In This Issue
- Cloud Apps Are Rising
- More Than Tech Shift
- Network Edge Change
- Report from the CEO
- Verizon & KT Join 5G
- ASE Selects NetApp
- Telefonica and Nokia
- Cloud Import NetApp
- EMC Global Survey
- IT Skills Shortage
- 12 Step Cyber Plan
- Step-Up Safeguards
- Msft & AWS FedRAMP
- Next Wave Security
- State Dept: IoT Saves
- DAO Vulnerability
- Coming DCIA Events
Cloud Apps Rise Despite Cloud Security Concerns
Excerpted from CIO Insight Report by Karen Frenkel

The percentage of organizations with more than half of their applications deployed in the cloud (16%) doubled since last year, when it was 8%.
The worldwide cloud computing spend grew 20 percent last year, but security of critical data and systems remain key issues and barriers to adopting cloud services.
As a result, cloud security concerns are rising as investment in cloud computing grows, according to a new report by Crowd Research Partners, but that’s not stopping companies from using the cloud.
The study, “2016 Cloud Security Spotlight Report,” was sponsored by cloud security vendors Alien Vault, Bitglass, Cato Networks, CloudPassage, Dell Software, Dome9 Security, IMMUNIO, ISC, and Randtronics.
The survey sample was 2,200 members of the Information Security Community on LinkedIn.
Says Holger Schulze, Founder of LinkedIn’s Information Security Community, “As organizations increase investments in cloud infrastructure, they are seeking a similar level of security controls and functionality to what’s available in traditional IT infrastructures… Read More
Cloud Computing More Than Just a Tech Shift
Excerpted from Trade Arabia Report by Sachin Bhardwaj

While the term cloud has become increasingly familiar, many of its business benefits can be overlooked due to the number of acronyms and options built-in around the service.
Cloud computing delivers significant benefits in terms of tangible business metrics such as simplified and flexible IT environment, right-sizing of IT requirements, and a pay-per-use consumption model.
These benefits are applicable whether the use case is a large enterprise with thousands of employees accessing common business applications or a smaller business accessing office type applications.
These benefits can be summarized as follows: Switch over from upfront capital investments (CapEx) into a predictable IT consumption expenses model based on actual usage (OpEx);
Addition and reduction of extra IT resources based on internal demand with minimum delays, without cumbersome procurement procedures for purchase, leading to agility and flexibility in the marketplace;
Focus on differentiating in the marketplace with customers and new revenue streams versus challenges of building internal IT skills… Read More
Beacons of Change at the Industrial Network Edge
Excerpted from ARC Report by Chantal Polsonetti
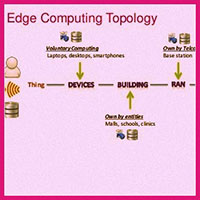
The industrial network “edge” is populated by devices, such as Ethernet, wireless, and cellular gateways; Ethernet switches and routers; and wireless access points (WAPs).
Traditionally relied upon to bridge information technology (IT) and operations technology (OT) environments or bring legacy equipment into automation or enterprise architectures, industrial network edge devices have often been an afterthought in the quest to integrate operations.
Originally intended largely to bring automation devices onto the enterprise backhaul, today’s network edge products target sensor-to-cloud integration to further industrial internet-based strategies designed to improve business performance.
Availability of microprocessor-based devices with standard operating systems, such as Linux and Windows 10, that can host applications also drives the march towards edge or fog computing.
Concurrent with this trend is the battle of the internet platforms extending to the industrial edge, with heavyweights, such as General Electric and the IBM/Cisco partnership bringing their platforms to edge devices via both their own and their partners’ products. Why? Because the edge is where the assets and the associated data to be analyzed by enterprise applications reside… Read More
Report from DCIA CEO Marty Lafferty

As the DCIA enters its fourteenth year, we take this opportunity to thank our member companies, association sponsors, conference exhibitors, delegates, and DCINFO readers.
We are privileged to serve a group of organizations as dynamic and diverse as the distributed computing industry.
And we are proud of the many accomplishments of people involved at all levels.
This year has seen a great deal of advancement in the technology sector – and in our ongoing support of further expansion.
Mobile cloud, big data, social networking, and internet of things (IoT) have continued to develop at a record pace.
Cybersecurity across both the public and private sectors emerged as an area of enormous need and exceptional opportunity.
Closer to home, since July 2015, we supported the introduction of the ADRM Working Group as a meaningful step towards improved cybersecurity.
We worked with consumer advocacy groups to support reasonable expectations of privacy with respect to data stored in the cloud by opposing measures that would expand government surveillance powers.
And by supporting reform of the Electronic Communications Privacy Act, which at this point has passed in the House of Representatives.
We launched the DCIA Compliance Audit Service to help companies with the Cybersecurity Act, which became law at the end of 2015.
We were honored to serve as an affiliate association of the CTA and promote virtual reality (VR) at our CES exhibit booth and demos.
We partnered on a global basis with more than a dozen additional firms to present cutting edge conferences and expos designed to help propel cloud computing, cybersecurity, mobile cloud, and the IoT in their respective markets.
And when warranted, we weighed in on our industry’s relation to world events, politics, and humanitarian concerns.
Now as the cloud computing phenomenon enters a cyclical change, we welcome the advent of fog and edge computing.
In the coming year, we’ll work with industry participants to practically define the differences between fog and edge computing, and more importantly, to foster use cases that prove the benefits of tapping decentralized compute resources to compliment data centers.
And we’ll continue our press for improved cybersecurity on many fronts, both publicly and privately, as a top priority. Share wisely, and take care.
Verizon & KT Join Hands for 5G Standard
Excerpted from Korea Times Report by Lee Min-Hyung

Korea Telecom (KT) has teamed up with US-based telecommunications giant Verizon to establish global standards and develop technologies for the fifth-generation (5G) wireless network.
The Korean mobile carrier said Sunday that it has signed a partnership with its US counterpart, as part of its aggressive move to strengthen its global profile ahead of its planned 5G demonstration in 2018.
As the existing long-term-evolution (LTE) network is reaching saturation in the local market, the nation’s leading mobile carriers have spared no efforts in finding next growth engines, such as the internet of things (IoT) and media businesses.
Given that 5G will be a major building block for all those new revenue sources, KT along with SK Telecom and LG Uplus have continued and expanded efforts to build the 5G infrastructure.
In particular, KT hopes its new partnership will speed-up the global standardization of 5G technology.
Under the deal, both firms agreed to cooperate on faster commercialization of the 5G which is expected to come in 2020.
In January, chiefs of both companies agreed to collaborate on developing technologies for their next revenue sources at CES… Read More
ASE Selects NetApp for Cloud Management Offerings
Excerpted from Market Wired Report

NetApp today announced that ASE has leveraged its existing partnership with the vendor to develop two new cloud management offerings based on NetApp Private Storage (NPS) and NetApp StorageGRID Webscale solutions.
As one of Australia’s top-10 most trusted cloud providers, ASE sought to offer customers new ways to manage their data in a public cloud with a simple and straightforward web portal.
Now, with a data center network spanning the United States, Australia, New Zealand, and Singapore, ASE supports over 200 companies ranging from small to medium enterprises to some of the world’s largest corporate organizations.
These corporations include First Wave, EzyPay, AW Edwards, Silver Trak Digital, and several global media companies.
ASE chose to work with NetApp because NetApp provides the data management features and innovations that ASE customers need from their cloud services.
ASE has become known for its top-shelf public, private, and hybrid clouds supported by smart solution design and dedicated 24/7 365 days per year technical assistance… Read More
Telefonica Chooses Nokia for Next-Gen Metro Optical Net
Excerpted from Telegeography Report

Spanish fixed line incumbent Telefonica Espana has selected Nokia’s next-generation optical solution for its new metro transport network to handle the significant traffic growth which has resulted from the uptake of its quadruple-play services.
In a press release, the Finnish vendor revealed it would deploy the network in areas of high population density including Barcelona and Catalonia, ultimately covering half of Spain.
Nokia will provide multiple elements of its recently enhanced optical portfolio based on the Nokia Photonic Service Engine version 2 (PSE-2), including: a scalable packet-OTN switch, the Nokia 1830 PSS-24x; the 1830 PSS 500G DWDM Muxponder, offering up to 500G of flexible bandwidth for delivery of 100G services; and its CDC-F Wavelength Routing solution, giving Telefonica touchless programmability at the optical layer.
Consisting of metro access, aggregation and core mesh connectivity, it has been claimed that the new transport network will provide the flexibility and scalability required to cope with traffic growth from Telefonica expanding its ‘Fusion’ branded multi-play services across high-density centers in Spain.
Commenting on the deal, Javier Gutierrez, Director of Network Strategy and Development at Telefonica Espana, was cited… Read More
Why Is the Cloud Transition Important for NetApp?
Excerpted from Market Realist Report by Adam Rogers
NetApp is a data storage and data management company headquartered in Sunnyvale, CA.
It was founded in 1992. In the last two decades, The company has seen a number of technological transitions.
NetApp, which started as a network-attached storage (or NAS) company, grew exponentially in the dot-com boom.
NetApp expanded in the enterprise segment and then added Fiber Channel technology, a core feature of its products.
This opened up new markets for Windows servers and Oracle (databases.
NetApp sees the cloud transition as one of the most important drivers for revenue growth.
NetApp is confident on the company’s transition to the cloud and is focusing on application development.
According to NetApp Chief Information Officer (CIO) Phil Brotherton, NetApp is the only independent storage company that has partnered with cloud heavyweights, such as Microsoft, VMware, and Amazon.
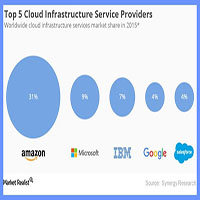
According to a recent report by Synergy Research, cloud infrastructure service revenues grew 52% on a year-over-year (YoY) basis in 2015… Read More
Cyber-Threat Impact Highlighted in EMC Global Survey
Excerpted from Cloud Computing Intelligence Report

EMC has launched its global Data Protection Index study revealing that organizations are failing to appreciate the growing challenges of protecting their data and, as a result, are experiencing the economic impact of data loss.
Incidents of traditional data loss and disruption are down since 2014, but new challenges mean 13% more businesses experienced loss overall.
36% of organizations have lost data in the last year as the result of a security breach.
The average cost of data loss is more than $914,000.
Over half of businesses fail to protect data in the cloud despite more than 80% indicating they rely on software-as-a-service (SaaS)-based business applications.
73% of organizations are not very confident they can protect flash storage environments.
$228,000 is the estimated average cost to respondent’s organizations who have experienced unplanned systems downtime in the last 12 months. 72% state their organization is less than very confident it can meet SLAs to fully recover systems/data… Read More
IT Skills Shortage Leading to Cybersecurity Issues
Excerpted from CloudTech Report by James Bourne

If a security system flags an issue in your organization and nobody acts on it, is it even an issue?
Many organizations are acting that way, according to a report from Skyhigh Networks and the Cloud Security Alliance (CSA).
The research found that security budgets continue to rise – more than half (53%) of the 220 IT and security professionals polled expect their allocations to go up in the coming year – and the myriad of tools at teams’ disposals is a growing trend, with one in five companies having more than 10 available to them.
Yet almost half (30%) of those polled admit to ignoring alerts because of the frequency of ‘false positives’ – an alert which erroneously flags normal behavior as malicious.
Part of the issue relates to a lack of IT skills, the report asserts, with respondents saying the most important new IT skill in the coming five years is incident response management.
IT workers believe the best solution to a shortage of skills is training current employees, while IT executives think bringing in junior IT workers is the best way forward. It leads to a worrying pattern; hackers staying one step ahead of organizations… Read More
12 Steps for an Exam-Proof Cybersecurity Plan
Excerpted from ThinkAdvisor Report by Melanie Waddell

As regulators continue to make cybersecurity a top exam priority and enforcement actions against advisors and brokers in the cyber space become more prevalent, Cipperman Compliance Services has devised a 12-step cybersecurity plan to give advisors some guidance on how to ensure compliance in this tricky area.
Indeed, not only did the Securities and Exchange Commission recently create a new senior advisor position on cybersecurity policy, which was filled by Christopher Hetner, but the agency’s second round of cyber exams are in full swing.
Morgan Stanley recently agreed to pay a $1 million penalty to the SEC to settle charges that it failed to protect customer information, some of which the agency says was hacked and offered for sale online.
The SEC found that Morgan Stanley failed to adopt written policies and procedures reasonably designed to protect customer data from 2011 to 2014, and that during that time a then-employee impermissibly accessed and transferred customer data on approximately 730,000 accounts associated with 330,000 different households to his personal server, which was ultimately hacked by third parties… Read More
Companies Step-Up Cybersecurity Safeguards
Excerpted from Baseline Magazine Report by Samuel Greengard

A seemingly endless barrage of cyber-attacks is forcing business and IT leaders to take notice and step-up protection.
According to a newly released study of 221 IT directors, managers and practitioners conducted by IT management firm SolarWinds in conjunction with Penton Research, “IT Security Survey North America,” preparedness and training are rapidly moving into the spotlight across a wide swath of industries.
Among other things, organizations are focusing on improving detection, reducing response and remediation times after an incident, cracking down on misused and abused credentials, gaining better control of network devices and spotting policy violations.
Organizations also are looking to ratchet up security training and boost the quality of the training, the report noted.
Yet, “While many organizations are less vulnerable today than they were a year ago,” noted Mav Turner, director of business strategy at SolarWinds, “it’s important for IT professionals to never get too confident in their organization’s security posture.”
Companies are improving detection, reducing response and remediation times, cracking down on misused credentials… Read More
AWS & Microsoft FedRAMP Approval for Sensitive Cloud Data
Excerpted from CloudTech Report by James Bourne

Another day, another piece of good news for both Microsoft Azure and Amazon Web Services (AWS); the vendors are two of three companies that have been given authority by the US government for federal agencies to use them for sensitive cloud data.
Azure and AWS, alongside CSRA’s ARC-P IaaS, have been given the green light under the new FedRAMP High Baseline requirements.
The full, mammoth spreadsheet documenting each guideline can be found on the FedRAMP website, but at a general level, the requirements enable government bodies to put ‘high impact’ data – including data which involves the protection of life and financial ruin – in the cloud.
Chanelle Sirmons, communications lead for FedRAMP, explained in an official post: “While 80% of federal information is categorized at low and moderate impact levels, this only represents about 50% of the federal IT spend.”
“Now that FedRAMP has set the requirements for high impact levels, that breaks open the remaining 50% of the $80 billion a year the US government spends on IT that could potentially move to the cloud securely… Read More
The Next Wave of Security Opportunities
Excerpted from TechCrunch Report by Mahendra Ramsinghani

More than 5 billion IoT devices were installed in 2015. Gartner estimates this will grow to 20 billion by 2020.
Unfortunately, experts agree that security is not only an afterthought, but often is actively resisted and circumvented.
IoT devices are attractive to hackers because they have very weak login credentials, are “on 24/7” and have little to no secure communication channels.
Hackers have started using these compromised devices to launch DDoS attacks, and even sell Instagram and Twitter robo “likes” for the vain.
Data from an HP IoT study shows that 80 percent of IoT devices failed to require passwords of sufficient complexity and length.
As much as 70 percent of the devices did not encrypt communications. And 60 percent of these devices raised security concerns with their user interfaces.
In an OpenDNS IoT study, 23 percent of respondents said they have no mitigating controls to prevent unauthorized device access in their company’s networks… Read More
US State Department Wants IoT to Save Money
Excerpted from ReadWrite Report by David Curry

The Department of State has announced plans to deploy an Internet of Things (IoT) energy platform to conserve more energy, identify potential issues quicker, and monitor the department’s sensors.
It will be working with C3 IoT (formerly C3 Energy) to deploy the IoT platform to hundreds of thousands of “data points” over the coming years.
This may include foreign embassies and treaty rooms, which the State Department control.
“We will be able to identify and address outliers across our global buildings portfolio, learn how to improve upon previous embassy designs and operations, and lower utility and maintenance costs,” said State Department senior adviser for energy, environment and sustainability, Landon Van Dyke, in a statement to the Wall Street Journal.
C3 IoT provides a development platform and a range of software-as-a-service apps for energy preservation. Detailed analytics can be provided to give the State Department smarter ways to lower energy consumption, while still keeping buildings secure.
The platform runs on GovCloud servers, which are owned by Amazon Web Services and isolated for sensitive government information… Read More
DAO Vulnerability Raises Questions of Trust & Human Factor
Excerpted from CCN Report by Elliot Maras

The discussion and debate around the DAO vulnerability raises questions about trust and the human factor in the evolving realm of distributed ledger technology, Sean Neville, Co-Founder and President of Circle, noted in a Medium blog.
Trust in the safety of assets and data in blockchain systems does not depend on human gatekeepers, Neville noted. But governance over software deployment of specific implementations still requires votes of trust.
Everyone in a peer-to-peer (P2P) network implicitly if not explicitly executes trust decisions in the software, its infrastructure and the contracts and apps that run on top of the software, Neville observed.
Everyone who joins the network makes such trust decisions by investing in assets, running nodes and relying on the asset data in the ledger(s), depending on the network’s executed logic, and adding quality-of-service (latency, throughput, etc.) dependencies between the system or other systems in their professional and personal lives.
But Neville asks: What happens when the system works as designed based on votes made with assets and CPUs but crosses a threshold that invested counterparties and humans view as a breach of fiduciary duty?
Can one intervene to change the system to add safety controls to apply retroactively and change the history… Read More
Coming Events of Interest
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
EuroCloud Forum – October 5th-6th in Bucharest, Romania. The seventh annual EuroCloud Congress will be held for the first time in Romania. With the theme “Creating New Frontiers in European Cloud,” it will be the sector’s largest forum on the future of cloud in Europe.
Security of Things World USA — November 3rd-4th in San Diego, CA. The newest event in the DCIA’s partnership with weCONECT Group has been designed to help you find pragmatic solutions to the most common security threats facing the IoT.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
