In This Issue
- Sil Valley Looks to AI
- Telefonica CEO Alierta
- FCC New Privacy Cop?
- Report from the CEO
- NetApp Data Analytics
- Oculus Rift: VR Portal
- Containers & MicSvcs
- Robin Sys & Zettaset
- FBI Apple Postmortem
- Apple vs. FBI and IoT
- NSA Director in Israel
- Wall Street Allegiance
- Korea Cloud Priority
- Scalability Dilemma
- Three Big Data Tips
- MarkAny DRM for 3D
- Coming DCIA Events
Silicon Valley Looks to AI for Next Big Thing
Excerpted from NY Times Report by Quentin Hardy
 As the oracles of Silicon Valley debate whether the latest tech boom is sliding toward bust, there is already talk about what will drive the industry’s next growth spurt.
As the oracles of Silicon Valley debate whether the latest tech boom is sliding toward bust, there is already talk about what will drive the industry’s next growth spurt.
The way we use computing is changing, toward a boom (and, if history is any guide, a bubble) in collecting oceans of data in so-called cloud computing centers, then analyzing the information to build new businesses.
The terms most often associated with this are “machine learning” and “artificial intelligence,” or “AI.”
And the creations spawned by this market could affect things ranging from globe-spanning computer systems to how you pay at the cafeteria.
“There is going to be a boom for design companies, because there’s going to be so much information people have to work through quickly,” said Diane B. Greene, the head of Google Compute Engine, one of the companies hoping to steer an AI boom.
“Just teaching companies how to use AI will be a big business.”
This kind of change is what keeps Silicon Valley going… Read More
Telefonica CEO Cesar Alierta to Step Down
Excerpted from Wall St. Journal Report by Jeannette Neumann
 Telefonica Chairman and Chief Executive Cesar Alierta is stepping down, capping nearly 16 years at the helm of the Spanish telecommunications giant where he oversaw a period of expansion followed by a more recent retrenchment as the firm grapples with a hefty debt load.
Telefonica Chairman and Chief Executive Cesar Alierta is stepping down, capping nearly 16 years at the helm of the Spanish telecommunications giant where he oversaw a period of expansion followed by a more recent retrenchment as the firm grapples with a hefty debt load.
Mr. Alierta, 70 years old, is proposing Chief Operating Officer Jose Maria Alvarez-Pallete to succeed him, the company said on Tuesday.
Telefonica’s Board will vote on Mr. Alvarez-Pallete’s appointment at an April 8th meeting.
While analysts and investors say they had anticipated Mr. Alierta would step down, Tuesday’s announcement came sooner than some had expected.
Telefonica didn’t provide any details on the timing of his exit.
Mr. Alierta will remain on the Board and continue to run the company’s foundation.
Mr. Alierta’s naming of Mr. Alvarez-Pallete, on the other hand, was no surprise to analysts and investors… Read More
Will FCC Be New Privacy Cop?
Excerpted from Morning Consult Report by Amir Nasr
 The Federal Communications Commission (FCC) will dive into a controversial policy proposal Thursday when the five-member panel convenes to vote on privacy rules for broadband Internet service providers (ISPs).
The Federal Communications Commission (FCC) will dive into a controversial policy proposal Thursday when the five-member panel convenes to vote on privacy rules for broadband Internet service providers (ISPs).
The new rules could thrust the FCC into the shared role of privacy cop with the Federal Trade Commission (FTC).
The rules are still in nascent stages, but they could have a major impact on ISPs and the broadband industry as a whole.
When the FCC took the unusual step of releasing a fact sheet about the proposal on March 10th, numerous industry groups weighed in worrying that the FCC’s entrance into the ISP space could create two sets of regulations enforced by two separate agencies.
The FTC also regulates ISPs.
It’s a long rulemaking process. But ISPs are already pushing back.
A new set of privacy requirements from a new regulator would give them far more work and expose them to more liability.
Providers argue that they already have requirements for how they handle consumer data enforced by the FTC… Read More
DCINFO Editor Update: Divided FCC Approves Broadband Privacy Rules
Report from DCIA CEO Marty Lafferty
 The DCIA is pleased to announce that we will be an Organizational Sponsor for the 2016 Creative Storage Conference (CS 2016), in support of our member company delegates, exhibitors, and speakers.
The DCIA is pleased to announce that we will be an Organizational Sponsor for the 2016 Creative Storage Conference (CS 2016), in support of our member company delegates, exhibitors, and speakers.
The Tenth Annual Creative Storage Conference will be held June 23rd at the DoubleTree Hotel – West Los Angeles in Culver City, CA.
The event brings together digital storage providers, equipment manufacturers, software distributors, and professional media and entertainment end-users to explore the conference theme “The Art of Storage.”
At CS 2016, you’ll be able to learn the latest developments in digital storage for media and entertainment, and network with industry professionals.
Conference registration is now open here.
This one-day conference and exhibits bring together the vendors, end-users, researchers, and visionaries who will meet growing demand for digital storage for content capture, editing, archiving, and distribution.
Corporate sponsors and exhibitors include Micron, SGL, Spectra Logic, SwiftStack, and Visuality Systems.
In addition to the DCIA, media and organization sponsors include Broadcast Beat, Colonial Purchasing, Drive Trust Alliance, Flash Memory Summit, HDDFA, Home Toys/AVSystems, M&E Tech, Parks Associates, Post Magazine, ProductionHub.com, RDC, reviewster, SMPTE, and SNIA.
Speaking proposals are being solicited for CS 2016 until May 1st.
You can submit your recommendations for solo presenters or panelists for this premiere event here.
We have a great agenda planned with six sessions throughout the day.
There also will be four keynote talks during the conference, and a sponsored reception in the evening.
The preliminary agenda is posted on the conference website.
Exhibiting and sponsoring opportunities also are still available for CS 2016.
Several levels of conference, website, and event sponsorships are available as well as table-top exhibits.
Information on sponsorship and exhibit opportunities is available here.
For additional information about the conference, please call 408-202-5098 or email info@creativestorage.org.
The Creative Storage Conference is hosted by the Entertainment Storage Alliance and Coughlin Associates. Share wisely, and take care.
NetApp Advances Data Analytics Performance
Excerpted from Company Press Announcement
 “With the significant amount of machine-generated data captured every day, we rely on NetApp E-Series to deploy Splunk for monitoring and troubleshooting the multiple platforms in our environment,” said Roy Shiladitya, head of Information Technology at ING DIRECT Australia.
“With the significant amount of machine-generated data captured every day, we rely on NetApp E-Series to deploy Splunk for monitoring and troubleshooting the multiple platforms in our environment,” said Roy Shiladitya, head of Information Technology at ING DIRECT Australia.
“This high-availability solution gives us the ability to quickly visualize and proactively analyze the data in order to respond to the business and meet SLAs.”
NetApp today announced new software for its NetApp EF-Series all-flash and E-Series storage arrays that dramatically boost the performance and value of data analytics applications.
New generations of business intelligence applications such as Splunk, Hadoop, and NoSQL are becoming key tools for the data-powered digital enterprise.
Customers want greater data visibility and performance from these applications to make the best decisions in a fast-changing business landscape.
The newest release of the NetApp SANtricity storage operating system accelerates time to value for customers… Read More
Oculus Rift: Clunky Portal to Promising VR
Excerpted from NY Times Report by Brian Chen
 A dream of science fiction, which is how Facebook’s Mark Zuckerberg describes virtual reality (VR) is about to come true.
A dream of science fiction, which is how Facebook’s Mark Zuckerberg describes virtual reality (VR) is about to come true.
Oculus, the VR company that Facebook acquired for $2 billion two years ago, released its much-hyped Oculus Rift system on Monday.
With a headset, camera, and game controller, the system, which costs $1,500 when bundled with a powerful computer, is the first VR product of its kind to reach consumers, before similar ones coming this year from HTC and Sony.
“People who try it say it’s different from anything they’ve ever experienced in their lives,” Mr. Zuckerberg wrote in a post when he announced the Oculus acquisition.
“But this is just the start. Imagine enjoying a courtside seat at a game, studying in a classroom of students and teachers all over the world or consulting with a doctor face-to-face — just by putting on goggles in your home.”
Over the last week, I tested the Rift and many pieces of content for the system to see how true Mr. Zuckerberg’s words might ring.
I can report that the Rift is a well-built hardware system brimming with potential… Read More
Containers & Microservices Enter Production Environments
Excerpted from Talkin’ Cloud Report by Christopher Tozzi
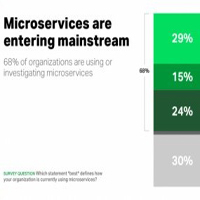 Containers — the data center technology you’ve heard all about, but probably not seen often in production — are finally making their way into the real world.
Containers — the data center technology you’ve heard all about, but probably not seen often in production — are finally making their way into the real world.
That’s according to a survey out this week from NGINX.
Titled “2016 Future of Application Development and Delivery Survey,” the report reveals data based on responses from more than 1,800 IT professionals. It covers a broad range of topics related to application development and deployment, ranging from cloud trends to security issues.
But the most interesting finding was about container adoption.
According to NGINX, 20 percent of respondents say they are now using containers in production.
And those that have already adopted containers are using them in a big way, with one-third reporting running them for more than 80 percent of workloads.
This suggests that, while the move to containers may have been slow to get underway, companies are doing much more than just dabbling… Read More
Robin Systems & Zettaset Secure Containerization
Excerpted from Company Press Announcement
 Robin Systems, the pioneer in containerization enterprise software, and Zettaset, the leader in Big Data security, today announced a strategic partnership that will provide organizations with a scalable, performance-optimized, and highly secure container-based solution for Big Data applications.
Robin Systems, the pioneer in containerization enterprise software, and Zettaset, the leader in Big Data security, today announced a strategic partnership that will provide organizations with a scalable, performance-optimized, and highly secure container-based solution for Big Data applications.
Robin’s container-based, application-aware, compute and storage platform liberates applications from servers, VMs, and storage limitations.
Robin ensures the best possible hardware utilization with multi-tenant harmony and complete performance isolation for each application.
By leveraging lightweight and portable container-based application packaging technology, Robin enables seamless application mobility across machines and across clouds.
Robin is the ONLY containerization platform that works with all types of enterprise applications, including performance-sensitive databases and Big Data clusters.
Robin’s Virtual Data Lake capability enables organizations to consolidate data across multiple HDFS clusters… Read More
FBI vs. Apple: A Postmortem
Excerpted from Hackaday Report by Elliot Williams
 By now you’ve doubtless heard that the FBI has broken the encryption on the iPhone of Syed Farook — the suicide terrorist who killed fourteen and then himself in San Bernardino, CA.
By now you’ve doubtless heard that the FBI has broken the encryption on the iPhone of Syed Farook — the suicide terrorist who killed fourteen and then himself in San Bernardino, CA.
Consequently, they won’t be requiring Apple’s (compelled) services any more.
A number of people have written in and asked what we knew about the hack, and the frank answer is “not a heck of a lot”.
And it’s not just us, because the FBI has classified the technique.
What we do know is that they paid Cellebrite, an Israeli security firm, at least $218,004.85 to get the job done for them.
Why would we want to know more?
Because, broadly, it matters a lot if it was a hardware attack or a software attack.
If the attack was hardware, it may not be such a big deal.
The iPhones supposedly prevent a brute-force (guessing) attack against the password by wiping memory… Read More
NSA Director in Israel to Talk Cybersecurity
Excerpted from Neowin Report by Paul Hill
 The head of the US National Security Agency (NSA) visited Israel last week, in secret, to meet with the Israel Defense Forces’ (IDF) Intelligence Corps Unit 8200, Israel’s signals intelligence (SIGINT) agency.
The head of the US National Security Agency (NSA) visited Israel last week, in secret, to meet with the Israel Defense Forces’ (IDF) Intelligence Corps Unit 8200, Israel’s signals intelligence (SIGINT) agency.
In the meeting, NSA head Admiral Michael Rogers, met with Israeli security officials to plan even closer ties between the two agencies.
A senior Israeli official told Haaretz that the closer ties between the NSA and Unit 8200 will strengthen the countries from cyber-attacks carried out by Iran and the Lebanese group Hezbollah.
The meeting came soon after the US Department of Justice charged seven Iranian hackers over several cyber-attacks that took place between 2011 and 2013, which involved banks and a small dam near New York City, NY.
Loretta Lynch, the US Attorney General, said the hacks were carried out “with the sole purpose of undermining the targeted companies and damaging the online operation of America’s free market.”
The NSA and Unit 8200 have had a close relationship for many years.
Their closeness has been shown recently with the Stuxnet virus, which experts claim was made in collaboration between the two agencies… Read More
Wall Street’s Alliance Against Hackers
Excerpted from ThinkAdvisor Report by Joyce Hanson
 JPMorgan Chase Chief Executive Jamie Dimon fired one of the first shots in the financial services industry’s war on computer hackers after a 2014 cyber-attack on his bank compromised the accounts of 7 million small businesses and 76 million households.
JPMorgan Chase Chief Executive Jamie Dimon fired one of the first shots in the financial services industry’s war on computer hackers after a 2014 cyber-attack on his bank compromised the accounts of 7 million small businesses and 76 million households.
In a letter to shareholders that year, Dimon spoke of the “absolute, critical, and immediate” need to combat cybersecurity threats along with related fraud issues and privacy protection.
Notably, Dimon followed up those words with an acknowledgment that businesses will have to work hand in hand with regulators to restrict use of the bank’s data by third parties and ensure that customers’ money and identities remain safe.
“I do not believe that most people fully understand what no longer is private and how their information is being bought, sold and used,” Dimon wrote.
“It is critical that government and business and regulators collaborate effectively and in real time.”
“Cybersecurity is an area where government and business have been working well together, but there is much more to be done. And if it is not done in a concerted way, we all will pay a terrible price… Read More
Korean Government Prioritizes Cloud Growth
Excerpted from Business Cloud News Report by Jamie Davies
 The Korean government has announced a new policy to accelerate the adoption of cloud computing in the country, according to Business Korea.
The Korean government has announced a new policy to accelerate the adoption of cloud computing in the country, according to Business Korea.
Speaking at a cloud computing conference in Korea, the Ministry of Science, ICT, and Future Planning has announced that it will be running a number of initiatives to increase the adoption of cloud computing from 6.4% to 13%, seemingly over the next twelve months.
Over the same period, the government also plans to increase the number of Korean cloud companies from 353 to 500, as well as growing private cloud adoption in public institutions to at least 3%.
The Korean government has estimated that should the new initiatives be successful the domestic cloud market could be worth in excess of 1.1 trillion won.
To support the growth of the industry, the government will also build a cloud computing support center in Daegu City, which will provide guidance for public institutions who are making the transition.
While the government has laid bare its intentions, it has not been stated how cloud computing is currently perceived by industry… Read More
Scalability Dilemma and Case for Decoupling
Excerpted from HPCwire Report by Justin Shi
 The need for extreme scale computing is driven by the seemingly forever fledgling Internet.
The need for extreme scale computing is driven by the seemingly forever fledgling Internet.
In abstract, the entire network is already an extreme scale computing engine.
The technical difficulty, however, is to harness the dispersed computing powers for a single purpose.
An analogy to this would be to build an engine capable of harnessing the combustive power of elements to move people or things.
The presence of such an engine could drive transformative changes in technology, society, and the economy.
The first requirement for such an extreme scale computing engine is the ability to gain incrementally better performance and reliability while concurrently expanding in size.
We expect more from this engine than we do from a sports car.
The “cost of doing business” should only include oil changes, tire, and bearing replacements, but not re-building the car when a tire bursts or the engine upgrades… Read More
Three Tips for Optimizing Big Data Analytics
Excerpted from Windows IT Report by Karen Schwartz
 Converged infrastructure systems provide many of the resources required for effective Big Data analytics, from the ability to handle Hadoop to storage scalability.
Converged infrastructure systems provide many of the resources required for effective Big Data analytics, from the ability to handle Hadoop to storage scalability.
Every year, the amount and type of data companies must manage increases.
Commonly called Big Data, this information — everything from social media posts, audio, and images to transaction records, sensor data, and video — continues growing unabated.
According to IDC, data is growing at 40 percent per year and will continue to do so into the next decade.
Companies are struggling with how to efficiently and cost effectively collect and store this fast-growing data.
But the real benefit lies in being able to analyze it in ways that can improve product quality, speed decision-making, boost customer service, and optimize business processes.
And it works; according to a Dell survey, 89 percent of companies with Big Data initiatives report significant improvements in corporate decision-making… Read More
Treacherous Cloud Computing Threats
Excerpted from Information Management Report
 Most organizations now have some presence in the cloud, but data security remains a top concern, especially when business units acquire cloud services independent of the IT department. To help illustrate the problems such practices can create, the Cloud Security Alliance has compiled its list of “The Treacherous 12: Cloud Computing Top Threats in 2016.”
Most organizations now have some presence in the cloud, but data security remains a top concern, especially when business units acquire cloud services independent of the IT department. To help illustrate the problems such practices can create, the Cloud Security Alliance has compiled its list of “The Treacherous 12: Cloud Computing Top Threats in 2016.”
The risk of data breach is not unique to cloud computing, but it consistently ranks as a top concern for cloud customers. Cloud providers are highly accessible and the vast amount of data they host makes them an attractive target.
Malicious actors masquerading as legitimate users, operators or developers can read/exfiltrate, modify and delete data; issue control plane and management functions; snoop on data in transit or release malicious software that appears to originate from a legitimate source.
APIs and UIs are generally the most exposed part of a system, perhaps the only asset with an IP address available outside the trusted organizational boundary. These assets will be the target of heavy attack, and adequate controls protecting them from the Internet are the first line of defense and detection.
With the advent of multitenancy in cloud computing, systems from various organizations are placed in close proximity to each other… Read More
MarkAny Develops DRM & Piracy Protection for 3D Print
Excerpted from 3ders Blog by Andre
 Digital Rights Management, or DRM for short, are tools made available to digital rights holders to protect their works.
Digital Rights Management, or DRM for short, are tools made available to digital rights holders to protect their works.
Throughout the years, all manner of video, audio, and text available for purchase and digital consumption have played with DRM to protect their intellectual property (IP).
Efforts in DRM are now being pushed forward in the 3D printing space thanks in part to Korean DRM and watermarking company MarkAny.
Originally announced in the summer of 2015, the company hopes to create what they call a 3D printing contents clearing center.
Their system is designed to detect violating files and, as they put it, “protect the output of 3D printing processes, such as 3D printing design, STL generation, G-Code conversion, and actual printing.”
Additionally, they also want to implement a monitoring system that watches illegal distribution of protected 3D print files.
Based on the newly released video presentation above, they certainly do seem serious about their efforts… Read More
Coming Events of Interest
Delivery of Things World — April 25th-26th in Berlin, Germany. DevOps specialists, continuous development strategists, architect newbies, development geeks, and cloud geniuses from across the spectrum of DevOps transformation come together at this stimulating and innovative event.
DataCloud Europe 2016 — June 8th-9th in Monte Carlo, Monaco. The 2016 conference will focus on cloud computing advances and changes in data management, with a stellar line-up of speakers including global infrastructure leaders and subject matter experts.
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
2016 Creative Storage Conference — June 23rd in Culver Cirty, CA. The tenth annual CS will bring together digital storage providers, equipment manufacturers, software distributors, and professional media and entertainment end-users to explore the conference theme “The Art of Storage.”
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Mobile World Congress Shanghai — June 29th – July 1st in Shanghai, China. MWC Shanghai is a very unique gathering that brings together industry participants ranging from C-Level mobile executives to end-user consumers passionate about mobile.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
