In This Issue
- Tech Outsourcing: US
- Ent Techs to Watch
- Cybersecurity Jobs
- Report from the CEO
- IoT Hacking Problem
- Retail Data Breaches
- Vulnerabilities of IoT
- Wells Fargo War Room
- COM Modules in IoT
- Step on Cyber Policy
- Fileless Cyberattacks
- IoT Edge Computing
- Cyber Scholarships
- Telefonica OoB Mobile
- AT&T Edge Computing
- Verizon #1 Mobile Net
- Coming DCIA Events
Hot Spot for Tech Outsourcing: The United States
Excerpted from NY Times Report by Steve Lohr
 For years, American companies have been saving money by “offshoring” jobs – hiring people in India and other distant cubicle farms.
For years, American companies have been saving money by “offshoring” jobs – hiring people in India and other distant cubicle farms.
Today, some of those jobs are being outsourced again – in the United States.
Nexient, a software outsourcing company, reflects the evolving geography of technology work.
It holds daily video meetings with one of its clients, Bill.com, where team members stand up and say into the camera what they accomplished yesterday for Bill.com and what they plan to do tomorrow.
The difference is, they are phoning in from Michigan, not Mumbai.
“It’s the first time we’ve been happy outsourcing,” said René Lacerte, the chief executive of Bill.com, a bill payment-and-collection service based in Palo Alto, CA.
Nexient is a domestic outsourcer, a flourishing niche in the tech world as some American companies pull back from the idea of hiring programmers a world away… Read More
Enterprise Technologies to Watch in 2017
Excerpted from ZDNet Report by Dion Hinchcliffe
 It was a rebuilding year in a sense, as emerging tech for the enterprise steadily proceeded but didn’t result in as many new targets to track as last year.
It was a rebuilding year in a sense, as emerging tech for the enterprise steadily proceeded but didn’t result in as many new targets to track as last year.
Yet it’s also abundantly clear the largest digital shifts by far are still ahead of us.
Here’s how 2017 is breaking down.
Enterprise IT in 2017 continues to be highly influenced by consumer technology, but for a change this year we can see a concerted push to craft business-ready versions of emerging tech in hot new categories.
This is particularly the case in areas like blockchain, digital twins, marketing integration solutions, and digital transformation target platforms.
Not too many items fell off this year’s enterprise tech to watch list either, as organizations continue to struggle to adopt the growing raft of relevant new technologies that have steadily arrived on the scene recently.
Consequently, the portfolio of emerging tech that must be managed continues to grow quickly… Read More
Booming Cybersecurity Job Market
Excerpted from Reuters Report by Joseph Menn and Jim Finkle
 The surge in far-flung and destructive cyberattacks is not good for national security, but for an increasing number of hackers and researchers, it is great for job security.
The surge in far-flung and destructive cyberattacks is not good for national security, but for an increasing number of hackers and researchers, it is great for job security.
The new reality is on display in Las Vegas, NV this week at the annual Black Hat and Def Con security conferences, which now have a booming side business in recruiting.
“Hosting big parties has enabled us to meet more talent in the community, helping fill key positions and also retain great people,” said Jen Ellis, a Vice President with cybersecurity firm Rapid7, which filled the hip Hakkasan nightclub on Wednesday at one of the week’s most popular parties.
Twenty or even 10 years ago, career options for technology tinkerers were mostly limited to security firms, handfuls of jobs inside mainstream companies, and in government agencies.
But as tech has taken over the world, the opportunities in the security field have exploded.
Whole industries that used to have little to do with technology now need protection, including automobiles, medical devices and the ever-expanding internet of things (IoT) – from thermostats and fish tanks to home security devices… Read More
Report from DCIA CEO Marty Lafferty

The expanding universe of connected devices and sensors known as the internet of things (IoT) is forecast to surpass 20 billion devices by 2020.
But the rapid growth and relative immaturity of this emerging sector have enabled a proliferation of insufficiently protected products, which in turn has created vulnerabilities in network security.
During the past year, susceptible IoT devices have been hacked to launch serious distributed denial-of-service (DDoS) attacks against websites, web-hosting servers, and internet infrastructure providers.
The DCIA commends US Senators Steve Daines (R-MT), Cory Gardner (R-CO), Mark Warner (D-VA), and Ron Wyden (D-OR) this week for introducing the Internet of Things Cybersecurity Improvement Act of 2017.
The bipartisan measure adroitly leverages the power of the federal procurement market, rather than imposing direct regulation, to require basic security protection in IoT products purchased by the US government.
Under terms of the bill, such devices will have to be patchable, rely on industry standard protocols, not use hard-coded or default passwords, and not contain known security vulnerabilities.
The Office of Management and Budget (OMB) will be directed to develop alternative network-level security requirements for devices with limited data processing and software functionality.
The measure also promotes securing the online ecosystem through adoption of coordinated vulnerability disclosure policies by federal contractors.
It will exempt cybersecurity researchers engaging in good-faith research and testing of networked systems integrity from liability under the Computer Fraud and Abuse Act (CFAA) and the Digital Millennium Copyright Act (DMCA).
And it will require executive agencies to inventory all IoT devices used by them.
Requirements to secure government firmware is a step towards broader marketplace adoption of IoT security solutions including in the area of greatest promise, security in the network, as well as connected devices.
Please click here for the text of the bill and here for a summary. Share wisely, and take care.
The Internet of Things Has a Hacking Problem
Excerpted from NHPR Report by Ben Henry
 A New Hampshire software developer is working on a way to protect household devices that are connected to the internet, the latest in a broader, nationwide push to keep the devices in our homes safe from hackers.
A New Hampshire software developer is working on a way to protect household devices that are connected to the internet, the latest in a broader, nationwide push to keep the devices in our homes safe from hackers.
David Brooks, who writes the Granite Geek column at the Concord Monitor, has been keeping a close eye on this topic – and he’s pretty worried.
Brooks spoke with NHPR’s Peter Biello:
Q. This is all about the Internet of Things (IoT), so bring us up to speed. What is that?
A. The IoT is all the interconnected, internet-connected, devices that are being sold now.
Things like your router, but also webcams, thermostats – so you can set your thermostat on your smartphone while you’re at work – baby monitors, security cameras, door locks, refrigerators, toasters.
There’s a ton of stuff out there.
Q. And if these devices are hacked, what threat do they pose to the people who own them… Read More
Retail Data Breaches Down, Concerns Up
Excerpted from IB Times Report by AJ Dellinger
 Half of retailers in the United States have experienced a data breach at some point and a vast majority believe they are vulnerable to hacking threats, according to a new survey.
Half of retailers in the United States have experienced a data breach at some point and a vast majority believe they are vulnerable to hacking threats, according to a new survey.
The data showing the fears of retail comes as part of the 2017 Thales Data Threat Report, Retail Edition conducted by 451 Research.
The survey included more than 1,100 senior security executives at global retail firms.
The fear that many retailers have about potential threats to sensitive data – 88 percent consider themselves to be vulnerable – appears not to have much effect in slowing reliance on that valuable information.
Ninety-five percent of US retailers surveyed said they would use sensitive data this year.
Consumers may take issue with this given the lack of confidence held by the retailers themselves in their ability to secure that data.
More than half of respondents said they believe sensitive data is being used without proper security in place… Read More
The IoT and Cybersecurity Vulnerabilities
Excerpted from TechTarget Report by Brian Berger
 The internet of things (IoT) is defined as the interconnectivity or networking of devices, sensors, and electronics to communicate through software.
The internet of things (IoT) is defined as the interconnectivity or networking of devices, sensors, and electronics to communicate through software.
With IoT and the typical computing infrastructure that is very familiar, the change in data, access, connectivity and monitoring requires a cybersecurity approach.
We tend to add technology to the existing fabric of our lives without considering how the bad guys will attack.
We are seeing IoT in our homes, automobiles, food safety, medical devices, critical infrastructure, and manufacturing – just to name a few.
Let’s talk about our homes and us as consumers of IoT first.
We have access to some cool and innovative technologies at home.
A favorite is Amazon’s Alexa digital assistant.
Alexa can turn on lights, change the temperature of a thermostat, change watering days and times on your irrigation controller… Read More
Inside Wells Fargo’s Cybersecurity War Room
Excerpted from American Banker Report by Penny Crossman
 To keep their cyberteams fit and ready to defend against a cyberattack at any time, large banks have begun using “cyber ranges” – virtual environments where real cyberattacks are launched on replicas of their actual IT systems.
To keep their cyberteams fit and ready to defend against a cyberattack at any time, large banks have begun using “cyber ranges” – virtual environments where real cyberattacks are launched on replicas of their actual IT systems.
“Special forces in the military train with live bullets shooting around them, so when and if they’re in the time of battle, they’re not ducking and covering because of these loud banging noises,” said Rich Baich, Wells Fargo’s Chief Information Security Officer.
“A cyber range is the same thing – your machine is actually being attacked. It’s no longer theoretical.”
Baich was a member of the US Navy for more than 20 years and worked as a Naval Information Warfare officer for the National Security Agency.
He is also Chairman of the Financial Services Sector Coordinating Council, a group set up to help the financial services sector prepare for and recover from cyberattacks.
He said he believes cyber ranges are what’s next for banks when it comes to dealing with asymmetric cyberattacks.
In some ways, cyber ranges are an extension of banks recruiting people like Baich… Read More
COM Modules in the Internet of Things
Excerpted from New Electronics Report by Peter Eckelmann and Tim Jensen
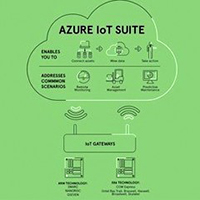 The internet of things (IoT), cloud-based solutions, and big data represent major challenges for future system designs.
The internet of things (IoT), cloud-based solutions, and big data represent major challenges for future system designs.
The Microsoft Azure cloud is providing a framework to encapsulate these paradigms in manageable chunks allowing them to be mastered in a straight-forward way.
MSC Technologies, producer of embedded hardware, has now certified its most popular COM products for the Azure Cloud, and is offering the software suite ‘Easy IoT’ which is a ready-to-run application for Azure.
The future begins now, and if the current project is not yet an IoT project, then the next one is certainly going to be.
Billions of interconnected node elements are forming the IoT, and concentrators near the edge of the Cloud are performing ‘Fog Computing,’ effectively thinning down the steady stream of IoT data to a trickle which can be digested more easily by the cloud’s servers.
Despite this the amount of data arriving in the cloud is unbelievably large, and once stored it can be searched, digested, extracted and acted upon.
Among the cloud service providers, Microsoft excels with leading growth rates of the number of users and of objects stored… Read More
Modest Step Forward on Cyber Policy
Excerpted from Washington Examiner Report by Charlie Mitchell
 Cybersecurity policy issues are inching forward on Capitol Hill as Congress lumbers through the dog days of summer.
Cybersecurity policy issues are inching forward on Capitol Hill as Congress lumbers through the dog days of summer.
Bills on issues like data security in the communications sector, encouraging or mandating the use of federal cyber standards across government and industries, and the cybersecurity of inter-connected and self-driving cars are languishing with little prospect of action in the near-term.
But House passage on July 20 of a first-ever reauthorization of the Department of Homeland Security – which plays a key role in securing federal computer networks and protecting critical industries – was a landmark achievement for multiple congressional committees, and a particular victory for Homeland Security Chairman Michael McCaul, R-TX.
McCaul helped orchestrate a deal among eight House committees that claim some share of DHS jurisdiction, which allowed the sprawling measure to advance following years of stalemate among the panels.
McCaul and Homeland Security ranking member Bennie Thompson, D-MS, each put out glowing statements about both the content of the bill and the bipartisan process that produced it.
“Today’s reauthorization of the Department is a major bipartisan accomplishment,” McCaul said… Read More
Guarding Against Fileless Cyberattacks
Excerpted from GovTech Report by Theo Douglas
 A cybercrime trend with alarming implications for public agencies remains popular as the year wears on; called “living off the land,” the technique is drawing increased interest from attackers looking to further reduce their profiles, a new white paper has found.
A cybercrime trend with alarming implications for public agencies remains popular as the year wears on; called “living off the land,” the technique is drawing increased interest from attackers looking to further reduce their profiles, a new white paper has found.
“Living off the land” techniques use tools already installed on users’ systems to access sensitive data – and are a “clear trend in targeted cyberattacks,” according to Living Off the Land and Fileless Attack Techniques, a special Internet Security Threat Report released July 12 by cybersecurity company Symantec.
Accompanying that trend, authors wrote, is a “growing interest” in four types of “fileless infection techniques:”
Memory-only threats run in a computer’s memory, with nothing written onto a file or disk; machines disinfect themselves when they reboot or restart, leaving no trace.
Fileless persistence ensures attacks begin anew even after a restart and disinfect, with the most popular strategy embedding malicious script data inside a computer’s registry.
Dual-use tools are clean tools used legitimately by a computer’s owner, but can be co-opted by hackers… Read More
Pairing Edge Computing With IoT
Excerpted from CRN Report by Lindsey O’Donnell
 As more customers adopt internet of things (IoT) products, solution providers say edge computing applications – where data is processed and analyzed at the end device level – are becoming more prevalent.
As more customers adopt internet of things (IoT) products, solution providers say edge computing applications – where data is processed and analyzed at the end device level – are becoming more prevalent.
“More IoT devices and sensors need to be ubiquitous to their environment,” said Aaron Kamphuis, IoT Practice Manager at Open Systems Technologies, a Grand Rapids, MI based solutions provider.
“We’re bundling in edge capabilities as part of our overall IoT solution so we can come in and figure out what data needs to be captured and how to capture it.”
In edge computing, sensors and other connected devices collect and analyze the data locally, alleviating the dependence on cloud or internet connectivity in specific situations where information needs to be processed quickly, reliably and securely.
Customers are recognizing the business benefits of bringing that intelligence closer to the end customer, and they’re spending accordingly.
Market research firm IDC predicts that by 2019 at least 40 percent of IoT-created data will be managed at the edge of the network… Read More
Senate Bill for Federal Cyber Scholarships
Excerpted from The Hill Report by Morgan Chalfant
 A Senate committee on Wednesday advanced legislation that would update and expand an existing federal cybersecurity scholarship program for students pursuing degrees in cyber fields.
A Senate committee on Wednesday advanced legislation that would update and expand an existing federal cybersecurity scholarship program for students pursuing degrees in cyber fields.
The bipartisan bill, sponsored by Senators Roger Wicker (R-MS) and Tim Kaine (D-VA), would expand a cyber scholarship-for-service program run by the National Science Foundation in an effort to bolster the nation’s cybersecurity workforce.
The Senate Commerce, Science and Transportation Committee approved a final version of the legislation amended by Wicker in a voice vote Wednesday morning.
The National Science Foundation’s Cyber Corps: Scholarships for Service program offers ROTC-style scholarships to students pursuing degrees in cybersecurity fields.
The bill approved Wednesday would amend 2014 law to expand the program to offer scholarships to part-time students.
It would also prioritize the employment placement of 80 percent of the scholarship awardees in an executive agency… Read More
Telefonica Out-of-the-Box Mobile Connectivity
Excerpted from Globe Newswire Report
 Gemalto, the world leader in digital security, is supplying Telefonica Group, one of the largest telecommunications companies in the world, with an On-Demand Connectivity cloud service that enables out-of-the-box mobile connectivity for consumer products such as connected PCs and wearables.
Gemalto, the world leader in digital security, is supplying Telefonica Group, one of the largest telecommunications companies in the world, with an On-Demand Connectivity cloud service that enables out-of-the-box mobile connectivity for consumer products such as connected PCs and wearables.
As a result, Telefonica can offer its customers seamless over-the-air management of a mobile subscription for any device fitted with an embedded SIM (eSIM).
End users will be able to directly purchase, modify or update their existing subscription plan, without the need to fit or change a SIM.
The new Gemalto cloud service is available to all Telefonica Group mobile operators, extending across 17 different countries.
Fully compliant with the latest GSMA Remote SIM Provisioning specifications, Gemalto’s solution aims at extending convenient mobile connectivity to millions of consumer devices and bringing new services to users – whether for health monitoring, asset-tracking, tablet and PC connectivity on the move, or fitness activities, without the need to carry a smartphone… Read More
Edge Computing: AT&T’s Next Big Play?
Excerpted from Light Reading Report by Carol Wilson
 Network operators are “uniquely positioned” to convert their central offices and cell towers into distributed computing facilities to support a wide range of third-party applications including self-driving cars, industrial robotics, and augmented/virtual reality, a top AT&T executive is saying.
Network operators are “uniquely positioned” to convert their central offices and cell towers into distributed computing facilities to support a wide range of third-party applications including self-driving cars, industrial robotics, and augmented/virtual reality, a top AT&T executive is saying.
And this could be the move that gets telecom operators back into the cloud computing game big time.
Andre Fuetsch, President of AT&T Labs and Chief Technology Officer, isn’t saying every one of AT&T ‘s 65,000 cell towers and roughly 5000 COs will become edge computing sites.
But that footprint, unique to network operators, represents an advantage in creating distributed cloud computing for high-intensity applications like AR/VR and self-driving cars, that will require much more compute power than devices will be able to deliver.
And as Fuetsch also notes, AT&T’s transition to 5G includes a new radio access network architecture “where we continue to disaggregate and open up interfaces – I think there is more and more opportunity to basically take advantage of multi-use resources to do many other things other than just provide a network service… Read More
Mobile Verizon Customers Have #1 Rated Network
Excerpted from PR Newswire Report
 According to the latest RootScore Report, the nation’s most rigorous, independent scientific study, Verizon won the overall performance award in Mobile.
According to the latest RootScore Report, the nation’s most rigorous, independent scientific study, Verizon won the overall performance award in Mobile.
Verizon also was ranked first in data and call performance and shared first in network reliability, text and speed.
Verizon invests heavily in its network to ensure its customers have the best possible experience when they’re looking to call, post, stream and text.
Last year, more than $11 billion was invested in the wireless network nationwide, including in Mobile.
This investment ensures Verizon customers have the best possible experience when they’re looking to call, post, stream and text. Investments include small cells hidden on top of traffic signals and utility poles, boosting coverage and capacity in highly populated areas, as well as advanced technologies to boost capacity and efficiency.
These sustained improvements helped the wireless carrier come out on top in the latest rankings by RootMetrics.
Verizon Communications headquartered in New York has a diverse workforce of 161,000 and generated $126 billion in 2016 revenues… Read More
Coming Events of Interest
Industry of Things World Europe — September 18th and 19th in Berlin, Germany. Join more than 1,000 high-level executives to rethink your technology and business strategy for scalable, secure, and efficient IoT.
IoT Solutions World Congress — October 3rd through 5th in Barcelona, Spain. This event has grown enormously in no time and is an excellent barometer and source of information, inspiration, collaboration and transformation.
2017 Storage Visions Conference — October 16th in Milpitas, CA. “New Visions for Digital Storage” will bring together the vendors, end-users, researchers, and visionaries who will meet the growing demand for digital storage for all aspects of unstructured and lightly structured data.
INTRASECT— November 1st and 2nd in Washington, DC. The first conference of its kind to engage key stakeholders in a comprehensive and engaging examination of existing and future regulatory policy governing the usage of commercial autonomous vehicles.
Government Video Expo & National Drone Show — November 28th-30th in Washington, DC. The 22nd annual GVE will feature a full exhibit floor with numerous training options, free seminars, keynotes, networking opportunities, and five new educational pavilions.
Delivery of Things World 2018 — April 23rd and 24th in Berlin, Germany. Meet the most influential DevOps practitioners and experts and discuss what DevOps means for your business.
