologies in silos with little or no communication between products and teams, according to the survey.
Also, respondents reported low confidence in their patch-management agents (37 percent), mobile-device management agents (35 percent), encryption agents (28 percent) and antivirus agents (27 percent).
“The data found that an average of 60 percent of organizations say they are ready for automation on a variety of their controls, including antivirus, advanced threat detection (ATD) and firewalls,” said Rob Greer, ForeScout’s CMO & SVP of Products… Read More
Small Businesses Also Need to Know about Data Breaches
Excerpted from Business News Daily Report by Nicole Taylor
 Cybersecurity is an issue that’s probably on the mind of every business owner.
Cybersecurity is an issue that’s probably on the mind of every business owner.
The growing list of corporate data breaches, coupled with the more-secure EMV credit card chip technology that emerged last year, has made businesses and consumers alike highly aware of the security risks that exist in today’s world.
Despite numerous studies and statistics on hackers targeting small businesses, many owners still have an, “It won’t happen to me” attitude about security.
This is a dangerous way of thinking that could ultimately leave your business open to a whole host of potential risks.
“Many small business owners underestimate how vulnerable they are to security threats,” said Sanjay Castelino, Vice President of Marketing at Spiceworks, a provider of information technology solutions.
“Our recent IT security report shows business owners are facing a number of threats from malware to phishing to ransomware, and the attackers range from lone hackers to rogue employees.
Once a business is successfully attacked, earning back customer trust and fixing the damage is often too costly for small companies… Read More
Are Cloud Computing Scares a Dying Trend?
 Are cloud computer scares a dying trend?
Are cloud computer scares a dying trend?
Cloud computing is on the rise, but behind the virtual cloud there isn’t always a silver lining.
In recent months the mainstream media has picked up on some serious issues with the cloud services of some major companies and organizations — and that’s caused some to question the safety of this technology.
Indeed, whether it was the ASUS incident where the company put thousands of users at risk by failing to fix a flaw in their routers or the LA Hospital security breach where malware in an email allowed hackers to lockdown the system and demand a ransom, cloud services have taken a beating recently.
There are a number of benefits to servers in the sky
Fortunately however, incidents such as those outlined above are few and far between and despite some of the negative press, cloud services are now changing our virtual lives.
The Internet is becoming a much more intricate place thanks to servers in the sky… Read More
NetApp Flash Storage Channel Consultancy Support
Excerpted from ChannelBiz Report by Antony Savvas
 Liquidware Labs and NetApp have launched a free program for consultants and partners to be able to deliver audits of their customers’ environments in order to quantify the benefits of deploying flash storage solutions.
Liquidware Labs and NetApp have launched a free program for consultants and partners to be able to deliver audits of their customers’ environments in order to quantify the benefits of deploying flash storage solutions.
The VDI PULSE program is based on Liquidware Labs’ Stratusphere UX and includes a custom-generated report designed in collaboration between NetApp and Liquidware Labs engineering teams.
“The high performance and enterprise-grade management capabilities of NetApp All Flash FAS arrays make it easier and faster for enterprises to adapt to new opportunities while delivering consistent customer experiences,” said Maria Olson, Vice President, Global and Strategic Alliances at NetApp.
“This custom-developed offer from Liquidware Labs and NetApp will further help customers deploying VDI solutions maximize the performance for their mission critical applications.”
The objective of the VDI PULSE program is to deliver a simple, fast and comprehensive audit to support NetApp partners and field consultants.
The detailed analysis is segmented into three main areas… Read More
Data Governance Key to Safe Cloud Computing
Excerpted from Arab News Report by Mamdouh Najjar
 A recent report on Managed Datacenters and Cloud Services in Saudi Arabia, issued by the Communications and Information Technology Commission, indicated that cloud computing services ranked third among the services that witnessed the most tremendous growth between 2011 and 2014.
A recent report on Managed Datacenters and Cloud Services in Saudi Arabia, issued by the Communications and Information Technology Commission, indicated that cloud computing services ranked third among the services that witnessed the most tremendous growth between 2011 and 2014.
Spending on cloud services totaled SR189 million with a growth rate of 373 percent.
The study also showed that cloud computing services are expected to grow rapidly over the next five years, surpassing SR476 million in 2019.
The study showed that many organizations are realizing that procuring cloud services can give them access to better technology than they could implement or purchase on their own.
We can, therefore, feel that user confidence in cloud computing services is increasingly growing day after day.
However, full-scale cloud services adoption in public and private sector organizations is hindered by many concerns and challenges.
A major challenge is trust — in protecting the security and privacy of the company’s data… Read More
Behind NetApp’s Focus on Strategic Solutions
Excerpted from Market Realist Report by Adam Rogers
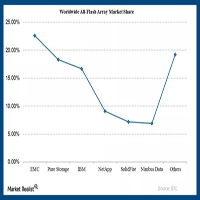 NetApp CEO George Kurian has stated that the firm will focus on strategic solutions “that represent our pivot to the growth segments of the market and are the foundation of how we enable customers’ success in the data-powered digital era.”
NetApp CEO George Kurian has stated that the firm will focus on strategic solutions “that represent our pivot to the growth segments of the market and are the foundation of how we enable customers’ success in the data-powered digital era.”
Kurian further stated that “as a baseline, our focus remains in enabling our customer success, as they navigate through their own IT transmissions, which leverage modern architectures and hybrid cloud solutions.”
Kurian also specified that “clustered ONTAP, branded E-Series, All-Flash arrays, hybrid cloud solutions, and OnCommand Insight are the set of strategic solutions that are the basis of our pivot to the growth segments of the market.”
Although NetApp has experienced impressive growth rates in its strategic solutions segment, these have not been sufficient to offset the headwinds from the mature areas of its business.
NetApp anticipates that its pivot toward growth areas in the market will positively impact revenue growth in the coming years, particularly as original equipment manufacturers (OEMs) and ONTAP 7-Mode becomes a smaller part of the company’s mix.
According to the research firm IDC, only Hewlett Packard experienced revenue growth in 2015… Read More
The Dragonslayer
Excerpted from The Verge Report by Nilay Patel
 Two years ago, John Oliver called Tom Wheeler a dingo.
Two years ago, John Oliver called Tom Wheeler a dingo.
The host of Last Week Tonight had set his sights on the then-raging net neutrality debate, acerbically calling out broadband providers like Comcast and Verizon for their throttling antics and intense Congressional lobbying.
Midway through the segment, Oliver dryly pointed to President Obama’s appointment of former cable and wireless lobbyist Wheeler as the new head of the Federal Communications Commission — “the equivalent of needing a babysitter and hiring a dingo.”
“Now that they are overseeing their own oversight, it is hardly surprising that cable companies are basically monopolies,” said Oliver.
This claim — that the FCC has been captured by the very interests it is supposed to regulate — has been around for years.
The path from a Commission seat to an aisle seat inside Comcast’s private jet and vice versa has been wide open for years: former FCC Chairman Michael Powell is now the President of the National Cable and Telecom Association… Read More
Coming Events of Interest
IoT Asia 2016 — March 30th-31st in Singapore. IoT Asia returns in 2016 with fresh insights on Internet of Things (IoT) developments around the world. The 3rd edition aims to further advance conversations and ideas on IoT and how it will impact our lives by delving into the real issues.
Delivery of Things World — April 25th-26th in Berlin, Germany. DevOps specialists, continuous development strategists, architect newbies, development geeks, and cloud geniuses from across the spectrum of DevOps transformation come together at this stimulating and innovative event.
DataCloud Europe 2016 — June 8th-9th in Monte Carlo, Monaco. The 2016 conference will focus on cloud computing advances and changes in data management, with a stellar line-up of speakers including global infrastructure leaders and subject matter experts.
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Mobile World Congress Shanghai — June 29th – July 1st in Shanghai, China. MWC Shanghai is a very unique gathering that brings together industry participants ranging from C-Level mobile executives to end-user consumers passionate about mobile.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
