In This Issue
- Staying Connected
- Huawei Global Cloud
- Sprint NFV & 5G Plans
- Report from the CEO
- How to Beat Hackers
- Getting on Same Page
- Measure Effectiveness
- Not Just Tech Problem
- Skills Shortage Study
- Cybersecurity Help
- Employees Defense
- Unlock Edge Promise
- Coming Era of Fog
- Are Developers Ready
- Convergence Value
- Hyperscale Disrupts
- Coming DCIA Events
Staying Connected During Irma
Excerpted from Cellular News Report
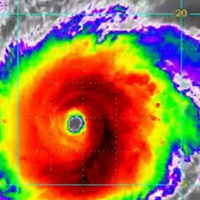 As Hurricane Irma maintains its strength, now is an important time to ensure you and your loved ones are prepared to stay connected if and when the superstorm affects you.
As Hurricane Irma maintains its strength, now is an important time to ensure you and your loved ones are prepared to stay connected if and when the superstorm affects you.
Verizon is there with you when you need us.
The reliability of your wireless network is never more important than when a crisis strikes.
That’s when a simple call or text message can keep you connected and be the most important communication you make in times of an emergency.
“We prepare year-round to keep you connected when you need it most,” said Sergei Mislevy, Executive Director for Network Assurance at Verizon Wireless.
“Our network is designed with end-to-end reliability in mind – for individuals, businesses, emergency responders and everyone who needs connectivity when the unexpected happens.”
Here are a few things you can do to prepare when severe weather threatens… Read More
Huawei Lays-Out Plans for Global Cloud Alliance
Excerpted from ITProPortal Report by Michael Moore
 Huawei has laid-out its bid to kick-start the next generation of cloud computing.
Huawei has laid-out its bid to kick-start the next generation of cloud computing.
At the Huawei Connect 2017 event in Shanghai today, rotating CEO Guo Ping pledged that the company is committed to building “one of the world’s five clouds” to benefit enterprises around the world.
Harking back to the 1948 prediction of IBM founder Thomas Watson that there would only ever be a worldwide market for five computers, Ping stated that Huawei is now looking for a similar ideal for cloud platforms in a bid to push forward collaboration and innovation.
“Society is experiencing a tangible Matthew effect in digital technology development.”
“Because of this, as well as economies of scale in investment, clouds around the world will begin to converge – becoming more and more centralized. In the future, we predict there will be five major clouds in the world.”
Similar to the existing airline collaborations such as OneWorld or Star Alliance, Huawei is hoping to create global alliances of cloud computing, working with partners around the world.
“We hope that in the future customers will be able to ask for Huawei cloud and be able to connect to the entire world,” Ping said. Read More
Sprint NFV Plans Essential for 5G Deployment
Excerpted from SDXCentral Report by Dan Meyer
 Sprint added details to its network virtualization plans ahead of the carrier’s push toward 5G, including new vendors and timelines.
Sprint added details to its network virtualization plans ahead of the carrier’s push toward 5G, including new vendors and timelines.
Gunther Ottendorfer, Chief Operating Officer of Technology at Sprint, in a blog post said the carrier has spent the past couple of years deploying its OpenStack cloud-based network functions virtualization (NFV) platform.
He explained the deployment has been “an essential building block” as the carrier builds toward its 5G network.
Ottendorfer said the carrier is set to expand the more than 30 data centers it has deployed in support of its common infrastructure goal.
The expansion will be part of a NFV-focused “cap and grow” model that will see the carrier cap investment on legacy core network hardware and grow investment in virtualized platforms.
That investment will be based on open-source software using standards-based hardware.
Ottendorfer said the focus builds on its C3PO efforts, and will be on supporting Sprint’s plans for 5G… Read More
Report from DCIA CEO Marty Lafferty

This week, Equifax revealed a major compromise of sensitive consumer data affecting more than half of US adults, exceeding the size of breaches recently experienced at Home Depot, Sony, Target, and the Office of Personnel Management (OPM).
Although not as large as last year’s Yahoo incident, Equifax’s breach of 143 million accounts is more serious: exposing names, birth dates, Social Security and driver’s license numbers.
Personally identifiable information — not only for Equifax customers, but also for consumers applying to obtain loans, mortgages, and credit cards — was subject to data theft through a website vulnerability from Mid-May through the end of July.
Once Equifax discovered the unauthorized access, the company engaged a cybersecurity firm to conduct a forensic review after which it began notifications and made its announcement.
Consumers can check with Equifax to find out if their data has been impacted, but are required to enter their last names and final six digits of their Social Security numbers to do so.
Equifax offers an optional enrollment date to those affected for a complimentary annual subscription to TrustedID Premier, an Equifax-owned monitoring service that screens Equifax, Experian, and TransUnion credit reports, provides identity-theft insurance, and internet scanning for subscribers’ Social Security numbers.
The company has also set-up a dedicated call-center, open daily from 7:00 AM to 1:00 AM ET, at 866-447-7559.
The Equifax incident underscores the need for improved cybersecurity practices industrywide as connected services grow in popularity and increasing amounts of data are collected and stored.
Software development needs to treat security as a primary design consideration and firewalls need to be applied to network data pathways so that sensitive data will be protected. Share wisely, and take care.
How to Beat the Hackers
Excerpted from Khaleej Times Report by Sachin Bhardwaj
 Recent months have seen several outrageous cyberattacks dramatically compromise the functions and data of several businesses, governments, and organizations across the globe.
Recent months have seen several outrageous cyberattacks dramatically compromise the functions and data of several businesses, governments, and organizations across the globe.
While hackers have been a threat for a considerable amount of time, the extent and scope of their attacks were often limited in the past — high profile cyberattacks tended to be the ones that compromised or breached heavily defended and access restricted networks.
The last two years in particular have, by contrast, witnessed attacks that are remarkable for the sheer number of networks they have compromised and the widespread geographies they have affected.
The skills and services of managed IT security service providers are being tested by the upswing in instances of ransomware, data theft and several other manifestations of cybercrime.
These threats can no longer be considered fringe or unlikely concerns for the average enterprise.
As IoT applications and mobile connectivity become the norm rather than exception and their advantages too favorable to ignore, the ability of hackers to compromise networks through distributed denial of services (DDoS) increases… Read More
Getting Cybersecurity Experts on Same Page
Excerpted from TechRepublic Report by Leah Brown
 IT professionals and policy makers often don’t speak the same language when it comes to cybersecurity. Gregory Michaelidis, TechRepublic Contributor and Cybersecurity Fellow at New America, advises how IT professionals and policy makers can work together to “solve the cybersecurity puzzle.”
IT professionals and policy makers often don’t speak the same language when it comes to cybersecurity. Gregory Michaelidis, TechRepublic Contributor and Cybersecurity Fellow at New America, advises how IT professionals and policy makers can work together to “solve the cybersecurity puzzle.”
Michaelidis compares this disconnect to one between a science and a literature professor at the same university.
Though they teach at the same place, the way they teach and the way they measure success differs.
Generally, tech professionals are known to move quickly, and like disruption and innovation, whereas policy makers tend to move at a slower pace and speak in more legalistic terms.
Michaelidis suggests that people in the cybersecurity community to attend a Hill Day in Washington, or talk with state and local representatives.
“It can really give you a sense of what the staff who deals with us are wrestling with on a given day,” Michaelidis said.
Conversely, he suggests for policy makers to get out of DC and meet with officials in state and local government and law enforcement… Read More
How to Measure Cybersecurity Effectiveness
Excerpted from CIO Report by Thor Olasvsrud
 Are you measuring the value and effectiveness of your cybersecurity efforts?
Are you measuring the value and effectiveness of your cybersecurity efforts?
Most companies around the world are failing to do so, according to a recent security measurement index benchmark survey.
Without establishing the proper metrics, you’re flying blind.
And even when organizations’ information security function does generate and deliver data about the business’ security, it typically never gets read.
“Many companies, while they’re making some effort in cybersecurity, they’re not looking at the effectiveness in terms of how it helps the business,” says Joseph Carson, Chief Security Scientist at Thycotic, which created its Security Measurement Index (SMI) based on standards for security specified in ISO 27001 and best practices from industry experts and associations.
“Many companies are not evaluating their risk versus their impact.”
“They’re not looking at this from a business impact evaluation or perspective… Read More
Cybersecurity Not Just a Tech Problem
Excerpted from Business Insider Report by Kate Prince
 Not too long ago, cybersecurity was an afterthought, a software installation that was often left to expire, or run in the background only to pop-up at inconvenient times.
Not too long ago, cybersecurity was an afterthought, a software installation that was often left to expire, or run in the background only to pop-up at inconvenient times.
But recent high profile attacks — and the very real world consequences that come with them — have demanded the attention of everyone from large enterprise CEOs to small business owners, and the cybersecurity industry has capitalized on the opportunity.
In Australia, 80% of CEOs rate cybersecurity as a top investment priority and place it amongst the top five risk areas for their business, according to the latest KPMG CEO Outlook survey.
However, ResponSight Founder and CEO Jeff Paine believes investment shouldn’t be the only way companies think about combating cybersecurity threats, especially when criminals now rely more on manipulating human behavior than breaking through security systems.
ResponSight’s technology uses behavioral analytics to detect changes in user behavior that could signal the system is compromised: If behavior suddenly becomes anomalous it could indicate malware or an attacker… Read More
Study Reveals Cybersecurity Skills Shortage
Excerpted from Campus Technology Report by Rhea Kelly
 The skills required for information security have changed in the last few years, according to IT security professionals in a recent survey.
The skills required for information security have changed in the last few years, according to IT security professionals in a recent survey.
Security and compliance company Tripwire conducted the study with assistance from Dimensional Research, which revealed 93 percent of security pros are concerned about the cybersecurity skills gap, and 72 percent said it’s more difficult to hire skilled security staff compared to two years ago.
The study findings are based on survey responses from 315 IT security professionals at US-based companies with more than 100 employees.
Among the findings: Just 20 percent of respondents said their company has hired people without specific security expertise for security roles, and 17 percent plan to do so in the next two years.
50 percent plan to invest in training existing security staff.
91 percent plan to supplement their security team by outsourcing for skills.
88 percent said managed services would help solve the skills gap problem… Read More
Cybersecurity Help Wanted
Excerpted from CSO Online Report by Steve Morgan
 Frederic Vezon has Aspergers. He’s President at ASPertise, an application development, big data, and cybersecurity services company that has offices in Paris and Montreal.
Frederic Vezon has Aspergers. He’s President at ASPertise, an application development, big data, and cybersecurity services company that has offices in Paris and Montreal.
The ASP in ASPertise stands for “Asperger Syndrome” — which the company explains as being manifested by significant difficulties in social interaction, associated with restricted interests and repetitive behavior.
A unique value proposition from ASPertise is their team of cybersecurity experts — with Aspergers.
Vezon’s firm expands on the syndrome, stating that Asperger people have difficulty interpreting and adapting to other’s nonverbal behaviors (eye contact, facial expressions, body postures, etc.), love repetition and routines, and lack social and emotional reciprocity.
These difficulties are often accompanied by other features, such as hypersensitivity to noise or specific kinds of foods, monotonic speech delivery, and resistance to change.
ASPertise says the syndrome is often called the “invisible disability” because people with Aspergers are frequently of normal or above average intelligence and exhibit great intellectual curiosity… Read More
Employees: Best Defense against Cyberattacks
Excerpted from Baseline Magazine Report by Nick Wilding
 Jim Baines, the CEO and Founder of Baines Packaging, a respected midsize US packaging firm, recently wrote an open letter to his peers in other organizations following a catastrophic cyberattack.
Jim Baines, the CEO and Founder of Baines Packaging, a respected midsize US packaging firm, recently wrote an open letter to his peers in other organizations following a catastrophic cyberattack.
It’s an emotional plea: “It never occurred to me that I, as the CEO, might be a target. We’re immune, aren’t we?”
“That’s what I thought. Now my company, which I built from nothing over nearly 30 years, into which I poured everything I had to ensure its success, is losing clients, losing money, and, most importantly, losing credibility.
“My reputation has been badly damaged, along with my relationships with my customers, my peers and my friends.”
“So, if you’re a business leader, you need to know that you’re also a target.”
“Everyone on your board is a target. No one is immune and everyone is vulnerable, no matter how powerful or successful they may be.”
Baines clicked on an innocent-looking email, and the disaster unfolded.
It takes only one person who’s not security-aware or vigilant to enable a cyberattack to succeed… Read More
Unlocking Promise of Edge Cloud Computing
Excerpted from ITPROPortal Report by Siavash Alamouti
 Internet of things (IoT) has started to impact every aspect of our daily lives.
Internet of things (IoT) has started to impact every aspect of our daily lives.
Our appliances, cars, gadgets, communication devices, tools, and even some of our clothing have become nodes on the internet.
By 2020, as many as 50 billion devices will be connected so there will be skyrocketing growth of traffic generated by devices at the edge of the network posing a monumental challenge to our networks and central cloud computing.
Thankfully, we can take advantage of the ever-increasing computing capabilities of edge devices to turn them into cloud servers and extend central-cloud capabilities to the edge.
Edge cloud to central cloud is like WiFi to Cellular Communication. Just as WiFi carries most of the global wireless traffic today, edge devices will soon manage most of the cloud computing burden.
According to Gartner’s 2017 Hype Cycle for Emerging Technologies, edge cloud computing is on the brink of becoming an “innovation trigger.”
Microchips and sensors continue to become embedded in everyday objects, making edge cloud computing an immense opportunity… Read More
Coming Era of Fog Computing
Excerpted from Embedded Computing Design Report by Lynne Canavan
 The IT pendulum is again in motion, as we shift away from cloud towards a more distributed computing model.
The IT pendulum is again in motion, as we shift away from cloud towards a more distributed computing model.
Gartner says that by 2022, 75 percent of enterprise-generated data will be created and processed outside the data center or cloud.
This movement is driven by massive amounts of data from IoT and other digital applications-now measured in petabytes-that dwarf all previous networking demands.
Given the requirements for real-time communication flows throughout and beyond IoT, 5G and AI apps, it’s clear that cloud-only approaches can no longer keep up with the necessary volume, latency, mobility, reliability, security, privacy, and network bandwidth challenges.
Fog computing and networking address these challenges by extending the traditional cloud-based computing model where architecture implementations can reside in multiple layers of a network’s topology.
Fog is a system-level horizontal architecture that distributes resources and services of computing, storage, control, and networking closer to users, enabling faster processing time and lower network costs… Read More
Are Developers Ready for Edge Cloud?
Excerpted from Jaxenter Report by Siavash Alamouti and Fay Arjomandi
 The world of connected devices has enormous potential but it is clear that we need distributed edge cloud to fulfill this promise.
The world of connected devices has enormous potential but it is clear that we need distributed edge cloud to fulfill this promise.
Developers can leverage edge cloud to write their applications and accelerate the growth of the internet of things (IoT) but are they really ready for the new era of edge cloud computing?
Today, at the dawn of the IoT, our devices constantly connect and communicate mostly through a central cloud and have transformed many aspects of our daily lives.
IoT is undoubtedly a transformative technology and will impact most industries, and the way businesses and consumers behave.
Some projections state that there will be more than 50 billion connected devices and as many as 22 billion IoT devices operating by 2021.
The big question is whether existing networks and the central cloud can cope with all the additional traffic.
I believe the answer is “no;” there is not enough bandwidth to cope with the explosion of the data at the edge of the network today… Read More
Convergence Adds Value in IoT
Excerpted from IT Online Report by Kathy Gibson
 Huawei is driving convergence in the internet of things (IoT) space and yesterday launched its “Platform + Connection + Ecosystem” enterprise IoT solution.
Huawei is driving convergence in the internet of things (IoT) space and yesterday launched its “Platform + Connection + Ecosystem” enterprise IoT solution.
Based on the OceanConnect IoT platform and wireless convergence access capacity, the solution also includes edge computing IoT (EC-IoT), IoT security, and other features that add to agility and security.
IoT is critical for enterprise looking to digital transformation, says Jiang Wangcheng, President: IoT Solution in the Huawei Technologies enterprise business group.
“It will help to drive increased revenue, improved competitiveness, improved O&M operations, and more.”
Huawei aims to deliver all the elements that are required to build IoT solutions, he adds, as a platform builder, a connectivity enabler and an ecosystem promoter.
The company offers products that address every part of the system: from the chip and operating system within devices for the ecosystem part of the story.
It has a full set of networking products including chips, modules, gateways, and base station that run on any network.. Read More
Hyperscale Will Disrupt Data Center Market
Excerpted from Data Center Frontier Report by Bill Kleyman
 There are more users, complex applications and data points accessing your infrastructure.
There are more users, complex applications and data points accessing your infrastructure.
Now, new kinds of demands are requiring modern organizations to rethink their data center environment, delivery model, and how cloud architecture can be utilized even more.
A recent Deloitte Technology report projects that by the end of 2018, spending on IT-as-a-Service for data centers, software and services will be $547 billion.
Deloitte Global predicts that procurement of IT technologies will accelerate in the next 2.5 years from $361 billion to $547 billion.
At this pace, IT-as-a-Service will represent more than half of IT spending by the 2021/2022 timeframe.
Furthermore, cloud computing continues to grow at rates much higher than IT spending generally.
Growth in cloud services is being driven by new IT computing scenarios being deployed using cloud models, as well as the migration of traditional IT services to cloud service and data center provider alternatives… Read More
Coming Events of Interest
Industry of Things World Europe — September 18th and 19th in Berlin, Germany. Join more than 1,000 high-level executives to rethink your technology and business strategy for scalable, secure, and efficient IoT.
IoT Solutions World Congress — October 3rd through 5th in Barcelona, Spain. This event has grown enormously in no time and is an excellent barometer and source of information, inspiration, collaboration and transformation.
2017 Storage Visions Conference — October 16th in Milpitas, CA. “New Visions for Digital Storage” will bring together the vendors, end-users, researchers, and visionaries who will meet the growing demand for digital storage for all aspects of unstructured and lightly structured data.
INTRASECT— November 1st and 2nd in Washington, DC. The first conference of its kind to engage key stakeholders in a comprehensive and engaging examination of existing and future regulatory policy governing the usage of commercial autonomous vehicles.
Industrial Internet of Things (IoT) Europe — November 7th and 8th in Munich, Germany. IoT Europe will bring together forward-thinking companies from the manufacturing, energy, and transportation sectors to pave the way for the Industrial IoT revolution.
Government Video Expo & National Drone Show — November 28th-30th in Washington, DC. The 22nd annual GVE will feature a full exhibit floor with numerous training options, free seminars, keynotes, networking opportunities, and five new educational pavilions.
Delivery of Things World 2018 — April 23rd and 24th in Berlin, Germany. Meet the most influential DevOps practitioners and experts and discuss what DevOps means for your business.
