In This Issue
- Cloud’s Killer Quarter
- Cloud Skills Pay Most
- America Tech Council
- Report from the CEO
- Agency Data Breaches
- St/Loc Cybersecurity
- Top Organization Risk
- Cybersecurity Mindset
- How to Train Workers
- WikiLeaks CIA Dump
- Site Security Checks
- True Cloud Definition
- Fog Is Coming: Good
- APIs Key to Transform
- Data Center Changes
- Cloud Wars New Phase
- Coming DCIA Events
Cloud Computing Has another Killer Quarter
Excerpted from Network World Report by Fredric Paul
 To most people, Jeff Bezos’ Amazon is known as the company reshaping the way people buy everything from books to shoes to groceries.
To most people, Jeff Bezos’ Amazon is known as the company reshaping the way people buy everything from books to shoes to groceries.
But the part of Amazon that is driving Bezos within shouting distance of becoming the world’s richest person doesn’t really sell anything, it rents computing power in the cloud.
As the New York Times put it on Thursday, “The profit Amazon can make on cloud-computing services is significantly bigger than in its retail sales, and that has helped turn the Seattle company from a consistent money-loser to a respectable moneymaker.”
And that, as Bloomberg noted, sparked a jump in Amazon’s stock price in after-hours trading that added more than $3 billion to Bezos’ nest egg, topping $80 billion for the first time and putting him within $5 billion of becoming the world’s richest person.
The first quarter numbers tell the tale. Amazon Web Services (AWS) booked a whopping $890 million in operating income in the period ending March 31, accounting for most of the company’s profits: the company as a whole recorded just $1.01 billion in net income… Read More
Cloud Computing Skills Pay the Most
Excerpted from Forbes Report by Louis Columbus
 These and many other insights are from Computerworld’s IT Salary Survey 2017 Results.
These and many other insights are from Computerworld’s IT Salary Survey 2017 Results.
The survey found the hiring outlook remaining steady with 43% of 1,263 IT managers interviewed predicting their companies’ IT staffs to expand this year.
49% said they expect staffing levels to remain the same.
Just 7% said they anticipate a decrease.
The survey was conducted between August and November 2016, during which 2,782 IT professionals who are employed full time or part time were interviewed.
At the 95% confidence level, the margin of error for this sample size is 1.9 percentage points.
Key takeaways from the survey include the following:
Average compensation for cloud computing jobs is $129,743 making it the most lucrative of all specialties in 2017… Read More
Trump Creates American Technology Council
Excerpted from Engadget Report by Timothy Seppala
 The White House has issued an executive order creating the American Technology Council.
The White House has issued an executive order creating the American Technology Council.
“Americans deserve better digital services from their government,” Donald Trump writes.
“The Federal Government must transform and modernize its information technology and how it uses and delivers digital services.”
The Council’s aim is to “coordinate the vision strategy, and direction for the federal government’s use of information technology (IT) and the delivery of services through information technology,” according to the order.
The executive order further states that the Council will use IT to advise policy decisions.
But, it “shall not extend to any national security systems.”
The order also says that the director of national intelligence will be “encouraged” to provide access to classified information regarding cybersecurity threats, vulnerabilities, and mitigation procedures.
While the executive order focuses heavily on modernizing the White House, there are still several vacancies… Read More
Report from DCIA CEO Marty Lafferty

The $1 trillion spending bill to fund the US federal government through September includes increases in areas of importance to the distributed computing industry.
The Federal Bureau of Investigation (FBI), Department of Homeland Security (DHS), and Secret Service each will receive additional levels of funding for cybersecurity.
The FBI will receive $277 million more for combating cyber-crime as well as $92 million more for the Immigration and Customs Enforcement (ICE) agency for cyber-crime investigations.
DHS’ cyber operations division will receive an additional $183 million, representing more than a ten percent boost to the division’s total budget, nearly all of which is earmarked for securing dot-gov networks and upgrading emergency communications.
The Secret Service will receive $112 million more in part for investigating financial cyber-crimes.
An additional significant change will be to standardize a government-wide definition of cybersecurity for budgeting purposes.
The Office of Management and Budget (OMB) will consult with the appropriations, budgeting, and homeland security panels in the House and Senate to arrive at a common understanding of what federal activities count as cybersecurity.
And finally, the bill also allocates $100 million to fund civic advocacy organizations that work to defend democratic institutions against Russian influence campaigns, including defense against cyberattacks and online propaganda efforts.
The omnibus appropriation will replace a short-term continuing resolution that expired May 5th, requiring approval in both houses of Congress and signature by the President. Share wisely, and take care.
A Third of Federal Agencies Had 2016 Data Breaches
Excerpted from Dark Reading Report
 One-third of federal government agencies reported experiencing a data breach in the last year, and 65% have experienced one in the past, according to the 2017 Thales Data Threat Report, Federal Edition.
One-third of federal government agencies reported experiencing a data breach in the last year, and 65% have experienced one in the past, according to the 2017 Thales Data Threat Report, Federal Edition.
Nearly all (96%) respondents consider themselves “vulnerable” to data breaches; about half (48%) state they are “very” or “extremely” vulnerable.
Researchers found 61% of US federal respondents are increasing their security spend this year, which is an increase from last year’s 58%, but still lower than healthcare (81%), retail (77%), and financial services (78%) industries.
Federal respondents claim their data insecurity is primarily due to budget constraints (53%) and lack of staff (53%).
Advanced technologies like cloud, big data, containers, and IoT are expected to worsen the problem as they are used without proper security measures in place.
Federal agencies must deal with critical needs for sensitive data in volume, the most challenging threat environments, the strictest regulations and the most difficult budget constraints – and it’s putting their data at risk… Read More
Bill Boosts State & Local Cybersecurity
Excerpted from CyberScoop Report by Shaun Waterman
 Proposed legislation establishing a Department of Homeland Security (DHS) grant program that would bolster cybersecurity for state and local government IT networks faces a steep climb in Congress, but its backers say the need is urgent.
Proposed legislation establishing a Department of Homeland Security (DHS) grant program that would bolster cybersecurity for state and local government IT networks faces a steep climb in Congress, but its backers say the need is urgent.
“There’s an acknowledgment that this is a real problem and that things could get worse. As former Defense Secretary Leon Panetta has observed, we’re at something of a pre-9/11 point in cyber,” said Congressman Derek Kilmer (D-WA)., a co-sponsor of the State Cyber Resiliency Act, HR 1344.
Cyber threats “aren’t aimed at red districts or blue districts – all of our communities are vulnerable. There is an obvious need and I hope that makes it more likely that this bill could move,” Kilmer told CyberScoop in an interview.
His GOP co-sponsor is Virginia Congresswoman Barbara Comstock.
An identical companion bill in the Senate, S 516, is sponsored by Senators Mark Warner (D-VA) and Cory Gardner (R-CO).
The proposed law, backed by a broad coalition of state and local leaders and tech vendors, would put the Federal Emergency Management Agency in charge of doling out the money, starting in fiscal 2018, which begins in October… Read More
Cybersecurity Tops 2017 Organization Risks
Excerpted from CIO Report by David Adler
 Cybersecurity and privacy continue to make headlines.
Cybersecurity and privacy continue to make headlines.
Experts have more questions than answers addressing risk management concerns in the evolving cybersecurity market.
On March 7, 2017, the CIA got doxed by the anti-secrecy organization WikiLeaks.
Nearly 9,000 documents appeared online showing the CIA sought to observe conversations, online browsing habits and other activities by infiltrating the systems that contained them, such as Apple and Android smartphones, laptops, TVs and even cars.
The government is not alone.
Third-party vendors remain a growing source of concern.
Companies are well-advised to look beyond their own cybersecurity policies and standards to the potentially bigger risk that arises from giving third-party vendors direct access into their systems.
Indeed, low-tech threats like errors by vendors’ employees represent an often-overlooked danger to company data security… Read More
Businesses Must Fix Wrong Cybersecurity Mindset
Excerpted from TechRepublic Report by Conner Forrest
 While businesses understand the importance of cybersecurity, they are relying on outdated strategies and misguided mindsets to protect themselves, according to a new report from CompTIA, released Tuesday.
While businesses understand the importance of cybersecurity, they are relying on outdated strategies and misguided mindsets to protect themselves, according to a new report from CompTIA, released Tuesday.
The report, titled ” The Evolution of Security Skills,” claims that many businesses remain too defensively-focused in the way they address cyber-threats.
Instead, CompTIA calls on security pros to become more proactive by seeking out and mitigating vulnerabilities before they are exploited.
“Building an impenetrable defense is no longer practical and the mentality of preventing all breaches is outdated,” Seth Robinson, Senior Director of Technology Analysis for CompTIA, said in a press release.
“But a new, proactive approach combining technologies, procedures and education can help find problem areas before attackers discover them.”
Business leaders tend to focus too heavily on threats they are familiar with – namely, malware and viruses, according to the report… Read More
How to Train Workers in Cybersecurity
Excerpted from Computerworld Report by Matt Hamblen

With workplace cyberattacks on the rise, industry experts are pressing businesses to train their workers to be more vigilant than ever to protect passwords and sensitive data and to recognize threats.
“It is imperative for organizations of all sizes to instill among employees the critical role they play in keeping their workplace safe and secure,” said Michael Kaiser, Executive Director of the National Cyber Security Alliance, a group that promotes education on the safe and secure use of the internet.
The group’s members include such major technology companies as Cisco, Facebook, Google, Intel and Microsoft.
Kaiser made his comments timed with last week’s release of a Dell End-User Security Survey that found that 72% of workers are willing to share confidential company information without regard for proper data security protocols.
The survey was conducted online in late February and early March with results from 2,608 professionals in companies with more than 250 workers.
“Cybersecurity education needs to be an integral part of the workplace culture,” Kaiser added… Read More
WikiLeaks CIA Dump Most Damaging Yet
Excepted from TechCrunch Report by Eric O’Neill
 It’s impossible to keep up with the nonstop news coverage and multiple storylines around the recent WikiLeaks CIA dump.
It’s impossible to keep up with the nonstop news coverage and multiple storylines around the recent WikiLeaks CIA dump.
The initial Vault 7 data drop led to Assange’s press conference about “helping” private companies patch vulnerabilities, all while fear started to spread around the intelligence community listening in to our internet-connected Samsung TVs and Apple products at home, and Cisco disclosing that its routers and Internet switches had been hacked.
Most recently, CIA Director Mike Pompeo criticized WikiLeaks in his first public address since being confirmed, calling the organization a “non-state hostile intelligence service.”
Pompeo makes an undeniable point about the far-reaching consequences of a leak such as this one – which, speaking from an intelligence perspective, is likely the most frightening yet.
The truth of the matter is that the breach of the CIA’s attack tools not only placed the US at a deficit in our offensive cyber-capabilities, it has threatened the world’s most critical businesses, organizations, and national security peace of mind.
To echo Pompeo’s statements, we are now all more vulnerable… Read More
Checking a Website’s Security
Excerpted from NY Times Report by JD Biersdorfer
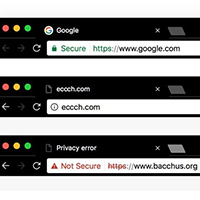 Q. I was browsing online and noticed a small letter “i” in a circle. What does that mean? I use the Chrome browser.
Q. I was browsing online and noticed a small letter “i” in a circle. What does that mean? I use the Chrome browser.
A. The web is full of sites that do not use the strongest security, and some browsers – including Google Chrome and Mozilla Firefox – now warn users when the page they are visiting may put their information at risk.
In Chrome, that “i” symbol indicates a site may not be secure because it is using an unencrypted connection to exchange data with your computer.
When you click the “i” on the left side of the Chrome address bar, you can see more information about the site, adjust some settings and possibly see a “Your connection to this site is not secure” warning.
As you may have noticed from online shopping, sites with secure connections use a form of the HyperText Transfer Protocol Secure technology to encrypt data between their web servers and your computer; this helps protect your credit-card number and other personal information from being intercepted by someone else.
These sites also have a security certificate from a presumably trusted authority that verifies the website’s identity… Read More
True Cloud Definition Lost on Some IT Pros
Excerpted from Search Cloud Computing Report by Mark May
 In almost any enterprise IT shop, you are likely to see at least one laptop sticker that says, “There is no cloud. It’s just someone else’s computer.”
In almost any enterprise IT shop, you are likely to see at least one laptop sticker that says, “There is no cloud. It’s just someone else’s computer.”
I understand that the saying is good for a laugh, but aside from that, it could not be further from the truth.
If we stick to the definition of cloud computing outlined by the US government’s National Institute of Standards and Technology (NIST), the cloud has five attributes: on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service.
Do you notice anything on that list about location?
Cloud computing, in all its various deployment models, has fundamentally changed how computing works.
It is not a place, but rather a way of managing IT resources.
If we dig deeper into the NIST definition of cloud computing, we can see it has three common service models:
Software-as-a-Service (SaaS) is a software deployment model where an application is delivered over the internet… Read More
Fog Is Coming: Good News for Cloud
Excerpted from CIO Report by Robert MacInnis
 The cloud has been in the news a lot lately, and mostly for bad behavior.
The cloud has been in the news a lot lately, and mostly for bad behavior.
It’s been slow, expensive, insecure or simply MIA – taking major corporations offline for hours and raising questions about the future of cloud computing.
Is cloud computing going away? Absolutely not, but a rapidly emerging new technology may mean that we won’t be stuck with our cloudy blues for long.
Imagine enabling organizations to leverage the benefits of both cloud and on-site IT, with the speed, resiliency, bandwidth and scalability to run existing workloads – regardless of location – and to power new technologies such as the Internet of Things (IoT) and machine learning.
This new approach is called “fog computing,” and it is poised to have a huge impact on how – and where – computing happens in the very near future.
Fog looks like a cloud, but it’s closer to you… Read More
APIs Key to Digital Transformation
Excerpted from CloudTech Report by Monica Brink
 Digital transformation continues to dominate boardroom discussions as businesses increasingly realize the organizational and cost efficiencies that digitization can provide.
Digital transformation continues to dominate boardroom discussions as businesses increasingly realize the organizational and cost efficiencies that digitization can provide.
The concept reflects technology’s role in both shaping and stimulating strategic decision-making, with its ability to automate and simplify business processes, improve customer relationships, enhance productivity, and reap cost savings.
In fact, IDC predicts that by the end of 2017, two-thirds of CEOs of global 2000 enterprises will have digital transformation at the center of their corporate strategy.
However, it can be a challenge for organizations to implement a digitization strategy against a background of increasingly complex day-to-day IT operations, which often involve managing both cloud and on-premises IT infrastructure.
For many, application programming interfaces (APIs) are an essential component of merging the old and the new IT platforms, capturing vast amounts of data and ultimately achieving their digital transformation strategy.
The most common description of an API is a set of functions and procedures that allow applications to access features or data… Read More
Cloud Changes Data Center Industry
Excerpted from Data Center Frontier Report by Rich Miller
 Welcome to our sixth Data Center Executive Roundtable, a quarterly feature showcasing the insights of thought leaders on the state of the data center industry, and where it is headed.
Welcome to our sixth Data Center Executive Roundtable, a quarterly feature showcasing the insights of thought leaders on the state of the data center industry, and where it is headed.
In our First Quarter 2017 roundtable, we will examine four topics: How the rise of the cloud is shaping the data center industry, the prospects for additional consolidation and M&A, the latest significant trends in data center tools, and how the focus on speed to market is affecting the data center supply chain.
Here’s a look at our distinguished panel:
Jeff Klaus is General Manager of Intel Data Center Software Solutions, which provide real-time, server-level data on the power and thermal conditions across a wide range of data center servers.
Sean Iraca is vice president of service enablement at Digital Realty, the leading provider of wholesale data centers and technology real estate.
Gary Niederpruem is Vice President, Global Marketing and Strategy for Vertiv… Read More
Cloud Wars Enter New Phase
Excerpted from CloudTech Report by Rick Delgado
 Imagine a business where the product keeps getting better and better, like storage space and video quality, but the prices keep falling steadily as the product continues to improve.
Imagine a business where the product keeps getting better and better, like storage space and video quality, but the prices keep falling steadily as the product continues to improve.
It’s happening in cloud computing – and this ‘race to zero’ has people in the industry deeply worried.
The current leader, Amazon Web Services (AWS), slashed their prices an astounding 44 times in the past six years.
Amazon’s strategy, it seems, is more of a low cost, high volume model.
This strategy seems to be working according to research company Gartner, who reported that AWS stores twice as much customer data as the next seven leading public cloud companies.
AWS profits in 2016 grew over 120% and sales grew over 60%, extinguishing any assumptions that AWS was a loss leader product for Amazon as a whole.
Amazon is betting at such a low cost, enterprise businesses will treat cloud services like you treat products at Walmart.
With such low prices on products, you’ll keep adding more to your cart… Read More
Coming Events of Interest
Security of Things World — June 12th and 13th in Berlin, Germany. A world class event focused on the next information security revolution. Security concerns that preoccupy enterprise customers today and pragmatic solutions to threats.
Autonomous Systems World — June 14th and 15th in Berlin, Germany. An international knowledge exchange among top experts in the field, providing a unique glimpse into the fascinating world of autonomous robots, intelligent machines, and smart technologies.
INTRASECT — June 29th and 30th in Washington, DC. The first conference of its kind to engage key stakeholders in a comprehensive and engaging examination of existing and future regulatory policy governing the usage of commercial autonomous vehicles.
Industry of Things World Asia — July 3rd and 4th in Singapore. An international knowledge exchange platform bringing together more than 300 high-level executives who play an active role in the industrial internet of things (IoT).
Industry of Things World Europe — September 18th and 19th in Berlin, Germany. Join more than 1,000 high-level executives to rethink your technology and business strategy for scalable, secure, and efficient IoT.
IoT Solutions World Congress — October 3rd through 5th in Barcelona, Spain. This event has grown enormously in no time and is an excellent barometer and source of information, inspiration, collaboration and transformation.
