In This Issue
- Email Privacy Bill Vote
- Cos Born in the Cloud
- Verizon Cloud Storage
- Report from the CEO
- Net Security Concerns
- Rethink Cybersecurity
- Congress’s Attempt
- Silicon Valley Unites
- Senate Bill a Threat
- Cos Getting Better
- AI + Humans = K-A C
- Mobile Containerizing
- VR Lures Media Cos
- Google’s Tensorflow
- The Chief Data Officer
- Next Big Thing per MZ
- Coming DCIA Events
House Committee Votes Unanimously for Email Privacy Act
Excerpted from TechCrunch Report by Kate Conger
 Maybe you’ve delighted in reading some of Hillary Clinton’s more humorous emails, released in several stages over the past year — there’s the one where she calls Harriet Tubman her “home girl,” or the time she jokes about Chinese hackers messing with her contacts.
Maybe you’ve delighted in reading some of Hillary Clinton’s more humorous emails, released in several stages over the past year — there’s the one where she calls Harriet Tubman her “home girl,” or the time she jokes about Chinese hackers messing with her contacts.
But imagine someone digging into your old emails and reading through all your bad jokes, family feuds, and business arrangements.
It’s not so funny anymore, right?
Here’s the thing — law enforcement officials can read through your old emails anytime without a warrant.
The House Judiciary Committee made its first move to fix this legal loophole today, voting 28-0 to approve the Email Privacy Act.
The bill would require officials to obtain a warrant before reading Americans’ old emails and texts, instant messages (IMs), and other cloud-stored communications… Read More
DCINFO Editor’s Note: The DCIA and fellow Digital Due Process (DDP) participants support this measure.
Will Companies Born In The Cloud Become Trapped There?
Excerpted from Forbes Report by Michael Elliott
 Unencumbered by the weight of legacy architecture, “born-in-the-cloud” companies have distinct advantages over traditional enterprises.
Unencumbered by the weight of legacy architecture, “born-in-the-cloud” companies have distinct advantages over traditional enterprises.
Their lack of adherence to legacy business models and staid corporate cultures frees them to adopt new technologies, deploy new services, and disrupt established industries.
Yet, despite the advantages of being born in the cloud, a dependence on public cloud services could become a disadvantage if their business-critical applications and data become trapped in the cloud.
Designing applications that can be moved across a hybrid environment is becoming a guiding principle for many IT organizations.
Last year, a Voice of the Enterprise study conducted by 451 Research found that 20% of cloud users had already moved one or more workloads from a public cloud environment to a private cloud, a process known as repatriation.
Another 10% planned to move some of their workloads from public to private cloud environments during the coming year. On average, those who planned to migrate workloads from public to private cloud environments within two years… Read More
Verizon Simplifies Cloud Storage Plans
Excerpted from Wireless Week Report by Diana Goovaerts
 Verizon has rolled-out a simplified plan structure for its cloud storage options.
Verizon has rolled-out a simplified plan structure for its cloud storage options.
The new system adopts the same sizing approach the carrier adopted for its wireless plans in August, offering options in small, medium, large and extra-large.
The cloud options offer storage ranging from 5 GB per month to 1 TB per month.
The small package, which offers 5 GB of storage, is free.
Customers can also get a medium package with 25 GB of storage for $2.99 per month, a large package with 250 GB of storage for $4.99 per month or an extra-large package with 1 TB of storage for $9.99 per month.
Verizon said customers who already have could subscriptions on the old 75 GB or higher plans will automatically be transferred to the new large or extra-large plans.
In addition to offering extra storage space for smaller memory devices, Verizon said cloud subscribers can also use the cloud backup to more efficiently transfer their information during device upgrades… Read More
Report from DCIA CEO Marty Lafferty
 We hope you’ll join us this week to meet with top DevOps thought leaders and innovators at Delivery of Things World.
We hope you’ll join us this week to meet with top DevOps thought leaders and innovators at Delivery of Things World.
This must-attend international continuous delivery event is taking place in Berlin, Germany on April 25th and 26th, and represents our second event in partnership with the we.CONECT Group.
More than three-hundred experts will appear during the two-day event to discuss challenges, technologies, and innovations defining the future of continuous delivery in a DevOps world.
Here’s an outline of what to expect.
There will be more than sixty case studies and interactive sessions with expert speakers from Maersk, ING, Etsy, Zalando, Rocket Internet, Xing, 1&1, The Guardian, Barclays, Ticketmaster, booking.com, Amdocs, the Financial Times and many more.
Networking and benchmarking sessions will include global-leading senior executives from Telefonica, Siemens, LogMeIn, Bayer Business Services, Daimler, Allianz, KUKA Roboter, American Express, Payback, SCA Hygiene Products, McKinsey & Company, and Cathay Pacific, among more than 300 DevOps experts.
For more information on key topics, speakers, sessions, and all the special features we have in store for you, please download the final agenda or visit the conference website.
To make sure you don’t miss out on the Delivery of Things World, secure one of the last tickets by booking online now.
We look forward to welcoming you in Berlin this week. Share wisely, and take care.
Public More Concerned with Internet Security
Excerpted from TeleCompetitor Report by Andrew Burger
 More than 8 in 10 people living across 24 countries (83%) believe there should be new rules regarding how companies, governments, and other users make use of personal data, according to new research about Internet security attitudes.
More than 8 in 10 people living across 24 countries (83%) believe there should be new rules regarding how companies, governments, and other users make use of personal data, according to new research about Internet security attitudes.
The research was commissioned by the Center for International Governance Innovation (CIGI) and conducted by research company Ipsos.
Eighty-five percent of people surveyed also believe governments should work in close collaboration, as well as with organizations, to enhance the safety and security of the Internet.
The 2016 CIGI-Ipsos Global Survey on Internet Security and Trust was released in Geneva April 18 at the United Nations Conference on Trade & Development E-Commerce Week.
Nearly 6 in 10 respondents to the Internet security attitudes survey (57%) said they were more concerned about online privacy and personal data security this year than last.
Just under 4 in 10 (38%) believed their Internet activities weren’t monitored, while less than half (46%) said they trusted their online activities were not being censored… Read More
Is it Time to Rethink Cybersecurity Strategies?
Excerpted from Baseline Magazine Report by Samuel Greengard
 The possibilities and opportunities that result from digital technology aren’t lost on today’s business and IT leaders.
The possibilities and opportunities that result from digital technology aren’t lost on today’s business and IT leaders.
However, locking down enterprise systems, software, data and other resources has become a growing nightmare.
According to a “2015 Cost of Data Breach Study” from the Ponemon Institute and IBM, the average cost of a data breach has reached approximately $3.8 million.
This represents a 23 percent increase since 2013.
What’s more, social engineering attacks—including phishing and whaling (phishing with a high-profile target)—are becoming far more sophisticated and dangerous.
For example, ransomware attacks have risen by double digits since 2015.
Navigating today’s threat landscape and putting the right cyber-security tools in place is a daunting challenge.
For years, organizations have thrown an array of security solutions at various hazards. These include firewalls, anti-malware products, intrusion detection and prevention, endpoint protection, data loss protection and encryption… Read More
Congress’s Cybersecurity Attempt Already Outdated
Excerpted from Washington Post Report by Aaron Levie
 When the news broke that the FBI and the DoJ dropped their case against Apple, successfully cracking open the San Bernardino, CA iPhone without the help of the consumer electronics giant, there was a collective sigh of relief from the technology industry and security experts.
When the news broke that the FBI and the DoJ dropped their case against Apple, successfully cracking open the San Bernardino, CA iPhone without the help of the consumer electronics giant, there was a collective sigh of relief from the technology industry and security experts.
Apple avoided a precedent-setting event requiring them to break their own security, and the government was able to unlock a device that may lead to advances in their investigation.
But if anyone thought this issue was concluded, they’d be mistaken.
Recently, draft legislation from Sens. Diane Feinstein and Richard Burr directed at addressing the Apple vs. FBI controversy circulated in the media.
The bill would require technology companies to build “backdoors” to the encryption within their products for law enforcement agencies.
Feinstein and Burr have taken the first step in what will no doubt be a contentious and important debate.
But instead of doubling down on applying the existing laws and norms we have operated under in the physical world for the past 200 years… Read More
Silicon Valley Unites against Encryption Bill
Excerpted from The Hill Report by Cory Bennett
 Major tech firms are banding together to oppose an encryption bill that would require them to help government investigators decrypt customer data.
Major tech firms are banding together to oppose an encryption bill that would require them to help government investigators decrypt customer data.
A coalition that includes Apple, Facebook, Google, Microsoft, and Twitter blasted the legislation as “unworkable” in a letter sent Tuesday to the bill’s backers, Sens. Richard Burr (R-NC) and Dianne Feinstein (D-CA).
The bill “would weaken the very defenses we need to protect us from people who want to cause economic and physical harm,” said the letter, which was signed by the coalition, known as Reform Government Surveillance, as well as several industry trade groups.
The efforts of Burr and Feinstein, who head the Intelligence Committee, have divided the tech community and law enforcement officials.
The pair developed the legislation in response to law enforcement concerns that criminals are increasingly using encrypted technology to hide from authorities.
The measure would require companies to provide “technical assistance” to investigators who cannot access this secure data on their own… Read More
Senate Bill Itself a Threat to National Security
Excerpted from ZDNet Report by Zack Whittaker
 It’s the bill that has everyone up in arms. In the wake of the dispute between Apple and the FBI over encryption, Congress has weighed in with its long-awaited response, and it was the definition of what people didn’t want.
It’s the bill that has everyone up in arms. In the wake of the dispute between Apple and the FBI over encryption, Congress has weighed in with its long-awaited response, and it was the definition of what people didn’t want.
The bill, released last week by Senators Richard Burr (R-NC) and Dianne Feinstein (D-CA), two leading senators on the Senate Intelligence Committee, would require tech companies and phone makers to decrypt customer data at a court’s request.
Just a few minutes after the first NSA leak was published, the phones of US lawmakers began to buzz, hours before most of America would find out over their morning coffee.
Or in the words of one opposing senator, Ron Wyden (D-OR), who also sits on the intelligence committee: “This is requiring American companies to build a backdoor.”
That poses a big problem for tech companies, who in recent years pushed back against the prying eyes of the US government’s secretive surveillance state.
With encryption becoming more ubiquitous in devices and apps than ever, the number of unencrypted services are falling into the minority… Read More
Companies Getting Better at Detecting Breaches
Excerpted from Wall St. Journal Report by Rachael King
 Data about cybercrime appears to grow worse and the warnings more apocalyptic.
Data about cybercrime appears to grow worse and the warnings more apocalyptic.
Yet the Trustwave Global Security Report, released Tuesday, offers some small nuggets of hope.
The cybersecurity company gathered data from hundreds of investigations it conducted in 2015 across 17 countries.
The report contains many of the usual details about malicious software and vulnerabilities.
But it also shows that in some areas, companies are getting better — ever so slightly — at shoring up defenses. Here are a few highlights:
In 2015, 41% of breaches were detected by victims themselves, up from 19% in 2014.
There wasn’t an explanation for the huge improvement but it suggests that companies now have better tools to detect breaches or that more employees have been trained to report unusual activity they see on computer systems.
The median time between intrusion and detection was 15 days for internally detected breaches, compared to 168 days for breaches detected by external parties. North America significantly exceeds other regions in point-of-sale compromises… Read More
AI + Humans = Kick-Ass Cybersecurity
Excerpted from Network World Report by Katherine Noyes
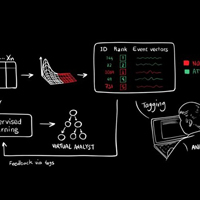 Neither humans nor artificial intelligence (AI) have proved overwhelmingly successful at maintaining cybersecurity on their own, so why not see what happens when you combine the two?
Neither humans nor artificial intelligence (AI) have proved overwhelmingly successful at maintaining cybersecurity on their own, so why not see what happens when you combine the two?
That’s exactly the premise of a new project from MIT, and it’s achieved some pretty impressive results.
Researchers from MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) and machine-learning startup PatternEx have developed a new platform called AI2 that can detect 85 percent of attacks.
It also reduces the number of “false positives” — non-threats mistakenly identified as threats — by a factor of five, the researchers said.
The system was tested on 3.6 billion pieces of data generated by millions of users over a period of three months.
The researchers presented a paper summarizing the project earlier this month at the IEEE International Conference on Big Data Security.
“You can think about the system as a virtual analyst,” said CSAIL scientist Kalyan Veeramachaneni, who developed AI2 with Ignacio Arnaldo… Read More
Mobile Containerization Matters More Than Ever
Excerpted from Blackerry Business Blog
 The mobile industry has reached an inflection point.
The mobile industry has reached an inflection point.
The value of providing employees with greater productivity must be balanced against threats such as data leakage, lost and stolen devices, and unsafe user practices.
As employee-owned devices become more widespread in enterprise and businesses start moving up the mobile maturity curve, traditional mobile device management (MDM) offers insufficient security controls.
Businesses have thus started to turn elsewhere.
Consumer-oriented devices have begun to ship with on-device containerization. Solutions such as Android for Work, Apple iOS Managed Apps and Samsung KNOX have grown increasingly common.
“App containers have begun to evolve as a complement or even a replacement for MDM as the foundational security layer for enterprise mobility,” reads a recent Good Technology White Paper.
Containers are a transformative technology for enabling enterprises to confidently deploy mobile apps that access corporate data… Read More
Virtual Reality Lures Media Companies to a New Frontier
Excerpted from NY Times Report by Katie Benner and Emily Steel
 Media and entertainment companies want to help shape the next entertainment platform: virtual reality.
Media and entertainment companies want to help shape the next entertainment platform: virtual reality.
Over the last several months, companies including Conde Nast and Vice Media have delved into the technology as a new frontier for storytelling and a potential outlet for selling ads.
They have forged partnerships with companies that make virtual reality headsets and software makers that broadcast events in virtual reality, and are trying to figure out how best to create virtual reality content.
Some media and entertainment companies are also starting to invest in virtual reality companies themselves.
HBO was recently the lead investor in an addition to a funding round for Otoy, a Los Angeles-based special effects start-up.
Otoy, whose LightStage facial rendering technology, used in films like “The Curious Case of Benjamin Button,” has won an Academy Award, has also gotten into virtual reality.
Discovery Communications and Liberty Media participated in the funding, which raised as much as $37 million and was an extension of financing that took place in 2014, according to VC Experts, a venture capital research firm… Read More
Google Updates TensorFlow Machine Learning Platform
Excerpted from App Developer Magazine Report by Stuart Parkerson
 Google’s TensorFlow is an open source software library for numerical computation using data flow graphs.
Google’s TensorFlow is an open source software library for numerical computation using data flow graphs.
The architecture provides the ability to deploy computation to one or more CPUs or GPUs in a desktop, server, or mobile device with a single API.
It its recent release of TensorFlow 0.8, Google is introducing distributed computing support, including everything needed to train distributed models on a company’s infrastructure.
Distributed TensorFlow is powered by the high-performance gRPC library, which supports training on hundreds of machines in parallel.
Google has published a distributed trainer for the Inception image classification neural network in the TensorFlow models repository.
Using the distributed trainer, Google reports that it trained the Inception network to 78% accuracy in less than 65 hours using 100 GPUs.
Small clusters can also benefit from distributed TensorFlow, as including more GPUs improves the overall throughput… Read More
The Rise of the Chief Data Officer
Excerpted from Segment Report by Brent Summers
 We’re all tired of hearing about “Big Data.”
We’re all tired of hearing about “Big Data.”
But if you want to learn how to use data to accelerate your company’s growth, don’t tune out yet.
As consumers, we are producing more data than ever before: by some reports, as much as 90% of the world’s data was created the last year.
The Internet in Real-Time clearly illustrates the stupefying amounts of data generated on the open web.
Consumers are growing increasingly comfortable sharing their preferences whether it’s passively like the brides on theknot.com (an early Segment customer!) who explore around 2,000 fashion products each minute or more actively with Amazon wish lists and Facebook likes.
A 2013 report from Bain found that top performing companies are both twice as likely to use data “very frequently” to make decisions and five times as likely to make decisions faster than their market peers. Also, companies that pay attention to what their customers are telling them are more apt to continue making products people actually want.
As a result, we’ve seen the rise of the Chief Data Officer (CDO), and many companies are making a commitment to vigilance… Read More
Next Big Thing According to Mark Zuckerberg
Excerpted from NY Times Report by Mike Isaac and Quentin Hardy
 Each Saturday, Farhad Manjoo and Mike Isaac, technology reporters at The New York Times, review the week’s news, offering analysis and maybe a joke or two about the most important developments in the tech industry. Mr. Manjoo is still off this week, so Quentin Hardy, a Times technology reporter, is filling in.
Each Saturday, Farhad Manjoo and Mike Isaac, technology reporters at The New York Times, review the week’s news, offering analysis and maybe a joke or two about the most important developments in the tech industry. Mr. Manjoo is still off this week, so Quentin Hardy, a Times technology reporter, is filling in.
Mike: Ahoy, Quentin! I appreciate you filling in for Farhad on his third and last week of vacation. Let me just take a moment to say I haven’t taken three weeks off work in a row since my last visit to the hospital. That Farhad sure knows how to lounge.
Quentin: Farhad has been away three weeks? Wow, he’s missed like five new versions of iTunes.
Mike: Indeed. So, on with the week’s news!
Microsoft decided to sue the government over the gag orders the Department of Justice puts on companies after they’ve received user data by obtaining a warrant. It’s been a practice for a while, blown wide open — or at least more widely noted — by the Snowden revelations a few years ago. Gutsy, Microsoft!
Quixey, a deep-linking start-up that had a lot of hype in its earlier days, just gave its CEO the boot after, uh, not living up to the hype… Read More
Coming Events of Interest
Delivery of Things World — April 25th-26th in Berlin, Germany. DevOps specialists, continuous development strategists, architect newbies, development geeks, and cloud geniuses from across the spectrum of DevOps transformation come together at this stimulating and innovative event.
DataCloud Europe 2016 — June 8th-9th in Monte Carlo, Monaco. The 2016 conference will focus on cloud computing advances and changes in data management, with a stellar line-up of speakers including global infrastructure leaders and subject matter experts.
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
2016 Creative Storage Conference — June 23rd in Culver Cirty, CA. The tenth annual CS will bring together digital storage providers, equipment manufacturers, software distributors, and professional media and entertainment end-users to explore the conference theme “The Art of Storage.”
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Mobile World Congress Shanghai — June 29th – July 1st in Shanghai, China. MWC Shanghai is a very unique gathering that brings together industry participants ranging from C-Level mobile executives to end-user consumers passionate about mobile.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
