In This Issue
- 2017 Cloud Priorities
- Cloud Comp Grows Up
- Joins the Mainstream
- Report from the CEO
- What Fog Means: IoT
- Edge Not Yet Priority
- Rebalancing Equation
- Smart City Challenge
- Politics of Resistance
- Checkpoint Security
- Security Predictions
- Hacked Yahoo Data
- IBM 25,000 US Jobs
- Raytheon & Pentagon
- Adobe Flash Player
- Pragmatic Hybrid Cld
- Coming DCIA Events
Cloud Priorities for 2017
Excerpted from Cloud Computing Intelligence Report by Monica Brink
 The growth of cloud computing has continued unabated in 2016 across technologies, industries and use cases.
The growth of cloud computing has continued unabated in 2016 across technologies, industries and use cases.
Given the level of growth, you would be forgiven for thinking that it has already established a winning position in the technology industry.
In reality, cloud spending is some distance away from reaching its peak compared to investment in traditional approaches to IT.
For IT leaders however, cloud will continue to dominate strategic technology decision making in 2017 but some clear priorities are coming into play for the UK cloud market.
Here are five key cloud priorities that I predict will come to the fore in 2017:
1. Security and Compliance
As we head into the New Year, we will no doubt see a continued focus on ensuring workloads that reside in the cloud are secure. With threats including ransomware and other cybersecurity attacks becoming increasingly sophisticated… Read More
Cloud Computing Grows Up
Excerpted from Markets Media Report by Brad Bailey

Cloud computing has become an overnight sensation in capital markets that has been a decade in the making, according to the authors of a white paper published by Celent.
“I think its title, ‘The Coming of Age in the Capital Markets,’ says it all,” said Brad Bailey, research director securities & investments at Celent and co-author of the paper.
The capital market’s investment in cloud computing has grown to 7% of the IT budget from 1% over the last five years, according to the authors.
Whether if it’s cost pressures, the advancement of cloud-enabling technology, or the realization of the ease in which you can get things done, Bailey foresees adoption only ramping up.
After polling a segment of the capital markets regarding their adoption of cloud computing, the authors found that 5% of the respondents are using private clouds while a smaller percentage are investing in public and hybrid cloud models, 0.5% and 2.5% respectively.
By 2021, the authors estimated that the use of a hybrid cloud computing model will rise to 17%… Read More
Cloud Evolves and Joins the Mainstream
Excerpted from Baseline Magazine Report by Samuel Greengard
 Clouds have rolled into the mainstream of business, and they now touch every aspect of IT and business. They’ve become an essential part of architecture.
Clouds have rolled into the mainstream of business, and they now touch every aspect of IT and business. They’ve become an essential part of architecture.
Only a few years ago, most business and IT leaders viewed the cloud with some trepidation.
Although many had begun to use cloud services and solutions, they still had questions about everything from viability to security.
But that was then, and this is now.
Clouds have rolled into the mainstream of business, and they now touch every aspect of IT and business.
The Cisco Systems sixth annual Global Cloud Index offers deep insights into how this space is changing and evolving-and how clouds are impacting the enterprise.
The report spotted several key trends and findings, including a rapidly growing use of the cloud and skyrocketing cloud traffic, a focus on public clouds, the growing use of video and social streams in the cloud… Read More
Report from DCIA CEO Marty Lafferty
 Federal Communications Commission Chairman Tom Wheeler, who has served in that role since 2013, made his decision public this week to leave the FCC on January 20th.
Federal Communications Commission Chairman Tom Wheeler, who has served in that role since 2013, made his decision public this week to leave the FCC on January 20th.
His announcement follows the US Senate’s non-renewal of a new term for fellow Democrat Commissioner Jessica Rosenworcel, who will need to depart on January 3rd.
This means that the new administration will have a two-to-one majority of Republican Commissioners at the commencement of President-elect Donald Trump’s term.
Tom Wheeler’s accomplishments at the helm of the FCC have been noteworthy for the integrity as well as energy with which he combined advocacy for communications policy advancement, technology innovation, and consumer interests.
He surprised observers who expected him to support industry status quo given his highly successful career as a leading lobbyist for cable and wireless telecommunications interests.
During an era where extreme partisanship has pervaded federal agencies and bureaus, Chairman Wheeler has had to advance his activist agenda with party-line votes, often 3-2 with a Democrat majority.
His legacy will include a number of major accomplishments, all the more remarkable given his relatively short tenure in the position, including rulemakings to ensure network neutrality, privacy protection by internet service providers (ISPs), and low-income broadband service subsidies.
He also made progress on promising initiatives such as opening set-top boxes (STBs) to commercial competition and broadband market reform, serving as a dedicated and tireless advocate on behalf of the public the Commission is intended to serve. Share wisely, and take care.
What Fog Computing Means for IoT
Excerpted from ReadWrite Report by Joachim Brathen

The Internet of Things (IoT) is projected to grow to as much as 20-30 billion connected devices by 2020.
The amount of data being created and subsequently sent to the cloud is therefore set to increase exponentially as a new set of devices achieves connectivity.
Storage and computing power increases according to Moore’s law.
That is they double about every 18 months, yet bandwidth is increasing at a far slower pace.
Some estimates place bandwidth growth at less than 40% per year.
The implication is of course that there will be more data wanting being sent to the cloud then there will be bandwidth. Enter the fog computing paradigm.
Fog computing refers to decentralized computation at the edges of the network, as opposed to being centralized in data centers.
By distributing computing to the edges, the results will be sent to the cloud, not the raw data itself… Read More
Edge Computing Not Yet Telco Priority
Excerpted from LightReading Report by Iain Morris
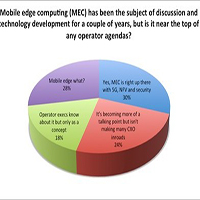 Mobile edge computing (MEC) is rising up the telco agenda even if it is not yet considered to be as strategically important as other next-generation technologies, judging by the results of a new Light Reading poll.
Mobile edge computing (MEC) is rising up the telco agenda even if it is not yet considered to be as strategically important as other next-generation technologies, judging by the results of a new Light Reading poll.
Asked if they thought MEC is near the top of any service provider agendas, only 30% of readers agreed the technology is attracting as much attention as 5G, NFV and security. Another 24% reckon it is becoming more of a talking point, albeit not yet at CXO level.
But 18% of respondents think operators are still relatively ignorant when it comes to MEC, saying telco executives “know about it only as a concept.” And 28% seem baffled by it themselves, choosing “mobile edge what?” in response to Light Reading’s question.
A total of 675 respondents participated in the survey about MEC.
Broadly speaking, the technology is supposed to let operators put their IT resources near base-stations, at the network’s edge, rather than in more centralized data centers.
By reducing network latency and boosting performance, that move – it is hoped – will open up new service opportunities… Read More
Rebalancing the Cyber Equation
Excerpted from NVCA Report by Teresa Shea
 2016 was another banner year for cybersecurity, due heavily to the dizzying number of attacks and data breaches.
2016 was another banner year for cybersecurity, due heavily to the dizzying number of attacks and data breaches.
As is custom at the end of a year, let’s recap some of what we’ve learned and experienced:
The Internal Revenue Service (IRS) reported that the personal information of more than 700,000 taxpayers was compromised in the 2015 hack vs. 100,000+ as it previously reported;
LinkedIn, MySpace, and Tumblr all suffered mega data breaches, leaving exposed an estimated combined total of 500 million accounts;
Yahoo fessed up to the largest single company discovered data breach since the beginning of the internet, which affected a minimum of 500 million accounts;
Popular websites and services including Twitter, Netflix, and Amazon were shut down due to a Distributed-Denial-of-Service (DDoS) attack using hacked Internet of Things (IoT) devices;
State actors breached the Democratic National Committee prior to the Presidential election… Read More
Security Challenges Smart City Adoption
Excerpted from RCRWireless Report by Sean Kinney
 Advances in communications technology, primarily reduced costs of devices and computing power, has set the stage for the internet of things (IoT) to transform urban areas into smart cities, which harness technology to create efficiencies and improve quality-of-life.
Advances in communications technology, primarily reduced costs of devices and computing power, has set the stage for the internet of things (IoT) to transform urban areas into smart cities, which harness technology to create efficiencies and improve quality-of-life.
But there are some major concerns that need to be addressed as smart city technologies are deployed, Petros Mouchtaris, President of Vencore Labs, explained in a talk during the IEEE GLOBECOM 2016 event.
He outlined three areas of risk: interoperability, device cost and lifespan, and security.
“From my perspective, that’s maybe the biggest area of concern.”
Mouchtaris explained that, generally, a low-cost device with a small amount of memory often equates to rudimentary security functions.
Further, IoT devices are difficult to patch due to scale and accessibility, as well as the norm of IoT device builders using third-party security measures, meaning an expertise in security architecture isn’t naturally built into an IoT device… Read More
How to Handle Politics of Cloud Resistance
Excerpted from InfoWorld Report by David Linthicum
 Why do cloud projects fail?
Why do cloud projects fail?
Why does cloud technology not meet expectations?
Why are security models are not transferable to the cloud?
How did you end up with performance issues that can’t be fixed? The answer is usually this: resistance from your colleagues.
The overwhelming issues that I run into when helping clients move to cloud computing are never the technology – those issues are easily fixed.
It’s the people issues.
But don’t despair because there are some actions you can take.
Most cloud computing projects threaten someone in the organization.
No matter if they admit it or not, or if their lives will actually change or not, the core idea of public cloud computing… Read More
Security Checkpointing in Distributed Systems
Excerpted from Search SOA Report by Fred Churchville

In an effort to mitigate the effects of both expected and unexpected service shutdowns, developers and application managers use checkpointing routines to save the state of an application, service or conversation between two or more computers.
Doing so can readily return an app to the state that it was in before a crash.
As an alternative to application-specific checkpointing, which requires developers to write a new checkpointing routine each time they develop an app, transparent checkpointing aims to be application-agnostic.
This approach allows developers to simply write their applications and implement a checkpointing program that works without being tailored to the specific application.
However, transparent checkpointing in distributed systems presents a number of interesting challenges, particularly when it comes to dealing with device and application diversity as well as certain security issues.
In the second part of a two-part Q&A, Professor Gene Cooperman of the College of Computer and Information Science… Read More
Top 15 Security Predictions for 2017
Excerpted from CIO Report by Taylor Armerding
 It is once again, as the song doesn’t quite say, “the most predictive time of the year.”
It is once again, as the song doesn’t quite say, “the most predictive time of the year.”
Not that anybody knows for sure what will be happening even a month from now, never mind six months to a year.
But that does not, and should not, stop organizations from trying.
The way to get ahead and stay ahead, especially in online security, is to look ahead.
So here are some of the best guesses about what we will see in 2017 from several dozen vendors and analysts.
There are many more than 15 predictions out there, of course, but these are the ones we heard most frequently.
Portnox, BitSight, Juniper Networks, HP Enterprise, TrapX Security, and Netskope Internet of Things (IoT) devices – everything from consumer devices to smart meters, medical devices, automobiles, and more – have already been conscripted as zombie troops for cyber attackers, due to their limited computing power and the firmware running on them, which in many cases can’t be patched or updated.
This will get much worse in 2017, given that too many organizations still aren’t inspecting their most commonly used apps… Read More
Hacked Yahoo Data for Sale on Dark Web
Excerpted from NY Times Report by Vindu Goel and Nicole Perlroth

Some time around August 2013, hackers penetrated the email system of Yahoo, one of the world’s largest and oldest providers of free email services.
The attackers quietly scooped up the records of more than 1 billion users, including names, birth dates, phone numbers, and passwords that were encrypted with an easily broken form of security.
The intruders also obtained the security questions and backup email addresses used to reset lost passwords – valuable information for someone trying to break into other accounts owned by the same user, and particularly useful to a hacker seeking to break into government computers around the world.
Several million of the backup addresses belonged to military and civilian government employees from dozens of nations, including more than 150,000 Americans.
No one knows what happened to the data during the next three years.
But last August, a geographically dispersed hacking collective based in Eastern Europe quietly began offering the whole database for sale… Read More
IBM to Create 25,000 US Jobs During Trump Presidency
Excerpted from The Blaze Report by Chris Enloe
 Computer technology giant IBM announced Tuesday that it plans to create more than 25,000 jobs in the United States during the four years of President-elect Donald Trump’s presidency.
Computer technology giant IBM announced Tuesday that it plans to create more than 25,000 jobs in the United States during the four years of President-elect Donald Trump’s presidency.
According to IBM chief executive Ginni Rometty, who wrote an op-ed for USA Today on Tuesday, approximately 6,000 of those new hires will occur over the next year as the company will begin a $1 billion investment into employee training and development.
“We are hiring because the nature of work is evolving – and that is also why so many of these jobs remain hard to fill,” Rometty wrote.
“As industries from manufacturing to agriculture are reshaped by data science and cloud computing, jobs are being created that demand new skills – which in turn requires new approaches to education, training and recruiting.”
“This is not about white collar vs. blue collar jobs, but about the ‘new collar’ jobs that employers in many industries demand, but which remain largely unfilled,” she added, noting that as many as one-third of all IBM employees lack a formal college degree. “What matters most is that these employees – with jobs such as cloud computing technicians… Read More
Raytheon to Help Pentagon Protect Grid from Cyberattacks
Excerpted from Boston Business Journal Report by Kelly O’Brien
 A subsidiary of Waltham defense contractor Raytheon will receive $9 million in funding from the Defense Advanced Research Projects Agency (DARPA) to help build technologies that protect the country’s power grid from cyberattacks, the company announced Monday.
A subsidiary of Waltham defense contractor Raytheon will receive $9 million in funding from the Defense Advanced Research Projects Agency (DARPA) to help build technologies that protect the country’s power grid from cyberattacks, the company announced Monday.
The contracts will go to Raytheon BBN Technologies, a research and development wing of the sprawling company, and are part of DARPA’s $77 million Rapid Attack Detection, Isolation and Characterization Systems program, announced in December 2015.
A main purpose of that program is to reduce the time it would take utility companies to restore power after a cyberattack to seven days, down from the many weeks it would likely take today.
“During the last two decades, industrial control systems have evolved so that most are now connected to the Internet, making them vulnerable to cyberattack,” Jason Redi, vice president for the Raytheon BBN Technologies Networking and Communications unit, said in a statement.
‘”A significant power disruption would have profound economic and human costs in the US so our goals are to prevent attacks… Read More
Adobe Fixes Critical Flaw in Flash Player
Excerpted from Computer World Report by Lucian Constantin
 Adobe Systems has released security updates for several products, including one for Flash Player that fixes a critical vulnerability that’s already known and exploited by attackers.
Adobe Systems has released security updates for several products, including one for Flash Player that fixes a critical vulnerability that’s already known and exploited by attackers.
The Flash Player update fixes 17 vulnerabilities, 16 of which are critical and can be exploited to execute malicious code on affected systems.
One of those vulnerabilities, tracked as CVE-2016-7892 in the Common Vulnerabilities and Exposures (CVE) catalogue, is already being used by hackers.
“Adobe is aware of a report that an exploit for CVE-2016-7892 exists in the wild, and is being used in limited, targeted attacks against users running Internet Explorer (32-bit) on Windows,” the company said in a security advisory.
The vulnerability was reported anonymously to the company.
Users of Flash Player on Windows, macOS and Linux should upgrade to the newly released version 24.0.0.186 as soon as possible. ‘The Flash Player plug-in bundled with Google Chrome and Internet Explorer on Windows 10… Read More
The Rise of the Pragmatic Hybrid Cloud
Excerpted from GeekWire Report by Dan Richman
 Amazon Web Services’ recent re:Invent conference in Las Vegas highlighted the excitement and momentum that public-cloud computing is generating these days, perhaps epitomized by shipping line Matson’s announcement that it is abandoning its own data centers and moving its entire IT operation to AWS.
Amazon Web Services’ recent re:Invent conference in Las Vegas highlighted the excitement and momentum that public-cloud computing is generating these days, perhaps epitomized by shipping line Matson’s announcement that it is abandoning its own data centers and moving its entire IT operation to AWS.
But such wholesale moves to the public cloud, where organizations rent all their computing, storage and networking resources rather than buying and maintaining their own hardware, remain unusual, noted David Linthicum, a podcasting pundit who’s senior VP of consultancy Cloud Technology Partners in Boston, during an interview.
The great majority of organizations using the public cloud – about 85 percent, he estimated – are also using data centers, whether their own or those of a managed-service provider (MSP) or a private hosting company.
Such straddling will remain the norm for a long time to come, Linthicum predicted.
There’s simply too much computing and data that can’t cost-effectively be moved to the cloud.
That means there will remain a strong need for tools and expertise that help the data center and the public cloud communicate… Read More
Coming Events of Interest
CES 2017 — January 5th-8th in Las Vegas, NV. More than 3,800 exhibiting companies showcasing innovation across 2.4 million net square feet, representing 24 product categories.
Industry of Things World USA — February 20th-21st in San Diego, CA. Global leaders will gather to focus on monetization of the Internet of Things (IoT) in an industrial setting.
fintech:CODE — March 16th-17th in London, UK. A new international knowledge exchange platform bringing together all DevOps, IT, and IoT stakeholders who play an active role in the finance and tech scene. Key topics include software development, technical challenges for DevOps, DevOps security, cloud technologies and SaaS.
retail:CODE — March 16th-17th in London, UK. 20 real-life case studies, state-of-the-art keynotes, and interactive World Café sessions, 35+ influential speakers will share their knowledge at the intersection of the retail and technology sectors.
Delivery of Things World — April 24th and 25th in Berlin, Germany. Over 400 IT executives will discuss what DevOps really means for business. This event brings together all stakeholders to share their experience and expertise.
Security of Things World — June 12th and 13th in Berlin, Germany. A world class event focused on the next information security revolution. Security concerns that preoccupy enterprise customers today and pragmatic solutions to threats.
