In This Issue
- Amazon’s Stock $1K
- ENISA Cybersecurity
- Telefonica & Huawei
- Report from the CEO
- Oracle and Tencent
- APAC Cybersecurity
- Rackspace Cloud CEO
- Cloud for Telephony?
- Edge vs. Cloud Sense
- Edge Replace Cloud?
- AetherWorks Joins OC
- Cisco’s IoT Platform
- Cybersecurity So Hard
- Threats to Address
- Why Problems Worse
- Redouble Your Efforts
- Coming DCIA Events
Amazon’s Stock Price Hits $1,000
Excerpted from NY Times Report
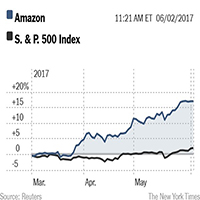 Amazon’s share price briefly topped $1,000 in early trading on Tuesday, a symbolic milestone for Jeff Bezos’ e-commerce company.
Amazon’s share price briefly topped $1,000 in early trading on Tuesday, a symbolic milestone for Jeff Bezos’ e-commerce company.
Amazon’s stock is up sharply over the last three months, the latest surge in a climb that has lasted two decades.
Another big tech stock is also near the $1,000 mark: Alphabet, the parent company of Google, is trading around $996 a share, having also risen sharply in recent months.
Amazon is making itself indispensable on a number of fronts, most notably e-commerce and cloud computing.
It is also expanding into areas like artificial intelligence and entertainment services.
Our tech columnist recently wrote that of the big five tech companies – Amazon, Alphabet, Apple, Facebook, and Microsoft – the one he would have the hardest time giving up was Amazon.
Among the many things Amazon has going for it: After years of unprofitability, it is reliably turning in profit.
Long the runaway leader in e-commerce, Amazon has tens of millions of subscribers for its Prime service… Read More
ENISA Advances Key Cybersecurity Areas
Excerpted from ENISA Press Announcement
 The EU Agency for Network and Information security – ENISA – together with industry recently reached a common position on cybersecurity, which reflects the concerns of industry and provides a set of suggestions for policy makers.
The EU Agency for Network and Information security – ENISA – together with industry recently reached a common position on cybersecurity, which reflects the concerns of industry and provides a set of suggestions for policy makers.
The paper focuses on four main areas actively debated at the EU level: standardization and certification, security processes and services, security requirements and implementation, and the economic dimensions.
The paper identifies key challenges and recommendations identified for the European Commission to accomplish the following.
Define a policy framework for ensuring minimal security requirements for connected devices.
The development of European security standards needs to become more efficient and/or adapted to new circumstances related to Internet of Things (IoT).
Based on those requirements, a European scheme for certification and the development of an associated trust label should be evaluated… Read More
DCINFO EDITOR’S NOTE: See also The Impact on US Discovery of EU Data Protection and Discovery Blocking Statutes
Telefonica & Huawei Take Aldea to the Cloud
Excerpted from RapidTVNews Report by Juan Gonzalez
 Canada’s Aldea Solutions has reached a five-year agreement with Telefonica and its partner Huawei to support its online video platform in Mexico.
Canada’s Aldea Solutions has reached a five-year agreement with Telefonica and its partner Huawei to support its online video platform in Mexico.
By using Telefonica Open Cloud, Aldea’s Mexican operation expects to reduce OPEX and improve business efficiency.
Through its technology partner Huawei, Telefonica is already offering public cloud services to a number of Mexican enterprises, SMEs and public sector organizations.
As provider of services and solutions for TV and media, Aldea offers integrated transmission services through its fiber network and associated teleports in Mexico.
The Aldea proposal includes: full-time and occasional use of services, video as a file, high-definition coding, and all production and transmission solutions that a client may need.
Present in the main cities throughout the Americas, located in Canada, the US, Mexico, Colombia, Panama, Venezuela, Brazil, Argentina, Peru and Chile, Aldea claims to operate the first fully-automated pan-American fiber-optic network for TV broadcasting services… Read more
Report from DCIA CEO Marty Lafferty

Last month, the DCIA signed-on to an industry letter to the government of China, and we now join a group of more than fifty trade organizations and chambers of commerce in urging officials to delay implementation of a new law that will be harmful to the advancement of cloud computing.
The National People’s Congress’s Standing Committee passed the law in 2016, and supplemental sections published by the government expanded its scope to cover business sectors beyond technology providers, making it even more onerous due to its ambiguous language, restrictive provisions, and anti-competitive regulatory framework.
The law requires that companies store data generated or gathered in China in servers located within the mainland, benefiting local cloud providers like Alibaba and Tencent to the detriment of international providers like Amazon and Microsoft.
In addition to restrictions on data transmission, another provision mandates inspection of equipment and applications before deployment in China, and verification of technology as subject to government control.
Beyond undergoing a comprehensive new security review process, hardware and software providers will also be required to assist authorities in conducting security investigations.
An additional regulation mandates that end users register their real names in order to access messaging services.
All told, the measures will add costly burdens, restrict competition, discourage innovation, and may in fact decrease the security of products and services as well as jeopardize the privacy of Chinese citizens.
Exacerbating the problems of ambiguous wording, there is also a great deal of confusion regarding implementation, which is not clearly spelled out in the law, therefore raising concerns with respect to compliance and enforcement.
Widespread uncertainty about the law will have a chilling effect on the growth of cloud computing and innovation in China.
To date, the Cyberspace Administration of China, which regulates the internet there, has delayed implementation of the regulations governing cross-border data flow until the end of 2018, and the DCIA urges similar postponements for the other provisions of the law.
Share wisely, and take care.
Oracle Expands Cloud Reach with Tencent
Excerpted from South China Morning Post Report by Bien Perez
 Oracle, the world’s largest seller of enterprise software, may look to its partnership with Tencent Holdings to distribute its NetSuite portfolio of online business applications in mainland China’s software-as-a-service (SaaS) market, an industry segment projected for total sales of up to $1.6 billion this year.
Oracle, the world’s largest seller of enterprise software, may look to its partnership with Tencent Holdings to distribute its NetSuite portfolio of online business applications in mainland China’s software-as-a-service (SaaS) market, an industry segment projected for total sales of up to $1.6 billion this year.
That initiative, following Oracle’s $9.3 billion acquisition of NetSuite last year, is part of the company’s latest investment in the world’s second-largest economy, where it has established operations since 1989, chief executive Mark Hurd recently told the South China Morning Post.
“We have a development center in Beijing that does a lot of localization for our products, and we’ve doubled our sales force in China over the past year,” Hurd said.
“So with NetSuite now part of Oracle, we plan to continue investments in the country, which is not without a few challenges here and there.”
Cloud computing enables companies to buy, sell, lease or distribute a range of software and other digital resources as an on-demand service over the internet, just like electricity from a power grid… Read More
Bill to Boost Cybersecurity in Asia-Pacific
Excerpted from The Hill Report by Morgan Chalfant
 A House Committee Chairman has introduced legislation aimed at increasing cyber cooperation with allies in the Indo-Asia-Pacific region.
A House Committee Chairman has introduced legislation aimed at increasing cyber cooperation with allies in the Indo-Asia-Pacific region.
The bill, introduced by House Armed Services Committee Chairman Mac Thornberry (R-TX), would require the Pentagon to report to Congress on how to enhance cyber defense efforts and counter propaganda coming from China, Russia and North Korea.
The proposed provision is part of a broader effort to boost security in the region, which has been hampered by North Korea’s ballistic missile and nuclear programs in addition to ongoing territorial disputes in the East and South China seas.
Both North Korea and China have been known to engage in cyberattacks, Pyongyang most infamously in the cyberattack against Sony Pictures Entertainment in 2014.
The bill, introduced before the holiday weekend, would authorize more than $2.1 billion in the coming fiscal year for security initiatives in the Indo-Asia-Pacific region.
Thornberry intends to include the measure in annual House defense legislation that the committee is scheduled to consider later this month… Read More
Rackspace Names President of Private Cloud
Excerpted from Talkin’ Cloud Report by Nicole Henderson

Rackspace announced on Thursday that it has named David Meredith president of private cloud and managed hosting, effective immediately.
Meredith is the second appointment Rackspace has made in as many weeks after naming Joe Eazor CEO at the end of May.
Meredith will lead the largest revenue-driving business at Rackspace, its single-tenant business, with the goal of growth through investments and product strategy.
He will report to Eazor, whose official start date is June 12th.
Prior to Rackspace, Meredith served as President of global data centers at CenturyLink.
Previously, he held various leadership roles in international managed hosting businesses.
“As a pioneer in the managed hosting business, Rackspace is strongly positioned to succeed in a market where businesses want help moving out of their legacy data centers so they can be more strategic in their IT operations,” Meredith said.
“I’m pleased to be joining the Rackspace team at such an exciting time in the company’s history, and in the industry overall… Read More
Is Cloud the Answer for Telephony?
Excerpted from Report by Alan Pritchard
 Telephony was among the first communication platforms to be used and has been around for nearly 150 years.
Telephony was among the first communication platforms to be used and has been around for nearly 150 years.
For most of this time, it existed as traditional hard-wired, exchange based technology.
Over the last 10 to 15 years a revolutionary change occurred with the advent of IP telephony using internet technology coinciding with the popularity of other services such as the World Wide Web, streaming, and online.
This is when the term Unified Communications was first coined, bringing together separate means of communication such as telephony, video, and chat.
Arguably it was the first radical move in a long-established industry and such was the popularity of this shift that today predominantly only IP Telephony products are available.
Most providers of IP telephony products supply similar products with differentiators such as reliability and features.
It has been common for businesses to buy, install, and maintain them themselves as was the case with their predecessors, traditional telephones… Read More
Make Sense of Edge vs. Cloud
Excerpted from InfoWorld Report by David Linthicum
 The internet of things (IoT) is real, and it’s a real part of the cloud.
The internet of things (IoT) is real, and it’s a real part of the cloud.
A key challenge is how you can get data processed from so many devices.
Cisco Systems predicts that cloud traffic is likely to rise nearly fourfold by 2020, increasing 3.9 zettabytes (ZB) per year in 2015 (the latest full year for which data is available) to 14.1ZB per year by 2020.
As a result, we could have the cloud computing perfect storm from the growth of IoT.
After all, IoT is about processing device-generated data that is meaningful, and cloud computing is about using data from centralized computing and storage.
Growth rates of both can easily become unmanageable.
So what do we do? The answer is something called “edge computing.”
We already know that computing at the edge pushes most data processing out to the edge of the network, close to the source of the data… Read More
Will Edge Computing Replace the Cloud?
Excerpted from InformationWeek Report by Andrew Froehlich
 Although we’re only beginning to scratch the surface when it comes to the capabilities of cloud applications, many are already contemplating the successor to cloud architectures.
Although we’re only beginning to scratch the surface when it comes to the capabilities of cloud applications, many are already contemplating the successor to cloud architectures.
One such technology being discussed is a called edge computing.
This is a concept where we move computation that’s currently centralized inside the cloud back to the edge in a distributed manner.
Doing this provides key benefits that make it superior to traditional cloud architectures. But will it eventually replace the cloud in the enterprise? That’s our topic of discussion today.
The notion of edge computing is nothing new.
In fact, prior to cloud computing, we relied on our PC to provide the lion’s share of our computational needs as we ran applications locally.
But the cloud has changed all that… Read More
AetherWorks Joins OpenFog Consortium
Excerpted from AetherWorks Press Announcement
 AetherWorks, a software research and venture development firm based in New York, announces its membership in the OpenFog Consortium, a global organization driving industry and academic leadership in Fog Computing.
AetherWorks, a software research and venture development firm based in New York, announces its membership in the OpenFog Consortium, a global organization driving industry and academic leadership in Fog Computing.
As part of the Consortium, AetherWorks will share insights and expertise to help shape policies and requirements for standards around Fog.
“As our first OpenFog member in New York’s Silicon Alley, AetherWorks is making important contributions to the advancement of fog computing through their patented work in software-defined storage and scalable deployment architectures,” said Helder Antunes, Chairman of OpenFog and Senior Director of Corporate Strategic Innovation Group at Cisco.
“AetherWorks’ investments in fog-related startups provides a ‘spark’ to new technologies that will ultimately help solve challenges in fog computing. We welcome their contributions in OpenFog as we work to deliver an open and interoperable architecture to enable advanced IoT and 5G applications.”
The AetherWorks mission is to bring original, high quality technology to market through development and investment.
The firm, which was started by CEO and Founder Robert MacInnis, PhD, specializes in fault-tolerant distributed systems… Read More
Partners Bullish on Cisco’s New IoT Platform
Excerpted from CRN Report by Mark Haranas
 Partners are pumped about the new IoT Operations Platform unveiled by Cisco today; they believe Cisco’s platform can solve many of the issues customers have when deploying internet of things (IoT) solutions.
Partners are pumped about the new IoT Operations Platform unveiled by Cisco today; they believe Cisco’s platform can solve many of the issues customers have when deploying internet of things (IoT) solutions.
“Right now, I’m dealing with customers in the medical industry that have problems with the WannaCry ransomware attack because these connected medical devices are running very old operating systems – they have no updates, no ability to change the operating system, they can’t scale.”
“There’s a lot of struggles with IoT,” said Robert Keblusek, CTO of Sentinel Technologies, a Downers Grove, IL solution provider and Cisco Gold partner.
“There’s not really an easy platform or at scale. How do you manage and scale these things? How do you secure them at scale? These are all questions I think Cisco’s platform can answer.”
Cisco recently finished a survey of 1,845 business IoT leaders which found that 60 percent of IoT initiatives stalled at the proof-of-concept stage.
Of the 40 percent of the IoT projects that made it through to the pilot stage, only 26 percent were deemed successful… Read More
Why Is Cybersecurity So Hard?
Excerpted from Harvard Business Review Report by Michael Daniel
 After nearly 20 years of trying and billions of dollars in investment, why are organizations are still struggling with cybersecurity?
After nearly 20 years of trying and billions of dollars in investment, why are organizations are still struggling with cybersecurity?
In fact, the problem seems to be getting worse, not better.
Answering this question requires moving beyond a purely technical examination of cybersecurity.
It’s true that the technical challenges are very real; we don’t know how to write bug-free code, for example.
But if you look at the challenge more broadly, even if we resolved the technical issues, cybersecurity would remain a hard problem for three reasons:
It’s not just a technical problem.
The rules of cyberspace are different from the physical world’s.
Cybersecurity law, policy, and practice are not yet fully developed… Read More
Emerging Cybersecurity Threats to Address
Excerpted from Dark Reading Report by Kelly Sheridan
 As security pros scramble to defend against today’s threats as well as a new wave of attacks such as the WannaCry ransomware worm, emerging technologies and determined cybercriminals are poised to make cyber-defense even more complex.
As security pros scramble to defend against today’s threats as well as a new wave of attacks such as the WannaCry ransomware worm, emerging technologies and determined cybercriminals are poised to make cyber-defense even more complex.
Machine learning and the internet of things (IoT) aren’t new terms, but they’re new to the workplace.
As more businesses adopt advanced systems, they’ll find themselves vulnerable to a broader range of security threats.
The geopolitical landscape will also drive security risk as nation-states target foreign adversaries without fear of punishment.
At last week’s Interop ITX conference in Las Vegas, security experts discussed the implications of current and future threats.
Here are what they identified as the next big threats for enterprises:
IoT poses a tremendous security threat as users and devices become increasingly connected.
The problem is, it’s so new that many people haven’t begun to worry about it… Read More
Why Cyber Problems Are Getting Worse
Excerpted from Dark Reading Report by Grant Elliott
 In 2016, over $18 billion was spent on cybersecurity.
In 2016, over $18 billion was spent on cybersecurity.
It’s estimated that almost a trillion dollars more will be spent over the next five years.
Despite this, research shows that the problem is getting worse. Data breaches are at an all-time high, and the fierceness of these attacks has never been greater.
The reason is not that we’re unable to develop smarter, better technologies to secure our data but that we use these technologies in a scattered and siloed approach.
Also, we fail to leverage most companies’ greatest asset — their people.
Protecting data has always been a challenge, but there are a number of reasons why it’s becoming harder in the digital age.
Digitization of information: Unprecedented amounts of data are now online.
If you were to put all the data on the Internet on CD-ROMs and stack them on top of each other, they would bypass the moon… Read More
Redouble Your Cybersecurity Efforts
Excerpted from CBS News Report by Ray Martin
 The WannaCry ransomware attack that crippled computers worldwide could result in the largest financial and economic losses ever.
The WannaCry ransomware attack that crippled computers worldwide could result in the largest financial and economic losses ever.
And it’s a harsh reminder of how difficult it can be to keep your data and devices safe.
Given that it’s all but impossible to function without using the internet every day, any connected device and your data are always exposed to cyberthreats.
They’re everywhere, and you can do little to stop them.
But you can take steps to safeguard yourself. Think if them as pieces of your personal cybersecurity policy.
Of course, the first and most important thing is to create strong passwords for your devices and online accounts — and change them often.
And don’t think a six-digit password will do. That’s almost like having no password at all.
Hackers use password-generation tools, multiple dictionaries of English and foreign words, and linguistic patterns… Read More
Coming Events of Interest
Security of Things World — June 12th and 13th in Berlin, Germany. A world class event focused on the next information security revolution. Security concerns that preoccupy enterprise customers today and pragmatic solutions to threats.
Autonomous Systems World — June 14th and 15th in Berlin, Germany. An international knowledge exchange among top experts in the field, providing a unique glimpse into the fascinating world of autonomous robots, intelligent machines, and smart technologies.
INTRASECT — June 29th and 30th in Washington, DC. The first conference of its kind to engage key stakeholders in a comprehensive and engaging examination of existing and future regulatory policy governing the usage of commercial autonomous vehicles.
Industry of Things World Asia — July 3rd and 4th in Singapore. An international knowledge exchange platform bringing together more than 300 high-level executives who play an active role in the industrial internet of things (IoT).
Industry of Things World Europe — September 18th and 19th in Berlin, Germany. Join more than 1,000 high-level executives to rethink your technology and business strategy for scalable, secure, and efficient IoT.
IoT Solutions World Congress — October 3rd through 5th in Barcelona, Spain. This event has grown enormously in no time and is an excellent barometer and source of information, inspiration, collaboration and transformation.
