In This Issue
- Trump Cybersecurity
- Most Data Breaches
- Top 2017 Tech Skills
- Report from the CEO
- Human Factor Area
- Cloud Revolutionized
- Cloud and Fog in IoT
- Cloud Computing End
- Politics of Resistance
- Checkpoint Security
- Security Predictions
- Hacked Yahoo Data
- IBM 25,000 US Jobs
- Raytheon & Pentagon
- Adobe Flash Player
- Pragmatic Hybrid Cld
- Coming DCIA Events
Steps Trump Should Take on Cybersecurity
Excerpted from The Hill Report by Jacob Olcott
 Despite all the hullabaloo about cybersecurity during the presidential campaign – from the WikiLeaks dumps of hacked emails to the Russia-linked breach of state electoral machinery – there was surprisingly little substantive talk by the candidates about how to stop cyberattacks.
Despite all the hullabaloo about cybersecurity during the presidential campaign – from the WikiLeaks dumps of hacked emails to the Russia-linked breach of state electoral machinery – there was surprisingly little substantive talk by the candidates about how to stop cyberattacks.
Now it will be up to President-elect Trump and his administration to figure out ways to thwart the cyber-crime that is occurring with greater frequency and severity against businesses, governments and critical infrastructure.
Shoring up cybersecurity is a massive and complex issue, but the new administration can take positive near-term steps in its own backyard by better protecting government data and creating accountability for departments and agencies.
Not only could these steps start bearing results almost right away; their fiscal cost would be negligible. Washington doesn’t need a Manhattan Project-style investment in cybersecurity research right now as much as simply a stronger commitment to fundamental policies and processes that improve readiness.
How to start?
Quickly gain situational awareness. The old adage that “you can’t manage what you can’t measure” is particularly true in cybersecurity… Read More
Most Data Breaches Due to Missed Details
Excerpted from CNBC Report by Elizabeth Gurdus
 Many large-scale cybersecurity failures like the one that resulted in Yahoo’s recently announced data breach happen because of carelessness of victim companies, cybersecurity expert Stephen Boyer told CNBC on Thursday.
Many large-scale cybersecurity failures like the one that resulted in Yahoo’s recently announced data breach happen because of carelessness of victim companies, cybersecurity expert Stephen Boyer told CNBC on Thursday.
“A lot of these breaches happen because somebody had a very obvious detail that they overlooked or a well-known vulnerability that was exploited,” the BitSight Technologies co-founder and CTO told “Squawk Box.”
Noting 2016 breaches at Neiman Marcus, Kohl’s, Wendy’s, and Vera Bradley, Boyer said large businesses need to increase their protection for the sake of themselves and their customers.
“You think about other controls that they need to put in place such as good password control, multifactor authentication,” he said. “They need to be able to monitor, protect, not only look at their own systems but their supply chain and monitor and watch that very diligently.”
Yahoo did not immediately respond to a CNBC request for comment.
The financial services sector has the best precautions, Boyer said. “They have a very good culture of risk management,” he said… Read More
Tech Skills Employers Looking for in 2017
Excerpted from Business Insider Report by Gianna Scorsone
 When it comes to the tech sector, the hottest, in-demand skills are always changing.
When it comes to the tech sector, the hottest, in-demand skills are always changing.
Tech and IT professionals must stay up to date with the evolving skill sets of their specializations in order to net the jobs with the highest salaries.
While tech professionals work to enhance their skill sets in the ever-changing industry of technology, companies are having a harder time finding the specialized talent they need to meet their business goals.
However, according to Mondo’s latest national survey, nearly 40% of C-level executives reported plans to increase their IT budgets by 25% in 2017.
What hot skills are these innovative businesses investing in for the coming year?
Here’s a look at the most in-demand tech skills companies will utilize in 2017 to remain competitive and successful in the tech-driven future:
1. Cybersecurity. While cybersecurity skills are nothing new when it comes to hot tech skills, they are now more in demand than ever… Read More
Report from DCIA CEO Marty Lafferty
 The year is ending with action related to cybersecurity in both the US Senate and House of Representatives.
The year is ending with action related to cybersecurity in both the US Senate and House of Representatives.
Senator Cory Gardner (R-CO) intends to introduce a bill in the next Congress that would create a select Senate committee to address cybersecurity matters.
Gardner’s announcement this week follows on the heels of a letter from Senators John McCain (R-AZ), Lindsey Graham (R-SC), Jack Reed (D-RI), and Charles Schumer (D-NY) calling for GOP leadership to create a new select committee on cybersecurity to investigate Russian hacking of the Presidential election.
Majority Leader Mitch McConnell (R-KY) has previously argued that the Senate Intelligence Committee rather than a new select committee should take the lead.
Meanwhile, in the House, the Encryption Working Group released its report opposing measures that would weaken encryption protections on computers and other devices.
The bipartisan group said it was not in the national interest to allow police officers to break into encrypted appliances even in the course of an investigation.
At the same time, the working group said Congress must address legitimate concerns of law enforcement and intelligence communities about encryption, and that the issue can no longer be viewed as a divisive binary debate.
The group is a joint project of the House Energy and Commerce and Judiciary Committees.
In addition to the Judiciary Committee Chairman Bob Goodlatte (R-VA), ranking member John Conyers (D-MI), Energy and Commerce Committee Chairman Fred Upton (R-MI) and ranking member Frank Pallone (D-NJ), the working group includes Congresspersons Yvette Clarke (D-NY), Suzan DelBene (D-WA), Darrell Issa (R-CA), Bill Johnson (R-OH), Joe Kennedy III (D-MA), Adam Kinzinger (R-IL), Zoe Lofgren (D-CA), and Jim Sensenbrenner (R-WI).
The benefits of encryption to national security and consumer privacy must be preserved, and a crackdown would be ineffective against criminals.
The report also found discrepancies among the abilities of state, local, and federal law enforcement and intelligence agencies regarding their capabilities to deal with encryption, with the national organizations more advanced.
Finally, the working group urged clarification of the legal means investigators may use to compel the release of information, and whether metadata analysis can substitute for the direct examination of encrypted material. Share wisely and take care.
Human Factor Area of Cybersecurity Risk
Excerpted from Health IT Security Report by Elizabeth Snell

A lack of cybersecurity staff members, a lack of employee training, and not enough boardroom prioritization are top contributions to cybersecurity risk, according to a recent study from the Information Systems Security Association (ISSA) and Enterprise Strategy Group (ESG).
For the survey, 437 information security professionals and ISSA members were interviewed. Respondents were in industries including information technology, government, financial, and healthcare.
Over half of those surveyed – 54 percent – said they have experienced at least one type of security incident. Reasons for the security incidents largely revolved around human factors.
Thirty-one percent said that the cybersecurity team is not large enough for the size of their organization, while approximately one-quarter reported a lack of training for non-technical employees.
Twenty-one percent said that business and executive management often put cybersecurity as a low priority.
“The results gleaned from this research are both alarming and enlightening,” said Candy Alexander, Cyber Security Consultant… Read More
Cloud Revolutionized Business for Everyone
Excerpted from TG Daily Report by Alice Williams
 If your organization hasn’t moved to the Cloud yet, it may be missing out on a host of cost-saving opportunities.
If your organization hasn’t moved to the Cloud yet, it may be missing out on a host of cost-saving opportunities.
The benefits are tremendous, ranging from better customer experience to greater mobile accessibility among your employees.
And according to a 2015 report by Exact, small businesses that employed Cloud-based solutions doubled their profits and generated 25% more revenue growth than their Cloud-reluctant counterparts.
If that’s not enough to convince you to make the switch to the Cloud, ask yourself these three questions and then keep reading to see how adopting the Cloud can revolutionize the way you do business.
1. Pay for Only What You Need. Instead of purchasing excessive equipment and IT infrastructure to support anticipated growth, you can stretch your budget further with the Cloud because you only pay for exactly what you need, when you need it.
The Infrastructure as a Service (IaaS) Cloud-computing platform is a good example.
With its pay-as-you-go model, scalable resources can be adjusted on demand. For instance, seasonal businesses can benefit… Read More
Cloud & Fog Computing in the IoT Revolution
Excerpted from Business Insider Report by Andrew Meola
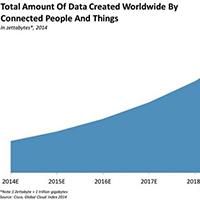 The Internet of Things (IoT) is starting to transform how we live our lives, but all of the added convenience and increased efficiency comes at a cost.
The Internet of Things (IoT) is starting to transform how we live our lives, but all of the added convenience and increased efficiency comes at a cost.
The IoT is generating an unprecedented amount of data, which in turn puts a tremendous strain on the Internet infrastructure. As a result, companies are working to find ways to alleviate that pressure and solve the data problem.
Cloud computing will be a major part of that, especially by making all of the connected devices work together. But there are some significant differences between cloud computing and the Internet of Things that will play out in the coming years as we generate more and more data.
Below, we’ve outlined the differences between the cloud and the IoT, detailed the role of cloud computing in the IoT, and explained “fog computing,” the next evolution of cloud computing.
Cloud computing, often called simply “the cloud,” involves delivering data, applications, photos, videos, and more over the Internet to data centers. IBM has helpfully broken down cloud computing into six different categories:
Software as a service (SaaS): Cloud-based applications run on computers off-site or “in the cloud”… Read More
Predicting the End of Cloud Computing
Excerpted from Network World Report by Brandon Butler
 Here’s a prediction you don’t hear very often: The cloud computing market, as we know it, will be obsolete in a matter of years.
Here’s a prediction you don’t hear very often: The cloud computing market, as we know it, will be obsolete in a matter of years.
The provocateur is Peter Levine, a general partner at venture capital firm Andreessen Horowitz. He believes that the increased computing power of intelligent Internet of Things devices, combined with ever-increasingly accurate machine learning technologies, will largely replace the infrastructure as a service public cloud market.
The cloud as it’s known today is a “very centralized model” of computing, Levine says.
Information is sent to the cloud where it is processed and stored. Many applications live in the cloud and whole data centers are being migrated to it.
Levine says we’re already starting to see signs of Internet of Things (IoT) devices replacing some of the computing power of the cloud.
There are smart cars, drones, robots, appliances and machines. Each of these devices collects data in real time… Read More
How to Handle Politics of Cloud Resistance
Excerpted from InfoWorld Report by David Linthicum
 Why do cloud projects fail?
Why do cloud projects fail?
Why does cloud technology not meet expectations?
Why are security models are not transferable to the cloud?
How did you end up with performance issues that can’t be fixed? The answer is usually this: resistance from your colleagues.
The overwhelming issues that I run into when helping clients move to cloud computing are never the technology – those issues are easily fixed.
It’s the people issues.
But don’t despair because there are some actions you can take.
Most cloud computing projects threaten someone in the organization.
No matter if they admit it or not, or if their lives will actually change or not, the core idea of public cloud computing… Read More
Security Checkpointing in Distributed Systems
Excerpted from Search SOA Report by Fred Churchville

In an effort to mitigate the effects of both expected and unexpected service shutdowns, developers and application managers use checkpointing routines to save the state of an application, service or conversation between two or more computers.
Doing so can readily return an app to the state that it was in before a crash.
As an alternative to application-specific checkpointing, which requires developers to write a new checkpointing routine each time they develop an app, transparent checkpointing aims to be application-agnostic.
This approach allows developers to simply write their applications and implement a checkpointing program that works without being tailored to the specific application.
However, transparent checkpointing in distributed systems presents a number of interesting challenges, particularly when it comes to dealing with device and application diversity as well as certain security issues.
In the second part of a two-part Q&A, Professor Gene Cooperman of the College of Computer and Information Science… Read More
Top 15 Security Predictions for 2017
Excerpted from CIO Report by Taylor Armerding
 It is once again, as the song doesn’t quite say, “the most predictive time of the year.”
It is once again, as the song doesn’t quite say, “the most predictive time of the year.”
Not that anybody knows for sure what will be happening even a month from now, never mind six months to a year.
But that does not, and should not, stop organizations from trying.
The way to get ahead and stay ahead, especially in online security, is to look ahead.
So here are some of the best guesses about what we will see in 2017 from several dozen vendors and analysts.
There are many more than 15 predictions out there, of course, but these are the ones we heard most frequently.
Portnox, BitSight, Juniper Networks, HP Enterprise, TrapX Security, and Netskope Internet of Things (IoT) devices – everything from consumer devices to smart meters, medical devices, automobiles, and more – have already been conscripted as zombie troops for cyber attackers, due to their limited computing power and the firmware running on them, which in many cases can’t be patched or updated.
This will get much worse in 2017, given that too many organizations still aren’t inspecting their most commonly used apps… Read More
Hacked Yahoo Data for Sale on Dark Web
Excerpted from NY Times Report by Vindu Goel and Nicole Perlroth

Some time around August 2013, hackers penetrated the email system of Yahoo, one of the world’s largest and oldest providers of free email services.
The attackers quietly scooped up the records of more than 1 billion users, including names, birth dates, phone numbers, and passwords that were encrypted with an easily broken form of security.
The intruders also obtained the security questions and backup email addresses used to reset lost passwords – valuable information for someone trying to break into other accounts owned by the same user, and particularly useful to a hacker seeking to break into government computers around the world.
Several million of the backup addresses belonged to military and civilian government employees from dozens of nations, including more than 150,000 Americans.
No one knows what happened to the data during the next three years.
But last August, a geographically dispersed hacking collective based in Eastern Europe quietly began offering the whole database for sale… Read More
IBM to Create 25,000 US Jobs During Trump Presidency
Excerpted from The Blaze Report by Chris Enloe
 Computer technology giant IBM announced Tuesday that it plans to create more than 25,000 jobs in the United States during the four years of President-elect Donald Trump’s presidency.
Computer technology giant IBM announced Tuesday that it plans to create more than 25,000 jobs in the United States during the four years of President-elect Donald Trump’s presidency.
According to IBM chief executive Ginni Rometty, who wrote an op-ed for USA Today on Tuesday, approximately 6,000 of those new hires will occur over the next year as the company will begin a $1 billion investment into employee training and development.
“We are hiring because the nature of work is evolving – and that is also why so many of these jobs remain hard to fill,” Rometty wrote.
“As industries from manufacturing to agriculture are reshaped by data science and cloud computing, jobs are being created that demand new skills – which in turn requires new approaches to education, training and recruiting.”
“This is not about white collar vs. blue collar jobs, but about the ‘new collar’ jobs that employers in many industries demand, but which remain largely unfilled,” she added, noting that as many as one-third of all IBM employees lack a formal college degree. “What matters most is that these employees – with jobs such as cloud computing technicians… Read More
Raytheon to Help Pentagon Protect Grid from Cyberattacks
Excerpted from Boston Business Journal Report by Kelly O’Brien
 A subsidiary of Waltham defense contractor Raytheon will receive $9 million in funding from the Defense Advanced Research Projects Agency (DARPA) to help build technologies that protect the country’s power grid from cyberattacks, the company announced Monday.
A subsidiary of Waltham defense contractor Raytheon will receive $9 million in funding from the Defense Advanced Research Projects Agency (DARPA) to help build technologies that protect the country’s power grid from cyberattacks, the company announced Monday.
The contracts will go to Raytheon BBN Technologies, a research and development wing of the sprawling company, and are part of DARPA’s $77 million Rapid Attack Detection, Isolation and Characterization Systems program, announced in December 2015.
A main purpose of that program is to reduce the time it would take utility companies to restore power after a cyberattack to seven days, down from the many weeks it would likely take today.
“During the last two decades, industrial control systems have evolved so that most are now connected to the Internet, making them vulnerable to cyberattack,” Jason Redi, vice president for the Raytheon BBN Technologies Networking and Communications unit, said in a statement.
‘”A significant power disruption would have profound economic and human costs in the US so our goals are to prevent attacks… Read More
Adobe Fixes Critical Flaw in Flash Player
Excerpted from Computer World Report by Lucian Constantin
 Adobe Systems has released security updates for several products, including one for Flash Player that fixes a critical vulnerability that’s already known and exploited by attackers.
Adobe Systems has released security updates for several products, including one for Flash Player that fixes a critical vulnerability that’s already known and exploited by attackers.
The Flash Player update fixes 17 vulnerabilities, 16 of which are critical and can be exploited to execute malicious code on affected systems.
One of those vulnerabilities, tracked as CVE-2016-7892 in the Common Vulnerabilities and Exposures (CVE) catalogue, is already being used by hackers.
“Adobe is aware of a report that an exploit for CVE-2016-7892 exists in the wild, and is being used in limited, targeted attacks against users running Internet Explorer (32-bit) on Windows,” the company said in a security advisory.
The vulnerability was reported anonymously to the company.
Users of Flash Player on Windows, macOS and Linux should upgrade to the newly released version 24.0.0.186 as soon as possible. ‘The Flash Player plug-in bundled with Google Chrome and Internet Explorer on Windows 10… Read More
The Rise of the Pragmatic Hybrid Cloud
Excerpted from GeekWire Report by Dan Richman
 Amazon Web Services’ recent re:Invent conference in Las Vegas highlighted the excitement and momentum that public-cloud computing is generating these days, perhaps epitomized by shipping line Matson’s announcement that it is abandoning its own data centers and moving its entire IT operation to AWS.
Amazon Web Services’ recent re:Invent conference in Las Vegas highlighted the excitement and momentum that public-cloud computing is generating these days, perhaps epitomized by shipping line Matson’s announcement that it is abandoning its own data centers and moving its entire IT operation to AWS.
But such wholesale moves to the public cloud, where organizations rent all their computing, storage and networking resources rather than buying and maintaining their own hardware, remain unusual, noted David Linthicum, a podcasting pundit who’s senior VP of consultancy Cloud Technology Partners in Boston, during an interview.
The great majority of organizations using the public cloud – about 85 percent, he estimated – are also using data centers, whether their own or those of a managed-service provider (MSP) or a private hosting company.
Such straddling will remain the norm for a long time to come, Linthicum predicted.
There’s simply too much computing and data that can’t cost-effectively be moved to the cloud.
That means there will remain a strong need for tools and expertise that help the data center and the public cloud communicate… Read More
Coming Events of Interest
CES 2017 — January 5th-8th in Las Vegas, NV. More than 3,800 exhibiting companies showcasing innovation across 2.4 million net square feet, representing 24 product categories.
Industry of Things World USA — February 20th-21st in San Diego, CA. Global leaders will gather to focus on monetization of the Internet of Things (IoT) in an industrial setting.
fintech:CODE — March 16th-17th in London, UK. A new international knowledge exchange platform bringing together all DevOps, IT, and IoT stakeholders who play an active role in the finance and tech scene. Key topics include software development, technical challenges for DevOps, DevOps security, cloud technologies and SaaS.
retail:CODE — March 16th-17th in London, UK. 20 real-life case studies, state-of-the-art keynotes, and interactive World Café sessions, 35+ influential speakers will share their knowledge at the intersection of the retail and technology sectors.
Delivery of Things World — April 24th and 25th in Berlin, Germany. Over 400 IT executives will discuss what DevOps really means for business. This event brings together all stakeholders to share their experience and expertise.
Security of Things World — June 12th and 13th in Berlin, Germany. A world class event focused on the next information security revolution. Security concerns that preoccupy enterprise customers today and pragmatic solutions to threats.
