In This Issue
- Intelligent Cloud Era
- DHS Seeking Vendors
- Senate Encryption Bill
- Report from the CEO
- WhatsApp End-to-End
- VZ & AwesomenessTV
- NetApp Flash Growth
- IoT Goes Mainstream
- Net-Connected TVs
- FCC Privacy Proposal
- MIT Tracking System
- Linux’s Torvalds: IoT
- Avoid Data Breaches
- Veriflow Secure Nets
- Virt Reality in Clouds
- VR to Go Mainstream
- Coming DCIA Events
Era of the Intelligent Cloud Arrives
Excerpted from Forbes Report by Louis Columbus
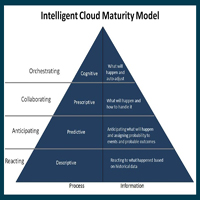 The following insights are based on a series of discussions with C-level executives and revenue team leaders across several industries regarding their need for an intelligent cloud:
The following insights are based on a series of discussions with C-level executives and revenue team leaders across several industries regarding their need for an intelligent cloud:
In the enterprise, the cloud versus on-premise war is over, and the cloud has won.
Nearly all are embracing a hybrid cloud strategy to break down the barriers that held them back from accomplishing more.
None of the C-level executives I’ve spoken with recently are satisfied with just measuring cloud adoption.
All are saying the want to measure business outcomes and gain greater insights into how they can better manage revenue and sales cycles.
Gaining access to every available legacy and third party system using hybrid cloud strategies is the new normal.
Having data that provides enterprise-wide visibility provides greater control over every aspect of selling and revenue management processes. And when that’s accomplished, the insights gained from the intelligent cloud can be turned into results… Read More
DHS Seeks Cybersecurity Center Vendors
Excepted from Federal Times Report by Aaron Boyd
 The Department of Homeland Security (DHS) released the final request for proposals (RFP) for its $395 million contract to support the agency’s network security services.
The Department of Homeland Security (DHS) released the final request for proposals (RFP) for its $395 million contract to support the agency’s network security services.
The Next Generation Security Operations Center (NextGen SOC) contract will enable DHS components — namely the Office of the CIO, National Protections and Programs Directorate and Science and Technology Directorate — to buy cybersecurity tools and support services to secure the department’s internal networks.
While OCIO, NPPD and S&T will take the lead, all DHS components will be able to issue task orders on the contract to secure their networks.
“The task orders issued hereunder will be designed to acquire a broad range of services and solutions — under various contract types — to fulfill the department’s cybersecurity mission,” according to the synopsis.
That mission includes a mandate to “prevent, detect, contain and eradicate cyber threats through monitoring, intrusion detection, and protective security services to DHS information systems.”
Those services will include continuous monitoring, digital media analysis, penetration testing, incident response, hunting for insider threats… Read More
Senate Intel to Release Draft Encryption Bill
Excerpted from The Hill Report by Cory Bennett
 A draft of the Senate Intelligence Committee’s encryption bill is expected to circulate sometime this week, Chairman Richard Burr (R-NC) told reporters on Monday.
A draft of the Senate Intelligence Committee’s encryption bill is expected to circulate sometime this week, Chairman Richard Burr (R-NC) told reporters on Monday.
The measure — a response to concerns that criminals are increasingly using encrypted devices to hide from authorities — would require firms to comply with court orders seeking access to locked data.
“My hope is that you will have it in your hands this week,” Burr said.
Privacy and civil liberties advocates have pre-emptively campaigned against the bill, arguing it would undermine global security and endanger online privacy.
But law enforcement officials and some lawmakers say such a measure is necessary to help police properly conduct criminal and terrorism investigations.
Burr has been on the cusp of unveiling his bill for several weeks now.
He previously indicated the draft might drop shortly before the Senate left town in mid-March for a two-week recess… Read More
Report from DCIA CEO Marty Lafferty
 The DCIA is pleased to announce an expansion of our partnership with NewBay Media to include Government Video Expo 2016.
The DCIA is pleased to announce an expansion of our partnership with NewBay Media to include Government Video Expo 2016.
NewBay Media connects and informs millions of constituents in the world’s most dynamic industries through its award-winning content, integrated media capabilities, and high-profile network-building informative events.
NewBay’s brands include Broadcasting & Cable, Multichannel News, TV Technology, Music Week — more than 60 print and digital publications in all, and over 100 integrated web and mobile applications, conferences and conventions, custom marketing services, and e-commerce capabilities.
Government Video Expo is the East Coast’s largest technology event designed for video, broadcast, and audio-video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and the Briefing Zone, an educational series of panel discussions.
Held at the Walter E. Washington Convention Center in Washington, DC, this three-day educational event will take place on December 6th through 8th, and includes multiple concurrent sessions.
At the 2015 event, attendees learned about cutting-edge video technologies and techniques at the DC Post|Production Conference; distance learning and education technology at the full-day seminar on Video Supporting Distance Learning in the Federal Government; and drone operation and production at the new National Drone Show.
Featuring conference programs designed to teach, enlighten and inspire, Government Video Expo 2016 will encourage attendees to get hands-on with the latest video gear in an exhibit hall featuring more than 175 suppliers, dealers, and distributors.
If you shoot, edit, post, store, or distribute video, or use AV solutions, please put this important event on your calendar.
Click here to receive event updates, and plan now to join the DCIA for the Government Video Expo 2016. Share wisely, and take care.
WhatsApp Introduces End-to-End Encryption
Excerpted from NY Times Report by Mike Isaac
 WhatsApp, the messaging app owned by Facebook and used by more than one billion people, on Tuesday introduced full encryption for its service, a way to ensure that only the sender and recipient can read messages sent using the app.
WhatsApp, the messaging app owned by Facebook and used by more than one billion people, on Tuesday introduced full encryption for its service, a way to ensure that only the sender and recipient can read messages sent using the app.
Known as “end-to-end encryption,” it will be applied to photos, videos and group text messages sent among people in more than 50 languages across the world, including India, Brazil and Europe.
Previously, only one-to-one text messages were fully encrypted.
“Every day we see stories about sensitive records being improperly accessed or stolen,” WhatsApp said in blog post.
“And if nothing is done, more of people’s digital information and communication will be vulnerable to attack in the years to come.”
“Fortunately, end-to-end encryption protects us from these vulnerabilities,” the company said.
The move thrusts WhatsApp further into a standoff between tech companies and law enforcement officials over access to digital data… Read More
Verizon & AwesomenessTV Redefine Mobile Video
Excerpted from TelecomTV Insights Report
 Verizon today announced it has entered into an agreement to purchase an approximate 24.5% stake in AwesomenessTV.
Verizon today announced it has entered into an agreement to purchase an approximate 24.5% stake in AwesomenessTV.
Upon completion of this transaction, the AwesomenessTV multi-platform media company will be valued at approximately $650 million.
DreamWorks Animation, which acquired AwesomenessTV in 2013, will remain the Company’s majority stakeholder with an approximate 51% ownership of outstanding shares, while Hearst will own the remaining 24.5%.
Brian Robbins, AwesomenessTV Founder and CEO, and Brett Bouttier, AwesomenessTV’s President, will continue to lead the company.
In addition to its equity investment, Verizon will enter into an agreement with AwesomenessTV to create a first-of-its-kind premium short-form mobile video service featuring leading talent in front of and behind the camera.
The new service will operate as a new and independent brand, and feature premium transactional content for a variety of audiences on par with the highest-end content seen on television today… Read More
Flash Products Fastest Growing in NetApp History
Excerpted from ETCIO Report by Sneha Jha
 Sneha Jha caught up with Lee Caswell, EVP Product, Solution & Services Marketing, NetApp during his recent visit to India.
Sneha Jha caught up with Lee Caswell, EVP Product, Solution & Services Marketing, NetApp during his recent visit to India.
And here’s what he had to say about the state of storage in the enterprise, the roadmap for NetApp and its growth opportunities in India.
“It’s a very interesting time in the storage industry,” quipped Caswell. With the Dell and EMC merger, Caswell believes that there is a great future for a standalone storage company like NetApp.
With new technologies constantly stretching the contours of the IT landscape, storage is very rich in value today. NetApp is a company in transition, operating in an industry that is in a flux.
Q: So in order to adapt to the IT landscape that is shifting dramatically, how have you changed the portfolio of technologies you offer customers, the way you bring those capabilities to market and the ecosystem of partnerships that you are developing? A: There are two major innovations happening – flash and cloud.
We are partnering with service provider companies all the way to cloud companies. We have a strategy called the Data Fabric… Read More
Verizon: Internet of Things Goes Mainstream
Excerpted from TelecomTV Insights Report
 With an addressable market that includes more than 150 million cars that are not currently connected, over 300 million utility meters, nearly 1 million vineyard acres, and 45 million people sharing goods and services in the US alone, the Internet of Things (IoT) is now mainstream according to a new report released today by Verizon.
With an addressable market that includes more than 150 million cars that are not currently connected, over 300 million utility meters, nearly 1 million vineyard acres, and 45 million people sharing goods and services in the US alone, the Internet of Things (IoT) is now mainstream according to a new report released today by Verizon.
Titled “State of the Market: Internet of Things 2016,” the report includes insights from an Oxford Economics study commissioned by Verizon among other new findings.
Throughout 2016 and beyond, Verizon’s experts say that IoT will continue to be a revenue driver for businesses both large and small due to the confluence of five macrotrends:
Consumers appreciate their smartphones, but in an IoT-enabled world, they are starting to understand and expect that their phones can do more.
In 3 to 5 years, average consumers will experience a much higher level of automation in their daily lives thanks largely to the ability to engage with IoT applications through a more simplified interface.
In fact, 81 percent of IoT adopters in the public sector believe their citizens expect them to offer enhanced services from data and IoT… Read More
Internet-Connected TVs Reach Age of Majority
Excerpted from TWICE Report by Joseph Palenchar
 Sixty percent of people ages 12 and older live in a household with an Internet-connected TV, up from 58 percent in a year-ago survey and 51 percent in a 2014 survey.
Sixty percent of people ages 12 and older live in a household with an Internet-connected TV, up from 58 percent in a year-ago survey and 51 percent in a 2014 survey.
That’s according to the Infinite Dial survey conducted in January and February by Edison Research and Triton Digital, a provider of online advertising technology.
The Internet-connected TVs include smart TVs and other TVs connected to the Internet via Internet-connected game consoles or such set-top boxes (STBs) as Apple TV and Amazon Fire.
Also among the respondents, 51 percent live in a household with one or more of the following unlimited video-subscription services: Netflix, Amazon Prime, and Hulu.
Netflix, however, enjoys the highest penetration. Forty-three percent of people ages 12 and older have a Netflix subscription in the household, followed by Amazon Prime at 22 percent and Hulu at 9 percent.
A total of 37 percent of the surveyed population streams on-demand video on a weekly basis from one of the three providers, again with Netflix at the top. Thirty-three percent said they stream Netflix on a weekly basis… Read More
FCC Privacy Proposal Shortchanges Consumers
Excerpted from USTelecom Press Announcement
 Background: Today the Federal Communications Commission (FCC) voted 3-2 for a proposal creating new privacy rules for broadband Internet service providers.
Background: Today the Federal Communications Commission (FCC) voted 3-2 for a proposal creating new privacy rules for broadband Internet service providers.
The following statement should be attributed to USTelecom President Walter McCormick:
“While we support the effort to ensure strong consumer privacy protections, rules should be consistent across the broadband economy.
Today’s proposal falls short by espousing tentative conclusions that are not in sync with the framework that has applied for years and is incorporated into a proposal presented to the commission by USTelecom and other major trade associations.
The FCC’s proposed tentative conclusions, if adopted, will create a morass of regulations in the Internet privacy space and fail to provide a platform allowing consumers to count on privacy rules that are evenly applied across the Internet economy.
We urge the commission to take the time to consider the systems at work in the larger Internet ecosystem, and implement rules that are consistent with the Federal Trade Commission’s longstanding and effective approach to privacy that has applied across the Internet… Read More
MIT Develops Accurate System for Tracking People via WiFi
Excerpted from Softpedia Report by Catalin Cimpanu
 MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) has created a new system called Chronos that can accurately detect the position of a person or object inside a room within tens of centimeters, using WiFi signals only.
MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) has created a new system called Chronos that can accurately detect the position of a person or object inside a room within tens of centimeters, using WiFi signals only.
Chronos works without the aid of any secondary sensors, only using a technology called time-of-flight calculation, which measures the time it takes data to travel from the WiFi access point to the user’s device.
Chronos is more accurate than current triangulation-based systems.
According to MIT, this new system is 20 times more accurate than the current WiFi-based tracking systems.
Researchers say that Chronos was 94 percent successful in detecting which room a person is currently in, and 97 percent successful in determining if a shop’s customer was inside or outside the store.
Researchers say that coffee shops and stores can benefit from something like Chronos because it will allow them to use passwordless WiFi connections for their clients, preventing nearby users from loitering on their WiFi.
Additionally, since Chronos can locate persons within tens of centimeters, researchers say that they could be mounted on drones… Read More
Linux Founder Torvalds on IoT: Security Second Fiddle
Excerpted from Report ZDNet by Steven Kaughan-Nichols
 For the first time, Linus Torvalds has spoken at an embedded Linux conference, the Linux Foundation’s 2016 Embedded Linux Conference & OpenIoT Summit.
For the first time, Linus Torvalds has spoken at an embedded Linux conference, the Linux Foundation’s 2016 Embedded Linux Conference & OpenIoT Summit.
It’s not that embedded Linux hasn’t been important before. Your DVRs and Wi-Fi routers almost certainly run Linux. What has changed is that the Internet of Things (IoT) is transforming embedded Linux from being a topic only programmers could love to one everyone will be using soon.
This development caught Torvalds, Linux’s founder, by surprise — 15 years ago. “I never see the entire chain running Linux. Twenty five years ago I started Linux wanting a workstation. From that to a server wasn’t a surprise. There was no single point where I was surprised, but 15 years ago I started seeing these odd, embedded systems. The first one that really caught my eye was a gas pump running Linux.”
Today, Torvalds continued, “Many changes have been invisible. Even I don’t see all the uses of Linux.”
Of course, Linux isn’t the right operating system for all embedded devices. After all, the Linux kernel keeps growing.
Therefore, Torvalds said, “If you’re doing something really tiny, like sensors, you don’t need Linux… Read More
Three Ways to Manage Data Breach Exposure
Excerpted from Becker’s Hospital Review Report by Carrie Pallardy
 The majority of organizations are concerned about the consequences of a large data breach, but just 45 percent believe they have the resources to detect all breaches, according to the “Mitigating the Inevitable: How Organizations Manage Data Breach Exposures” report from id experts and Advisen.
The majority of organizations are concerned about the consequences of a large data breach, but just 45 percent believe they have the resources to detect all breaches, according to the “Mitigating the Inevitable: How Organizations Manage Data Breach Exposures” report from id experts and Advisen.
While cybersecurity strategy is essential to preventing data breaches, healthcare organizations are still likely to suffer a breach at some point.
It is important to have a breach response plan in place to mitigate the consequences of the incident.
Here are three strategies for minimizing the effects of a data breach.
1. Cyber insurance. Cyber insurance can help minimize the financial burden of a large scale breach.
2. Outside legal council or internal resources. Small data breaches that fall below a cyber insurance policy’s deductible can be handled by outside legal counsel or internal resources.
3. Vendor services. There are number of vendor services designed to help healthcare organizations handle the fallout of a breach… Read More
Veriflow Promises to Bulletproof Networks
Excerpted from Network World Report by Ben Kepes
 Veriflow is starting to emerge from stealth and is lifting the covers from its network verification tool.
Veriflow is starting to emerge from stealth and is lifting the covers from its network verification tool.
The company wants to help eliminate its customers’ change-induced outages and breaches and does so by using a mathematical verification approach.
The Veriflow platform promises to ensure network policy correctness and can identify when a change to networking environments will be impactful to the organization – whether that change is caused by intentional changes or external (not to mention internal) sabotage.
The company was created by a team of computer science professors and PhD students in the EnterpriseWorks incubator at the University of Illinois, is backed by New Enterprise Associates (NEA), the National Science Foundation (NSF), and the US Department of Defense (DoD), and is already claiming success in multiple Fortune 500 and government networks.
Interesting the company has raised some initial funding from not only traditional investors but also government agencies including the NSF and the DoD. While the quantum ($2.9 million in total) is small, the strategic investment is telling… Read More
VR in the Clouds: Merging Today’s Hottest Computing Trends
Excerpted from TechSpot Report by Bob O’Donnell
 Two of the hottest technologies in tech today are virtual reality/augmented reality (AR/VR) and cloud computing.
Two of the hottest technologies in tech today are virtual reality/augmented reality (AR/VR) and cloud computing.
Together the two have garnered a good percentage of the attention in both consumer and industry publications, blogs, and websites.
They both also share the appeal of being intriguing new opportunities that each create new kinds of applications and usage models.
But while they’ve been covered at length separately, there hasn’t been much discussion about combining the two.
Of course, the primary reason for this is that there aren’t very many companies trying to actively bring these two technologies directly together.
Virtually all current VR/AR headset designs demand strong local computing and graphics power, and most all cloud computing models are intentionally independent of the display capabilities of a connected client device.
Setting these and other technical challenges aside for the moment—I’ll address them in a bit—the potential possibilities… Read More
Virtual Reality About to Go Mainstream
Excerpted from TechCrunch Report by Tony Scherba
 Technology is surrounding us; its surface is becoming more complex, pliable and familiar to the eye.
Technology is surrounding us; its surface is becoming more complex, pliable and familiar to the eye.
Virtual reality is no longer creeping into the mainstream: It’s leaping.
Just last month, secretive VR startup Magic Leap received more than $793 million in new funding through Google, Qualcomm and others, quickening its progress toward creating seamless experiences in which digital and physical worlds collide.
When MIT Technology Review editor Rachel Metz visited Magic Leap’s headquarters, she discovered a world where crisp virtual characters were already roaming the halls, waiting for a device to be perfected that will bring them into the public eye.
Not to be outdone, Microsoft revealed its plans to release a sleek-looking augmented reality headset this year, too.
HoloLens will allow users to interact with holographic surroundings and characters, and Microsoft partners Volvo, NASA and Trimble are already testing it in the business world.
Though the industry is giddy with the potential of VR, the consumer is still a step away from being able to enjoy a virtual experience… Read More
Coming Events of Interest
Delivery of Things World — April 25th-26th in Berlin, Germany. DevOps specialists, continuous development strategists, architect newbies, development geeks, and cloud geniuses from across the spectrum of DevOps transformation come together at this stimulating and innovative event.
DataCloud Europe 2016 — June 8th-9th in Monte Carlo, Monaco. The 2016 conference will focus on cloud computing advances and changes in data management, with a stellar line-up of speakers including global infrastructure leaders and subject matter experts.
Cloud and DevOps World Forum 2016 — June 21st-22nd in London, England. Now in its eighth year, C&DWF is firmly established as the leading content-led exhibition for the European Cloud and DevOps community and the premiere meeting place for CIOs.
2016 Creative Storage Conference — June 23rd in Culver Cirty, CA. The tenth annual CS will bring together digital storage providers, equipment manufacturers, software distributors, and professional media and entertainment end-users to explore the conference theme “The Art of Storage.”
Security of Things World — June 27th-28th in Berlin, Germany. Topics include securing cyber physical systems for IoT, expanding IT security with intelligence-led ops, business continuity management considerations, data privacy in an interconnected world, and security strategies.
Mobile World Congress Shanghai — June 29th – July 1st in Shanghai, China. MWC Shanghai is a very unique gathering that brings together industry participants ranging from C-Level mobile executives to end-user consumers passionate about mobile.
Industry of Things World Europe — September 19th-20th in Berlin, Germany. IoT business models, new IoT markets and strategies, product lifecycle management, next generation data handling and value assessment, IoT organizational impacts, and IoT security issues.
