In This Issue
- Cloud Now Mainstream
- Salesforce & Twitter?
- Cloud Security Scores
- Report from the CEO
- Cyber Alert: Scrutiny
- Smart-Home Concern
- Self-Driving Cars List
- Cellphone Alerts Used
- IoT, Edge, Big Data
- Guccifer 2.0 DNC Docs
- Team8’s New Startup
- Outdated Fed Systems
- New Cloud Landscape
- DHS Chf on Vote Hack
- FTC vs Ransomware
- EU Unifies Digital Mkt
- Coming DCIA Events
Official: Cloud Computing Is Now Mainstream
Excerpted from The Register Report by Drew Cullen

Cloud computing is so mainstream these days that maybe it should just be called “computing.”
That’s what an IDC survey of 6,100 organizations in 31 countries, released today, indicates, with 68 per cent of respondents using public, private, or hybrid cloud in their IT mix.
This is a 60 per cent jump from 42 per cent of respondents doing cloud in 2015.
IDC reckons that just three per cent of the organizations have deploying cloud-optimized strategies resulting in “superior business outcomes.”
And of this select “cloud-advanced” bunch, ninety-five per cent have built a hybrid infrastructure that uses “multiple private and public clouds based on economics, location and governance policies.”
Globally the most advanced companies attribute $3 million in additional revenues and $1 million in cost savings to their cloud adoption, although admittedly this may be self-reporting, self-back-patting.
Some more tidbits for you: almost a third (29 per cent) of cloud adopters are using cloud-based Internet of Things (IoT) applications… Read More
Salesforce Considers Takeover of Twitter
Excerpted from Wall St. Journal Report by Dana Mattioli and Yoree Koh

Twitter may be contemplating a future in the hands of an acquirer after a year-long effort to sharpen its focus and ignite user growth has fallen short.
Salesforce is considering a takeover of the social media company, according to people familiar with the matter.
The exploration is in early stages, one of the people said, and might not lead to a deal.
Shares of Twitter rose 21% to $22.62 on Friday after CNBC reported talks of a possible sale.
Before Friday, the stock had fallen 30% over the past year and its market value was about $13 billion. Its all-time high of $40.7 billion came in December 2013.
The sales talks shift the conversation around Twitter from constant business turmoil to the strategic and financial value it could bring to any number of Silicon Valley giants.
Twitter is approaching the three-year anniversary of its flashy IPO, when its stock shot up 73% as investors crowned the company a social media star rivaling Alphabet’s Google and Facebook for advertising dollars… Read More
Security Scores for Cloud Companies on the Way
Excerpted from InfoWorld Report by Fahmida Rashid

Compromised vendor systems have led to several major data breaches recently.
And sometimes, vendors get breached because of a partner’s lax security.
A group of tech companies led by Uber are banding together as the Vendor Security Alliance to prevent more of these types of attacks.
The newly formed coalition, which includes founding member companies AirBnb, Atlassian, Docker, Dropbox, GoDaddy, Palantir, Square, Twitter, and Uber, would streamline the security vetting process for third-party providers so that businesses will know the security mindset of the vendors they’re partnering with.
An organization’s security depends on what the partners, and the partners of those partners, are doing, but strengthening that relationship is a challenge.
“It’s no longer enough to embrace these cybersecurity practices at your business alone — ensuring the companies you work with as vendors also have the most secure Internet practices is just as important,” wrote Ken Baylor, Uber’s head of compliance… Read More
Report from DCIA CEO Marty Lafferty

We commend The US House of Representatives for passing legislation this week that will task the Small Business Administration (SBA) with assisting small businesses in improving their preparedness against cyber-threats.
The Improving Small Business Cyber Security Act will increase the cybersecurity offerings of small-business development centers (SMBCs) including awareness building, technical training, and access to expertise in this space.
HR 5064 was sponsored by Congressman Richard Hanna (R-NY), Chairman of the House Small Business Committee’s contracting and workforce subcommittee, and co-sponsored by Derek Kilmer (D-WA).
Small Business Committee Chairman Steve Chabot (R-OH) and ranking member Nydia Velazquez (D-NY) joined Congressman Hanna and Kilmer in co-sponsoring the bill.
Under the new measure, the SBA will be charged with expanding cybersecurity programs through the SMBCs in accordance with a small-business security strategy to be developed with the Department of Homeland Security (DHS).
The co-sponsors explained that their bill addresses urgent concerns for small businesses that are the target of three out of every five cyberattacks.
“Hackers often view small businesses as easier targets because many lack adequate protections to avoid intrusions and lack incident response plans.”
Indeed, information security has posed challenges for small businesses for a number of years, and the SBA itself has endured cybersecurity failings and weaknesses as detailed in a Government Accountability Office (GAO) report published last year.
HR 5064 not only addresses the expertise gap for small businesses, but also responds to complaints within the small-business community that recent cybersecurity laws have primarily helped large businesses.
In the DCIA’s view, this bipartisan, common-sense legislation should move ahead swiftly in a companion bill through the Senate.
It will provide real value in helping small businesses access tools they need to protect themselves and their customers from cyberattacks. Share wisely, and take care.
Cyber Alert: You Don’t Need a Breach to Face Regulatory Scrutiny

Class action lawsuits from consumers, shareholders, and financial institutions are now not an exception, but are increasingly becoming expected.
Similarly, since the Federal Trade Commission (FTC) began focusing on data security nearly 15 years ago, it has engaged in enforcement actions against numerous companies that were subject to a data breach or other security compromise.
State attorneys general have also joined the fray. Notably, these consequences are post hoc, in that they stem from the actual occurrence of a security incident that results in data compromise, loss or exposure.
Recently, however, there has been an increase in regulatory and litigation actions based not on breaches or security incidents but on identified security vulnerabilities alone that, if exploited, could result in data compromise, leakage or exposure and so pose a potential risk of harm, whether economic or otherwise, to customers and consumers. One possible explanation for this gradual change is that vulnerabilities are increasingly being brought to light through various means… Read More
Security Is Consumers’ Chief Smart-Home Concern
Excerpted from TWICE Report by Alan Wolf

With data breaches and hacked email servers making headlines, it should come as no surprise that personal data security is the No. 1 concern for consumers when buying connected devices.
According to an exclusive new survey by TWICE and research partner Creative Channel Services (CCS), fully 43 percent of shoppers queried in stores cited security as their top IoT concern, presenting a potential roadblock to smart-home growth.
Indeed, consumers said privacy issues were more pressing than price, which was cited by less than a quarter as their major category concern (see charts, below).
Moreover, only 5 percent of respondents said they were “extremely concerned” by the complexity of installation, which is either a vote of confidence for the custom integration community or a testament to plug-and-play.
The survey also showed that smart-tech is already fairly well established — at least among consumers surveyed within CE stores or departments — with 79 percent reporting ownership of a smart device. Thermostats make up the majority of products owned (38 percent), followed by home security (19 percent) and lighting (17 percent).
As to where they purchased or plan to buy their connected gear, nearly half (49 percent) cited CE specialty retailers… Read More
The 15-Point Federal Checklist for Self-Driving Cars
Excerpted from NY Times Report by Cecilia Kang

Federal Regulators announced their first safety checklist ever for semi-autonomous and driverless cars this week.
In the guidelines, the United States Department of Transportation urged automakers and tech companies to prove that their semi-autonomous and autonomous vehicles could meet a 15-point list of safety expectations before the autos hit the road.
We broke down the 15 points:
DATA SHARING These giant computers on wheels collect piles of driving data. Carmakers should store that data and share it with regulators who can use the information to reconstruct what went wrong in a crash or system breakdown.
PRIVACY Car owners should have a clear understanding of what kind of data is being collected by the vehicles. They should also be able to reject any collection of personal information such as on biometrics or driver behavior.
SYSTEM SAFETY The cars must be engineered to respond safely to software malfunctions, near crashes, loss of traction and other risks… Read More
Cellphone Alerts Used to Search for Bombing Suspect
Excerpted from NY Times Report by J. David Goodman and David Gelles
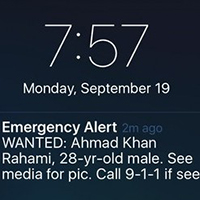
Across New York City, cellphones blared on Monday morning with the dissonant but familiar tone of an emergency alert, typically used for weather-related advisories or abducted children. But this was different.
For what is believed to be the first time, the nation’s Wireless Emergency Alerts system was deployed as an electronic wanted poster, identifying a 28-year-old man sought in connection with the bombings in Manhattan and New Jersey over the weekend.
Suddenly, from commuter trains to the sidewalks of the city, millions were enlisted in the manhunt.
The message was simple: “WANTED: Ahmad Khan Rahami, 28-yr-old male. See media for pic. Call 9-1-1 if seen.”
In an instant, the reach and ubiquity of law enforcement in an age of terrorism and digital technology became apparent.
The system, in place for several years, has been used to assist the authorities in moments of chaos and potential danger: after the Boston bombing in 2013, when the Boston suspects were still at large, and last month in Los Angeles, during an active shooter scare at the airport… Read More
IoT, Edge, Big Data – Next Wave in Data Center Innovation
Excerpted from PCQuest Report by Ashok Pandey
 The next wave of data center improvement will be driven by the need for connectivity and using technology to enable data center managers to effectively manage inherently complex environments.
The next wave of data center improvement will be driven by the need for connectivity and using technology to enable data center managers to effectively manage inherently complex environments.
While in the past the focus was on improving the management of one facility, the emerging ecosystem of hybrid cloud computing has shifted the management of the infrastructure into an exercise of managing multiple facilities with virtualized environments.
Over the past few years, the Internet of Things (IoT) has been a pretty hot topic.
It has many definitions.
Gartner describes IOT as the network of physical objects that contain embedded technology to communicate and sense or interact with their internal states or the external environment.
IDC defines the IoT as a network of networks of uniquely identifiable endpoints (or “things”) that communicate without human interaction using IP connectivity… Read More
Guccifer 2.0 Drops More DNC Docs
Excerpted from Politico Report by Cory Bennett

The hacker persona Guccifer 2.0 has released a new trove of documents that allegedly reveal more information about the Democratic National Committee’s (DNC) finances and personal information on Democratic donors, as well as details about the DNC’s network infrastructure.
The cache also includes purported memos on tech initiatives from Democratic vice presidential nominee Tim Kaine’s time as governor of Virginia, and some years-old missives on redistricting efforts and DNC donor outreach strategy.
DNC interim chair Donna Brazile immediately tied the leak to GOP presidential nominee Donald Trump.
“There’s one person who stands to benefit from these criminal acts, and that’s Donald Trump,” she said in a statement Tuesday night, adding that Trump has “embraced” Russian President Vladimir Putin and “publicly encouraged further Russian espionage to help his campaign.”
Trump claims his remarks were meant in jest and that he has no knowledge of who hacked the DNC.
Brazile also urged people to use “extreme caution” in accessing the documents, cautioning they may contain malicious espionage software… Read More
Team8 Unveils Critical Infrastructure Cybersecurity Startup
Excerpted from Geektime Report by Gabriel Avner

In a massive funding announcement that marks their debut after a long period of stealth mode, Team8’s latest startup Claroty released today that they have raised $32 million in a combined Series A and B round.
The primary backers of the new company are Bessemer Venture Partners, Eric Schmidt’s Innovation Endeavors, Marker, ICV, Red Dot Capital Partners, and Mitsui & CO., Ltd. David Cowan, a partner at Bessemer Venture Partners, has joined Claroty’s board as its director.
Co-founded in 2014 by CEO Amir Zilberstein, Chief Business Development Officer Galina Antova and CTO Benny Porat.
Each of the founding team members come to this project with extensive backgrounds in the field. Zilberstein was a co-founder at Waterfall Security that also dealt with critical infrastructure and Antova has served as Siemens’ Global Head of Industrial Security Services.
Both Zilberstein and Porat led research teams in the IDF’s cyber core, an organization which has had its fair share of practice learning how to penetrate and defend these kinds of systems.
Nadav Zafrir, Team8 Co-Founder and CEO tells Geektime that they looked to tackle critical infrastructure as their next project… Read More
Panel Approves Bill to Replace Outdated Federal Systems
Excerpted from The Hill Report by Joe Uchill
Until Tuesday when the bills merged, Congressmen Will Hurd (R-TX) and Steny Hoyer (D-MD) had rival plans to modernize the government’s outdated communications systems.
Two days later, the new Modernizing Government Technology Act has already left committee.
“We did something today that was a big deal,” Hurd said at a conference for the Internet Security Alliance after the Thursday markup.
The bill combines Hoyer’s idea, a centralized loan program repaid through the cost savings agencies would achieve by using newer, more efficient technology, with a direct funding approach advocated by Hurd.
Agencies will reinvest the savings realized by using the direct funds to purchase more new technology.
Federal Chief Information Officer Tony Scott has advocated both ideas, saying modernizing infrastructure is not only cheaper in the long run, but also more secure from hackers.
“Not once did my constituents see a campaign ad about IT procurement… Read More
Enterprise Demands Shift Cloud Computing Landscape
Excerpted from InfoWorld Report by Raejeanne Skillern
 The initiatives put forth today by business leaders require enterprises to leverage advanced technology to deliver new and superior business outcomes.
The initiatives put forth today by business leaders require enterprises to leverage advanced technology to deliver new and superior business outcomes.
While public and private clouds are growing, enterprises are increasingly adopting a hybrid strategy leveraging public cloud to gain instant access to on-demand capacity and on premises, private cloud for core IP and their stable workloads.
This approach gives IT managers the ability to manage fluctuations in their business cycle, reduce capital costs and free up time and resources needed to develop new applications.
A recent Intel study showed that about 45% of current public cloud usage by businesses is driven by new, cloud-enabled workloads.
These are workloads such as powerful cloud-based HPC solutions that some IT organizations wouldn’t have done on premise (due to capital outlay and complexity) but can with public cloud ease of access and cost.
Cloud installations are based on maintaining a reliable, secure, and high performing environment essential to enterprise success… Read More
DHS Chief: ‘Very Difficult’ for Hackers to Skew Vote
Excerpted from The Hill Report by Julian Hattern
 Department of Homeland Security (DHS) Secretary Jeh Johnson on Thursday downplayed concerns about malicious hackers influencing US elections amid rising fears about foreign actors trying to wreak havoc on Election Day.
Department of Homeland Security (DHS) Secretary Jeh Johnson on Thursday downplayed concerns about malicious hackers influencing US elections amid rising fears about foreign actors trying to wreak havoc on Election Day.
While hackers in the US or abroad might be able to steal data from individual election officials, Johnson said at an event hosted by The Atlantic, they would not be able to skew the overall vote count.
“It would be very difficult through any sort of cyber intrusion to alter the ballot count, simply because it is so decentralized and so vast,” he said, noting the series of state, local, and county systems involved in running elections. “It would be very difficult to alter the count.”
Johnson was responding to new fears about hackers from Russia, in particular, whom intelligence officials are reportedly investigating over suspected efforts to disrupt the election.
The FBI is separately investigating hacks at election sites in Arizona and Illinois, and Russia is believed to be behind this summer’s release of massive data files from the Democratic National Committee.
Despite Johnson’s claims, however, hackers would not necessarily need to alter a particular vote count in order to inject chaos… Read More
FTC Focuses on Combating Ransomware
Excerpted from CIO Report by Kenneth Corbin
 Ransomware, where a hacker commandeers a user’s computer files and threatens to permanently delete them unless an extortion payment is made, is on a sharp uptick and now ranks “among the most troubling cyberthreats,” the head of the Federal Trade Commission (FTC) is warning.
Ransomware, where a hacker commandeers a user’s computer files and threatens to permanently delete them unless an extortion payment is made, is on a sharp uptick and now ranks “among the most troubling cyberthreats,” the head of the Federal Trade Commission (FTC) is warning.
FTC Chair Edith Ramirez addressed the issue at a recent forum that the agency convened to examine the spread of ransomware and explore strategies to combat the crime.
“The spate of ransomware incidents are escalating at an alarming rate,” Ramirez says, citing an estimate from the Department of Justice (DoJ) that incidents of ransomware, now averaging some 4,000 a day, have increased 300 percent in the past year.
“The financial motivation for ransomware attacks suggests that the threat is unlikely to go away any time soon,” she says, warning businesses to step up their own defenses to ensure that they are protecting their users from online scammers.
The agency has already brought dozens of enforcement actions against companies for failing to adopt what it considers reasonable security protections… Read More
EU Rules Look to Unify Digital Market
Excerpted from NY Times Report by Mark Scott
 Google may have to pay publishers for their content. Facebook might, too. WhatsApp could have to follow tougher telecom standards.
Google may have to pay publishers for their content. Facebook might, too. WhatsApp could have to follow tougher telecom standards.
A new set of rules, expected to be unveiled by European Union (EU) officials on Wednesday, is likely to put new pressure on American tech companies.
Europe calls it consumer protection. Silicon Valley calls it protectionism.
In some ways, they are both right.
In a decade of sluggish growth, local lawmakers assert that these proposed changes will bring together the region’s national economies into a so-called single digital market.
The aim? To give the bloc’s roughly 500 million consumers unfettered access to services like movie streaming, online shopping and cloud computing, no matter where they live.
At the same time, the proposals would force some of the world’s largest tech companies to comply with stringent rules… Read More
Coming Events of Interest
EuroCloud Forum — October 5th-6th in Bucharest, Romania. The seventh annual EuroCloud Congress will be held for the first time in Romania. With the theme “Creating New Frontiers in European Cloud,” it will be the sector’s largest forum on the future of cloud in Europe.
Internet & Mobile World 2016 — October 5th-6th in Bucharest, Romania. The largest business-to-business (B2B) expo-conference for information technology (IT) and digital solutions in Central & Eastern Europe (CEE).
Security of Things World USA — November 3rd-4th in San Diego, CA. SoTWUSA has been designed to help you find pragmatic solutions to the most common security threats facing the IoT.
Rethink! Cloudonomic Minds — November 21st-22nd in London, England. R!CM will cover how IoT is impacting cloud strategies and how to take advantage of these two key technology trends.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
CES 2017 — January 5th-8th in Las Vegas, NV. More than 3,800 exhibiting companies showcasing innovation across 2.4 million net square feet, representing 24 product categories.
Industry of Things World USA — February 20th-21st in San Diego, CA. Global leaders will gather to focus on monetization of the Internet of Things (IoT) in an industrial setting.
