In This Issue
GOP Chairman Makes Change to Email Privacy Bill
Excerpted from The Hill Report by Mario Trujillo
 Email privacy legislation heading toward a long-anticipated House Judiciary Committee markup has undergone a series of small but significant changes ahead of Wednesday’s vote.
Email privacy legislation heading toward a long-anticipated House Judiciary Committee markup has undergone a series of small but significant changes ahead of Wednesday’s vote.
But Judiciary Chairman Bob Goodlatte (R-VA) on Friday circulated a substitute amendment with a few differences, including the removal of a provision that would have required the government to quickly notify customers after obtaining their emails from a provider.
The substitute amendment could go through small changes before the markup, but supporters say there is a deal in principle.
Securing a committee vote on the bill is a small victory for privacy advocates, who have complained for years that Goodlatte dragged his feet on advancing the bill that has more than 300 co-sponsors.
Further movement is uncertain in a cramped election-year schedule.
The core bill would still update the 30-year-old Electronic Communications Privacy Act (ECPA) to require the government to get a warrant before forcing technology companies to hand over their customers’ electronic communications… Read More
Senators Propose Encryption Rules
Excerpted from Wall St. Journal Report by Damian Paletta
 Two key lawmakers Wednesday circulated a proposal that would require companies to unlock encrypted technology when served with a court order, a notable change in the law that could escalate the clash between Silicon Valley and Washington.
Two key lawmakers Wednesday circulated a proposal that would require companies to unlock encrypted technology when served with a court order, a notable change in the law that could escalate the clash between Silicon Valley and Washington.
Senate Intelligence Committee Chairman Richard Burr (R-NC) and the panel’s Vice Chairman, Senator Dianne Feinstein (D-CA), are seeking input on proposed legislation that attempts to address one of the thorniest security issues vexing policy makers — how to deal with the use of technology that cannot be read for law enforcement or national security purposes.
The 10-page “discussion draft” would require firms, when served with a court order, to provide “such information or data” or “provide technical assistance as is necessary to obtain such information or data” when the government is seeking to obtain encrypted material.
A company would be required to assist the government if the data “has been made unintelligible by a feature, product, or service owned, controlled, created, or provided by the covered entity or by a third party on behalf of the entity.”
Congress has been facing pressure to craft a balance between security and privacy when it comes to encryption… Read More
Obama Names Cyber-Experts to New Panel
Excerpted from Reuters Report by Roberta Rampton
 The chief executive of MasterCard, the former head of the National Security Agency (NSA), and officials from Microsoft and Uber will join a commission to strengthen US cyber-defenses, the White House said on Wednesday.
The chief executive of MasterCard, the former head of the National Security Agency (NSA), and officials from Microsoft and Uber will join a commission to strengthen US cyber-defenses, the White House said on Wednesday.
After high-profile hacks in the private sector and an embarrassing theft of information from government personnel files, President Barack Obama this year set up a Commission on Enhancing National Cybersecurity.
The commission, due to make long-term recommendations by early December on tightening cyber security in the private sector and government, is part of Obama’s $19-billion proposal to boost defenses against hackers.
The panel will hold its first public meeting on Thursday at the Commerce Department, joined by Obama’s counter-terrorism adviser Lisa Monaco and Commerce Secretary Penny Pritzker, the White House said in a blog post.
As previously announced, the panel will be co-chaired by Tom Donilon, Obama’s former National Security Advisor, and Sam Palmisano, former CEO of IBM.
The panel, selected by Obama and congressional leaders from both parties, also includes: Retired General Keith Alexander, former director of the National Security Agency, now CEO of IronNet Cybersecurity… Read More
Report from DCIA CEO Marty Lafferty
 The DCIA joined with fellow Digital Due Process (DDP) participants this week to send a clear message to the House Judiciary Committee.
The DCIA joined with fellow Digital Due Process (DDP) participants this week to send a clear message to the House Judiciary Committee.
More than fifty civil society organizations, companies, and trade associations, expressed our support for the Manager’s Substitute Amendment to the Email Privacy Act (H.R. 699).
The amendment updates the Electronic Communications Privacy Act (ECPA), the now outdated law that sets standards for government access to private Internet communications.
This important measure is intended to reflect Internet users’ reasonable expectations of privacy with respect to emails, texts, notes, photos, and other sensitive data stored in the cloud.
The bill would end ECPA’s arbitrary “180-day rule,” which permits email communications to be obtained without a warrant after 180 days.
The Act would also reject the Department of Justice (DoJ) interpretation of ECPA that the act of opening an email removes it from warrant protection.
These reforms would ratify the Sixth Circuit’s decision in the US v. Warshak case, which held that email content is protected by the Fourth Amendment, and that law enforcement access requires a probable cause warrant.
Moreover, the changes reflect current practices.
DoJ and FBI policies already require law enforcement officials seeking content to obtain a search warrant; and many service providers will not relinquish their users’ content without one.
The Manager’s Substitute does not achieve all of the reforms we had hoped for.
It removes key provisions of the proposed bill, which are necessary to protect users, such as requiring notice from the government to the customer when a warrant is served.
However, it does impose a warrant-for-content rule with limited exceptions.
We are particularly pleased that the Manager’s Substitute does not carve out civil agencies from the warrant requirement, which would have expanded government surveillance power and undermined the very purpose of the bill.
For these reasons, we support the bill as amended by the Manager’s Substitute. Share wisely, and take care.
Activists Pressure White House to Reject Encryption Bill
Excerpted from The Hill Report by Cory Bennett
 The Obama administration is under increasing pressure from privacy activists to disavow legislation that would force companies to help investigators decrypt data upon request.
The Obama administration is under increasing pressure from privacy activists to disavow legislation that would force companies to help investigators decrypt data upon request.
More than three dozen activists, academics, and advocacy groups sent the White House a letter on Monday urging it to oppose the bill, which they say “would threaten the safety of billions of Internet users.”
The White House is currently reviewing a draft of the measure from Senators Richard Burr (R-NC) and Dianne Feinstein (D-CA), the leaders of the Intelligence Committee.
The legislation is a response to concerns that criminals and terrorists are increasingly using encryption to hide from authorities.
Law enforcement has long pressed Congress for a bill that would give them greater access to this locked data.
But the tech community and privacy advocates insist such access would undermine security and endanger online privacy. Encryption only works, they say, if it is inaccessible.
The measure is called the Compliance with Court Orders Act of 2016… Read More
EU Call for Changes to US Data-Transfer Deal
Excerpted from NY Times Report by Mark Scott
 Only two months after the European Union‘s top policy makers agreed to a hard-won data-sharing pact with United States officials, the bloc’s national privacy regulators said on Wednesday that the deal did not go far enough to safeguard the personal information of Internet users in Europe.
Only two months after the European Union‘s top policy makers agreed to a hard-won data-sharing pact with United States officials, the bloc’s national privacy regulators said on Wednesday that the deal did not go far enough to safeguard the personal information of Internet users in Europe.
The agreement, the so-called EU-US Privacy Shield, which would allow companies to continue sending personal data back and forth across the Atlantic, is still widely expected to be ratified by early summer.
But by sounding the alarm over the current deal, national privacy watchdogs from France, Germany, and other European Union member states have served notice that American companies like Google, Facebook, and Amazon could face protracted country-by-country legal battles.
The regulators say they worry that companies could misuse data, including information from search engine queries and social media posts.
They also say they fear that American law enforcement and intelligence agencies might gain access to European citizens’ personal information without sufficient safeguards in place… Read More
Hackers Drive Huge Global IoT Security Market Growth
Excerpted from ReadWrite Report by Donal Power
 The widespread deployment of Internet of Things (IoT) technology is driving increased security breaches that will spark incredible growth in the IoT security industry.
The widespread deployment of Internet of Things (IoT) technology is driving increased security breaches that will spark incredible growth in the IoT security industry.
A recent study by Market Research Reports predicts that compound annual growth in the IoT security market will reach nearly 55% over the next year.
“With the continuously widening expanse of 2G, 3G, and 4G networks across the globe, the threat to digital data is also rising,” the report press release stated.
“A rising number of highly sophisticated and complex data hacking incidences has rocked the digital world in the past few years, bringing the issue of data security to the forefront.”
The report entitled “Global IoT Security Market 2015-2019” looked at the competitive landscape in the IoT space and how security concerns were mounting there.
“With the mounting volumes of digital data being communicated between devices and people, governments are taking strict measures to secure network from viruses and hackers by establishing stringent regulations and policies,” it said… Read More
Unexpected Security Holes
Excerpted from Semiconductor Engineering Report by Ed Sperling
 Security is emerging as one of the top challenges in semiconductor design across a variety of markets, with the number of security holes growing by orders of magnitude in sectors that have never dealt with these kinds of design constraints before.
Security is emerging as one of the top challenges in semiconductor design across a variety of markets, with the number of security holes growing by orders of magnitude in sectors that have never dealt with these kinds of design constraints before.
While security has been a topic of conversation for years in mobile phones and data centers, commercial and industrial equipment is being connected to the Internet for the first time.
This provides benefits such as remote management capabilities and alerts for potential failures.
But it also increases the risk of data theft or remote tampering.
Consider a commercial refrigerator, for example, which may be used to store medical samples or transplant organs.
In this market there are no standards for security, no guidelines for best practices, and little awareness of why anyone would ever want to hack into one of these systems.
With a medical-grade refrigerator you’ve got a publisher of data that can be used for machine service… Read More
NetApp Privacy Officer: TPP is Fundamentally Flawed
Excerpted from ARN Report by Chris Player
 NetApp chief privacy officer, Sheila Fitzpatrick, is a unique figure in the storage industry.
NetApp chief privacy officer, Sheila Fitzpatrick, is a unique figure in the storage industry.
She is charged with setting the privacy policy of the entire company and how it complies with the laws of countries in which it operates.
With over thirty years’ experience as an international employment and data protection attorney, she is considered one of the world’s leading experts in data privacy laws.
On a recent visit to Australia, Fitzpatrick sat down with ARN to discuss her role, what she is doing in Australia, the impact of the Cloud phenomenon and the Trans Pacific Partnership.
Q: Why have a data privacy officer?
A: NetApp has always taken data privacy extremely seriously because we are a data management company.
You can’t be a data management provider and not understand that data is your greatest asset, and if that data is breached, you have substantial problems. Eight years ago I built the data privacy program at NetApp… Read More
New Decentralized Cloud Storage Platform Goes Live
Excerpted from NewsBTC Report by Gautham
 Storj Labs, the encrypted end-to-end cloud storage company yesterday announced the beta launch of its cloud service.
Storj Labs, the encrypted end-to-end cloud storage company yesterday announced the beta launch of its cloud service.
The service, according to the company, enables software developers to push and pull their application data on a decentralized network.
The Storj decentralized blockchain-based cloud storage service appears similar to any other distributed networks.
The storage space for the files to be stored on the platform will be provided by the community.
The community members — called farmers — are similar to bitcoin miners.
However, instead of contributing their processing power to the pool, they contribute storage space in return for the platform’s own cryptocurrency called Storjcoin.
According to the company’s blog post, the beta release of the Storj platform is currently operating in an invite-only stage.
Therefore, only the users with invitations will be able to use the platform and evaluate its performance… Read More
Physics: Unite to Build a Quantum Internet
Excerpted from Nature Report by Stefano Pirandola & Samuel Braunstein
 Almost 25 years ago, physicists discovered a way of ‘teleporting’ a quantum system from one place to another without moving it.
Almost 25 years ago, physicists discovered a way of ‘teleporting’ a quantum system from one place to another without moving it.
There are physical limits to such teleportation: nothing can be transmitted faster than the speed of light; and Heisenberg’s uncertainty principle restricts what we can know about the state of a quantum system at a given time.
Nevertheless, the transported system is a replica that perfectly mimics the original, thanks to the weirdest feature of quantum mechanics — entanglement.
Described by Albert Einstein as “spooky action at a distance”, this property enables distinct quantum systems to become intimately correlated so that an action performed on one has an effect on the other, even for systems that are too far apart to physically interact.
Quantum states are fragile and cannot be sent through conventional lines of communication; quantum teleportation offers a reliable and efficient way to transfer quantum information across a network.
It provides the most promising mechanism for a future quantum Internet, with secure communications… Read More
What Technology Will Help You Create the Next Best App?
Excerpted from NewsWatch Report
 Microsoft recently held their annual conference for developers called “Build.”
Microsoft recently held their annual conference for developers called “Build.”
The company made announcements about technology that will enable developers to create the next best app or program solution for the latest devices and computers.
In fact, according to Microsoft, billions of opportunities exist for developers with the latest technology.
And we were lucky enough to get an inside look with Microsoft CEO, Satya Nadella who explains the importance of cloud computing:
“Cloud is not a single destination, it is a new form of computing. It enables the experience of mobility across all our devices.
It then infuses those experiences with intelligence. It has the ability to reason over large amounts of data using a distributed computing fabric.”
We are opening up Office 365 unlike ever before. Your applications and your data open through Office 365 connectors… Read More
Containerization Platform for Enterprise Applications
Excerpted from Robin Systems Press Announcement
 Robin Systems, a Silicon Valley-based enterprise software company, today announced Robin Containerization Platform for Enterprise Applications, the industry’s first Application-Defined Data Center software platform.
Robin Systems, a Silicon Valley-based enterprise software company, today announced Robin Containerization Platform for Enterprise Applications, the industry’s first Application-Defined Data Center software platform.
Robin Containerization Platform is designed to create an application-centric IT era by liberating applications from servers, storage and VM boundaries.
This application-driven approach simplifies the application lifecycle, “unlocks” hidden hardware capacity by deploying multiple applications per machine without compromising performance or availability, and boosts application performance through Robin’s Application-to-Spindle Quality of Service Guarantee.
Robin unveiled and demonstrated the first release of this product at Strata+Hadoop World in San Jose, CA.
Robin is the first company to bring containerization benefits to mission-critical enterprise applications such as databases and Big Data clusters, enabling high-performance workload consolidation with the agility and flexibility previously available only to micro applications.
Robin Containerization Platform transforms commodity hardware into a compute, storage, and data continuum… Read More
New Regs Could Choke Business Broadband and Cost Jobs
Excerpted from CED Magazine Report by Laura Hamilton
 An FCC decision to take over pricing of business broadband services could eliminate up to 43,560 jobs, cut economic output by $3.4 billion over a five-year period and prevent 67,000 buildings from getting access to fiber, according to a report by Hal Singer, principal of Economists and adjunct professor with Georgetown University’s McDonough School of Business.
An FCC decision to take over pricing of business broadband services could eliminate up to 43,560 jobs, cut economic output by $3.4 billion over a five-year period and prevent 67,000 buildings from getting access to fiber, according to a report by Hal Singer, principal of Economists and adjunct professor with Georgetown University’s McDonough School of Business.
USTelecom commissioned the study.
The study comes as some companies are asking the FCC to set prices in the market.
Singer reportedly found no evidence of lack of competition, and says that monthly prices for some business broadband services declined between 7 and 17 percent from 2013 to 2015.
Singer used Charlotte, NC, as a test bed because it reportedly has a population and supply of office buildings considered representative of an average US city.
He extrapolated the results to assess the impact of regulatory change nationwide. Projecting over a five-year period, the study predicts that if there is no regulation of fiber-based networks, providers would be able to light up nearly 122,000 buildings… Read More
Cloud Computing’s Giants Take in Billions
Excerpted from NY Times Report by Quentin Hardy
 Imagine building an enormous beach resort, maybe the best in the world.
Imagine building an enormous beach resort, maybe the best in the world.
Instead of renting the rooms, you charge guests based on the grains of sand they touch.
You charge very little per grain, but if they lie on enough of them, it adds up.
That is one way to think about what is going on at the world’s biggest cloud-computing companies.
Instead of grains of sand, think about computing cycles, the activity that goes on in a computer server that is running software. For a price, think about one line of software code for two one-millionths of a penny.
When tolls that tiny are paid often enough, they can make a billion-dollar business.
At Amazon Web Services, which pioneered this method late last year, there is no charge for the first million times a customer runs code.
Thereafter, AWS charges by the million times, or for the hundreds of milliseconds the computer is used.
“The scale at which we operate allows us to do innovative things,” said Matt Wood, General Manager of Product Strategy at AWS… Read More
Cloud Computing Infrastructure Spending to Surge
Excerpted from ZDNet Report by Larry Dignan
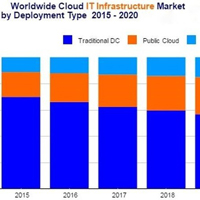 Global cloud infrastructure spending on server, storage, and networking is expected to surge 18.9 percent in 2016 even as spending on traditional data center gear fades.
Global cloud infrastructure spending on server, storage, and networking is expected to surge 18.9 percent in 2016 even as spending on traditional data center gear fades.
According to IDC, the spending on infrastructure for cloud environments will hit $38.2 billion in 2016.
IDC noted that its tally excludes double counting between storage and server.
Private cloud infrastructure spending will be up 11.1 percent to $13.9 billion in 2016 with public cloud delivering growth of 14.1 percent to $24.4 billion.
Spending on traditional data centers will fall 4 percent in 2016, but still account for 63.8 percent of total spending.
In the long run, IDC estimated that cloud infrastructure spending will grow at a 12.5 percent five year annual growth rate to $57.8 billion in 2020.
Of that spending, public cloud providers will spend $37.5 billion on infrastructure in 2020 with private cloud spending hitting $20.3 billion. Among the categories of cloud infrastructure spending, Ethernet switches will grow at a 26.8 percent clip… Read More
Coming Events of Interest
Delivery of Things World — April 25th-26th in Berlin, Germany. DevOps specialists, continuous development strategists, architect newbies, development geeks, and cloud geniuses from across the spectrum of DevOps transformation come together at this stimulating and innovative event.
DataCloud Europe 2016 — June 8th-9th in Monte Carlo, Monaco. The 2016 conference will focus on cloud computing advances and changes in data management, with a stellar line-up of speakers including global infrastructure leaders and subject matter experts.
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
2016 Creative Storage Conference — June 23rd in Culver Cirty, CA. The tenth annual CS will bring together digital storage providers, equipment manufacturers, software distributors, and professional media and entertainment end-users to explore the conference theme “The Art of Storage.”
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Mobile World Congress Shanghai — June 29th – July 1st in Shanghai, China. MWC Shanghai is a very unique gathering that brings together industry participants ranging from C-Level mobile executives to end-user consumers passionate about mobile.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
