In This Issue
- Olympians & IoT Help
- Fog Is IoT Killer App
- “Network of Things”
- Report from the CEO
- Cloudlets: Int Devices
- IoT Nervous System
- Data Privacy Battle
- DNC & Cybersecurity
- GOP & Telecom Law
- China Sparks Concern
- Distrib Batch Control
- Cooling at the Edge
- Half of Cloud Outside
- FCC Plans Revoked
- Fog Min Resources
- Amazon Wins Race
- Coming DCIA Events
Olympians Go for the Gold with Help from the IoT
 The world’s best athletes are currently on display at the 2016 Summer Olympics in Brazil, and some are using wearable technology powered by the Internet of Things (IoT) to help them go for the gold.
The world’s best athletes are currently on display at the 2016 Summer Olympics in Brazil, and some are using wearable technology powered by the Internet of Things (IoT) to help them go for the gold.
United States sprinter Allyson Felix has reached Olympic glory already, taking home gold medals in the 2008 Olympics in Beijing and the 2012 Olympics in London, but she is still looking for a leg-up on her competition.
According to a report from The Huffington Post, she is just one of several athletes embracing wearable IoT technology as they look to improve their training and boost their performance in the games.
Felix trained for her upcoming track-and-field events with a pair of 3D-printed shoes designed specifically for her feet.
The sneakers not only conform perfectly to her foot but provide Felix with feedback on her performance.
According to the report, Felix isn’t the only American Olympian looking to the Internet of Things for improved athletic training and performance.
The men’s cycling team is using technology called Solos Smart Eyewear that allows the cyclists and their coaches to measure distance… Read More
Why Fog Computing is the Killer App for the IoT
Excerpted from RTInsights Report by Carlos Aragon
 The speed at which technology evolves these days is amazing.
The speed at which technology evolves these days is amazing.
Although we are still in the middle of the cloud revolution, suddenly a new networking paradigm has appeared: fog computing.
And it seems to be a key component of another popular trend, the Internet of Things (IoT), or as we prefer to call it, the Internet of Everything.
The evolution from cloud to fog computing shares similarities with the history of computing itself.
Just as computers evolved from bulky mainframes to personal computers as processing power and local storage became smaller and more affordable, networking and applications that started with a centralized model have also evolved.
When mobile devices began to proliferate, keeping information stored and available presented a major challenge.
The first generation of smartphones and tablets had limited storage and processing power and wireless network speeds were significantly slower than their wired counterparts.
This made providers realize that some applications and services could be better served with a centralized model and the cloud was born… Read More
“Network of Things”
Excerpted from ITBusiness Edge Report

The National Institute of Standards and Technology (NIST) has released a new publication that provides a basic model aimed at helping researches better understand the Internet of Things (IoT) and its security challenges.
Expected to approach nearly $2 trillion in market value by 2020, the IoT covers an incredibly large range of technologies – everything from smart homes, wearables, smart factories and building, self-driving cars to health care monitors.
Given the breadth of devices involved, NIST computer scientist Jeff Voas determined that “there is no formal, analytic or even descriptive set of building blocks that govern the operation, trustworthiness and lifecycle of IoT components.”
Instead, Voas has created a new model called the Network of Things (NoT) based on distributed computing, which has been in use for decades.
In distributed computing, computer components are networked and share messages about tasks to operate efficiently.
A simple example is the local area network in an office where computers share a printer.
The Network of Things (NoT) model is based on four fundamentals at the heart of IoT- sensing, computing, communication, and actuation… Read More
Report from DCIA CEO Marty Lafferty
 Computer scientist Jeffrey Voas, through his National Institute of Standards (NIST) Special Publication 800-183, has provided industry with a tool to help address security implications exposed by the Internet of Things (IoT).
Computer scientist Jeffrey Voas, through his National Institute of Standards (NIST) Special Publication 800-183, has provided industry with a tool to help address security implications exposed by the Internet of Things (IoT).
He uses the term Network of Things (NoT) in addition to IoT to encompass local area networks of things that are not connected to the internet, which should be included in this consideration.
Voas’s document also confirms the point we made two years ago at the start of the DCIA’s IoT Marathon: at its most basic level, the IoT can be defined as distributed computing – but with more sensing.
The four fundamentals of NoT are also the same as distributed computing: computation, communication, actuation, and sensing.
While traditional use cases for distributed computing, however, featured a limited amount of sensing, with IoT/NoT, practically every device is a sensor.
And it is sensing, with the resultant enormity of data that is generated, that opens the IoT/NoT to its greatest security problem.
Voas asserts that securing data even on a small scale is challenging, so when it’s scaled to an IoT/NoT scenario, it becomes even more difficult due to heterogeneity and pedigree.
The larger the NoT system, the more difficult it is to determine the integrity of data generated by a connected device – or whether the device is actually connected.
In addition, because IoT is unbounded, security and reliability involving comparisons and analytics, are only meaningful when applied to specific sub-networks.
Voas provides some valuable guidance to assist in this area by defining five primitives, or building blocks, to facilitate comparisons:
Sensors – a physical device which collects raw data.
Aggregators – software that converts raw data into meaningful groupings.
Communication channels – how data is transmitted (e.g., USB, wireless, wired).
External utilities – software or hardware products or services that “execute processes or feed data into the overall workflow of a NoT (e.g., databases, mobile devices, clouds, CPUs).
Decision trigger – a conditional expression that triggers an action.
Voas continues to explain that security ramifications affect each of these building blocks in the architecture of a NoT.
Having a fundamental vocabulary and a scientific foundation to understand IoT/NoT is essential for meaningful risk assessment. Share wisely, and take care.
Cloudlets: Where the Cloud Meets Intelligent Devices
Excerpted from InfoWorld Report by Robert Shimp
 Hyperscale public clouds are well established as the new platform for systems of record.
Hyperscale public clouds are well established as the new platform for systems of record.
Providers of ERP, supply chain, marketing, and sales applications are today predominantly or exclusively based in hyperscale public clouds.
Oracle alone has thousands of customers for its front-office and back-office SaaS.
And the list of customers is growing at a rate far exceeding that of traditional front-office and back-office applications.
Hyperscale public clouds are also, of course, a proper place to run new cloud-native applications that enhance or extend those system-of-record applications.
These new applications are architected differently.
While systems of record are typically large, monolithic applications running in virtual machines in the cloud, cloud-native applications are usually written as micro-services, packaged in containers, and orchestrated to deliver a complete application to users… Read More
The Nervous System of the IoT
Excerpted from Machine Design Report by Michael Heflin
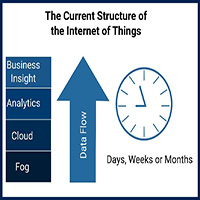 In the human body, the nervous system collects continuous streams of sensory data and transmits the information to the brain to be processed.
In the human body, the nervous system collects continuous streams of sensory data and transmits the information to the brain to be processed.
It helps coordinate actions throughout the body, efficiently collecting data about the environment and simultaneously driving actions.
If software is the brain of the IoT, sensors are the nervous system.
There is no questions the Internet of Things (IoT) is currently a hot topic across industries.
Although there is much discussion about solutions leveraging the IoT, it is still largely underutilized.
There are numerous obstacles to overcome before organizations can fully reap the rewards of successful IoT deployments.
The focus of IoT conversations have been on Big Data, analytics, and cloud computing, but as much as the IoT is about software, it is equally about sensors.
This article offers a framework for understanding the Internet of Things and discusses the path forward in order to achieve its full potential… Read More
Battle over Who Regulates Data Privacy Rages on
Excerpted from Cincinnati Report by Jack Greiner
 As the anecdotes about data breaches continue to accumulate, one lingering question is just who exactly gets to regulate this area?
As the anecdotes about data breaches continue to accumulate, one lingering question is just who exactly gets to regulate this area?
The Federal Trade Commission (FTC) has actively stepped up its efforts – contending that Section 5 of the Federal Trade Commission Act provides the authority.
That Act allows the Commission to challenge “unfair or deceptive acts or practices affecting commerce.” In recent years, the FTC’s authority to go after companies who’ve allowed personal information to be hacked has been challenged – most notably by the Wyndham Hotel chain – but so far, it looks like the FTC can continue its efforts.
In a case involving Wyndham, a federal appellate court noted it is up to the FTC, on a case by case basis, to determine what is “unfair.”
That court concluded Congress “designed the term “unfair” as a ‘flexible concept with evolving content.'” And in a recent decision involving a clinical laboratory called LabMD, the FTC demonstrated how that flexibility works.
LabMd was accused of allowing a massive data breach which compromised personal, medical information of 9,300 consumers… Read More
DNC Creates Cybersecurity Advisory Board Following Hack
Excerpted from Politico Report by Nolan McCaskill
 The Democratic National Committee (DNC) is creating a four-member cybersecurity advisory board, according to a memo obtained by POLITICO on Thursday.
The Democratic National Committee (DNC) is creating a four-member cybersecurity advisory board, according to a memo obtained by POLITICO on Thursday.
The advisory board is a response to the recent DNC hack and subsequent email leak that led to the resignation of former Chairwoman Debbie Wasserman Schultz and other top DNC officials.
“To prevent future attacks and ensure that the DNC’s cybersecurity capabilities are best-in-class, I am creating a Cybersecurity Advisory Board composed of distinguished experts in the field,” interim DNC Chairwoman Donna Brazile wrote in a memo.
“The Advisory Board will work closely with me and the entire DNC to ensure that the party is prepared for the grave threats it faces-today and in the future.”
Members include Rand Beers, former Department of Homeland Security Acting Secretary; Nicole Wong, former Deputy CTO of the US and a former technology lawyer for Google and Twitter; Aneesh Copra, Co-Founder of Hunch Analytics and former CTO of the US; and Michael Sussmann, a Partner in privacy and data security at Perkins Coie and a former DoJ cybercrime prosecutor… Read More
Republicans See Fresh Chance to Overhaul Telecom Law
Excerpted from The Hill Report by David McCabe
 Republicans believe they are finally close to overhauling a landmark law that has been a cornerstone of tech and telecom regulation for decades.
Republicans believe they are finally close to overhauling a landmark law that has been a cornerstone of tech and telecom regulation for decades.
The effort to update the Communications Act, which gives the Federal Communications Commission (FCC) its authority, has been years in the making and has powerful support.
The Chairman of the Senate Commerce Committee and veteran lawmakers on the House Energy and Commerce Committee are vowing to make changing the law a centerpiece of their 2017 agenda.
Proponents of updating the law, first written in 1934 and last revised in 1996, say it’s showing its age and is ill-suited to dealing with a world dominated by high-speed internet and mobile devices instead of phone service and traditional radio broadcasts.
“There are way more moving parts now than there were back then,” said Senate Commerce Committee Chairman John Thune (R-SD) in July, “and we think it’s time for Congress to be heard from again.”
“You know, in the 1996 rewrite, I think the internet, if it was mentioned at all, we maybe mentioned it one or two times,” he said… Read More
China’s Proposed Cybersecurity Laws Spark Concerns
Excerpted from International Business Times Report by India Ashok
 China’s proposed cybersecurity laws have sparked concerns among international businesses, prompting a coalition of 46 business groups from the US, Europe, and Asia to caution that the new rules, if implemented, may negatively impact international trade relations.
China’s proposed cybersecurity laws have sparked concerns among international businesses, prompting a coalition of 46 business groups from the US, Europe, and Asia to caution that the new rules, if implemented, may negatively impact international trade relations.
The group sent a letter to China’s top economic official Premier Li Keqiang, warning that the proposed laws, imposing limitations on information security, may make it easier for hackers to steal data and may also be in violation of World Trade Organization (WTO) rules.
“The current drafts, if implemented, would weaken security and separate China from the global digital economy,” the letter said.
It was signed by the US Chamber of Commerce, Washington DC-headquartered Business Software Alliance (BSA), as well as organizations for insurers and manufacturers from the UK, Japan, Mexico, and Australia, ZDnet reported.
The proposed laws would require technology companies to show Chinese authorities how their products work as well as store information about Chinese citizens within the nation… Read More
The Move to Flexible, Distributed Batch Control
Excerpted from Automation World Report by Stephanie Neil
The term “edge computing” is floating all around the enterprise and on the factory floor as companies push computing applications away from centralized servers toward the corners of the network.
This way, data transactions and analytics take place locally on the device rather than “calling home” to a server or the cloud for instructions.
The impetus for edge computing is the Industrial Internet of Things (IIoT), because as more smart devices are added to the computing infrastructure, network bandwidth may be compromised causing problems in mission critical systems.
This modern approach to processing data locally not only eases network traffic, but also enables real-time analytics and scalability.
And, interestingly, a similar concept is also being applied to more traditional batch applications.
Last month, Rockwell Automation introduced its SequenceManager software, which enables operators to configure, view and obtain critical information about the batch sequences right at the Logix controller… Read More
Resolving Cooling Challenges at the Edge
Excerpted from CIO Review Report

After the welcoming of a wave of disruptive trends, notably the cloud, mobility, social network, and big data, edge computing is the next change that is pushing beyond the conventional data center to the network edges.
Edge computing decreases the amount of data that needs to be transferred, the resulting traffic, and its traveling distance.
It places data and control functions, high bandwidth content, and applications so that they will be more accessible to the end-user.
By doing so, there will be significant reduction in cost, improved quality of services, and the much desired reduction in latency.
Although edge computing is definitely the future, like all data centers, the ones at the edge also have power and cooling issues.
The expulsion of heat from the systems in these data centers requires certain methods and specialized cooling installations.
The conventional wall mount AC systems that are generally used in enterprises do not match the cooling needs in such circumstances… Read More
Half of Cloud Services Outside, but IT Gets Wiser
Excerpted from ZDNet Report by Joe McKendrick
 For starters, the survey of 3,476 IT and IT security practitioners, commissioned by Gemalto, a digital security vendor, finds that half of all cloud services and corporate data stored in cloud are not controlled by IT departments.
For starters, the survey of 3,476 IT and IT security practitioners, commissioned by Gemalto, a digital security vendor, finds that half of all cloud services and corporate data stored in cloud are not controlled by IT departments.
So, there’s a lot of cloud activity among business units that’s potentially not vetted or governed.
However, IT departments are getting a better handle on things, the survey also shows.
Fifty-four percent of respondents are “confident” that the IT organization knows all cloud computing applications, platform or infrastructure services in use – a nine percent increase from a similar survey from 2014.
The survey doesn’t spell out how and why IT is getting a better grip on shadow cloud adoption.
It may be assumed that there are more policies in place and greater communication and collaboration on best practices.
IT may be getting more active in its evolving role as cloud broker or service provider to the enterprise, providing catalogs or directories of vetted services available to business users.
Still, cloud adds a whole dimension to security and governance… Read More
FCC Municipal Broadband Plans Revoked by Appeals Court
Excerpted from TelecomTV Report by Guy Daniels
 The US FCC has received something of a setback in its attempts to foster and encourage greater use of municipal broadband.
The US FCC has received something of a setback in its attempts to foster and encourage greater use of municipal broadband.
The Sixth Circuit Court of Appeals ruled yesterday to reverse the FCC’s 2015 action in support of local broadband projects, unanimously stating that the FCC had exceeded its authority (although there was support for the FCC from Judge Helene White).
It’s a blow to FCC Chairman Tom Wheeler’s attempts at encouraging greater broadband adoption cross the country, especially in areas not served or under-served by telcos.
“While we continue to review the decision, it appears to halt the promise of jobs, investment and opportunity that community broadband has provided in Tennessee and North Carolina,” said Wheeler.
“In the end, I believe the Commission’s decision to champion municipal efforts highlighted the benefits of competition and the need of communities to take their broadband futures in their own hands.”
However, he pledged to fight on, promising: “Should states seek to repeal their anti-competitive broadband statutes, I will be happy to testify… Read More
Fog Computing with Minimal Resources
Excerpted from Embedded Computing Report by Rich Nass
 Edge devices don’t always have the compute power to make compute-intensive decisions. Hence, data is collected at the edge and transferred to the cloud, where the heavy compute engines reside.
Edge devices don’t always have the compute power to make compute-intensive decisions. Hence, data is collected at the edge and transferred to the cloud, where the heavy compute engines reside.
The numbers are crunched and the information is sent back to the edge where some action takes place.
The upside to such a solution is that the edge devices can remain relatively inexpensive, allowing the number crunching to occur where the processing power already lies – in the cloud.
One downside to this approach is that you may be pushing large amounts of data up to the cloud, which can be expensive, as that’s one way that the carriers make their money.
Second, and potentially more important depending on the application, is that there’s a time delay to send, compute, and receive the information.
If it’s a real-time, mission-critical application, such as something in medical or automotive, you may not have the luxury of time. Thanks to Sendyne’s dtSolve, there’s a way to handle those computations at the edge… Read More
Amazon Wins the Cloud Computing Race Again
Excerpted from Profit Confidential Report
 According to Gartner’s “Magic Quadrant” report, Amazon is still the undisputed king of cloud computing.
According to Gartner’s “Magic Quadrant” report, Amazon is still the undisputed king of cloud computing.
Its continued dominance suggests that AMZN stock will keep moving “up and to the right” for the foreseeable future.
In fact, Amazon will become the first trillion-dollar company if its share price keeps rising.
The company’s growth has been nothing short of spectacular this year-so much so that CEO Jeff Bezos became richer than Warren Buffett. Yes, the Warren Buffett.
Bezos’ avalanche of new wealth came directly from a surge in AMZN stock.
Shares of the Internet giant have risen 58.89% since its February lows, sending the firm’s market cap to a whopping $363.13 billion.
Needless to say, it’s been a good year for Amazon.
But when stocks rise as quickly as AMZN stock, investors are left in an awkward position… Read More
Coming Events of Interest
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
EuroCloud Forum — October 5th-6th in Bucharest, Romania. The seventh annual EuroCloud Congress will be held for the first time in Romania. With the theme “Creating New Frontiers in European Cloud,” it will be the sector’s largest forum on the future of cloud in Europe.
Internet & Mobile World 2016 — October 5th-6th in Bucharest, Romania. The largest business-to-business (B2B) expo-conference for information technology (IT) and digital solutions in Central & Eastern Europe (CEE).
Security of Things World USA — November 3rd-4th in San Diego, CA. The next event in the DCIA’s partnership with weCONECT Group has been designed to help you find pragmatic solutions to the most common security threats facing the IoT.
Rethink! Cloudonomic Minds — November 21st-22nd in London, England. The newest event in the DCIA’s partnership with weCONECT Group will cover how IoT is impacting cloud strategies and how to take advantage of these two key technology trends.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
