In This Issue
- Cloud Computing Wins
- Cloud and Telephony
- Edge vs. Cloud Sense
- Report from the CEO
- Edge Replace Cloud?
- What Is Torrenting?
- AetherWorks Joins OC
- Cisco’s IoT Platform
- Fog, Mist, Hardware
- Cybersecurity So Hard
- Threats to Address
- Pay Ransomware?
- Why Problems Worse
- Redouble Your Efforts
- Hughes Hubbard Wins
- No Drone Registration
- Coming DCIA Events
Cloud Computing Is Winning EVERYTHING
Excerpted from Network World Report by Fredric Paul
 Everyone knows that thoroughbred racehorses typically get funny, exotic names – from Hit It A Bomb to Paulassilverlining.
Everyone knows that thoroughbred racehorses typically get funny, exotic names – from Hit It A Bomb to Paulassilverlining.
But who knew there was a horse named Cloud Computing, let along that nag would snag the second jewel in the 2017 Triple Crown?
It turns out The Preakness Stakes winner was a 13-1 long shot, but it doesn’t take an expert handicapper to see that the technology platform is becoming a prohibitive favorite.
Heck, I’ve been making that call for a while now, including down the stretch this year:
Cloud computing has another killer quarter—April 28
The cloud is growing 7 times faster than the rest of IT—February 21
The cloud continues to rise—and fast—February 6
More proof the cloud is winning big—January 19… Read More
Is Cloud the Answer for Telephony?
Excerpted from Report by Alan Pritchard
 Telephony was among the first communication platforms to be used and has been around for nearly 150 years.
Telephony was among the first communication platforms to be used and has been around for nearly 150 years.
For most of this time, it existed as traditional hard-wired, exchange based technology.
Over the last 10 to 15 years a revolutionary change occurred with the advent of IP telephony using internet technology coinciding with the popularity of other services such as the World Wide Web, streaming, and online.
This is when the term Unified Communications was first coined, bringing together separate means of communication such as telephony, video, and chat.
Arguably it was the first radical move in a long-established industry and such was the popularity of this shift that today predominantly only IP Telephony products are available.
Most providers of IP telephony products supply similar products with differentiators such as reliability and features.
It has been common for businesses to buy, install, and maintain them themselves as was the case with their predecessors, traditional telephones… Read More
Make Sense of Edge vs. Cloud
Excerpted from InfoWorld Report by David Linthicum
 The internet of things (IoT) is real, and it’s a real part of the cloud.
The internet of things (IoT) is real, and it’s a real part of the cloud.
A key challenge is how you can get data processed from so many devices.
Cisco Systems predicts that cloud traffic is likely to rise nearly fourfold by 2020, increasing 3.9 zettabytes (ZB) per year in 2015 (the latest full year for which data is available) to 14.1ZB per year by 2020.
As a result, we could have the cloud computing perfect storm from the growth of IoT.
After all, IoT is about processing device-generated data that is meaningful, and cloud computing is about using data from centralized computing and storage.
Growth rates of both can easily become unmanageable.
So what do we do? The answer is something called “edge computing.”
We already know that computing at the edge pushes most data processing out to the edge of the network, close to the source of the data… Read More
Report from DCIA CEO Marty Lafferty

Following up on our reports focusing on US President Donald Trump’s cybersecurity executive order, White House Cybersecurity Coordinator Rob Joyce this week provided additional insights at a meeting of the National Telecommunications Advisory Committee.
Key provisions include holding agency leaders accountable for IT security within their organizations and requiring agency adherence to the NIST cybersecurity framework.
A major thrust of the directive is to institute a more holistic government-wide approach to federal networks and how to protect them.
At the present time, many agencies in various branches of government employ outdated hardware and programs that provide less protection against cyberattacks than can be provided with up-to-date systems, components, and software.
The administration intends to pinpoint the locations of the risks, analyze and prioritize best methods to mitigate them, and reallocate funds to address needs to update the systems where such risks are unacceptable.
Joyce stressed the benefits of a government-wide approach versus continuing to have departments take individual responsibility, which can lead to a lowest common denominator weakest link in the interlinked federal network.
The Department of Homeland Security (DHS) and Commerce Department are tasked with engaging the private sector on a voluntary basis to combat botnets, and Joyce encouraged cooperation in doing so. Share wisely, and take care.
Will Edge Computing Replace the Cloud?
Excerpted from InformationWeek Report by Andrew Froehlich
 Although we’re only beginning to scratch the surface when it comes to the capabilities of cloud applications, many are already contemplating the successor to cloud architectures.
Although we’re only beginning to scratch the surface when it comes to the capabilities of cloud applications, many are already contemplating the successor to cloud architectures.
One such technology being discussed is a called edge computing.
This is a concept where we move computation that’s currently centralized inside the cloud back to the edge in a distributed manner.
Doing this provides key benefits that make it superior to traditional cloud architectures. But will it eventually replace the cloud in the enterprise? That’s our topic of discussion today.
The notion of edge computing is nothing new.
In fact, prior to cloud computing, we relied on our PC to provide the lion’s share of our computational needs as we ran applications locally.
But the cloud has changed all that… Read More
What’s Torrenting? 4 Things to Know
Excerpted from Cloudwards Report by Fergus O’Sullivan
 You’ve probably heard of Internet piracy and copyright infringement and that it’s made possible by something called torrenting.
You’ve probably heard of Internet piracy and copyright infringement and that it’s made possible by something called torrenting.
But what is torrenting exactly? How does it work?
In this article Cloudwards.net is going to explain to you what torrenting is, the risks associated with torrenting and how you can get started up- and downloading files yourself.
Before we start, realize that torrenting is a kind of file sharing and is not inherently illegal.
However, most of the stuff you find on torrent sites is copyrighted material and downloading it is very much not allowed; if you torrent a movie, book or game, you’re breaking the law.
What you do is up to you, but know you’re doing it on your own lookout.
When you download something off the Internet, you usually click a download button and the files comes onto your computer like manna from heaven… Read More
AetherWorks Joins OpenFog Consortium
Excerpted from AetherWorks Press Announcement
 AetherWorks, a software research and venture development firm based in New York, announces its membership in the OpenFog Consortium, a global organization driving industry and academic leadership in Fog Computing.
AetherWorks, a software research and venture development firm based in New York, announces its membership in the OpenFog Consortium, a global organization driving industry and academic leadership in Fog Computing.
As part of the Consortium, AetherWorks will share insights and expertise to help shape policies and requirements for standards around Fog.
“As our first OpenFog member in New York’s Silicon Alley, AetherWorks is making important contributions to the advancement of fog computing through their patented work in software-defined storage and scalable deployment architectures,” said Helder Antunes, Chairman of OpenFog and Senior Director of Corporate Strategic Innovation Group at Cisco.
“AetherWorks’ investments in fog-related startups provides a ‘spark’ to new technologies that will ultimately help solve challenges in fog computing. We welcome their contributions in OpenFog as we work to deliver an open and interoperable architecture to enable advanced IoT and 5G applications.”
The AetherWorks mission is to bring original, high quality technology to market through development and investment.
The firm, which was started by CEO and Founder Robert MacInnis, Ph.D., specializes in fault-tolerant distributed systems… Read More
Partners Bullish on Cisco’s New IoT Platform
Excerpted from CRN Report by Mark Haranas
 Partners are pumped about the new IoT Operations Platform unveiled by Cisco today; they believe Cisco’s platform can solve many of the issues customers have when deploying internet of things (IoT) solutions.
Partners are pumped about the new IoT Operations Platform unveiled by Cisco today; they believe Cisco’s platform can solve many of the issues customers have when deploying internet of things (IoT) solutions.
“Right now, I’m dealing with customers in the medical industry that have problems with the WannaCry ransomware attack because these connected medical devices are running very old operating systems – they have no updates, no ability to change the operating system, they can’t scale.”
“There’s a lot of struggles with IoT,” said Robert Keblusek, CTO of Sentinel Technologies, a Downers Grove, IL solution provider and Cisco Gold partner.
“There’s not really an easy platform or at scale. How do you manage and scale these things? How do you secure them at scale? These are all questions I think Cisco’s platform can answer.”
Cisco recently finished a survey of 1,845 business IoT leaders which found that 60 percent of IoT initiatives stalled at the proof-of-concept stage.
Of the 40 percent of the IoT projects that made it through to the pilot stage, only 26 percent were deemed successful… Read More
Fog, Mist, and Hardware in Factory Automation
Excerpted from Smart Industry Blog by JC Ramirez
 Although cloud computing is pervasive and popular in consumer technology, the cloud isn’t always ideal in industrial applications because factory automation needs real-time connectivity without latency or intermittent-connectivity issues, as well as industrial-grade equipment that can handle the factory environment.
Although cloud computing is pervasive and popular in consumer technology, the cloud isn’t always ideal in industrial applications because factory automation needs real-time connectivity without latency or intermittent-connectivity issues, as well as industrial-grade equipment that can handle the factory environment.
The next generation of computing–fog and mist–and the applications for factory automation and embedded devices are just now being realized.
On the hardware side, the latest processers are small-form-factor systems that enable industrial applications.
By bringing connected hardware, data processing, data analytics, and data storage closer to the edge with nearer physical proximity, fog and mist computing address many cloud-computing issues.
Fog computing brings that proximity to the factory floor (close to the machine) while mist computing brings it right onto or into the machine… Read More
Why Is Cybersecurity So Hard?
Excerpted from Harvard Business Review Report by Michael Daniel
 After nearly 20 years of trying and billions of dollars in investment, why are organizations are still struggling with cybersecurity?
After nearly 20 years of trying and billions of dollars in investment, why are organizations are still struggling with cybersecurity?
In fact, the problem seems to be getting worse, not better.
Answering this question requires moving beyond a purely technical examination of cybersecurity.
It’s true that the technical challenges are very real; we don’t know how to write bug-free code, for example.
But if you look at the challenge more broadly, even if we resolved the technical issues, cybersecurity would remain a hard problem for three reasons:
It’s not just a technical problem.
The rules of cyberspace are different from the physical world’s.
Cybersecurity law, policy, and practice are not yet fully developed… Read More
Emerging Cybersecurity Threats to Address
Excerpted from Dark Reading Report by Kelly Sheridan
 As security pros scramble to defend against today’s threats as well as a new wave of attacks such as the WannaCry ransomware worm, emerging technologies and determined cybercriminals are poised to make cyber-defense even more complex.
As security pros scramble to defend against today’s threats as well as a new wave of attacks such as the WannaCry ransomware worm, emerging technologies and determined cybercriminals are poised to make cyber-defense even more complex.
Machine learning and the internet of things (IoT) aren’t new terms, but they’re new to the workplace.
As more businesses adopt advanced systems, they’ll find themselves vulnerable to a broader range of security threats.
The geopolitical landscape will also drive security risk as nation-states target foreign adversaries without fear of punishment.
At last week’s Interop ITX conference in Las Vegas, security experts discussed the implications of current and future threats.
Here are what they identified as the next big threats for enterprises:
IoT poses a tremendous security threat as users and devices become increasingly connected.
The problem is, it’s so new that many people haven’t begun to worry about it… Read More
Should You Pay Ransomware?
Excerpted from CNET News Report by Alfred Ng
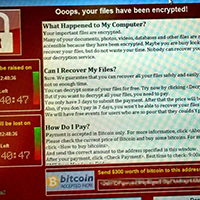 The people behind the WannaCry ransomware want you to pay up.
The people behind the WannaCry ransomware want you to pay up.
If you’re one of the 4,000 victims a day who gets hit with ransomware, you’re now stuck with a dilemma.
While the key advice to dealing with ransomware is prevention — update your patches, back up your files, don’t open any suspicious emails — it really doesn’t mean much after you’ve already been locked out of your computer while hackers extort your own encrypted files from you.
So now the question is: Do you pay up?
The short answer is no, but if you want the long answer, keep reading.
The WannaCry virus has struck in more than 200 countries, seized more than 300,000 devices and set a deadline for this Friday — one week after it infected hospitals, universities and businesses.
Payments for the ransom spiked on Monday, one day before the ransom doubled from $300 to $600.
There were more payments on that Monday than on Tuesday, Wednesday and Thursday combined, according to a tracker following bitcoins… Read More
Why Cyber Problems Are Getting Worse
Excerpted from Dark Reading Report by Grant Elliott
 In 2016, over $18 billion was spent on cybersecurity.
In 2016, over $18 billion was spent on cybersecurity.
It’s estimated that almost a trillion dollars more will be spent over the next five years.
Despite this, research shows that the problem is getting worse. Data breaches are at an all-time high, and the fierceness of these attacks has never been greater.
The reason is not that we’re unable to develop smarter, better technologies to secure our data but that we use these technologies in a scattered and siloed approach.
Also, we fail to leverage most companies’ greatest asset — their people.
Protecting data has always been a challenge, but there are a number of reasons why it’s becoming harder in the digital age.
Digitization of information: Unprecedented amounts of data are now online.
If you were to put all the data on the Internet on CD-ROMs and stack them on top of each other, they would bypass the moon… Read More
Redouble Your Cybersecurity Efforts
Excerpted from CBS News Report by Ray Martin
 The WannaCry ransomware attack that crippled computers worldwide could result in the largest financial and economic losses ever.
The WannaCry ransomware attack that crippled computers worldwide could result in the largest financial and economic losses ever.
And it’s a harsh reminder of how difficult it can be to keep your data and devices safe.
Given that it’s all but impossible to function without using the internet every day, any connected device and your data are always exposed to cyberthreats.
They’re everywhere, and you can do little to stop them.
But you can take steps to safeguard yourself. Think if them as pieces of your personal cybersecurity policy.
Of course, the first and most important thing is to create strong passwords for your devices and online accounts — and change them often.
And don’t think a six-digit password will do. That’s almost like having no password at all.
Hackers use password-generation tools, multiple dictionaries of English and foreign words, and linguistic patterns… Read More
Hughes Hubbard Wins Patent Venue Supreme Court Case
Excerpted from Hughes Hubbard News Announcement

Hughes Hubbard scored a decisive victory for TC Heartland LLC in the Supreme Court of the United States.
The Court’s 8-0 decision restores patent venue protections which US businesses had enjoyed for nearly a century between 1897 and 1990.
The patent venue statute, 28 U.S.C. § 1400(b) provides that patent infringement actions “may be brought in the judicial district where the defendant resides ”
The statute governing “venue generally,” 28 U.S.C. § 1391, has long contained a subsection (c) that, where applicable, deems a corporate entity to reside in multiple judicial districts.
In Fourco Glass Co. v. Transmirra Products Corp., 353 U.S. 222 (1957), the Supreme Court held that § 1400(b) is not to be supplemented by § 1391(c), and that as applied to corporate entities, the phrase “where the defendant resides” in § 1400(b) “mean[s] the state of incorporation only.” Id. at 226.
That interpretation of § 1400(b) stood for more than 30 years until the Federal Circuit, in VE Holding Corp. v. Johnson Gas Appliance Co… Read More
Court Strikes Down Drone Registration Rule
Excerpted from TV Technology Report by Deborah McAdams
 A federal court has struck down the Federal Aviation Administration’s drone registration rule.
A federal court has struck down the Federal Aviation Administration’s drone registration rule.
The US Court of Appeals for the DC Circuit today ruled in favor of John Taylor, a Washington, DC model aircraft enthusiast who challenged the FAA’s registration requirement in court. “The 2012 FAA Modernization and Reform Act provides that the FAA ‘may not promulgate any rule or regulation regarding a model aircraft,’ yet the FAA’s 2015 Registration Rule is a ‘rule or regulation regarding a model aircraft.’
Statutory interpretation does not get much simpler.
The registration rule is unlawful as applied to model aircraft,” the ruling stated. The FAA first opened up the web-based registration for model unmanned aircraft owners on Dec. 21, 2015.
More than 300,000 drones were registered within the first month.
Registration required information on the manufacturer, model and serial number, in addition to the owner’s physical and email addresses… Read More
Coming Events of Interest
Security of Things World — June 12th and 13th in Berlin, Germany. A world class event focused on the next information security revolution. Security concerns that preoccupy enterprise customers today and pragmatic solutions to threats.
Autonomous Systems World — June 14th and 15th in Berlin, Germany. An international knowledge exchange among top experts in the field, providing a unique glimpse into the fascinating world of autonomous robots, intelligent machines, and smart technologies.
INTRASECT — June 29th and 30th in Washington, DC. The first conference of its kind to engage key stakeholders in a comprehensive and engaging examination of existing and future regulatory policy governing the usage of commercial autonomous vehicles.
Industry of Things World Asia — July 3rd and 4th in Singapore. An international knowledge exchange platform bringing together more than 300 high-level executives who play an active role in the industrial internet of things (IoT).
Industry of Things World Europe — September 18th and 19th in Berlin, Germany. Join more than 1,000 high-level executives to rethink your technology and business strategy for scalable, secure, and efficient IoT.
IoT Solutions World Congress — October 3rd through 5th in Barcelona, Spain. This event has grown enormously in no time and is an excellent barometer and source of information, inspiration, collaboration and transformation.
