In This Issue
- NetApp’s S-S Arrays
- Cybersecurity Focus
- Privacy Protection
- Report from the CEO
- Car Hacking Threat
- Protect Customers
- NSA Broke Encryption
- Cloud Data Encryption
- Why Still a Challenge
- Retail Not Investing
- Architecture Concerns
- Cooling at the Edge
- Half of Cloud Outside
- FCC Plans Revoked
- Fog Min Resources
- Amazon Wins Race
- Coming DCIA Events
NetApp Recognized as Leader in Solid-State Arrays
Excerpted from MarketWired Report
 NetApp announced that it has been named a Leader in the 2016 Gartner Magic Quadrant for Solid-State Arrays, based on its ability to execute and its completeness of vision.
NetApp announced that it has been named a Leader in the 2016 Gartner Magic Quadrant for Solid-State Arrays, based on its ability to execute and its completeness of vision.
According to Gartner, Leaders execute well against their current vision and are well positioned for tomorrow.
“We believe our position as a Leader in this year’s Magic Quadrant for Solid-State Arrays underscores the fact that NetApp is enabling customers’ successful transition to flash,” said George Kurian, Chief Executive Officer (CEO) of NetApp.
“As flash replaces hard disk drives for primary workloads, we are winning against and replacing both established and emerging vendors because of the successful business outcomes enabled by our highly differentiated all-flash-array portfolio.”
A Gartner Magic Quadrant is a culmination of research in a specific market, providing readers with a wide-angle view of the relative position of the market’s offerings.
By applying a graphical treatment and a uniform set of evaluation criteria, Gartner Magic Quadrants assess vendors on their ability to execute and the completeness of their vision… Read More
Corporate Directors Focusing on Cybersecurity
Excerpted from San Diego Union-Tribune Report by Mike Freeman
 As high profile data breaches continue to grab headlines, corporate boards need to make sure they’re deeply involved in the cyber-safeguards at their companies.
As high profile data breaches continue to grab headlines, corporate boards need to make sure they’re deeply involved in the cyber-safeguards at their companies.
“They have to accept responsibility,” said David Finn, a former federal prosecutor who spent 16 years leading Microsoft’s efforts to fight cybercrime, counterfeiting and fraud.
“It’s not just a server room issue. It’s a board room issue.”
A group of national cybersecurity experts will discuss cyber-threats next week at the Corporate Directors Forum at Qualcomm’s headquarters.
The San Diego, CA non-profit helps corporate board members with training and networking.
Finn, who is now Chief Operating Officer (COO) at AppEsteem in Seattle, will join Illumina Chief Information Officer (CIO) Norm Fjeldheim and FBI Cyber Division Section Chief Philip Celestini on for the Corporate Directors Forum meeting.
After a high-profile hack 3 years ago at Target compromising millions of shoppers’ data, the retailer’s board ousted CEO Gregg Steinafel… Read More
California Adds Privacy Protection to Data Breach Law
Excerpted from Planet Biometrics Report

A California lawmaker has proposed that a standard be established for businesses to protect personal consumer information including location and biometric data.
Assemblyman Mike Gatto (D) wants to revive an old privacy bill, adding new standards for businesses to use reasonable security procedures and practices if they hold or maintain personal information, reports Bloomberg Law.
Gatto told Bloomberg that his new amendments reflect a compromise he negotiated for two years with business and privacy groups that still accomplishes his intent to set standards for protecting personal data where none now exist.
“The next frontier is to use facial recognition to track you when you walk into a mall,” he said.
“People who store this information should have strong encryption and consumer protections.”
The newspaper notes that the new bill would expand the definition of personal information in California law beyond social security numbers, driver’s license numbers, and medical information to include geolocation and biometric data, tax identification numbers, passport numbers, military identification numbers, and employment identification numbers… Read More
Report from DCIA CEO Marty Lafferty
 Following up on last week’s report, the National Institute of Standards and Technology (NIST) has placed a request for information (RFI) in the Federal Register to support the new White House Commission on Enhancing National Cybersecurity
Following up on last week’s report, the National Institute of Standards and Technology (NIST) has placed a request for information (RFI) in the Federal Register to support the new White House Commission on Enhancing National Cybersecurity
Information of interest to the Commission encompasses a great many issues related to cybersecurity concerns and issues that can be forecast through the coming decade.
Private sector organizations, including corporations, universities, and security professionals – as well as trade associations – are encouraged to submit responses by the deadline of September 9th.
The RFI invites replies from numerous perspectives regarding best practices to prevent cyber-attacks and mitigate the impact of attempted hacks.
The use of cybersecurity products and services, similarly, to prevent unwanted intrusions on businesses and individuals, is another general topic area suitable for submission.
Coverage of specific technical operations subjects ranging from identity management to conditional access to phishing prevention, for example, also will be welcome.
Of interest, too, are recommendations related to industry standards setting for cybersecurity in emerging technologies in such areas as mobile cloud and the Internet of Things (IoT) and international protocols, behavioral norms, and cooperative practices among nations.
Proposed techniques for adopting the NIST Cybersecurity Framework, a series of planning guidelines, are also sought.
And as part of any discussion of cybersecurity, in the view of the DCIA, data privacy should be as much of a consideration as sharing threat intelligence.
As a DCIA member company or DCINFO reader, if you need assistance in responding to the RFI by the September 9th deadline, please contact me. Share wisely, and take care.
Advocates Want FCC to Address Car Hacking Threat
Excerpted from Morning Consult Report by Amir Nasr
 The burgeoning Internet of Things (IoT) has brought with it a slew of new devices.
The burgeoning Internet of Things (IoT) has brought with it a slew of new devices.
The automobile industry is among those poised to be a key player in this world, with technology that could enable vehicles to communicate with one another and infrastructure such as smart traffic lights.
But those developments bring with them added vulnerabilities for carmakers.
Hackers could exploit vehicles’ use of airwaves to steal personal information or even take control of driving functions.
Those worries have prompted advocacy groups and some Senate Democrats to call on the Federal Communications Commission (FCC) to issue rules requiring automakers to bolster cybersecurity and privacy protections for consumers.
The rulemaking process will take a step forward Wednesday, the deadline for comments on a petition filed in June with the FCC requesting that the agency draft rules for the privacy and cybersecurity practices of automobile and tech companies that use the Direct Short Range Communication service.
Responses to those comments are due on September 8th… Read More
8 Tips for Protecting Your Customers’ Data
Excerpted from The Business Journals Report by Marc Prosser
 With data breaches running rampant these days, trying to ensure that your customers’ sensitive data should be a top priority.
With data breaches running rampant these days, trying to ensure that your customers’ sensitive data should be a top priority.
But it can also be scary; are you really able, as a small business, to protect that information from potential hackers?
Just like with any potential threat, there are always practices you can implement that can shore up your security and reduce the risk of a data breach.
Here are a few simple (and affordable) practices to start implementing today.
1. Keep your software updated.
You might be annoyed whenever that pop-up box tells you it’s time to update software, but doing so is key to avoiding security risks. Hackers look for weak spots in software, and attacking older versions is like shooting fish in a barrel.
When Microsoft stopped supporting Windows XP, they let users know that anyone still using it would be at risk, and encouraged people to update to the new version of Windows… Read More
Leak Reveals How NSA Broke Encryption
Excerpted from Forbes Report by Thomas Fox-Brewster
 The leak of NSA hack tools, now all-but confirmed, included an exploit for old Cisco product PIX, which provided firewall and VPN capabilities.
The leak of NSA hack tools, now all-but confirmed, included an exploit for old Cisco product PIX, which provided firewall and VPN capabilities.
It’s the first time a specific NSA VPN exploit has been uncovered and proven to work.
If the Shadow Brokers’ leak of NSA files is legit, as is now all but confirmed, they have offered a glimpse into how the intelligence agency exploited security systems created by American tech vendors.
And one of the vulnerabilities has offered proof of just how the US’ finest digital spies were able to snoop on encrypted communications, in particular those provided by Virtual Private Networks (VPNs).
The weakness resided in Cisco’s PIX product, discontinued back in 2009, according to an analysis by London-based security researcher Mustafa Al-Bassam.
The so-called BENIGNCERTAIN exploit dropped by the Shadow Brokers was not dissimilar to the infamous Heartbleed hacks of 2014: the snoop would send specially-crafted requests to a Cisco PIX server… Read More
Cloud Data Encryption – Great, But Not Magic Bullet
Excerpted from CloudTech Report by Ed Macnair
 The headlong stampede of enterprise data into the cloud has passed by.
The headlong stampede of enterprise data into the cloud has passed by.
A few years ago I might have written it was “underway,” but this would grossly understate the situation.
Data which was once stored on premise has left the building, the twinkling lights on the tin box in your racks are slowly blinking out.
Data osmosis is taking place, draining life force from these antiquated shells into vast data-centers run by some of the largest companies on earth.
It is more than a trend. It is just reality.
So as a million barn gates are slammed, the new question on everyone’s lips is one of security.
How do we keep that perfectly curated company data safe when prying eyes hidden in a world of VPNs, bulletproof hosting and dark forums are watching?
In this world, encryption is often touted as a savior… Read More
Why Is Cloud Security Still a Challenge?
Excerpted from Baseline Magazine Report by Samuel Greengard
 Over the past couple of years, cloud adoption has spiked.
Over the past couple of years, cloud adoption has spiked.
Organizations increasingly view the technology as a productive and secure way to approach IT.
Yet, despite remarkable advances in this space, the initiatives are increasingly complex, according to a newly released report from the Ponemon Institute and security firm Gemalto.
The “2016 Global Cloud Data Security Study” found that cloud security and data security remain a challenge for many organizations.
Among other things, not all data is controlled by IT departments, highly sensitive data often remains unencrypted, security and privacy protections are often lacking, and shadow IT can represent real-world risks.
The study, which includes responses from 3,476 IT and IT security practitioners worldwide, offers insight into key trends in data governance and security practices for cloud-based services.
As Larry Ponemon, Founder and Chairman of the Ponemon Institute explains: “Cloud security continues to be a challenge for companies… Read More
Retailers Aren’t Investing in Cybersecurity
Excerpted from FedScoop Report by Chris Bing
 As high-profile hacks like Target, Home Depot and Eddie Bauer show, US-based retail stores are especially susceptible to damages caused by hackers.
As high-profile hacks like Target, Home Depot and Eddie Bauer show, US-based retail stores are especially susceptible to damages caused by hackers.
A new survey out Tuesday shows how much that damage usually amounts to.
A data breach costs retail outlets, on average, roughly 19 percent of their customer base, according to a survey conducted by global audit, tax and advisory firm KPMG.
Nearly one-fifth of respondents told KPMG they would avoid a retailer that was the target of a successful cyber-attack, regardless of how the company remediated damages caused by hackers.
Another 33 percent of people surveyed said they would wholly abandon an affected business for about three months, due to immediate fears concerning the exposure of personal and financial information typically stored by the retailer.
Interestingly, these same customers also said they are least likely to return to a hacked store when its leadership fail to publicize a solid plan to prevent future cyber-attacks… Read More
Architecture Concerns for Distributed Systems
Excerpted from DZone Report by Munish Gupta
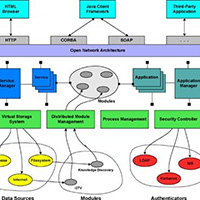
Application architectures are evolving from the era of large monoliths to a more distributed design based model.
One of the key initiators of this movement is the advent of cloud computing and the ability it brings in terms of handling ever-increasing scale.
When an enterprise primarily soaked (people and processes) with the model of building and managing monolithic applications, the journey to build new distributed systems requires re-learning some of the older design techniques and adopting some new patterns.
As part of this, I will detail certain architecture concerns that become prominent when moving to a distributed model of application.
Scheduler/Orchestration management: Going from managing hundreds of instances to managing thousands of instances require the ability to orchestrate/schedule service instances/containers across hosts in a seamless manner.
To handle increasing scale, workload scheduling/orchestration is a key ingredient of distributed system… Read More
Resolving Cooling Challenges at the Edge
Excerpted from CIO Review Report

After the welcoming of a wave of disruptive trends, notably the cloud, mobility, social network, and big data, edge computing is the next change that is pushing beyond the conventional data center to the network edges.
Edge computing decreases the amount of data that needs to be transferred, the resulting traffic, and its traveling distance.
It places data and control functions, high bandwidth content, and applications so that they will be more accessible to the end-user.
By doing so, there will be significant reduction in cost, improved quality of services, and the much desired reduction in latency.
Although edge computing is definitely the future, like all data centers, the ones at the edge also have power and cooling issues.
The expulsion of heat from the systems in these data centers requires certain methods and specialized cooling installations.
The conventional wall mount AC systems that are generally used in enterprises do not match the cooling needs in such circumstances… Read More
Half of Cloud Services Outside, but IT Gets Wiser
Excerpted from ZDNet Report by Joe McKendrick
 For starters, the survey of 3,476 IT and IT security practitioners, commissioned by Gemalto, a digital security vendor, finds that half of all cloud services and corporate data stored in cloud are not controlled by IT departments.
For starters, the survey of 3,476 IT and IT security practitioners, commissioned by Gemalto, a digital security vendor, finds that half of all cloud services and corporate data stored in cloud are not controlled by IT departments.
So, there’s a lot of cloud activity among business units that’s potentially not vetted or governed.
However, IT departments are getting a better handle on things, the survey also shows.
Fifty-four percent of respondents are “confident” that the IT organization knows all cloud computing applications, platform or infrastructure services in use – a nine percent increase from a similar survey from 2014.
The survey doesn’t spell out how and why IT is getting a better grip on shadow cloud adoption.
It may be assumed that there are more policies in place and greater communication and collaboration on best practices.
IT may be getting more active in its evolving role as cloud broker or service provider to the enterprise, providing catalogs or directories of vetted services available to business users.
Still, cloud adds a whole dimension to security and governance… Read More
FCC Municipal Broadband Plans Revoked by Appeals Court
Excerpted from TelecomTV Report by Guy Daniels
 The US FCC has received something of a setback in its attempts to foster and encourage greater use of municipal broadband.
The US FCC has received something of a setback in its attempts to foster and encourage greater use of municipal broadband.
The Sixth Circuit Court of Appeals ruled yesterday to reverse the FCC’s 2015 action in support of local broadband projects, unanimously stating that the FCC had exceeded its authority (although there was support for the FCC from Judge Helene White).
It’s a blow to FCC Chairman Tom Wheeler’s attempts at encouraging greater broadband adoption cross the country, especially in areas not served or under-served by telcos.
“While we continue to review the decision, it appears to halt the promise of jobs, investment and opportunity that community broadband has provided in Tennessee and North Carolina,” said Wheeler.
“In the end, I believe the Commission’s decision to champion municipal efforts highlighted the benefits of competition and the need of communities to take their broadband futures in their own hands.”
However, he pledged to fight on, promising: “Should states seek to repeal their anti-competitive broadband statutes, I will be happy to testify… Read More
Fog Computing with Minimal Resources
Excerpted from Embedded Computing Report by Rich Nass
 Edge devices don’t always have the compute power to make compute-intensive decisions. Hence, data is collected at the edge and transferred to the cloud, where the heavy compute engines reside.
Edge devices don’t always have the compute power to make compute-intensive decisions. Hence, data is collected at the edge and transferred to the cloud, where the heavy compute engines reside.
The numbers are crunched and the information is sent back to the edge where some action takes place.
The upside to such a solution is that the edge devices can remain relatively inexpensive, allowing the number crunching to occur where the processing power already lies – in the cloud.
One downside to this approach is that you may be pushing large amounts of data up to the cloud, which can be expensive, as that’s one way that the carriers make their money.
Second, and potentially more important depending on the application, is that there’s a time delay to send, compute, and receive the information.
If it’s a real-time, mission-critical application, such as something in medical or automotive, you may not have the luxury of time. Thanks to Sendyne’s dtSolve, there’s a way to handle those computations at the edge… Read More
Amazon Wins the Cloud Computing Race Again
Excerpted from Profit Confidential Report
 According to Gartner’s “Magic Quadrant” report, Amazon is still the undisputed king of cloud computing.
According to Gartner’s “Magic Quadrant” report, Amazon is still the undisputed king of cloud computing.
Its continued dominance suggests that AMZN stock will keep moving “up and to the right” for the foreseeable future.
In fact, Amazon will become the first trillion-dollar company if its share price keeps rising.
The company’s growth has been nothing short of spectacular this year-so much so that CEO Jeff Bezos became richer than Warren Buffett. Yes, the Warren Buffett.
Bezos’ avalanche of new wealth came directly from a surge in AMZN stock.
Shares of the Internet giant have risen 58.89% since its February lows, sending the firm’s market cap to a whopping $363.13 billion.
Needless to say, it’s been a good year for Amazon.
But when stocks rise as quickly as AMZN stock, investors are left in an awkward position… Read More
Coming Events of Interest
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
EuroCloud Forum — October 5th-6th in Bucharest, Romania. The seventh annual EuroCloud Congress will be held for the first time in Romania. With the theme “Creating New Frontiers in European Cloud,” it will be the sector’s largest forum on the future of cloud in Europe.
Internet & Mobile World 2016 — October 5th-6th in Bucharest, Romania. The largest business-to-business (B2B) expo-conference for information technology (IT) and digital solutions in Central & Eastern Europe (CEE).
Security of Things World USA — November 3rd-4th in San Diego, CA. The next event in the DCIA’s partnership with weCONECT Group has been designed to help you find pragmatic solutions to the most common security threats facing the IoT.
Rethink! Cloudonomic Minds — November 21st-22nd in London, England. The newest event in the DCIA’s partnership with weCONECT Group will cover how IoT is impacting cloud strategies and how to take advantage of these two key technology trends.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
