In This Issue
- CEO Revived NetApp
- Telefonica Open Cloud
- Fed Cyber Incidents
- Report from the CEO
- LOCK DOWN LOGINS!
- Body-Based Transmit
- Dem Cellphone Hack
- Unified Cybersecurity
- NIST Assessment Tool
- Cyber Insurance Bill
- Regs Remain Murky
- States Breach Laws
- McCaul: Decryption
- Blockchain Caucus
- Enterprise Storage
- NetApp HD Program
- Coming DCIA Events
New CEO Revived NetApp without Upsetting Culture
Excerpted from eWeek Report by Chris Preimesberger

It wasn’t connecting often enough in clutch sales situations, even though in seasons past it was known for getting big hits with key products at the right times in the major-league IT marketplace.
Like a favorite hometown ball club, the Fortune 500 company has its diehard fan base, the flag-waving customers who bank on it to come through with wins in the form of products that it knows and trusts.
That fan base is now starting to see a rebirth of what was once known as a “nice little file server company” that grew into the No. 2 network-attached storage (NAS) provider in the world behind EMC.
Change usually does not come without discomfort.
Fifteen months ago, on June 1, 2015, NetApp’s board named Executive Vice President George Kurian as its interim CEO, replacing respected longtime storage veteran Tom Georgens.
Changes in several of NetApp’s other leadership positions followed… Read More
Telefonica Launches Open Cloud in Brazil, Mexico, Chile

Telefonica Business Solutions, a leading provider of a wide range of comprehensive communication solutions for the B2B market, and Huawei, a leading global information and communications technology (ICT) solution provider, have launched the Open Cloud and Cloud Server services in Chile, Brazil, and Mexico.
This launch is carried out in the context of the comprehensive partnership agreement established between the two companies to drive the migration of customers’ traditional IT services to the cloud.
Open Cloud is a public cloud service based on OpenStack technology and hosted in Telefonica‘s data centers in Chile, Brazil, and Mexico.
The service represents Telefonica’s commitment to an open and secure cloud and provides a broad range of services ranging from computing, storage, networks, and databases to more advanced application development, security, and analysis services.
One of the main advantages of Open Cloud is the ability to connect to customers’ private networks, as well as the connectivity to additional Telefonica’s data center services… Read More
Fed Cyber Incidents Up 1,300% from 2006 to 2015
Excerpted from Network World Report by Michael Cooney
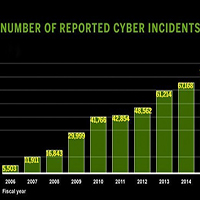
That’s one amazingly scary number: Since 2006 cyber incidents involving the Federal government have grown 1,300%.
Another Government Accountability Office report on Federal cybersecurity out this week offers little in the way of optimism for the cyber-safeguard of the massive resources the government has control over.
Federal information systems and networks are inherently at risk.
They are highly complex and dynamic, technologically diverse, and often geographically dispersed.
This complexity increases the difficulty in identifying, managing, and protecting the myriad of operating systems, applications, and devices comprising the systems and networks.
Compounding the risk, systems used by federal agencies are often riddled with security vulnerabilities – both known and unknown.
For example, the national vulnerability database maintained by the Mitre Corporation has identified 78,907 publicly known cybersecurity vulnerabilities and exposures as of September 15, 2016, with more being added each day,” the GAO wrote… Read More
Report from DCIA CEO Marty Lafferty
 On Monday evening, Hillary Clinton and Donald Trump met at Hoftra University in the first of three US Presidential candidate debates.
On Monday evening, Hillary Clinton and Donald Trump met at Hoftra University in the first of three US Presidential candidate debates.
While our industry did not receive the attention it deserves given the relative importance of distributed computing to economic growth and national security, cybersecurity at least was briefly discussed.
NBC moderator Lester Holt stated, “Our institutions are under cyberattack, and our secrets are being stolen;” and then asked, “Who’s behind it? And how do we fight it?”
Clinton responded first, acknowledging that, “Cybersecurity… will be one of the biggest challenges facing the next President,” and noting there are “two different kinds of adversaries… independent hacking groups and… increasingly… states.”
She went on to echo the Obama administration’s identification of Russia most recently as using “cyberattacks against all kinds of organizations in our country,” and to decry opponent Trump for being “very praiseworthy of Vladimir Putin.”
She added, “We need to make it very clear – whether it’s Russia, China, Iran, or anybody else – the United States has much greater capacity; and we are not going to sit idly by and permit state actors to go after our information, our private-sector information or our public-sector information.”
And then chastised Trump for “publicly invit(ing) Putin to hack into Americans. That is just unacceptable.”
Trump responded, casting doubt on certain culpability for the recent DNC hacks, saying, “It could be Russia, but it could also be China; it could also be lots of other people; it also could be somebody sitting on their bed that weighs 400 pounds,” noting the revelations showed that, “Bernie Sanders was taken advantage of.”
He added that although the Internet is largely an American invention, “When you look at what ISIS is doing with the Internet, they’re beating us at our own game.”
“So we have to get very, very tough on cyber and cyber warfare. It is – it is a huge problem… The security aspect of cyber is very, very tough. And maybe it’s hardly doable… But we are not doing the job we should be doing… We have so many things that we have to do better, Lester, and certainly cyber is one of them.”
In the DCIA’s view, neither candidate demonstrated a depth of understanding nor indicated that she or he has prepared a cybersecurity agenda to expand and improve upon the work begun in this space by President Obama.
Neither specified an action plan to address the very serious problem raised by Holt, and we urge industry participants, who realize what’s at stake, to press the parties to offer more substantive technology policies in the final month leading to the election. Share wisely, and take care.
White House to Public: LOCK DOWN YOUR LOGIN!
Excerpted from FedScoop Report by Shaun Waterman

The Obama administration and a bevy of nonprofit organizations, technology firms, and financial services companies joined forces Wednesday in a public campaign to get Americans to stop relying on passwords and use stronger methods of identity authentication.
“Your usernames and passwords are not enough to keep your accounts secure,” states the campaign website, which went live Wednesday in the run-up to the 13th annual National Cybersecurity Awareness Month.
“Luckily,” the website continues, “there’s a simple and quick way to put you in control of your personal information and keep your key accounts like email, banking and social media safer – it’s called strong authentication.”
Strong authentication, also called multi-factor or second-factor authentication, has long been advocated by security experts as an alternative or addition to passwords.
Unfortunately, as the campaign factsheet notes, 72 percent of Americans believe their online accounts are secure with just a password and login – something that repeated breaches of password data, like the one revealed last week by Yahoo, have shown to be untrue. Under the slogan “Lock down your login” the campaign advocates one or more of three authentication technologies… Read More
Body-Based Transmission Keeps Passwords Secure
Excerpted from New Atlas Report by Michael Irving
 Trying to remember a pile of passwords is a hassle many people get around by just using the same codes for everything, but that’s hardly secure.
Trying to remember a pile of passwords is a hassle many people get around by just using the same codes for everything, but that’s hardly secure.
Smartphone manufacturers have embraced sensors like fingerprint and iris scanners, and thanks to a new system out of the University of Washington (UW), that security and ease of use could soon be extended to other devices, by relaying a signal from a fingerprint scanner through the body to a receiving device in direct contact with the user.
Like similar systems that have used magnetic fields to transmit data through the body, the UW team’s technique is designed as an alternative to sending signals wirelessly through the air via Bluetooth or Wi-Fi.
The advantage of this, the researchers say, is that it’s much harder for hackers to intercept the signal, since they’d have to be physically touching the person.
“Let’s say I want to open a door using an electronic smart lock,” says co-lead author, Merhdad Hessar.
“I can touch the doorknob and touch the fingerprint sensor on my phone and transmit my secret credentials… Read More
Dem Officials’ Cellphones Hacked
Excerpted from The Hill Report by Joe Uchill

The FBI is investigating the hacked cellphones of several Democratic Party officials with the belief the attacks are connected to a spate of breaches at party networks and under the assumption that Russia is behind the hacking, Reuters reports:
“The FBI is investigating suspected attempts to hack mobile phones used by Democratic Party officials as recently as the past month, four people with direct knowledge of the attack and the investigation told Reuters.
The revelation underscores the widening scope of the US criminal inquiry into cyber attacks on Democratic Party organizations, including the presidential campaign of its candidate, former US Secretary of State Hillary Clinton.
US officials have said they believe those attacks were orchestrated by hackers backed by the Russian government, possibly to disrupt the November 8th election in which Clinton faces Republican Party candidate Donald Trump.
Russia has dismissed allegations it was involved in cyberattacks on the organizations.”
The phones, says the report, were hacked within “the past month or so.”
That would put the timing of the breach soon after hackers, widely suspected to be Russian intelligence, were booted… Read More
Panelists Stress Unified Cybersecurity Plan
Excerpted from Insurance Journal Report by Elizabeth Blosfield
As cyberattacks become a growing concern with advances in technology, firms should be working to establish a cybersecurity plan that is cohesive across business operations to effectively reduce damage and cyber insurance claims, according to panelists at the 2016 Professional Liability Underwriting Society (PLUS) Cyber Liability Symposium held Tuesday at the Hilton Midtown in New York City.
“That is the biggest barrier to quickly acting when you have a risk event,” said panelist Cari Toneck, Chief Compliance and Risk Officer at Methodist Hospital of Southern California.
“You need to think of cybersecurity like disaster management – similar to your plan for an event like hurricane Katrina – where everybody is on the same page.
The key players in an organization need to immediately get together to respond to an event in a cohesive fashion and look at cyber risk as something that has the potential to domino into other claims and exposure.”
Toneck pointed to one example of a local hospital in California that recently suffered a ransomware attack, where attackers demand ransom payments in exchange for the return of stolen data… Read More
NIST Cybersecurity Self-Assessment Tool
Excerpted from FedScoop Report by Shaun Waterman
 The National Institute for Standards and Technology (NIST) has published a draft questionnaire that companies and other organizations can use to assess their cybersecurity “maturity” – a response, NIST says, to demand from the private sector.
The National Institute for Standards and Technology (NIST) has published a draft questionnaire that companies and other organizations can use to assess their cybersecurity “maturity” – a response, NIST says, to demand from the private sector.
Boosters say the document will help specialists explain the importance of cybersecurity to the company’s bottom line – the “holy grail” of business cybersecurity.
But some critics have questioned how useful it will be to smaller companies.
The Baldrige Cybersecurity Excellence Builder is one of a number of tools NIST offers that are named for the Reagan-era Commerce Secretary Malcolm Baldrige, credited as one of the leaders of the quality management movement in the 1980s.
It’s designed to walk organizations through the process of figuring out “how to integrate cybersecurity risk management into larger enterprise business practices and processes,” Matthew Barrett explained to FedScoop.
Barrett is the Program Manager for the NIST Cybersecurity Framework – a document that catalogs the five areas of cybersecurity every company needs to know: identify, protect, detect, respond, and recover… Read More
New Bill Would Give Tax Credits for Cyber Insurance
Excerpted from The Hill Report by Joe Uchill

Congressman Ed Perlmutter (D-CO) introduced legislation this month to subsidize data breach insurance for businesses while encouraging practices that would keep them from ever having to use it.
The Data Breach Insurance Act would offer a tax deduction of 15 percent of the cost of breach insurance.
Perlmutter said he has received positive feedback for the bill from both legislators and stakeholders.
“Using an incentive approach rather than a mandate gives this a much better chance of succeeding, both in the marketplace and in the Congress,” he said.
The bill, he said, would promote breach protection for consumers on both the “front and back end.” The insurance rebate would only apply to policies that required companies to enact good cybersecurity practices, like those in the National Institute of Standards and Technology (NIST) Cybersecurity Framework.
The NIST framework was explicitly developed as guidelines for good cybersecurity and was not intended to be used in regulations. It says its suggestions should be customized for the unique needs of any user… Read More
Regs for Disclosing Data Breaches Remain Murky
Excerpted from The Street Report by Ellen Chang
The breach at Yahoo is likely the largest hacking incident to date to occur, as the company confirmed last week that it affected 500 million users in 2014, but other infiltrations have remained under the radar.
When companies are breached, they are required by the SEC and state regulatory agencies to disclose the incident, but the rules are vague and fraught with loopholes.
Each state has its own notification requirements while the SEC says the hacking incidents need to be materially relevant to be declared.
Determining how soon a company needs to disclose its hacking incident is complicated as some companies work first with law enforcement to determine the breadth of the infiltration and what information was stolen.
Some experts believe the regulations need to be stricter so the public can be informed sooner that their personal information, often containing financial information such as credit card data, was stolen.
In Yahoo’s case, the company confirmed two years after the fact that users were affected by a state-sponsored actor… Read More
More State Data Breach Notification Laws
Excerpted from Health IT Security Report by Elizabeth Snell

Federal regulations, such as HIPAA and the HITECH Rule, garner the majority of attention when it comes to the data breach notification process. However, state laws also exist, and tend to vary.
Covered entities and business associates must ensure they adhere to their state’s requirements for data breaches, along with the federal regulations.
As technology continues to evolve, and medical information becomes more highly sought after on the black market, more states are adjusting their data breach legislation. While not all states include health insurance or medical information under what is considered protected personal information, it is still necessary that healthcare organizations understand state law.
Here are some of the more recent cases of amendments and laws affecting the state data breach notification process.
Earlier this year, Illinois Governor Bruce Rauner signed several amendments to a data breach notification law that would impact healthcare data security regulations starting in 2017.
The revised Personal Information Privacy Act will include health insurance and medical information… Read More
McCaul: US Must Gain Decryption Edge
Excerpted from Bank Info Security Report by Eric Chabrow
 House Homeland Security Committee Chairman Michael McCall is calling on Congress to increase spending on quantum computing research to ensure that the United States is the first nation to employ quantum computing as a tool to decrypt data.
House Homeland Security Committee Chairman Michael McCall is calling on Congress to increase spending on quantum computing research to ensure that the United States is the first nation to employ quantum computing as a tool to decrypt data.
“We can’t lose this one to the Chinese,” he says.
Speaking at a US Chamber of Commerce Cybersecurity Summit September 27th, McCaul (R-TX) noted, “If China develops quantum computing first, it would be a national security disaster.”
“If we want to be first in this area, the federal government has to be driving this.”
McCaul compared the quantum computing race to the space race in which the United States landed the first person on the moon.
“We want to be first in this; it’s really important,” he said.
The National Institute of Standards and Technology (NIST) has begun work on quantum computing… Read More
Tech-Savvy Lawmakers Found Blockchain Caucus
Excerpted from FedScoop Report by Shaun Waterman
 Two lawmakers are joining hands across the aisle to form a congressional caucus to promote blockchain – the distributed ledger technology underlying bitcoin and other cryptocurrencies.
Two lawmakers are joining hands across the aisle to form a congressional caucus to promote blockchain – the distributed ledger technology underlying bitcoin and other cryptocurrencies.
Congressmen Mick Mulvaney (R-SC) and Jared Polis (D-CO) announced the formation of the new bipartisan Congressional Blockchain Caucus Monday, saying it would be “dedicated to the advancement of sound public policy toward cryptocurrencies and other blockchain-based technologies.”
The move was welcomed by the technology’s enthusiasts.
“For the past two years, we’ve worked with both congressmen to educate lawmakers about blockchain – what it is, how it works, why it’s important,” said Jerry Brito, Executive Director of Coin Center, a think tank that focuses on policy questions raised by the new technology.
He told FedScoop the caucus would formalize that pedagogic work, “Especially with the new Congress.”
Its members would be lawmakers who see the potential in the technology and want it to flourish… Read More
Enterprise Storage: Opportunity for Right Vision
Excerpted from Forbes Report by John Webster
 As someone well-placed at a major storage vendor pointed out to me recently, big box storage arrays are going the way of the dinosaur because a single all flash array can replace multiple disk arrays.
As someone well-placed at a major storage vendor pointed out to me recently, big box storage arrays are going the way of the dinosaur because a single all flash array can replace multiple disk arrays.
And for that reason, the all flash revenue potential isn’t anywhere near that of disk even though solid state storage is a hot market.
Add to that the fact that storage software can’t make up the shortfall in revenue from exiting disk arrays either and you have a glum near-term outlook for the well-known big box storage vendors.
Nevertheless, enterprise storage is still a land of opportunity for those with the right vision.
Remember that those who have traditionally predicted meteoric data growth haven’t backed off.
The Internet of Things (IoT) is only the latest data volume generator and more will come when we get to some others now appearing on the horizon like blockchain.
So there are now some interesting startups looking to capitalize on some hot storage trends… Read More
NetApp to Unveil Hard Deck Program for Partners
Excerpted from CRN Report by Joseph Koyar
 NetApp is in the process of rolling out a “hard deck” program and other changes to its channel program, targeting accelerated growth in the storage vendor’s small and midsize business market.
NetApp is in the process of rolling out a “hard deck” program and other changes to its channel program, targeting accelerated growth in the storage vendor’s small and midsize business market.
A “hard deck” in channel terms is a program in which a vendor sets aside a certain number of customers or potential customers, typically its largest, as targets for either its direct sales team or direct sales working with partners, and leaving the rest to be handled exclusively by solution providers.
For NetApp, the hard deck is defined as a line just below NetApp’s top 1,000 accounts, said Scott Strubel, vice president of NetApp’s Americas partner organization.
Strubel told CRN at this week’s NetApp Insight conference in Las Vegas that the company’s partner presence above that line remains unchanged.
“We expect our partners to play a very big role above the line, in that top-1,000 accounts,” he said. “We have a very high percentage of our business in the top 1,000 accounts going with and through partners.”
“But we’re going to guarantee that, below that line, 100 percent of our business is going to go through partners… Read More
Coming Events of Interest
EuroCloud Forum — October 5th-6th in Bucharest, Romania. The seventh annual EuroCloud Congress will be held for the first time in Romania. With the theme “Creating New Frontiers in European Cloud,” it will be the sector’s largest forum on the future of cloud in Europe.
Internet & Mobile World 2016 — October 5th-6th in Bucharest, Romania. The largest business-to-business (B2B) expo-conference for information technology (IT) and digital solutions in Central & Eastern Europe (CEE).
Security of Things World USA — November 3rd-4th in San Diego, CA. SoTWUSA has been designed to help you find pragmatic solutions to the most common security threats facing the IoT.
Rethink! Cloudonomic Minds — November 21st-22nd in London, England. R!CM will cover how IoT is impacting cloud strategies and how to take advantage of these two key technology trends.
Government Video Expo — December 6th-8th in Washington, DC. GVE is the East Coast’s largest technology event for broadcast and video professionals, featuring a full exhibit floor, numerous training options, free seminars, keynotes, panel discussions, networking opportunities, and more.
CES 2017 — January 5th-8th in Las Vegas, NV. More than 3,800 exhibiting companies showcasing innovation across 2.4 million net square feet, representing 24 product categories.
Industry of Things World USA — February 20th-21st in San Diego, CA. Global leaders will gather to focus on monetization of the Internet of Things (IoT) in an industrial setting.
