In This Issue
- Election Night Threat
- Voting System Hacks
- Cyberattacks Whither
- Report from the CEO
- Chinese Cyber Law
- Chip-Level Security
- 100K Infected Devices
- ISPs Could Secure IoT
- DDoS and Cloud Users
- Data Process Options
- Telefonica Solutions
- NetApp Secures Data
- Micros & Smart Nets
- Tech vs. Shutdowns
- IoT Power to Net Edge
- Trends in 2017 Cloud
- Coming DCIA Events
National Threat: An Election Night Hack
Excerpted from CNBC Report by Barbara Booth

For Carmen Medina, the biggest threat facing our nation today is the “super-empowered individual.”
The former CIA Deputy Director of Intelligence joined CNBC’s Squawk Box team Tuesday to discuss intelligence, cybersecurity, the geopolitical situation and the fight against terrorism.
She also addressed the massive DDoS attack on the internet domain directory Dyn on October 21st, in which hackers managed to knock offline a number of popular websites, including Twitter, Netflix, PayPal, Amazon and Spotify.
What made this attack so disturbing is that it appears to have been carried out through hundreds of thousands of internet-connected devices, such as cameras, baby monitors, and routers.
“Just about anybody with decent computer literacy could pull something off like that,” said Medina, who has 32 years in the intelligence field.
She added: “The attacks last week could very well have been disaffected gamers.”
The biggest threat facing our nation right now could involve election night, she said… Read More
Protecting Voting Systems from Hacks
Excerpted from ABC News Report by Geneva Sands

Nearly every state has asked the Department of Homeland Security (DHS) to help protect election systems from hacks, according to the latest tally by DHS.
As of October 31st, 46 states and 35 county or local election agencies have reached out to the department for assistance.
Only 33 states and 11 localities had asked for help as of October 10th.
Time is of the essence for states that need assistance since it can take up to two weeks from the time DHS receives authorization to run the scans and identify vulnerabilities.
It can then take at least a week to mitigate any vulnerabilities that are found, according to DHS.
Homeland Security offers so-called “cyber hygiene scans” on systems linked to the internet, as well as risk and vulnerability assessments for local agencies.
Earlier this month, US intelligence agencies publicly blamed Russia for recent cyberattacks that compromised emails of political organizations in the US, such as the Democratic National Committee… Read More
Feds Hope Cyberattacks Will Wither
Excerpted from ReadWrite Report by David Curry

The Obama Administration is looking to make sure the type of cyberattack that took major websites – like Spotify, Netflix, and Twitter – offline recently does not happen again.
The Department of Homeland Security (DHS) will develop a set of “strategic principles” for connected devices, to ensure they meet security standards and don’t fall into the hands of adversaries.
More than one million connected devices have fallen into the hands of bad actors, most of them don’t have any security or hard encryption.
The DHS is calling for manufacturers to integrate more security into the device, like better encryption and other authentication methods. It is also working with the police to teach officers about defect units.
Two Chinese companies issued recalls earlier this week for compromised connected devices, but there’s little evidence an attack on this scale will not happen again.
The US government hasn’t mentioned who it thought was behind this attack, though some have pointed to state sponsored hackers… Read More
Report from DCIA CEO Marty Lafferty
 The DCIA commends the Federal Communications Commission (FCC) for its approval of broadband consumer privacy rules on Thursday to protect internet users from certain methods of unauthorized collection and utilization of sensitive data regarding their online activity.
The DCIA commends the Federal Communications Commission (FCC) for its approval of broadband consumer privacy rules on Thursday to protect internet users from certain methods of unauthorized collection and utilization of sensitive data regarding their online activity.
The action represents an important – but by no means final – step towards empowering consumers and thereby fostering sustainable advancement and innovation of online services.
The FCC rules apply to broadband network operators, while online web companies are covered separately under privacy protection rules enforced by the Federal Trade Commission (FTC).
Visibility into online users’ behavior is different for internet service providers (ISPs) than for web-based companies, and a critical next step will be to synthesize these different regimes to ensure equitability, provide for a nondiscriminatory approach with consistent regulatory standards, and avoid confusion at the consumer level.
There’s no question that consumers are attracted to online services, regardless of the source, supported by business models that defray costs through the integration of targeted advertising, which can be more valuable to both service providers and end-users than untargeted messages.
In addition, individualized content with enhancements driven by such factors as browsing data and other usage behavior benefits customers greatly.
An essential component to distributed computing industry expansion is maintaining and, where possible, increasing consumer trust, and the FCC’s action attempts to move us in that direction.
The FCC’s rules, which will go into effect next year, require broadband operators to notify subscribers of their new mechanisms for obtaining permission to gather and release data on their web browsing, app use, location, and financial information, in a broader categorization of covered types of data than the FTC’s rules.
The public will be able to decide whether and what information may be collected while using broadband services to connect to the internet by means of devices ranging from PCs to laptops to tablets to smartphones.
Arguably, the structure for consent and the definitions of what constitutes sensitive information should be brought into line for such data collection and for that conducted by online offerings ranging from browsers to websites to software programs to mobile applications.
The bottom line is we agree with FCC Chairman Tom Wheeler: “There is a basic truth: It is the consumer’s information. It is not the information of the network the consumer hires to deliver that information.”
But we also believe that more work is necessary to develop a reasonable and coherent framework of regulations that are consistent and transparent to the consumer, even if enforced by separate agencies, to be applied fairly and in an unbiased manner at all levels of the distributed computing ecosystem. Share wisely, and take care.
Chinese Cybersecurity Law Approval
Excerpted from Reuters Report by Paul Carsten and Michael Martina

A controversial Chinese cybersecurity law that has sparked protests from foreign governments and business groups neared approval on Monday as parliament held the third reading of the draft bill.
The official Xinhua news agency said parliament had fully taken on board the views of the its standing committee and other parties, and had proposed passing the third and typically final reading at its current meeting from Monday to November 7th.
China enforces widespread controls over the internet that it has sought to codify in law.
The new cybersecurity law has met with a barrage of opposition from foreign business lobbies and governments, which say it is vague and could discriminate against overseas companies.
In its previously seen form, published after the second reading, the cybersecurity law would codify sweeping powers for the government, ranging from widespread censorship to heightened control over certain technologies.
Critics are particularly concerned about requirements that companies store data locally and provide encryption keys.
Technology firms are worried that could impinge on privacy and mean they would have to pass on sensitive intellectual property… Read More
The Birth of Chip-Level Security
Excerpted from Electronics360 Report by Tom Kevan
 A little-known technology called physical unclonable functions (PUFs) stands poised to change the fundamental nature of security processes like authentication and cryptographic key generation.
A little-known technology called physical unclonable functions (PUFs) stands poised to change the fundamental nature of security processes like authentication and cryptographic key generation.
IC fabrication processes create slight variations in each chip, creating “silicon biometrics.”
Developers are using these physical unclonable functions to enable IC-level authentication and key generation features.
PUFs mark a shift to a security approach in which hardware plays a major role, providing the means to implement a scalable security scheme that extends down to the IC level.
These changes represent a major transformation in the way security is perceived and implemented.
The question is: what forces triggered this shift and propelled PUFs to the forefront?
Also, what makes this technology so relevant now?
The answer to these questions can be found in the emergence of the Internet of Things (IoT) and distributed infrastructure paradigms… Read More
DDoS from 100K Infected Devices
Excerpted from PC World Report by Michael Kan
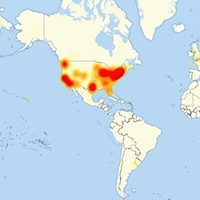
Friday’s massive internet disruption came from hackers using an estimated 100,000 devices, many of which have been infected with a notorious malware that can take over cameras and DVRs, said DNS provider Dyn.
“We are able to confirm that a significant volume of attack traffic originated from Mirai-based botnets,” Dyn said in a Wednesday blog post.
The malware known as Mirai had already been blamed for causing at least part of Friday’s distributed denial-of-service attack, which targeted Dyn and slowed access to many popular sites in the US.
But on Wednesday, Dyn provided new findings, saying Mirai-infected devices were actually the primary source for Friday’s internet disruption.
The statement also suggests that the hackers behind the attack may have been holding back.
Companies have observed variants of the Mirai malware spreading to more than 500,000 devices built with weak default passwords, making them easy to infect… Read More
ISPs Could Secure All IoT Devices
Excerpted from Wired Report by Lily Hay Newman
 A cyberattack on the Internet infrastructure company Dyn on October 21st hindered internet browsing for hours while the company scrambled to restore service.
A cyberattack on the Internet infrastructure company Dyn on October 21st hindered internet browsing for hours while the company scrambled to restore service.
The as-yet unidentified attackers were helped by a millions-strong army of Internet of Things (IoT) devices, including enterprise webcams and DVRs, that were quietly conscripted into a botnet to launch the denial-of-service attack.
The incident is the latest reminder that many IoT devices aren’t adequately secured.
These types of attacks will continue as long as a large enough number of vulnerable devices exists. So the question facing the security industry is how to shrink that number.
Looking forward, the most important step is ensuring that new IoT products are strongly secured before they reach consumers.
This is particularly important for IoT devices, even more so than smartphones and laptops, because IoT products can function for years and consumers often don’t have a reason to replace them… Read More
What DDoS Attacks Mean for Cloud Users
Excerpted from Cloud Expo Report by David Paquette
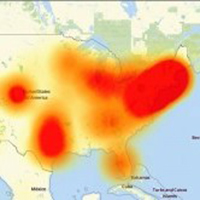 Cloud services are supposedly known for being highly available but various types of outages prevent users from accessing those services, sometimes on very large scale.
Cloud services are supposedly known for being highly available but various types of outages prevent users from accessing those services, sometimes on very large scale.
What are the implications of DDoS attacks on Cloud services and what are the alternatives?
Last Friday, DDoS attacks disrupted major parts of the internet in both North America and Europe.
The attacks seems largely targeted on DNS provider Dyn disrupting access to major service providers such as Level 3, Zendesk, Okta, Github, Paypal, and more, according to sources like Gizmodo.
This kind of botnet-driven DDoS attack is a harbinger of future attacks that can be carried out over an increasingly connected device world based on the Internet of Things (IoT) and poorly secured devices.
This disruption highlights a particular vulnerability to businesses that have chosen to rely on cloud-based services like IaaS, SaaS, or PaaS.
The ability to connect to these services is critical to business operations because if users cannot connect, it is considered downtime… Read More
Multiple IoT Data Processing Options
Excerpted from BizTech Report by Alexander Slagg
The cloud is not the only tool companies can use to capture and analyze data generated by the Internet of Things (IoT).
Alex is a content strategist at CDW, editing and managing digital and print content, with a special focus on security, networking and cloud technologies. He also blogs about creativity and the craft of writing. He currently lives in Chicago.
The IoT comprises billions of connected devices and is often difficult to comprehend.
One of the myths surrounding IoT – that all data processing is done in the cloud – was debunked at the recent Smart Industry conference in Chicago.
There are, in fact, many kinds of edge computing models that handle data processing for IoT connections.
Vivek Dave, Director of Technology Development for Harting, a global manufacturer of industrial connectors, and Wes Dillon, Solutions Consultant for MachineShop, an IoT software company, discussed the growing importance of edge computing at Harting.
Their presentation, “3D Printing and New Conceptual Framework for the IoT Edge,” sparked a conversation… Read More
Telefonica IoT Solutions to Greek Telco
Excerpted from IoT Business News Report
Telefonica Business Solutions, a leading provider of a wide range of integrated communication solutions for the B2B market, will provide Wind Hellas, Greek telecom operator, Telefonica’s Smart m2m solution, its best-in-class platform to manage and control IoT communications.
This Telefonica’s IoT Solution will allow Wind Hellas’ customers not just to have the best connectivity but also end-to-end management and the comprehensive control needed to achieve world-leading, reliable and secure IoT communications between machines.
Juan Revilla, Wholesale business unit CEO, stated, “This agreement with Wind Hellas strengthens our new Telco4Telco approach offering a wide range of digital services and platforms such as IoT, Security, Cloud, Big Data and Consultancy services to our Wholesale customers, enhancing our customers experience and allowing them to generate new revenue streams.”
Developed and built with Telefonica’s own assets and resources, Smart m2m incorporates new advanced features including real time consumption monitoring, supervision and global tracking… Read More
NetApp Secures Data in Hybrid Cloud
Excerpted from BGR Report by Ians

American data storage company NetApp on Wednesday introduced new data fabric solutions and services that maximize control and improve the secure movement of data across the hybrid Cloud.
The company also introduced new versions of NetApp AltaVault, StorageGRID Webscale, and SnapCenter technologies to help customers extract the value of their data from anywhere in the hybrid Cloud.
“Building a hybrid Cloud using NetApp’s data fabric solutions and services allows customers to efficiently control and secure their data while capitalizing on its value for maximum business benefit,” said Phil Brotherton, Vice President of Cloud Business Unit, NetApp, in a statement.
AltaVault, a Cloud-integrated storage solution speeds recovery and reduces risk, enabling customers to securely back up data to on-premises and public Clouds at up to 90 percent lower cost compared to traditional on-premises solutions.
NetApp’s object-based storage solution for web applications “StorageGRID Webscale” is designed for the hybrid Cloud to store and manage massive datasets in a single global namespace.
The latest release of SnapCenter centralizes data protection and clone management with new application plug-ins… Read More
Microservices & Smart Networks
Excerpted from Linux.com Report by Carla Schroeder
 Imagine smart cars talking directly to each other so they don’t crash.
Imagine smart cars talking directly to each other so they don’t crash.
Imagine hooking your smart phone into a giant mesh of phone video streams at a stadium event, so you can watch your event from multiple perspectives.
Imagine smart factory devices that manage themselves for better safety and efficiency.
Imagine intelligent phones, and other intelligent devices, communicating directly at close range so they don’t bog down the Internet or cell phone networks.
It doesn’t take much imagination to see how this benefits disaster management, to give one example, which traditionally is hampered by overloaded phone networks.
What makes all of this possible?
Robert Shimp of Oracle paints a picture at LinuxCon North America of a fascinating future full of specialized distributed services and devices… Read More
Advanced Tech vs. Future Shutdowns
Excerpted from Daily Caller Report by Eric Lieberman
 An internet shutdown in the Northeastern US happened roughly a week ago, and the experts are looking for ways to prevent this attack from ever happening again.
An internet shutdown in the Northeastern US happened roughly a week ago, and the experts are looking for ways to prevent this attack from ever happening again.
Websites like Twitter and Spotify were inaccessible for thousands of people following the distributed denial of service (DDoS) attack on Dyn, a major domain name system (DNS) host. DNS, the technical network that converts web address names into numbers, is essentially the “yellow pages” of online addresses.
The perpetrators likely “hijacked the devices [equipped with internet] by installing the malware and then conscripted them into a ‘botnet,’ which is essentially an army of electronic devices unwittingly controlled by an unauthorized individual or entity,” Jeff Baron, a web pioneer who owned an accredited domain name registrar business, told The Daily Caller News Foundation.
The DDoS attack reportedly infected hundreds of thousands of devices around the globe and then directed those electronics to flood servers with artificial traffic.
The effects of malware on IoT devices could have a range of different effects… Read More
IoT Drives Computing Power to Edge
Excerpted from Computerworld Report by Stuart Corner
 According to Matt Henshall, the ‘head of things’ at global software development company Thoughtworks, the Internet of Things (IoT) is reversing to some extent the trend of recent years of moving processing power to the cloud and instead distributing it at the edge.
According to Matt Henshall, the ‘head of things’ at global software development company Thoughtworks, the Internet of Things (IoT) is reversing to some extent the trend of recent years of moving processing power to the cloud and instead distributing it at the edge.
“Corporates are only just getting used to the idea of having the cloud but now those of us ahead of developments are saying we need to distribute some of that power to the edge, and that is going to be an interesting challenge,” Henshall told Computerworld.
“As more devices are connected to the Internet there will be a shift to edge computing, sometimes called fog computing.”
Fog computing is a term invented by Cisco that is now gaining wide acceptance following the formation of the Open Fog Consortium, with the backing of a number of major vendors.
Henshall took on the role of head of things with Thoughtworks based in San Francisco in February 2015 after three years as CTO of Australian smart home and environment IoT company, Environexus.
He told Computerworld that his role was to bring a perspective on IoT to Thoughtworks and its clients… Read More
Trends to Shape Cloud Computing in 2017
Excerpted from CIO Report by Clint Boulton
 Cloud computing has helped many enterprises transform themselves over the last five years, but experts agree that the market is entering something of a second wave, both for public cloud and private cloud services built and hosted in corporate data centers.
Cloud computing has helped many enterprises transform themselves over the last five years, but experts agree that the market is entering something of a second wave, both for public cloud and private cloud services built and hosted in corporate data centers.
The cloud market will accelerate faster in 2017 as enterprises seek to gain efficiencies as they scale their compute resources to better serve customers, says Forrester Research in a new report.
“The No. 1 trend is here come the enterprises,” says Forrester analyst Dave Bartoletti, primary author of the research.
“Enterprises with big budgets, data centers and complex applications are now looking at cloud as a viable place to run core business applications.”
Forrester says the first wave of cloud computing was created by Amazon Web Services, which launched with a few simple compute and storage services in 2006. A decade later, AWS is operating at an $11 billion run rate.
Forrester found that 38 percent of 1,000-plus North American and European enterprise infrastructure technology decision-makers… Read More
Coming Events of Interest
Rethink! Cloudonomic Minds — November 21st-22nd in London, England. R!CM will cover how IoT is impacting cloud strategies and how to take advantage of these two key technology trends.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
CES 2017 — January 5th-8th in Las Vegas, NV. More than 3,800 exhibiting companies showcasing innovation across 2.4 million net square feet, representing 24 product categories.
Industry of Things World USA — February 20th-21st in San Diego, CA. Global leaders will gather to focus on monetization of the Internet of Things (IoT) in an industrial setting.
fintech:CODE — March 16th-17th in London, UK. A new international knowledge exchange platform bringing together all DevOps, IT, and IoT stakeholders who play an active role in the finance and tech scene. Key topics include software development, technical challenges for DevOps, DevOps security, cloud technologies and SaaS.
retail:CODE — March 16th-17th in London, UK. 20 real-life case studies, state-of-the-art keynotes, and interactive World Café sessions, 35+ influential speakers will share their knowledge at the intersection of the retail and technology sectors.
